Risk and resilience priorities, as told by chief risk officers

CROs acknowledge that they need to spend more time considering “over the horizon
risks.” This gap in thinking was brought into sharp focus by the heavy impact
the COVID-19 pandemic and geopolitical tensions had on their institutions’ risk
profiles—including second- and third-order effects—such as supply chain risk,
inflation, and rising interest rates—which were not anticipated by most banking
executives. Institutions were little prepared to address these highly
consequential risks. The failure goes well beyond risk functions, however. Many
organizations used forecasting to develop market strategies, but this approach
failed to pick up major reality shifts in the recent past—from the financial
crisis of the 2000s to the pandemic to geopolitical realignments. Leading
institutions are moving to scenario-based foresight to increase institutional
resilience against over-the-horizon risks. The risk function can play an
important role here in ensuring that the scenarios capture existing and expected
risks, while aligning function priorities against scenarios.
Should central banks use DLT for CBDC?
When it comes to the topic of whether “to DLT or not to DLT” in the world of
CBDC, Mikhalev took a slightly different position. He stated central banks have
taken a top-down approach for hundreds of years, and while this works in many
jurisdictions, it doesn’t work as well in emerging markets. “To have blockchain
or not for CBDCs is increasingly being answered in the negative across
established economies. ... This could reduce volatility in these emerging
markets. These aspects which are specifically inherent to decentralisation and
the distribution of power, should have positive effects in emerging economies.”
However, Mikhalev continued, in each conversation carried out with central
bankers in developed countries, he has found that they perceive blockchain as
having little effect in situations where the supervisory institutions are not
ready or unwilling to alter their business models around a new technology.
“Blockchain doesn't really make much difference if nothing changes in terms of
the existing established top-down structure of CBDCs. However, in emerging
economies, this seems to differ,” Mikhalev noted.
A compliance fight in Germany could hurt Microsoft customers

German compliance authorities “can live with the situation where Microsoft
pretends to do everything right and the authorities pretend to have done
everything in their power to force Microsoft to become compliant,” Hence said in
an interview with Computerworld. Microsoft “does not fulfill the most basic
requirements of GDPR. They lack basic transparency. We can’t assess what they
are doing because they are not telling us.” This is where politics comes
into play, wheret practical forces can influence government compliance actions.
German regulators “are afraid of retribution. (With regulators thinking) we
won't get more budget if we say that you can’t use Office any more. Or even
Google Analytics, any more,” Hence said. “These are poltical issues. Nobody
wants to be the bad guy.” Thus, Microsoft is likely to skate on the issue —
at least for now. But what about enterprise IT execs? Are companies using
Microsoft products immune from compliance punishments? Not necessarily. It might
not seem fair to let Microsoft get away with this but to fine and otherwise
punish its customers, but Hence argues that's quite likely. And not just in
Germany.
Policy Developments around Blockchain
On September 15, 2022, Singapore’s Monetary Authority (MAS) launched the
Financial Services Industry Transformation Map 2025 that provides a
framework of strategies to develop the country as a leading global financial
center through enhanced payment connectivity to build a responsible digital
asset ecosystem. It also laid out clear strategies to explore DLT in use
cases such as cross-border payments, trade finance, and capital markets,
besides supporting tokenization of financial assets. The policy supports a
central bank digital currency (CBDC) and public-private collaboration to
develop the infrastructure required to deliver such a currency. However, the
first off the blocks in 2022 was the Securities and Futures Commission of
Hong Kong which issued a joint circular with the HK Monetary Authority on
intermediaries that can undertake virtual asset-related activities. Per the
statement, intermediaries distributing virtual assets need to comply with
the SFC’s requirements for sale of the products.
Share of Emerging Technologies in IT Budgets

National Association of Software and Services Companies (NASSCOM) and Boston
Consultancy Group (BCG) today released a report titled "Sandboxing into the
Future: Decoding Technology's Biggest Bets" on the sidelines of NASTech 2022
in Bengaluru. The report aims to uncover and develop perspectives on big-bet
technologies that can potentially disrupt markets in the next 3-5 years.
Enterprise Tech spending is estimated to reach $4.2 Tn by 2026 globally,
amongst which Tech Services companies represent the largest segment and are
expected to become $1.7 Tn by 2026 with a CAGR of 8.1%. As part of the
study, 28 emerging technology themes from 11 tech families were identified –
across markets and verticals - with the potential to disrupt markets, basis
current tech spending, growth potential, innovation maturity, and funding
momentum. Amongst these 12 emerging technologies, with high funding momentum
and R&D focus, have emerged as the “Biggest Bets,” including, Autonomous
analytics, AR & VR, Autonomous Driving, Computer Vision, Deep learning,
Distributed Ledger, Edge Computing, Sensor Tech, Smart Robots, Space Tech,
Sustainability Tech, and 5G/6G.
Amazon Wants to Kill the Barcode

The system, called multi-modal identification, isn't going to fully replace
barcodes soon. It's currently in use in facilities in Barcelona, Spain, and
Hamburg, Germany, according to Amazon. Still, the company says it's already
speeding up the time it takes to process packages there. The technology will
be shared across Amazon's businesses, so it's possible you could one day see
a version of it at a Whole Foods or another Amazon-owned chain with
in-person stores. The problem that the system eliminates -- incorrect items
coming down the line to be sent to customers -- doesn't happen too often,
Amazon says. But even infrequent mistakes add up to significant slowdowns
when considering just how many items a single warehouse processes in one
day. Amazon's AI experts had to start by building up a library of images of
products, something the company hadn't had a reason to create prior to this
project. The images themselves as well as data about the products'
dimensions fed the earliest versions of the algorithm, and the cameras
continually capture new images of items to train the model with. The
algorithm's accuracy rate was between 75% and 80% when first used, which
Amazon considered a promising start.
Cyber crime threatens manufacturing production

