Are California's New Data Privacy Controls Even Legal?

In the rush to get a GDPR-style regulatory framework in place in California, no one seemed to stop and ask whether what they were doing was actually legal. Indeed, many of the controls enshrined in the European law are fundamentally at odds with American principles of permissionless innovation and open interstate commerce. Huddleston and Adams point out that state laws like the CCPA may run into constitutional problems concerning speech and interstate trade. Data is often speech. Laws that regulate speech are subject to a high level of legal scrutiny because of our First Amendment protections. States don't get to ignore the First Amendment just because they really don't like Facebook. If they try to regulate data-as-speech, the courts may promptly strike them down. How might this look in terms of a state data law? One popular idea is to treat data usage differently depending on whether that data is "for sale" or not. Given the populist anger about data brokers and "monetizing our personal information," it makes sense that this would make its way into a bill.
Your First Month as a CISO: Forming an Information Security Program
As with any significant undertaking, it makes sense to begin by understanding the current state of the security program and the context in which you'll manage it. Start by covering the following: What security concerns do you, your colleagues, and your customers have? What gaps exist, and how might they affect the business? Sometimes figuring this out requires a formal assessment. Other times, it may require an informal survey, conversations with colleagues, and analysis to get to a sufficient starting point. I was fortunate to become the CISO after holding another role at Axonius, but there were many questions that my new position required me to ask that I hadn't asked before; What expectations does the organization have of the security program and your role? Account for your own ideas and, of course, get input from your manager and other stakeholders. When outlining the goals, understand the business and technical needs that will influence the security program. You can see my objectives at Axonius, if you're curious; and Get to know the technical and business environment in which you'll be operating.
Agile teams: 5 signs of trouble

