4 Ways CFOs Can Mitigate Costs of Poor Data Management

CFOs can also join forces with their IT counterparts to elevate security
procedures as part of the company ethos (without detracting from employee
productivity). Incentivizing employees to be mindful of data security and data
management policies that could lead to financial impacts is one way to
jump-start this effort. ... When approving IT expenditures, CFOs have a great
opportunity to ensure the emphasis is on data management projects that reduce
financial risk and prevent waste of resources. For example, it may be worth
investing in the establishment of a single sign-on for company employees. A
single sign-on allows access to company data to be quickly turned off upon an
employee’s departure. In general, tools that speed up the response time to
vulnerabilities and reduce the attack surface — and hopefully stop breaches
before they happen — are worth prioritizing. Freeware for data sanitization
exists, but enterprise-grade tools provide assurances, such as certificates of
erasure, which equate to less risk. Also, automating the different stages of
data management processes not only increases productivity but can also
significantly expedite the recycling or disposal of assets, mitigating storage
issues and security risks.
The Unheard Story of Lost Anonymity
Although there are data privacy regulations in the picture, it is expected
that pieces of our information will fall into some wrong hands through
organization acquisitions, data breaches or data theft. Have you at any point
asked yourself why banks you have never opened an account with flood you with
calls offering loans and credit cards? Or why you receive countless spam
messages from unknown numbers asking you to update your KYC? How do these
people you never shared your information with know your full name and your
number? It is important to understand that your number is not simply a number.
It is connected to a lot of information that may be sensitive—for example,
your employer information, bank balance, personally identifiable information
(PII) or maybe even personal health information. This information might begin
from data you provided to a bank, to an e-recharge website or to a
retail/e-commerce store where you might have made a purchase; however, from
that point onward, your consent does not make any difference. Your information
could be sold to anyone, from a marketing agency to criminals looking for
targets.
What is ChatGPT and why does it matter? Here's what you need to know
Despite looking very impressive, ChatGPT still has limitations. Such
limitations include the inability to answer questions that are worded a
specific way, requiring rewording to understand the input question. A bigger
limitation is a lack of quality in the responses it delivers -- which can
sometimes be plausible-sounding but make no practical sense or can be
excessively verbose. Lastly, instead of asking for clarification on ambiguous
questions, the model just takes a guess at what your question means, which can
lead to unintended responses to questions. Already this has led developer
question-and-answer site StackOverflow to at least temporarily ban
ChatGPT-generated responses to questions. "The primary problem is that while
the answers that ChatGPT produces have a high rate of being incorrect, they
typically look like they might be good and the answers are very easy to
produce," says Stack Overflow moderators in a post. Critics argue that these
tools are just very good at putting words into an order that makes sense from
a statistical point of view, but they cannot understand the meaning or know
whether the statements it makes are correct.
HHS: Web Trackers in Patient Portals Violate HIPAA
The warning from the department's Office of Civil Rights comes months after
revelations that medical providers have used free web user tracking code
offered by Facebook and Google in websites frequented by patients. Facebook
parent Meta faces a proposed class action alleging it violated privacy law by
collecting patient information via its Pixel tracker, including data on
doctors, conditions and appointments. At least three major healthcare
organizations in recent weeks have treated their previous use of web tracking
code as a reportable data breach. ... "Providers, health plans, and
HIPAA-regulated entities, including technology platforms, must follow the law.
This means considering the risks to patients' health information when using
tracking technologies,” said HHS OCR Director Melanie Fontes Rainer in a
statement. The bulletin specifies that trackers embedded into login pages such
as a patient or health plan beneficiary portal or a telehealth platform are
particularly susceptible to transmitting protected health information if they
contain trackers.
The Case for Transparency in Data Collection

The relationship between consumers and data transparency (or in some cases,
lack of transparency) is not unique to internet marketing. Parallels can be
drawn between online data transparency and methods used for years by retailer
loyalty programs. Long before the internet, enrolling in a loyalty program
gave the issuer access to a consumer’s personal spending habits, geographic
spending data, and other personal data -- and consumers rarely read the fine
print in their agreements. The reality is, reading and taking the time to
digest privacy policies is a huge ask, especially in the context of the
internet, which has become synonymous with instant gratification. One study
found it takes more than 200 hours -- longer than a typical work month -- to
read the average privacy policy word-for-word on the websites we visit each
year. Although that is an entertaining statistic, most consumers do not have
any idea what they are saying yes to when signing into apps or agreeing to a
website’s terms of service. They are blissfully unaware of exactly how
companies use consumer data to test marketing campaigns, improve the customer
journey, or share with third parties.
Tone From The Top: How Top-Down Inspires Bottom-Up In PrivSec

Simply put, privacy and security are everyone's responsibility in the modern
workplace. Gone are the days when cybersecurity "belongs" to the IT department
and privacy "lives" in the legal team. Physical security and guest privacy
begin at the reception desk, social engineering defenses start in the call
center, and business email compromise (BEC) prevention starts in the finance
office. Privacy and security are role-based these days, and as such, you need
to start right at the bottom and work your way up. ... In working your way up
the chain, it generally goes well until you hit the complexities of divisions
with certain powers to bypass policy, often at the executive level. When any
member of an executive team regularly avoids adhering to policies, it
undermines the policy that has been put in place. Often, this is exercised
under the guise of "being agile" or "responding to demand" in the quickest way
possible, but it does far more damage than it does good. Effectively in these
situations, the executive has stopped playing by the company rules. And when
this happens, it very easily and very rapidly rubs off on the rest of the
staff and paves the way for "normalization of deviance."
What you should know when considering cyber insurance in 2023

