How 6G will work: Terahertz-to-fiber conversion

Upcoming 6G wireless, superseding 5G and arriving possibly by 2030, is envisaged to function at hundreds of gigabits per second. Slowly, the technical advances needed are being made. A hole in the tech development thus far has been at the interface between terahertz spectrum and hard, optical transmission lines. How does one connect terahertz (THz), which is basically through-the-air spectrum found between microwave and infrared, to the transmission lines that will be needed for the longer-distance data sends? The curvature of the Earth, for one thing, limits line of sight, so hard-wiring is necessary for distances. Short distances, too, can be impeded by environmental obstructions: blocking by objects, even rain or fog, becomes more apparent the higher in spectrum one goes, as wavelengths get shorter. ... The fiber-terahertz connection in 6G, though, isn’t the only area that must be addressed over the next few years. Spatial multiplexing also needs to be mastered at terahertz to get the kinds of throughputs desired, experts say. Spatial multiplexing is where individual data signals are beamed out in streams. Every bit of the bandwidth thus gets used and reused continually, introducing bandwidth efficiency.
Ultimate Guide to Become a REAL Programmer
As a beginner, mostly you are a learner in addition to the developer. In programming, your learning will never end. But as a junior, you will have to learn even more. Learning and impostor syndrome are closely related and one of the reason is that learning is a sole journey. People around could guide you but in the end, it is you who has to go through the fire. This sole journey amplifies the negative feelings and developers get demotivated and think of themselves as incompetent. Beware it is impostor syndrome. ... It is very difficult to keep yourself motivated. You may feel motivated by reading about a top performer having impostor syndrome but it will not last. I have created a tool of motivation that you can use it to keep your motivation up on-demand. I created it by documenting my progress. I use my journal to document my progress. Here is the step-by-step guide to documenting your progress. At the end of the quarter and year, I review my past progress with the help of my journal. I always get amazed by looking at the projects I have completed.
Microsoft's October 2 event will be about more than just new Surface devices

There's some speculation as to whether Microsoft also could introduce a new Surface-branded portable speaker at the event. It seems as if this device would be more business-focused and built around Microsoft's Teams group-chat service based on some hints in a recent patent filing. As one of my readers speculated, maybe such a device also could be used with "Teams for Life," an as-yet-unannounced (but expected) version of Teams that Microsoft could offer for families. I'd think if and when Teams for Life becomes available, it could be a cornerstone for Microsoft's expected Microsoft 365 Consumer subscription bundle. The biggest question in the minds of many of us Microsoft watchers is what, if anything, Microsoft will say about its still unofficially acknowledged "Windows Lite" OS, which is expected to be a ChromeOS competitor. Microsoft has been building a dual-screen PC, codenamed "Centaurus," which could be one of a number of different Microsoft and third-party devices to run Lite OS. Microsoft recently showed off advanced renders of Centaurus at an internal meeting, but my contacts say the device is still quite a way from being commercialized.
Organizations And Customers Opting For Passwordless Future: Study

A dangerous side-effect of password forgetfulness is the use of easily guessable (AKA hackable) passwords. A weak password not only puts consumer data at risk—it puts the companies that hold this data at risk, too. Some extra authentication methods may include a notification email sent to the user or administrator. Here are some ways they do this ... CIAM software allows you to connect your app or website to a 3rd party provider that your customer uses. This way, your customers can sign in to your app or website using their existing credentials instead of creating a new password. Ex: Sign In with Apple. Therefore, anyone who uses Apple will never have to remember a password when connecting to integrated 3rd-party apps. In addition, users can hide their emails, allowing for greater privacy and security. A common example of BYOI is social login, where a customer may use Facebook or other social platforms to access a website or app ... Instead of asking people what they know (passwords), many enterprises are using authentication methods based on what people have—their smartphones. The common term for this is SMS-based authentication.
IoT will dominate Bluetooth market in 2024

