A CISO's Guide to Avoiding Jail After a Breach
_Michael_Burrell-Alamy.jpg?width=850&auto=webp&quality=95&format=jpg&disable=upscale)
The key to avoiding trouble as a security leader, Nall says, is awareness of
three things: how government investigations work, how the government interacts
with companies during the process, and the incentives companies have to resolve
their cases in one way or another. When push comes to shove, for example,
companies will be pressured to name and shame individuals. In his proceedings,
Sullivan's legal team painted a picture of a company (Uber) trying to rebrand
itself, and holding him up as a lamb to the slaughter. "It's very
unfortunate because the consequences are faced by one individual, or a few
individuals, although the ability to make sure that [an incident] doesn't happen
is a community-based effort within organizations," says ArmorCode's Karthik
Swarnam, formerly chief information security officer (CISO) of Kroger, DIRECTV,
and TransUnion. To avoid being singled out (and because it's good security
practice), CISOs should focus on building clear and robust lines of
communication that bring other board members into the cybersecurity
decision-making process.
How Pearson’s CIO manages technical debt
Keen to address this, Wells and the Pearson technology working group, which
includes tech leadership from across the brand’s different organizations, came
up with 12 key attributes, including security and maintainability, to rate their
technology assets in a consistent way. These tech debt audits provided a clearer
picture of where their biggest risks were, which, in turn, allowed them to
prioritize what needs to be addressed first. “We developed an algorithm to
measure our different applications based on these 12 categories so we can
eliminate technical debt via a more strategic and standardized approach,” she
says, noting that the goal was to do away with any guesswork and make decisions
based on opportunities and potential revenue risks. ... As part of the process,
she and her team needed to get the various leaders from across the business on
board by making sure they understood that technical debt isn’t just a technology
problem. “We really had to communicate that this is a priority, but we couldn’t
do so by only talking to them about technology,” she says.
Strategic alignment in the age of AI: The 7 foundations of competitive success

The strategy must align with the capabilities of the organization and the
competitive reality of the environment. Such an alignment has never been
more important, as artificial intelligence (AI) and other changes disrupt
industries and sectors. Before rushing to adopt the latest AI tool, whether
it is deep learning or large language models, organizations must assess
whether the new tech is strategically aligned. ... Aligning people with the
desired strategic position and vision for the organization is critical. In
high-performing organizations, employees and members understand their
strategic mission and vision and are dedicated to achieving it. They become
acolytes of their leaders and passionate advocates for their organizations.
They see how their role contributes to the strategy of the organization and
execute with a sense of purpose and teamwork. How many of your employees can
articulate how your AI efforts advance your strategy? ... In truth,
strategic alignment may be rare. If you are fortunate, you can recall a
situation where alignment occurred, allowing you and your organization to
achieve incredible heights.
The AI Revolution Will Not Be Monopolized
Open source in AI and machine learning is not just about software, it's
about the synergy of code and data. The growing ecosystem of open-source
models encompasses everything from code to data and weights, making powerful
tools widely accessible. ... The term "large language models" (LLMs) is
often used broadly and imprecisely, muddying discussions about their
capabilities and applications. The distinction between encoder models and
large generative models is therefore very important. Encoder models involve
task-specific networks that predict structured data, while large generative
models rely on prompts to produce free-form text, necessitating additional
logic to extract actionable insights. ... Companies like OpenAI might
dominate the market for user-facing products but not necessarily the AI and
software components behind them. While user data is advantageous for
improving human-facing products, it is less critical for enhancing the
foundational machine-facing tasks. Gaining general knowledge doesn't require
specific data, which is at the core of the innovation behind large
generative models.
CISA Warns Chemical Facilities of Data Theft After Hacker Breached CSAT Security Tool via Ivanti

CISA says that all information in the CSAT tool was encrypted using AES 256
algorithm, and the keys were also inaccessible “from the type of access the
threat actor had to the system.” The agency also found “no evidence of
credentials being stolen.” However, impacted organizations should assume
data theft “out of abundance of caution” and assume that “that this
information could have been inappropriately accessed,” the agency said. The
agency also stated that even without data theft, the intrusion “met the
threshold of a major incident under the Federal Information Security
Modernization Act (FISMA),” given the number of individuals and chemical
facilities impacted. Subsequently, CISA directed impacted chemical
facilities to maintain cyber and physical security measures to prevent
potential attacks as a result of the cyber incident. Similarly, CISA
encourages individuals who had CSAT accounts to reset their passwords for
all online accounts that share the same password to prevent future password
spraying attacks.
