The Seven Patterns Of AI
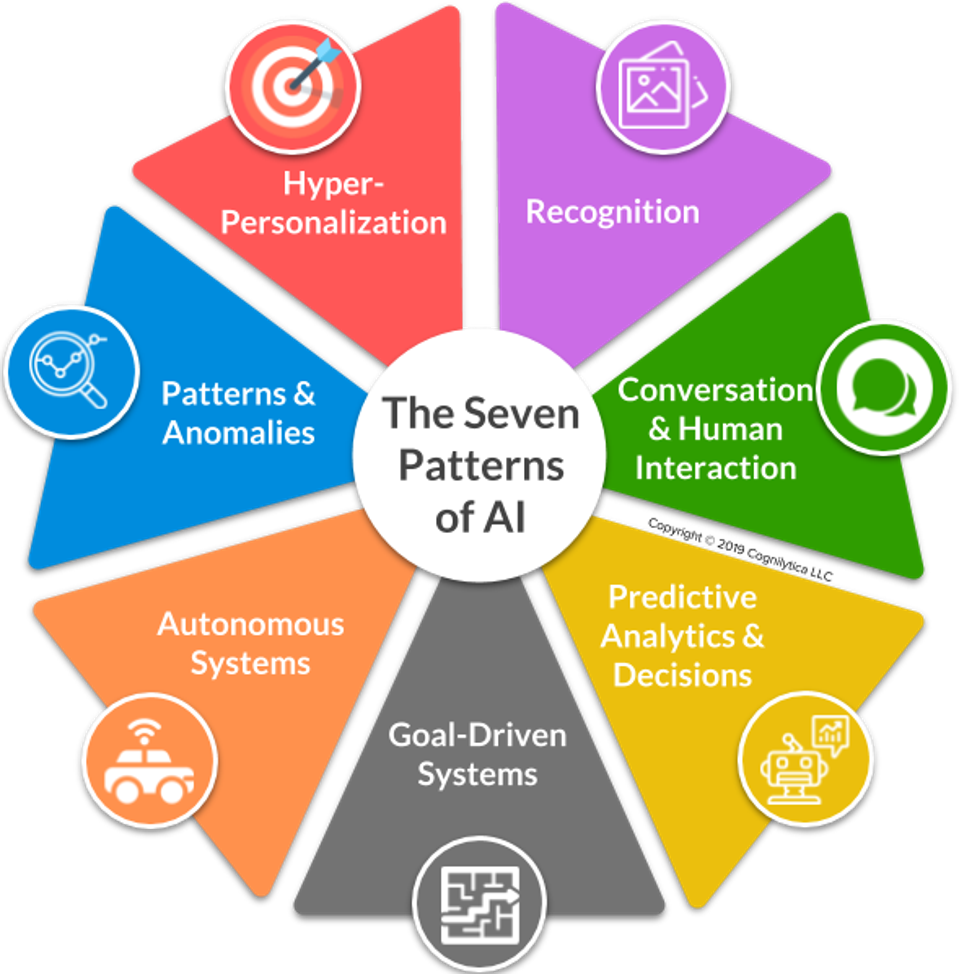
From autonomous vehicles, predictive analytics applications, facial recognition, to chatbots, virtual assistants, cognitive automation, and fraud detection, the use cases for AI are many. However, regardless of the application of AI, there is commonality to all these applications. Those who have implemented hundreds or even thousands of AI projects realize that despite all this diversity in application, AI use cases fall into one or more of seven common patterns. The seven patterns are: hyperpersonalization, autonomous systems, predictive analytics and decision support, conversational/human interactions, patterns and anomalies, recognition systems, and goal-driven systems. Any customized approach to AI is going to require its own programming and pattern, but no matter what combination these trends are used in, they all follow their own pretty standard set of rules. ... While these might seem like discrete patterns that are implemented individually in typical AI projects, in reality, we have seen organizations combine one or more of these seven patterns to realize their goals. By companies thinking of AI projects in terms of these patterns it will help them better approach, plan, and executate AI projects. In fact, emerging methodologies are focusing on the use of these seven patterns as a way to expedite AI project planning.
Aliro aims to make quantum computers usable by traditional programmers