Both Wi-Fi and Bluetooth will still rely on smartphones for the majority of its business, but in five years ABI reported that smartphones will represent less that 30% of the market. "Bluetooth will continue to grow in other areas, such as speakers, headsets, mobile, and PC accessories, and both technologies will continue to push into other consumer electronics devices such as connected toys and home entertainment. However, IoT is beginning to take an increasingly significant share of the market," said Andrew Zignani, principal analyst for ABI. The study laid out a number of different sectors that will begin to take larger shares of the Bluetooth and Wi-Fi markets as we move into the 2020s. ABI predicts that asset management, and device location tools will grow to become 8.5% of the Bluetooth market by 2024. These kinds of devices are mainly beacons or trackers, which will become more prevalent as factories turn more to robotic equipment. Smartwatches, activity trackers, and smart clothing will also drive sections of the Bluetooth market, with ABI predicting that there will be at least 400 million Bluetooth-enabled wearable devices by 2024.
Secret CSO: Ryan Weeks, Datto

The shortfall of qualified InfoSec candidates is a real problem. If I can work closely with my team and those in supporting functions to expand their potential and grow their capability then that pays dividends for the cybersecurity programme and ultimately keeping data and systems safe from intrusion. ... I find qualified Intrusion Analysts and Experienced Penetration Testers to be difficult roles to fill, taking on average six months to find a suitable fit. I have built relationships with universities that have cybersecurity programmes and find that building a pipeline of talent from universities through mentoring, internships, ... In cybersecurity you can never stop learning. We have to stay aware of the latest trends and attacker tactics. I find podcasts, news articles, on-the-job experience, career development events, and peer groups to be a large source of continuous learning. ... Managing people is ‘real' work. A friend, who knew my propensity for individual contribution, challenged me with this statement and it helped me to focus on growing those around me as much as achieving outcomes independently. It gave me perspective that created balance at a key time in my career.
Top 3 Misconceptions About SD-WAN

While you may find some areas where you can replace MPLS with a less costly service, there’s no guarantee that operational costs will be reduced with SD-WAN, especially if you add additional connections to some or all sites. “We don’t see spend immediately go down with SD-WAN. Rather, it stays the same or maybe increases,” because companies add services, Lawson says. “But it does provide more efficient bandwidth utilization and is a more efficient way to grow your network.” Zeus Kerravala, founder and principal analyst with ZK Research, agrees. “If the business ditches its MPLS and replaces it with broadband, then the transport costs will certainly drop. In most of the implementations I have seen, though, the company keeps the MPLS and buys broadband to augment that network, which results in a net higher cost,” he writes in Network World. You may see reduced capital costs, however, since SD-WAN doesn’t require routers or switches; it’s delivered via an appliance or even as a virtual service.
Researchers invent cryptocurrency wallet that eliminates ‘entire classes’ of vulnerabilities