Autonomous Vehicles Can Make All Cars More Efficient

To illustrate how the technology works, the team installed a traffic signal
along the demonstration pathway. Gankov says an actual traffic-light timer
from a traffic-signal cabinet was connected to a TV screen, providing a
visual for attendees. A dedicated short range communications (DRSC) radio
was also attached, broadcasting the signal’s phase and timing information to
the vehicle. This setup enabled the vehicle to anticipate the traffic
light’s actions far more accurately than a human driver could. ... These
autonomous driving strategies can lead to significant energy savings,
benefiting not just the autonomous vehicles themselves, but also the entire
traffic ecosystem. “In a regular traffic situation, autonomous vehicles
operating in ecomode influence the driving behavior of all the cars behind
them,” says Gankov. “The result is that even vehicles with Level 0 autonomy
use fuel more sparingly.” ... Employing techniques like efficient highway
merging were key strategies in their approach to making the most of each
tank of fuel or battery charge.
SyncBack is the best free backup software on Windows and everyone should use it
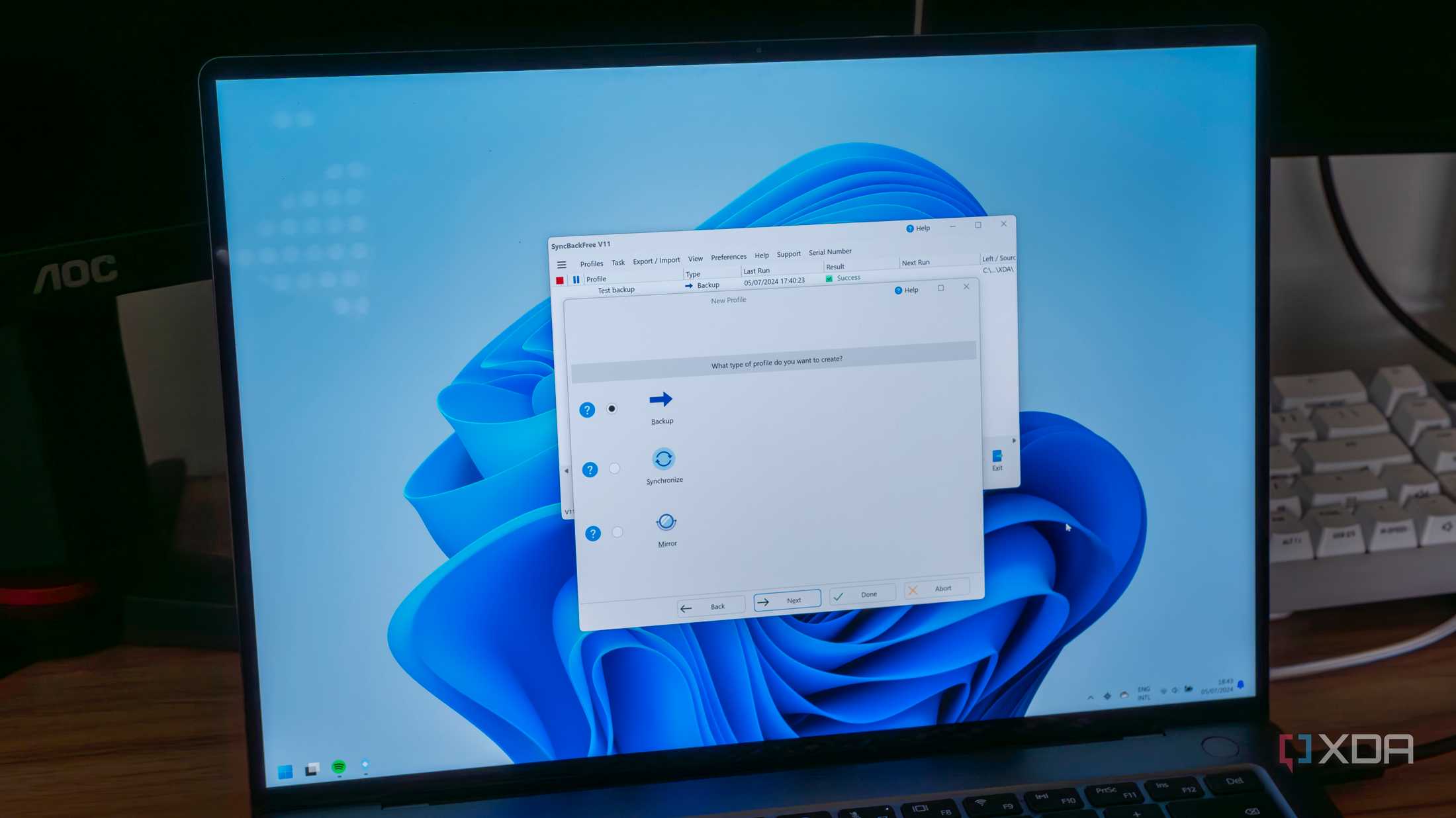
On top of changing the type of sync or backup you want to perform, SyncBack
also has a ton of configuration options for almost everything about how it
works. By default, each profile you create is a manual backup, so whenever
you want to backup your files, you just run the profile. Even then, if you
want to run it on demand, you can create a hotkey to quickly run a specific
profile and run it at any time. But if you're a "set it and forget it" type
of person, then you can also automate the backups. SyncBack uses the Task
Scheduler in Windows to allow you to create a scheduled backup with whatever
frequency you prefer. ... Since each profile is only meant to sync one
folder, if you want to sync files in completely different locations, you'll
need separate profiles, but you can create group profiles so that all the
profiles within are run at the same time, rather than sequentially. You can
also enable things like compression for files copied, decrypt files when
they're copied, change whether you want files to be copied when syncing two
folders or if the mismatched file should be deleted, and even enable a
rudimentary form of ransomware detection.
From Scalability to Speed: Generative AI has Put Testing on Steroids
In the past, testing quality has been a big concern, necessitating early
integration of QA into the development life cycle. Now, with GenAI, the
focus has advanced beyond simply assurance to actively engineering quality.
The key distinction lies in the approach — classic AI involves human
intervention and manual processes, while GenAI automates and innovates
testing methodologies. Consider dealing with requirement quality early in
the software development life cycle. Using classic AI, a business analyst
might define requirements to cover various interpretations, which may lead