Security advisors and consultants say they see insurers asking more questions
of those seeking insurance policies. They’re requiring proof that applicants
have achieved certain levels of security hardening, such as SOC 2 compliance.
They’re reviewing security strategies and policies as well as security
training and awareness programs. “Insurance companies are taking a closer look
at all of those,” Wilkison says. This in turn has required more involvement
from enterprise security leaders in the insurance procurement process. ...
CISOs may also have to make adjustments to their strategies based on insurer
demands. “If you want to get your claim, you usually have to use their panel
of vendors or follow their procedures,” says Michael Pisano, a managing
director at global consulting firm Protiviti. For example, they will be
required to have detailed response and recovery plans in place—in the event of
an incident, insurers want clients to meet specific requirements, such as
which lawyers should be used and what forensics should be performed, and by
whom.
How to Build Privacy By Design Into Customer Experience

The demands for data privacy are growing and there is no turning back. But is it
too late to make a real difference? “We need to push back on the thinking that
privacy is dead,” says Baber Amin, COO of Veridium, an integrated identity
management platform provider. “It is not dead. In fact, more than ever, it needs
to be nurtured and thought through in light of modern technology. A good example
of not giving up is [the US Supreme Court case] Carpenter v United States.” The
question remaining in this discussion is: Are companies ready, willing, and able
to provide data privacy protections? ... “The proper way to go forward is
through transparent privacy policies that notify users about the data and
information we collect,” says Apu Pavithran, CEO of Hexnode, a device management
company. “Transparency is the key if you want to generate trust and build a more
valuable connection with consumers. However, building trust via openness
requires time and effort, but can help firms outperform their competitors in
terms of sales, revenue, and marketing ROI.”
Value-creating chief data officers: Cementing a seat at the top table

Across every industry, we found more CDO appointments have been made since our
last study. The heavily regulated financial services industry—where effective
use of data is vital for both reporting and compliance—continues to set the bar.
Just over half of banks and insurers now have a CDO in place, a number that
accounts for 22% of CDOs globally. But although we saw most CDOs appointed at
banks (25), and capital goods (18) and software (13) firms this year, household
and personal products, automotive, food and beverage, and retail organizations
saw the highest year-on-year increase in the proportion of companies with a CDO.
Regardless of industry, CDO growth is still being driven by the largest
companies—those with multimillion-dollar revenues and the largest head count.
This is likely due to their greater organizational and technological complexity.
However, CDO appointments are on the rise across businesses of all sizes. The
emergence of CDO positions in midsized firms suggests the role is beginning to
be more widely recognized as a useful way to help executive teams pursue
business growth.
What Is Code Churn?
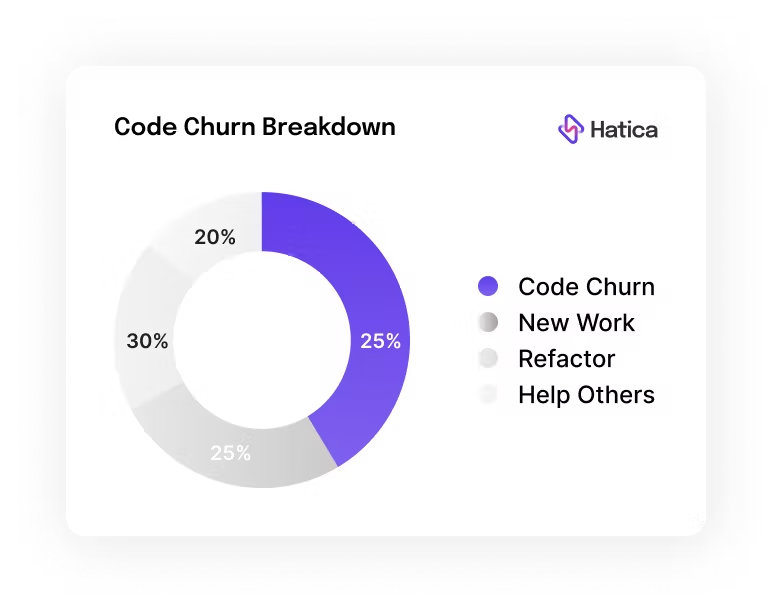
Code churn, also known as code rework, is when a developer deletes or rewrites
their own code shortly after it has been composed. Code churn is a normal part
of software development and watching trends in code churn can help managers
notice when a deadline is at risk, when an engineer is stuck or struggling,
problematic code areas, or when issues concerning external stakeholders come up.
It is common for newly composed code to go through multiple changes. The volume
and frequency of code changes in a given period of time can vary due to several
factors and code churn can be good or bad depending upon when and why it is
taking place. ... Code churn varies depending on many factors. For instance,
when engineers work on a fairly new problem, churn would most likely be higher
than the benchmark, whereas when developers work on a familiar problem or a
relatively easier problem, churn could most likely be lower. Churn could also
vary depending on the stage of a project in the development lifecycle. Hence, it
is important for engineering managers and leaders to develop a sense of the
patterns or benchmarks of churn level for different teams and individuals across
the organization.
Quote for the day:
"Listening to the inner voice,
trusting the inner voice, is one of the most important lessons of
leadership." -- Warren Bennis
No comments:
Post a Comment