Does Your Organization Need a Data Diet?

The scenario is all-too-familiar: There’s a security breach, and afterward, the
affected organization asks what it must do to better protect its data. But what
if that organization never collected and stored that sensitive information in
the first place? Often, the best defense against an embarrassing and costly
breach is to collect only data that is essential to an entity’s mission. Some
who work in computer privacy circles refer to this as “going on a data diet.”
They know the temptation is great for organizations to bulk up on data of all
kinds. After all, storage costs are low. With the move to the cloud, an
organization doesn’t even need to invest in hardware and upkeep to store the
information it collects. So why not grab whatever data a customer or client is
willing to provide? Because we live in a time when the only sensible approach to
computer security is to wonder when your entity might be breached—not if. That’s
why it pays to not only go on a data diet, but to adopt a regimen for keeping
your organization’s databases lean and, as a result, your customer relationships
healthy.
DeFi Opens New Possibilities for Banks Willing to Embrace Change
Banks have already shown that they are aware of the growing urgency to pivot
fully into the digital age. FinTechs have been key drivers in the development of
banking alternatives, offering customers new ways to pay and manage their money,
and urgency is building for banks to adapt. Authentication plays a role in the
customer experience, and DeFi can help improve trust between financial
institutions (FIs) and the customers who trust them with their money, the
panelists said. Vicandi told PYMNTS that the growth in DeFi is shaking the very
core of financial services. ... “They’ve produced their own products, sell those
products though their networks, to their own end customers.” But in the current
environment and with the emergence of blockchains, Vicandi said that DeFi exists
as a threat not only to the regional banks which tend to lack the scale and of
their larger national and international brethren, but as an existential and
cultural change to finance as we know it.
Solutions against overfitting for machine learning on tabular data
The simplest way to detect overfitting is to look at the performance between
your train and test data. If your model performs very well on the training data
and poorly on the test data, your model is probably overfitting. ...
Cross-validation is an often used alternative to the train/test split. The idea
is to avoid creating a train/test split by fitting the model multiple times on a
part of the data, while testing on the other part of the data. At the end, all
parts of the data have been used for both training and testing. The
cross-validation score is the average score on all the test evaluations that
have been done throughout the process. The cross-validation score is based only
on test data, and therefore it is a great way to have one metric instead of a
separate train and test metric. We could say that cross-validation is equivalent
to the test score of the model. Using the cross-validation score will not help
you to detect overfitting, because it will not show you the training
performance. So it is not a way to detect overfitting, but the cross-validation
score can tell you that your test performances are bad (without the reason).
Working Together as Embedded Engineering Teams

Part of the value of these long-term pairings is you build relationships and
context. It is expensive to move people because it breaks these connections.
Most embedded organizations tend to move people more than they should. It can be
frustrating to have embeds on your team if you can’t rely on them to stay. Yet
it is tempting for the embed’s manager to move people around. They want to react
to changing needs, and sometimes there aren’t enough people to go around. This
can be a source of friction. A new embedded person has a more complex situation
than new employees do. They have another manager and things outside your team
they may be paying attention to. Kick off the relationship with explicit
conversations. Spend twice the care you would with onboarding a generalist
employee. Gus Shaffer offers this advice: “One thing that I found helpful when
embedding staff engineers was to conduct a standard Kick-off process with a
Statement of Work as output. Early on I learned the hard way that leaving
success criteria loose leads to lingering engagements/disappointment/confusion.”
Microsoft under fire in Europe for OneDrive bundling; legal fight brewing
Lead by Nextcloud, a coalition of European Union (EU) software and cloud
organizations and companies formed the "Coalition for a Level Playing Field.”
“Microsoft’s combination of the dominant Windows (operating software) with the
OneDrive (cloud) offering makes it nearly impossible to compete with their
SaaS services,” Nextcloud said in a blog post. “It illustrates
anti-competitive practices such as ‘self-preferencing’ on the basis of the
market dominance of Windows.” Frank Karlitschek, CEO and founder of Nextcloud,
also pointed out in his blog that over the last several years, Microsoft,
Google, and Amazon have grown their market shares to 66% of the total European
market, while local European software and service providers have declined from
26% to 16%. “Behavior as described above is at the core of this dramatic level
of growth of the global tech giants in Europe,” Karlitschek said. “This should
be addressed without any further delay.” “There are deliberate, abusive
practices and those practices are no accidents. Other Big Tech firms are
showing similar conduct.
RansomOps: Detecting Complex Ransomware Operations