to certain ambiguity and potential failures. ... using GenAI is not about
replacing the human workforce, but enhancing our capabilities. The shortage
of senior automation testers results in a loss in business revenue. However,
with GenAI, junior engineers can now harness the power of gen AI-enabled
automation, performing tasks with the built-in knowledge of a seasoned
architect. Gen AI’s prowess is not arbitrary; it has learned from
billions of data points. By combining traditional knowledge with AI
capabilities, new solutions bring scalability and speed to testing.
How organisations can thrive with resilience and empathy

While many organisations embrace the value of empathy, they often fall short
in delivering it with genuine sincerity. Superficial expressions of empathy
without meaningful actions, including consistent recognition, lead to
employee dissatisfaction and high turnover rates. However, demonstrating
sincere empathy and providing meaningful recognition can be challenging.
Leaders sometimes face criticism for being "too considerate," particularly
when their decisions appear to benefit employees during setbacks
disproportionately. This dynamic can result in empathy fatigue, where the
constant demand for empathetic responses and recognition strains HR
professionals and leaders. ... Change can only occur when an organisation
adopts the principles of nimble resilience and empathy, using them to shape
policies, programs, and workplace culture. This approach encourages
employees to build relationships, find new solutions, work collaboratively
across disciplines, and embrace a forward-thinking perspective. As a result,
trust in leaders and team members increases, along with connections to the
organisation and its purpose.
Mind the Gap: The Product in Data Product Is Reliability
The data product concept has been fleshed out in recent years with
definitions, reference architectures, and platforms. They consist of …
actually, let’s not worry about what data products consist of. At least, not
right now. That’s not the important part. Instead, let’s start where we
should always start: the consumer. ... Your assurance that its contents are
always correct is the most significant distinguishing characteristic of a
data product. You provide the ongoing validation, certification, and
research so that your users don’t have to. You ensure that the data product
is kept current with new arriving data. You continuously monitor its data
quality. In addition to content, you must also be concerned with semantics.
Changes in the business as implemented in the source systems and propagated
through the data may necessitate changes to the data product. ... Technology
can facilitate, but technology alone is not remotely sufficient. I’ve seen
the data product label slapped on data marts, summary tables, and even raw
data with none of the curation or monitoring.
Quote for the day:
"The only limit to our realization
of tomorrow will be our doubts of today." --
Frank D Roosevelt
No comments:
Post a Comment