An agile team needs autonomy, but every team needs proper management and organization given the fast-paced nature of agile development. The duty often lies with the scrum master, who should be implementing the best communication processes suited for the team. However, if your daily standups are longer than 15 minutes, then your team might not be as organized as you think. I have seen many different organizations hold long, crowded meetings with people who weren’t necessary to the project - which, not surprisingly, led to a bored and unmotivated team. The best practice is to narrow the number of invites to the people who are vital to the task at hand: Wasted meeting time leads to a lower ROI. Another consideration is to assess how teams are communicating on schedules, stories, and responsibilities. Determine if your team is communicating adequately on their boards, and ensure that everyone understands the overarching goal and that each person is aware of their role. If these points are not drummed into each individual member, then you need to take a step back and reorganize how the work is being done.
3 Real-World Disaster Recovery Scenarios
One of the worst-case scenarios that a modern business can face is a disaster that destroys part or all of its datacenter—and all of the servers and disks inside it. While such a situation is rare, it can happen, and not only as a result of a major natural disaster like an earthquake or hurricane. Issues such as electrical surges and even ill-fated squirrels can cause permanent datacenter damage. The best way to prepare your business for recovery from this type of disaster is to ensure that you have offsite copies of your data. If your production data lives on-premise in one of your datacenters, this would mean keeping backups of the data at another datacenter site or in the cloud. If your data is hosted in the cloud, you could back it up to local storage, to another cloud or a different region of the same cloud. You will also want to make sure that you have a way of restoring the backup data to new infrastructure quickly. Moving large amounts of data from one site to another over the Internet can take a long time, so it’s not always a wise strategy within the context of disaster recovery.
Expected skills needs for the future of work
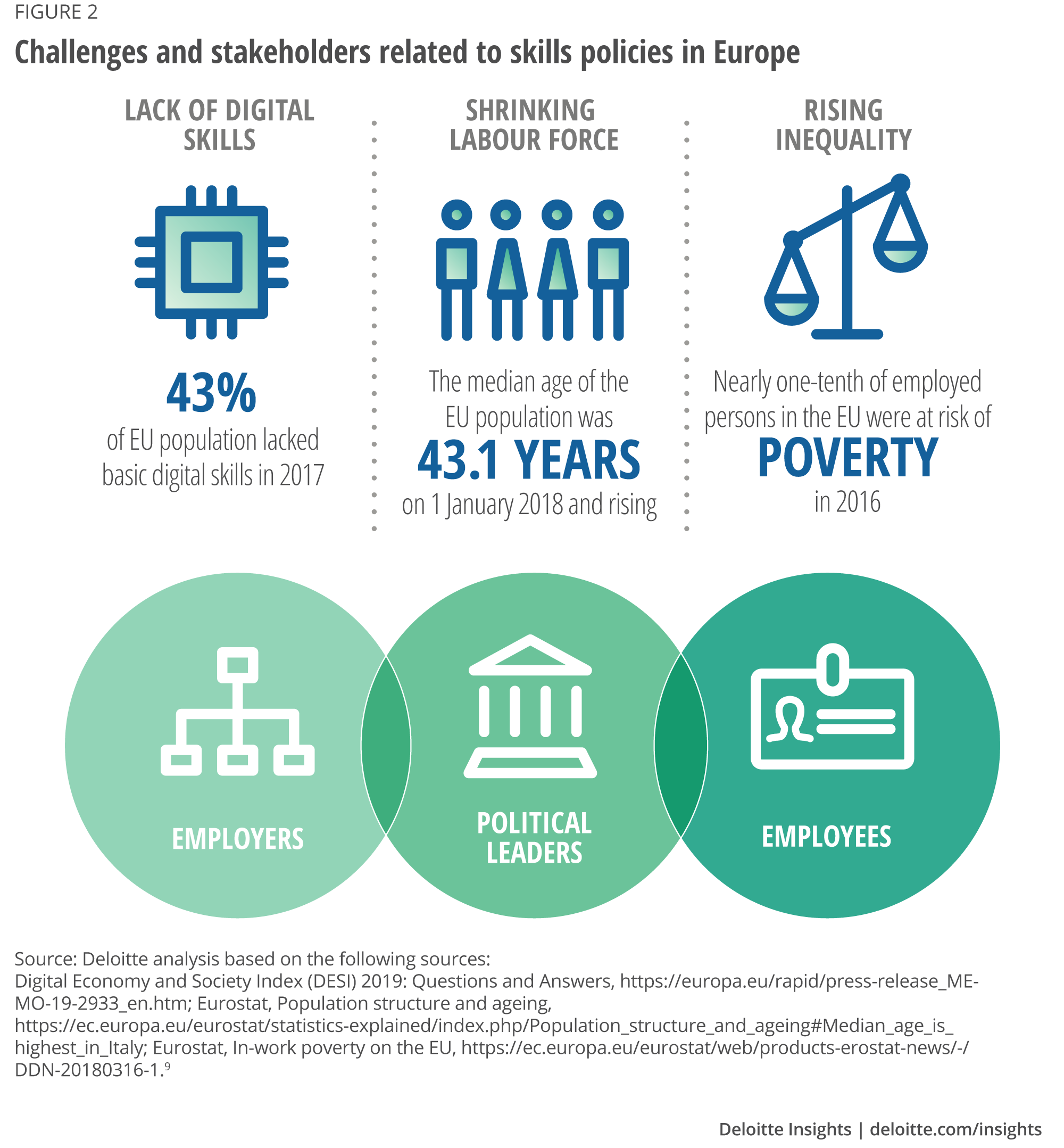
The ‘future of skills’ receives considerable attention from governments around the world and stands high on the political agenda of many international organizations. As an example, the EU has adopted an overarching strategy – the New Skills Agenda7 – to tackle a wide range of skills-related challenges. Many of the tools contained in this initiative aim at empowering individuals to develop new skills or to exploit the skills they already have. Nevertheless, even with the most innovative policies in place and the mobilization of huge public resources, the success of any skills strategy depends heavily on the motivation of individuals and their decisions to take a step forward. Hence, it is of great importance for policymakers and other stakeholders to understand the impact of technological change from the perspective of workers in order to develop effective policy tools to create a future that works for all. A number of academic studies already shed light on the potential changes in the labour force of the future. This article which presents the opinions of more than 15,000 workers across ten European countries, was designed to contribute to the overall debate by giving voice to the workers themselves and potentially bring them closer to policymakers.
Technology is the answer to the healthcare productivity challenge
While there are major productivity gains to be secured through better management of clinical activity, technology can also transform many of the NHS’ support functions. In particular, the recruitment and the management of temporary staff is often slow and inefficient, with checks being carried out manually. Yet many of these processes could be automated and significantly reduce the time taken to get staff where they are needed on the ward. The opportunities are not just to improve the way the providers work. Patients too can benefit from the increasing availability of online and skype consultations which save them time and provide better, more accessible care. They are also more efficient. It is undoubtedly true that technology has often been hailed as the answer to the NHS’ problems and then it has disappointed. The reasons for these failures lies in the NHS’ tendency to buy technology and then look for a problem for it to solve. To secure the productivity gains it needs, that approach must be reversed.
Tech-skill certificates may be more valuable than a college degree