It’s possible for organizations to defend themselves at each stage of a
ransomware attack. In the delivery stage, for instance, they can use malicious
links or malicious macros attached documents to block suspicious emails.
Installation gives security teams the opportunity to detect files that are
attempting to create new registry values and to spot suspicious activity on
endpoint devices. When the ransomware attempts to establish command and
control, security teams can block outbound connection attempts to known
malicious infrastructure. They can then use threat indicators to tie account
compromise and credential access attempts to familiar attack campaigns,
investigate network mapping and discovery attempts launched from unexpected
accounts and devices. Defenders can flag resources that are attempting to gain
access to other network resources with which they don’t normally interact, and
discover attempts to exfiltrate data as well as encrypt files.
A unique quantum-mechanical interaction between electrons and topological defects in layered materials
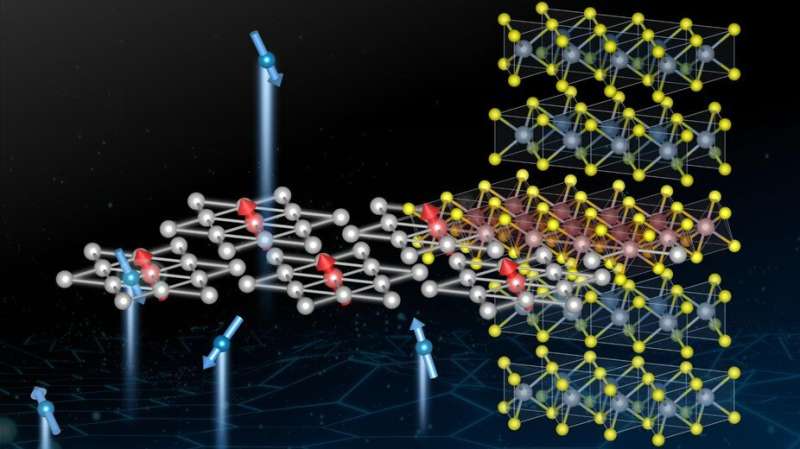
"Once we first identified the anomaly in electronic conductivity, we remained
very puzzled," says Edoardo Martino, the study's first author. "The material
was behaving like a pretty standard metal whose electrons move along the
plane, but when forced to move between planes its behavior became that of
neither a metal nor an insulator, and was unclear what else to expect. It was
thanks to a discussion with our fellow colleagues and theoretical physicists
that we were pushed in the right direction: just apply a magnetic field and
see what happens." After applying the magnetic field, the EPFL scientists
realized that the more powerful the magnet, the more exotic the material's
behavior becomes. They started experimenting with 14 Tesla superconducting
magnets available at EPFL, but soon they realized they needed more. Working
with the Laboratoire National des Champs Magnétiques Intenses in Grenoble and
Toulouse, they accessed some of the world's most powerful magnets.
The purpose of “purpose”
It starts with a goal that feels directly connected to the business, rather
than a lofty statement that could be used by dozens or hundreds of other
organizations. “It has to be real and tangible and live,” said author Margaret
Heffernan when I interviewed her about her most recent book, Uncharted: How to
Navigate the Future. “It has to be something people feel that they can do.”
These are the difficult questions that every leader must wrestle with, even
though they may seem philosophical and not directly relevant to the bottom
line: Why do you matter? How do you make a difference? What would be lost if
your organization went out of business? Healthcare businesses can make a
credible case that they are improving or saving people’s lives. A nonprofit is
often founded with a clear idea of the impact it wants to have. But the job
can seem trickier if you are in a kind of commodity business. Imagine for a
second that you run, say, a company that processes beets for sugar. How do you
build a purpose around that? Paul Kenward took up that challenge. As managing
director of British Sugar, which is based in the east of England, he faced the
task of defining a sense of purpose for the company.
Report: No Patch for Microsoft Privilege Escalation Zero-Day

The flaw found under the "Access work or school" settings can only be
triggered by clicking on "export your management log files" and confirming by
pressing "export," he says. "At that point, the Device Management Enrollment
Service is triggered, running as Local System. This service first copies some
log files to the MDM Diagnostics folder, and then packages them into a CAB
file whereby they're temporarily copied to Temp folder. The resulting CAB file
is then stored in the MDM Diagnostics folder, where the user can freely access
it," Kolsek notes. He highlights that while copying the CAB file to the Temp
folder is vulnerable, a local attacker could create a soft link with a
predictable file name used in routine export processes, directing to some file
or folder that the attacker would want to have copied, in a location
accessible to the attacker. "Since the Device Management Enrollment Service
runs as Local System, it can read any system file that the attacker can't,"
Kolsek notes.
Design Patterns for Serverless Systems
In agile programming, as well as in a microservice-friendly environment, the
general approach to designing and coding has changed from the monolith era.
Instead of stuffing all the logic into a single functional unit, agile and
microservice developers prefer more granular services or tasks obeying the
single responsibility principle (SRP). Keeping this in mind, developers can
decompose complex functionality into a series of separately manageable tasks.
Each task gets some input from the client, executes its specific
responsibility consuming that input, and generates some output, which is then
transferred to the next task. Following this principle, multiple tasks
constitute a chain of tasks. Each task transforms input data into the required
output, which is an input for the next task. These transformers are
traditionally known as filters and the connector to pass data from one filter
to another is known as a pipe. A very common usage of the pipes and filter
pattern is the following: when a client request arrives at the server, the
request payload must go through a filtering and authentication process
Quote for the day:
"Strategy is not really a solo sport _
even if you_re the CEO." -- Max McKeown
No comments:
Post a Comment