Targeted attacks are the most common, with smaller companies often the most
vulnerable, yet many offering no cyber security training to staff. Sixty-two
percent of manufacturers now have a formal cyber security procedure in place
in the event of an incident, up 11% on last year’s figures with the same
number giving a senior manager responsibility for cyber security. More than
half (58%) have escalated this responsibility to board level. Stephen
Phipson, CEO of Make UK, the manufacturers’ organisation said: “Digitisation
is revolutionising modern manufacturing and becoming increasingly important
to drive competitiveness and innovation. “While cost remains the main
barrier to companies installing cyber protection, the need to increase the
use of the latest technology makes mounting a defence against cyber threats
essential. No business can afford to ignore this issue and while the
increased awareness across the sector is encouraging, there is still much to
be done. “Every business is vulnerable, and every business needs to take the
necessary steps to protect themselves properly.”
How Do Agility and Software Architecture Fit Together?
But the question is, I mean, when we, when we create software, we make
decisions all the time. So the question is, what what is architecture? Like?
How is architecture is different from all of these normal decisions that we
take. And when I think about that, I always use a very loose definition. And
this is, architecture is about the important things. I think Martin Fowler
said something like that, and I really liked that, because it's about those
things that have a high risk or a high cost of change, if we need to re
evaluate them if we need to redo them. And, and I think that that these
types of decisions qualifies architectural decisions. And then the question
is, I mean, when do we when do we decide on these important things, whatever
important means, and in my opinion, there is something that is quite
underappreciated in most Scrum teams and from from my experience, it is that
the product owner has a very, very important part when it comes to software
architecture, because it always starts with what is the vision of the
product?
What’s a distributed compliance ledger and how is one integrated into Matter?
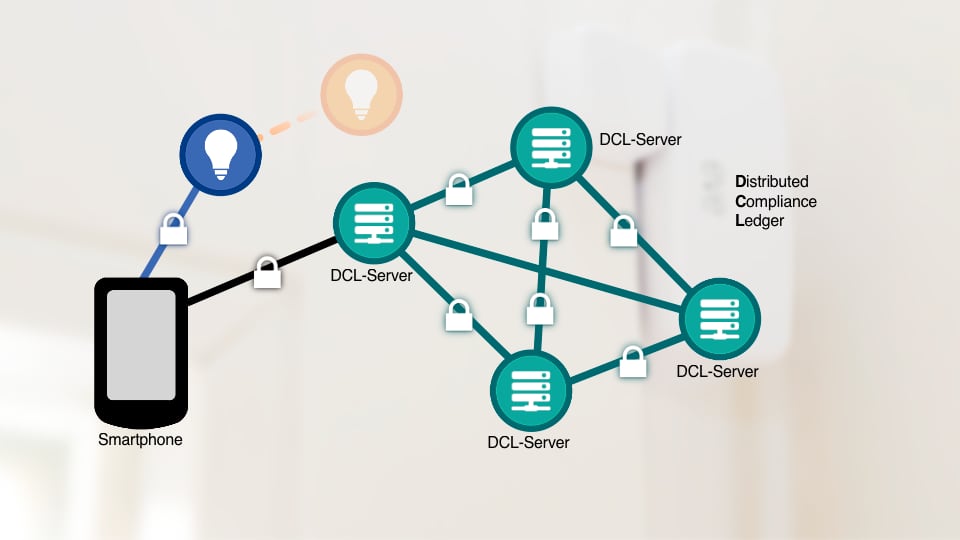
Matter’s DCL is a network of independent servers operated by the CSA and its
partners. Each DCL server includes a complete copy of the database. The
original data is managed and controlled by the CSA. The DCL is implemented
by connecting all the servers using a cryptographically secured protocol.
The DCL makes it difficult to manipulate the data in the database and
increases the security of Mater devices and networks. ... The manufacturer
writes the data to the database to add a new product to the DCL. It’s not
‘active’ until approved by the CSA. Once the device has passed certification
and the CSA has received the confirmation from the PPA, the CSA adds
“certified” to the status list letting all members of the Matter ecosystem
know that this is an approved device and ready to be added to Matter
networks. Database access is restricted. Device makers can only add data for
their own products that are linked to their vendor identification (VendorID)
number. Software updates must also be linked to the VendorID, or they will
be rejected. Official CSA PPA bodies or the CSA can confirm or revoke device
compliance data.
4 tips for implementing consistent configuration and automation standards

The team regularly reviews standards with squads and SMEs to keep the
operating system and middleware standards current and compliant with
security and other requirements. We created a naming structure for standards
to maintain version control for compliance and audit purposes. The standards
form a baseline for maintaining playbooks for consistent automation across
the environment. The organization also promotes InnerSource (the use of open
source practices to improve internal software) and advocates reusing
playbooks. We base the playbooks on common configuration and automation
standards. This establishes governance for operating systems and middleware
support. ... Automation is a continuous journey. Achieving touchless
deployments requires standard configurations, processes, procedures,
security guidelines, and other dependencies that you must review and
validate periodically. These standards form the baseline that the automation
team will adopt and implement.
Quote for the day:
"We are drowning in information, but
starved for knowledge." -- John Naisbitt
No comments:
Post a Comment