Stages of quantum computing are generally divided into quantum supremacy—the threshold at which quantum computers are theorized to be capable of solving problems, which traditional computers would not (practically) be able to solve—is likely decades away. While quantum volume, a metric that "enables the comparison of hardware with widely different performance characteristics and quantifies the complexity of algorithms that can be run," according to IBM, has gained acceptance from NIST and analyst firm Gartner as a useful metric. Aliro proposes the idea of "quantum value," as the point at which organizations using high performance computing today can achieve results from using quantum computers to accelerate their workload. "We're dealing with enterprises that want to get business value from these machines…. "We're not ready for many levels of abstraction above the quantum hardware, but we're ready for a little bit. When you get down to the equivalent of the machine language, these things are very, very different, and it's not just what kind of qubits they are. It's noise characteristics, it's connectivity," Ricotta said. "Riggeti and IBM Q machines both use superconducting Josephson junctions around the same number—approximately, the same order of magnitude of qubits—but they are connected in different ways ..."
New hacking group targets IT companies in first stage of supply chain attacks

In two of the attacks, researchers found that hundreds of computers were compromised with malware, indicating that the attackers were simply infecting all the machines they could throughout the organisations in order to find key targets. The most recently recorded activity from Tortoiseshell was in July 2019, with attacks by the group identified by a unique custom payload: Backdoor.Syskit. This malware is built in both Delphi and .NET programming languages and secretly opens an initial backdoor onto compromised computers, allowing attackers to collect information including the IP address, the operating system version and the computer name. Syskit can also download and execute additional tools and commands, and Tortoiseshell attacks also deploy several publicly available tools as information stealers to gather data on user activity. While it remains uncertain how the malware is delivered, researchers suggest that it could potentially be distributed via a compromised web server, because in one instance the first indication of malware on the network was a compromised web shell – something that can provide an easy way into a targeted network.
How Ransomware Criminals Turn Friends into Enemies
As someone whose job it is to learn as much as possible about the online criminal ecosystem, I often spot trends before they make mainstream headlines. This type of attack was high on my list of attacks likely to increase. Supply chain attacks aren't new. They've been increasing in frequency, however, and gaining more attention. While there are many types of supply chain attacks, this particular type — compromising a service provider to gain access to its customers — is becoming more popular among skilled ransomware crews. ... Managing IT can be hard, especially for small and midsize businesses lacking the necessary resources. It probably seemed like a great idea for these small dental practices to outsource IT to Digital Dental Record. They're not alone. The managed services industry is growing extremely fast with businesses struggling to manage the technology required to run a modern establishment. With attacks on MSPs on the rise, MSPs need to step up their security game, regardless of the kind of specialized services they provide.
AI in cyber security: a necessity or too early to introduce?

Dr Leila Powell, lead security data scientist from Panaseer, agrees that “the key challenge for most security teams right now is getting hold of the data they need in order to get even a basic level of visibility on the fundamentals of how their security program is performing and how they measure up against regulatory frameworks like GDPR. This is not a trivial task! “With access to security relevant data controlled by multiple stakeholders from IT to MSSPs and tool vendors there can be a lot of red tape on top of the technical challenges of bringing together multiple siloed data sources. Then there’s data cleaning, standardisation, correlation and understanding — which often require a detailed knowledge of the idiosyncrasies of all the unique datasets. “As it stands, once all that work has gone in to data collection, the benefits of applying simple statistics cannot be underestimated. These provide plenty of new insights for teams to work through — most won’t even have the resources to deal with all of these, let alone additional alerting from ML solutions.
2019 Digital operations study for energy
Looking ahead to the next five years, the picture improves somewhat and offers more hope for the utilities sector. For instance, of the EMEA utilities surveyed by Strategy&, 5 percent said they had already implemented AI applications and another 9 percent sa they had piloted such programs. That compares with 20 percent and 6 percent, respectively, for chemicals companies. But through 2024, including planned technologies, AI adoption in the utilities sector may increase by another 15 percent, according to the survey, and that would be on par with chemicals companies and just below oil and gas AI implementation. ... Many utilities make the mistake of trying to implement too many ambitious digital strategies at the same time and end up spreading their financial and staff resources, as well as their capabilities, too thin. A better approach is to define the three to five critical digitization efforts that are strategically essential to defending and expanding competitive advantage among startups and established power companies.
Microsoft brings IBM iron to Azure for on-premises migrations

