The Carbon Cost Of Digital Tech

“The cloud is more efficient, but that doesn’t automatically mean it’s more environmentally friendly,” Adams points out. “A less efficient data centre running on renewables will almost always be a better choice, environmentally speaking, than an efficient one that uses coal.” For the last 10 years, the Green Web Foundation has maintained the world’s largest database of website and digital providers using renewable power, making it easier for companies to find greener options. Becoming a sustainable, environmentally positive business isn’t just about decarbonisation. It’s equally as important, for example, to think about where investment is going. Take Google, a company that has taken significant steps to run data centres more efficiently. Last year, the tech giant was the world’s largest corporate buyer of renewable energy, and reached its goal of sourcing 100 per cent of its energy from renewable sources in 2017. Despite this, Google is far from perfect. “Google is funding climate deniers in the US, and supporting politicians who consistently cripple effective legislation in other sectors, as well as aggressively chasing business in the oil and gas sector,” Adams says.
The Struggles of Innovative People

In his book, Adam Grant takes as an example a whole bunch of examples of social struggles in the USA, including among others the rights of black people and the fight for women's right to vote. He retains a pattern that comes up very often. First, people who would be described as radical and often violent highlight the problem. These are poorly monitored, misunderstood and fail, but not totally. Their message is heard by more moderate people, who want to go through significantly more legal means, and with a non-aggressive message. It is then that the people in power give in to their demands because the subject of the struggle is presented in a non-aggressive way, and heard by all. Unlike violent people. Some will argue that it is because violent people always threaten that governments negotiate with non-violent people. But from there we can learn two things. You have to get the message across while having people in power who fear something. It is the combination of fear + solution that makes people move.
Ransomware: 11 steps you should take to protect against disaster

It's not just criminal gangs that have noticed the power of ransomware: state-backed hacking groups have also used ransomware to create both chaos and profit for their backers. ... A recovery plan that covers all types of tech disaster should be a standard part of business planning, and should include a ransomware response. That's not just the technical response -- cleaning the PCs and reinstalling data from backups -- but also the broader business response that might be needed. Things to consider include how to explain the situation to customers, suppliers and the press. Consider whether regulators need to be notified, or if you should call in police or insurers. Having a document is not enough: you also need to test out the assumptions you have made, because some of them will be wrong. ... First, there's no guarantee that the criminals will hand over the encryption key when you pay up -- they are crooks, after all. If your organisation is seen to be willing to pay, that will probably encourage more attacks, either by the same group or others. There's also the broader impact to consider.
The Driver in the Driverless Car
This book came about from a simple observation. I noticed that even my techie friends in Silicon Valley were feeling overwhelmed by the pace of technological change. I also believe that the risks of letting technology just develop without thinking through societal implications is a massive problem - look at the rise of Facebook and all the problems that came because they refused to consider the privacy implications or the implications of their tools being hijacked for genocide and hate speech. ... Robots are good for three types of tasks: dirty, dangerous and dull jobs. Dirty jobs might be for example, cleaning out oil pipelines. Dangerous are jobs like bomb disposal or drones inspecting communications towers, infrastructure, or roof tops for faults and damage. Dull jobs are things like delivering food in a hospital or dispensing medicine. Curiously, autonomous vehicles are a great use case for robots - driving is both dangerous and dull. It’s also important to capture that a job can be both complex and based on repetition.
Adoption of AI Surveillance Technology Surges
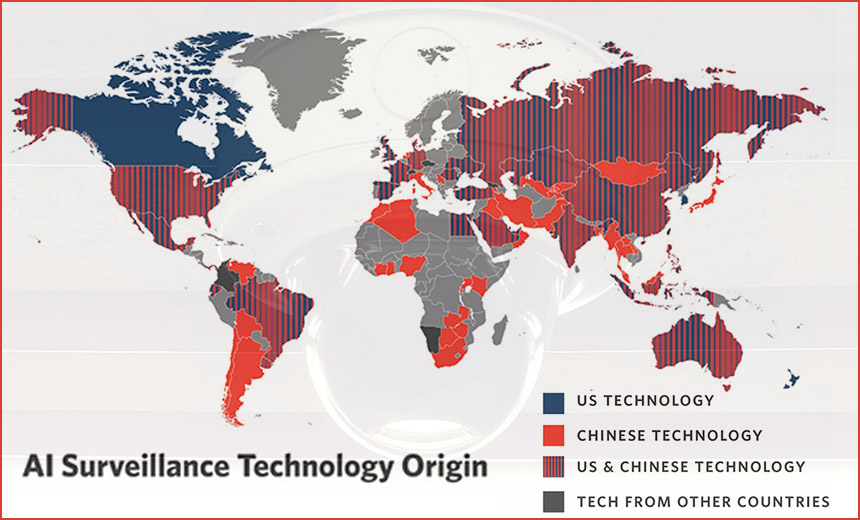
"Sadly I'm not surprised," says Alan Woodward, a computer science professor at the University of Surrey, commenting on the report's finding that AI surveillance technology is being rapidly embraced by governments. "Adoption of something this useful for security is bound to run ahead, and as is so often the case, particularly ahead of the legislation or regulation one might hope for." Technology, of course, is the limiting practical factor when designing more automated surveillance systems. But tool set capabilities and combinations have been rapidly improving. "Several breakthroughs are making new achievements in the field possible: the maturation of machine learning and the onset of deep learning; cloud computing and online data gathering; a new generation of advanced microchips and computer hardware; improved performance of complex algorithms; and market-driven incentives for new uses of AI technology," says Feldstein, who's also a nonresident fellow in Carnegie's Democracy, Conflict, and Governance Program. He formerly served as a deputy assistant secretary in the Democracy, Human Rights, and Labor Bureau at the U.S. Department of State.
How to better integrate IT security and IT strategy