A study, "Degrees at Work," released by Emsi in August, found only two majors directly sent grads into its business: engineering and computer science. The study also revealed that non-STEM grads devalue their education. Yet there are many available tech jobs , including positions unfilled for up to months at a time. And a reason for the disparity? Lack of skills. Graduates, and students in general, lack not only experience, but also practical skills to land the kind of jobs to which they aspire. "Our educational system is not equipped to meet the demands of the modern workplace," said Grace Suh, vice president of education for IBM citizenship. "We have more jobs than skilled people to fill them. There are already more than 700,000 open technology jobs in the US, and another half million expected over the next decade. Part of the problem is that we've focused too heavily on just one path to a good job: a bachelor's degree." To address this issue of the educated, but unskilled, corporations pair with schools and alternative credentialing programs to help fill open positions, as well as match employees with their interest.
6 Essential Security Features for Network Monitoring Solutions

What are the essential security features that every network monitoring solution needs to have? Traditionally, network monitoring solutions focus strictly on examining the performance of a network and all connected devices. However, in order to unify security and performance monitoring for network professionals, an increasing number of network monitoring tools include security features. As one of the largest causes of performance-related issues for networks is security threats (such as malware), network monitoring solutions must be prepared to deal with security-related performance events. The exact scope of a network monitoring tool’s security feature set depends on the vendor’s focus, but every solution should have at least some native security capabilities built-in. Below, we’ve listed six essential security features for network monitoring solutions! If you’re looking for resources to help you evaluate network performance and security monitoring solutions, our free Network Monitoring Buyer’s Guide has you covered!
DataOps: Your path to a culture of inclusion and innovation

A typical DataOps team incorporates data analysts, who prepare and wrangle data for operations and analysis; data scientists, who find new and emergent patterns in data, and data engineers, who create stable, scalable data pipelines. You may already have some or all of these roles within your company, or you may be able to outsource some of these functions to a third-party. Then there are customers, both internal and external, who focus on defining data requirements and consuming data. People are just one part of the equation, and it is the convergence of people, process and technology that is needed to run your DataOps. To help the DataOps team succeed in their endeavours, there are specific tools available, which are generally more advanced technologies than those used in DevOps and agile methodologies. Self-service tooling for data discovery (search), data transformation and preparation, warehousing, data lake, AI/ML and API management can all play vital roles in developing your DataOps. This advanced tooling can lead to the blurring of roles and a more emergent data ecosystem.
Wasmtime Enables Running WebAssembly From .NET Programs
Huene says sharing WebAssembly modules is significantly easier than sharing native libraries, e.g. C libraries, which requires platform-specific builds. Instead, WebAssembly modules can be distributed without modifications. ... This workflow is not yet perfectly streamlined, since you have to deal with a number of low-level details such as converting between values, but things should improve in the future, says Huene, thanks to the upcoming WebAssembly interface types proposal. This will improve interoperability and simplify the exchange of complex data types between WebAssembly and .NET without requiring too much of glue code to do value marshalling and making a WebAssembly module appear just as any other .NET package. Untrusted code isolation is made possible by WebAssembly requirement of explicitly importing all external functions that a module is allowed to use and only accessing a region of memory reserved by the host platform. This makes WebAssembly modules effectively run inside a sandbox that enables the execution of foreign plugins with the guarantee they cannot access the host platform indiscriminately.
Quote for the day:
"Leaders begin with a different question than others. Replacing who can I blame with how am I responsible?" -- Orrin Woodward
No comments:
Post a Comment