What makes Notary different is a set of hardware fail-safes designed to mitigate successful cyberattacks. Known as "reset-based switching," the wallet will reset the CPU, memory, and other hardware components when a user switches between one app to another. "The goal of this approach is for applications to be more strongly isolated from one another so that the security of apps in the wallet is not threatened if a single app is hacked or has a vulnerability," MIT says. Reset-based switching is intended to remove the threat of vulnerability classes by changing the infrastructure of a device to act as a multiple computer system. Notary runs management code on one system and applications on another -- and so when task-switching occurs, the management console resets the application computer fully before booting up another app. By using physically separate systems-on-a-chip, this could nullify threats such as Rowhammer. The research team says that due to reset-switching, memory errors -- especially those involving vulnerable memory protection units able to break app isolation, can be avoided. MPUs in themselves are not used, in favor of physically separate domains and resets.
Government Agencies Field More Cybersecurity Maturity Models
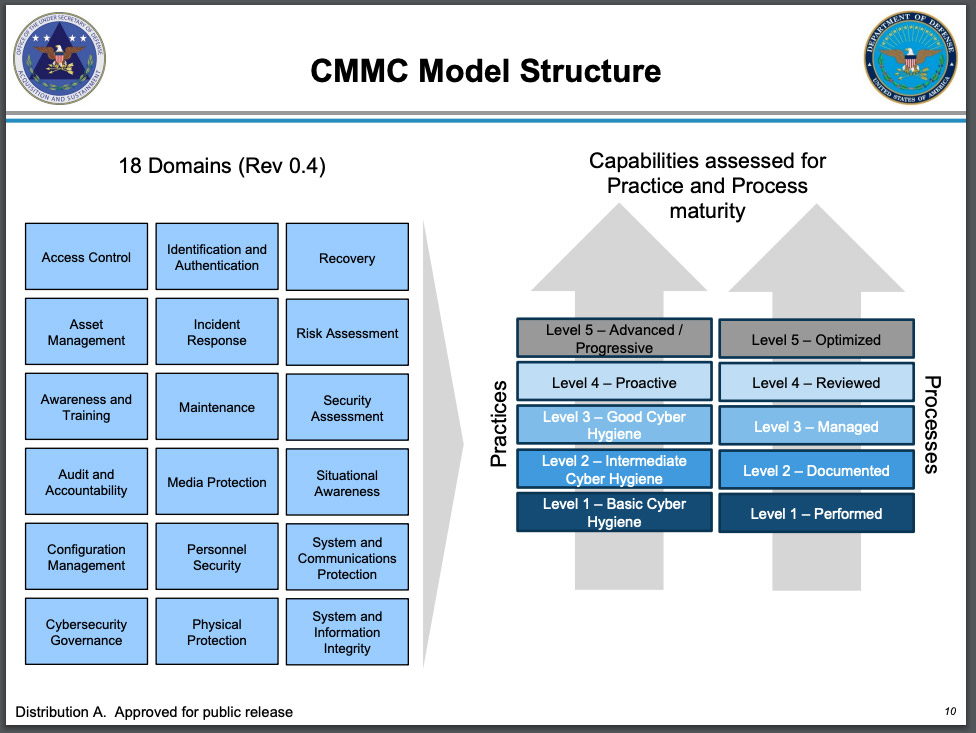
As defined by DOE, "a maturity model is a set of characteristics, attributes, indicators, or patterns that represent capability and progression in a particular discipline," so organizations can identify their maturity level and then next steps for improvement. "Model content typically exemplifies best practices and may incorporate standards or other codes of practice of the discipline." ... Caltagirone at Dragos says the release of C2M2 and upcoming CMMC point to increasing cybersecurity maturity across multiple sectors and the importance of better sector-specific guidance. "Cybersecurity, and cybersecurity in critical infrastructure, is such a new domain that the proliferation of models and frameworks such as C2M2 is expected, and welcomed," he says. "It seems as if new models are created every day, and they are, but that is a sign of progress - that we recognize deficiency and work to improve it. The industry should have as many descriptive and supportive models as possible as none are perfect, but we should strive for few prescriptive models. ... "
Best Practices for Event-Driven Microservice Architecture
Of course, event-driven architectures have drawbacks as well. They are easy to over-engineer by separating concerns that might be simpler when closely coupled; they can require significant upfront investment; and often result in additional complexity in infrastructure, service contracts or schemas, polyglot build systems, and dependency graphs. Perhaps the most significant drawback and the challenge is data and transaction management. Because of their asynchronous nature, event-driven models must carefully handle inconsistent data between services, incompatible versions, watch for duplicate events, and typically do not support ACID transactions, instead of supporting eventual consistency which can be more difficult to track or debug. Even with these drawbacks, an event-driven architecture is usually the better choice for enterprise-level microservice systems. The pros—scalable, loosely coupled, dev-ops friendly design—outweigh the cons.
Quote for the day:
"Trust is the lubrication that makes it possible for organizations to work." -- Warren G. Bennis
No comments:
Post a Comment