“The human element is the biggest risk facing any IT organization today,” McGibney says. “A successful phishing campaign can easily bring a company to a screeching halt. To provide true defense in depth, IT and security need to work together to implement solutions across the attack surface, whether it be on-[premises] solutions or cloud-based. What the security group implements effects infrastructure and what infrastructure implements effects security. They truly go hand-in-hand.” IT and security teams need to understand what they are both trying to accomplish, and why it’s important to the organization, Wenzler says. “It’s easy to get risk strategies out of alignment with technology goals when the two sides don’t talk to each other,” he says. “While separate functions, they are integral to each other’s success, so without constant communication they’ll remain out of sync.” It’s also important for the two disciplines to build better relationships with each other. Information security people are sometimes seen as roadblocks to projects and hindering workflows, Cardamone says.
How a small business should respond to a hack

Responding to an attack starts long before it occurs. You should – if you haven't already – put in place an action plan for responding to an attack. All staff should know what is expected of them if the worst occurs, and particularly how to respond to customers who might be worried about their personal data being stolen. You should also prioritize the parts of your business that are most at risk during a cyberattack and focus your security measures on them. Many small businesses cannot afford to invest in sophisticated security measures for the whole of their IT infrastructure, but you can protect the systems and databases that contain the most sensitive information. Regular audits of the information you hold will also help you to identify exactly what has been stolen and will also help law enforcement track down the culprits. ... First, it's important that all of your staff know how to identify a hack at the earliest possible opportunity. If you can catch an attack whilst it is still in progress, all the better: this might allow law enforcement to identify the criminal immediately.
Java SE 13 adds performance, security, stability features
Gil Tene, CTO of Azul Systems, said he was skeptical of the sped-up Java release cadence, but the stability of the Java Community Process (JCP) along with the Java reference implementation and the Java Technology Compatibility Kit (TCK) gave him assurance that the speedier cadence would work just fine. Bruno Souza, president of SouJava, a Java user group based in Brazil, concurred. In moving to the six-month cadence, Oracle and the JCP kept its commitment to a fast, open source development model, but also kept the same standards of compatibility and quality, he said. OpenJDK, the open source version of Java SE, is where innovation will occur, Souza said. "And the TCK lets us verify that all these implementations run the same way," he added. Meanwhile, Java tools vendors have begun to take the Java release cadence into account for their products and services. For instance, Mala Gupta, a developer advocate at JetBrains, which produces the popular IDEA IntelliJ Java IDE, said JetBrains has a four-month release cycle that is tuned to keep up with each new release of Java.
Encrypted Smartphone Takedown Outed Canadian Mole

Bill Majcher, a former RCMP officer with extensive experience in conducting undercover operations, tells Global News that Ortis would have had access to almost any type of classified information, which the publication notes "could include the force's blueprints for covert operations worldwide, as well as the identities of undercover officers, police agents working within transnational crime groups, officers from Five Eyes partners used in RCMP probes, and even witnesses relocated to other countries." Lucki says the charges against Ortis have "shaken many people throughout the RCMP," as well as Canada's intelligence partners. "While these allegations, if proven true, are extremely unsettling, Canadians and our law enforcement partners can trust that our priority continues to be the integrity of the investigations and the safety and security of the public we serve," she says. The arrest of Ortis appears to have resulted from authorities taking down a secure smartphone service marketed to criminals.
Important Things You Need To Know About Agile Development

In the agile world, testing becomes a regular part of the process. Small pieces of the project are tested and presented on a regular basis. This gives everyone a better sense of the project’s timeline. In addition, this frequent testing allows developers to catch bugs before they become deeply entrenched in the code. ... Agile development does not mandate particular practices, but a number of standard practices have come into place as a result of the values of the agile model. One common example is paired programming. Here, two developers work together as they code a piece of the project. One programmer does the coding, and the other reviews the code as it is written. Another common agile practice is the daily standup meeting. Here, each team will give a status report to the project manager. Then, new goals are set for the current day. The final practice is working in sprints. Rather than set a long goal, many agile models encourage doing work in short bursts. Many offices use a two-week sprint model, where developers try to handle as many issues or address several user stories in a short period.
Quote for the day:
"Leaders must know where they are going if they expect others to willingly join them on the journey." -- Kouzes & Posner
No comments:
Post a Comment