Under the deal, Microsoft will deploy Power S922 servers from IBM and deploy them in an undeclared Azure region. These machines can run the PowerVM hypervisor, which supports legacy IBM operating systems, as well as Linux. "Migrating to the cloud by first replacing older technologies is time consuming and risky," said Brad Schick, CEO of Skytap, in a statement. "Skytap’s goal has always been to provide businesses with a path to get these systems into the cloud with little change and less risk. Working with Microsoft, we will bring Skytap’s native support for a wide range of legacy applications to Microsoft Azure, including those dependent on IBM i, AIX, and Linux on Power. This will give businesses the ability to extend the life of traditional systems and increase their value by modernizing with Azure services." As Power-based applications are modernized, Skytap will then bring in DevOps CI/CD toolchains to accelerate software delivery. After moving to Skytap on Azure, customers will be able to integrate Azure DevOps, in addition to CI/CD toolchains for Power, such as Eradani and UrbanCode.
Prepare for cloud security and shared responsibility

IT infrastructure teams typically control the platform from the ground up and through the OS layer. Admins work with security teams to ensure platforms are hardened and adhere to compliance needs. After the platform is built, infrastructure and security teams turn it over to the dev or application owners for final installations and deployments. Application owners still work with an infrastructure team to ensure security and compliance measures are maintained through the deployment process. Ideally, the platform gets a final verification from the security team. The same parties will still be involved and maintain that level of ownership and responsibility even if an organization uses automation. But this process gets upended when a cloud provider gets involved. AWS manages the hypervisor, hardware and, in some cases, the OS. This means the deployment process starts in the middle of the traditional application lifecycle rather than at the beginning. Admins have to find a way to contribute in an ecosystem where the infrastructure is run by another party.
Digital dexterity: What it is, why your organization needs it, and how CIOs can lead the charge

If you're not sure what digital dexterity is, you aren't alone. Craig Roth, Gartner Research vice president, explained it as "the ability and ambition to use technology for better business outcomes." That definition can still seem a bit fuzzy if you aren't sure where ability and ambition come in to the successful use of tech in business, but digging down just a bit helps make the whole thing more understandable. Helen Poitevin, vice president and analyst at Gartner, expands the definition of digital dexterity by adding that it's less about tech skills and more about "a specific set of mindsets, beliefs and behaviors." ... So, where does the CIO fit into all of this? They're basically the cornerstone of the entire concept, said Daniel Sanchez Reina, senior director and analyst at Gartner. "The CIO will play a key role in supporting desired behaviors and changing the processes, procedures, policies and management practices that shape how work gets done to encourage desired behaviors." It can be tough to transform an entire organization from one that resists, or at the very least grudgingly accepts, new technology. CIOs have a tough road ahead of them, but that doesn't mean it's impossible.
New ransomware strain uses ‘overkill’ encryption to lock down your PC

FortiGuard Labs says that 2048 and 4096 strings are generally more than adequate to encrypt and secure messages, and so the use of an 8192 size is "overkill and inefficient for its purpose." "Using the longer key size adds a large overhead due to significantly longer key generation and encryption times [...] RSA-8192 can only encrypt 1024 bytes at a time, even less if we consider the reserved size for padding," the researchers note. "Since the configuration's size will surely be more than that due to the fact that it contains the encoded private key, the malware cuts the information into chunks of 1000 (0x3e8) bytes and performs multiple operations of the RSA-8192 until the entire information is encrypted." The heavy use of encryption means that it is "not practically possible" to decrypt a compromised system, according to the cybersecurity firm. This is unfortunate, as decryption programs offered by cybersecurity firms can sometimes be the only way to recover files lost to ransomware infections without paying up.
Quote for the day:
"Don't measure yourself by what you have accomplished. But by what you should have accomplished with your ability." -- John Wooden
No comments:
Post a Comment