How to eliminate ransomware risk, not just manage it
 There are a multitude of solutions available, all of which are designed to
reduce risk and protect specific areas of the network. However, there is one
method that is rising in popularity and has proven to be highly effective. Zero
Trust approaches to security are being applied by organisations on a daily
basis, developed on the grounds that trust should never be given out
superfluously – transitioning from “Trust but Verify” to “Verify, then Trust”.
Forrester recently announced that Zero Trust can reduce an organisation’s risk
exposure by 37% or more. This model eliminates automatic access for any asset,
whether internal or external. It instead assumes that the context of any action
must be validated before it can be allowed to proceed. Another technique that
has emerged as being one of the best for protecting businesses from ransomware
attacks, and that is closely aligned to the Zero Trust model, is
micro-segmentation. Micro-segmentation restricts adversary lateral movement
through the network and reduces a company’s attack surface. A strong security
perimeter, whilst important, is no longer enough to protect business IT networks
from ransomware threats – since it just takes one breach of the perimeter to
compromise the network.
There are a multitude of solutions available, all of which are designed to
reduce risk and protect specific areas of the network. However, there is one
method that is rising in popularity and has proven to be highly effective. Zero
Trust approaches to security are being applied by organisations on a daily
basis, developed on the grounds that trust should never be given out
superfluously – transitioning from “Trust but Verify” to “Verify, then Trust”.
Forrester recently announced that Zero Trust can reduce an organisation’s risk
exposure by 37% or more. This model eliminates automatic access for any asset,
whether internal or external. It instead assumes that the context of any action
must be validated before it can be allowed to proceed. Another technique that
has emerged as being one of the best for protecting businesses from ransomware
attacks, and that is closely aligned to the Zero Trust model, is
micro-segmentation. Micro-segmentation restricts adversary lateral movement
through the network and reduces a company’s attack surface. A strong security
perimeter, whilst important, is no longer enough to protect business IT networks
from ransomware threats – since it just takes one breach of the perimeter to
compromise the network.How to conquer synthetic identity fraud
 The arrival of our truly physical-digital existence has forced identity
protection to the forefront of our minds and amplified the need to understand
how, through technology, our identities and behavior can be used to equalize and
authenticate our access to all of life’s experiences. Second, there’s been an
exceptional rise in all types fraud, including synthetic. Tackling this will
require an intelligent, coordinated defense against cybercriminals employing new
and more sophisticated techniques. Not unlike a police database that tracks
criminals in different states, there’s a need for platforms where companies can
anonymously share data signatures about bad actors with one another so that
fraudulent activity becomes much easier to detect. According to the Aite Group,
72% of financial services firms surveyed believe synthetic identity fraud is a
much more pressing issue than identity theft, and the majority plan to make
substantive changes in the next two years. With collaboration driving that
change, we have seen some cases of increasing synthetic fraud detection by more
than 100% and the ability to catch overall forged documents by 8% in certain
platforms.
The arrival of our truly physical-digital existence has forced identity
protection to the forefront of our minds and amplified the need to understand
how, through technology, our identities and behavior can be used to equalize and
authenticate our access to all of life’s experiences. Second, there’s been an
exceptional rise in all types fraud, including synthetic. Tackling this will
require an intelligent, coordinated defense against cybercriminals employing new
and more sophisticated techniques. Not unlike a police database that tracks
criminals in different states, there’s a need for platforms where companies can
anonymously share data signatures about bad actors with one another so that
fraudulent activity becomes much easier to detect. According to the Aite Group,
72% of financial services firms surveyed believe synthetic identity fraud is a
much more pressing issue than identity theft, and the majority plan to make
substantive changes in the next two years. With collaboration driving that
change, we have seen some cases of increasing synthetic fraud detection by more
than 100% and the ability to catch overall forged documents by 8% in certain
platforms.A Look at GitOps for the Modern Enterprise
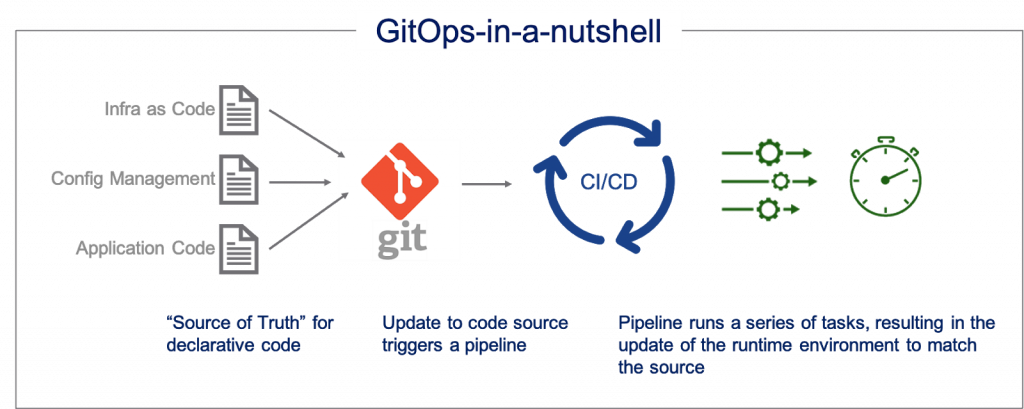 In the GitOps workflow, the system’s desired configuration is maintained in a
source file stored in the git repository with the code itself. The engineer will
make changes to the configuration files representing the desired state instead
of making changes directly to the system via CLI. Reviewing and approving of
such changes can be done through standard processes such as — pull requests,
code reviews, and merges to the master branch. When the changes are approved and
later merged to the master branch, an operator software process is accountable
for switching the system’s current state to the desired state based on the
configuration stored in the newly updated source file. In a typical GitOps
implementation, manual changes are not allowed, and all changes to the
configuration should be done to files put in Git. In a severe case, authority to
change the system is given just to the operator software process. In a GitOps
model, the infrastructure and operations engineers’ role changes from
implementing the infrastructure modifications and application deployments to
developing and supporting the automation of GitOps and assisting teams in
reviewing and approving changes via Git.
In the GitOps workflow, the system’s desired configuration is maintained in a
source file stored in the git repository with the code itself. The engineer will
make changes to the configuration files representing the desired state instead
of making changes directly to the system via CLI. Reviewing and approving of
such changes can be done through standard processes such as — pull requests,
code reviews, and merges to the master branch. When the changes are approved and
later merged to the master branch, an operator software process is accountable
for switching the system’s current state to the desired state based on the
configuration stored in the newly updated source file. In a typical GitOps
implementation, manual changes are not allowed, and all changes to the
configuration should be done to files put in Git. In a severe case, authority to
change the system is given just to the operator software process. In a GitOps
model, the infrastructure and operations engineers’ role changes from
implementing the infrastructure modifications and application deployments to
developing and supporting the automation of GitOps and assisting teams in
reviewing and approving changes via Git.
Preventing Transformational Burnout
Participation can be viewed as a strain—it’s a tool that comes in different sizes and models and it is useful. Still, when individuals are forced to participate in anything that doesn’t resonate with their inner motivation, a leader is the one pulling the trigger of burnout. Note that passion is often thought to serve as a band-aid to the individual burnout when there is the perception that, “I care so much I must put all my efforts in the matter.” In situations where management doesn’t wish to share decision-making control with others, where employees or other stakeholders are passive or apathetic (or suffering from individual burnout), or in organizational cultures that take comfort in bureaucracy, pushing participatory efforts may be unwise. Luckily, agile stems from participation and self-organization. As you plan for employee participation in your transformation efforts, it’s important to have realistic expectations. Not all “potential associates” desire to participate and those that do may not yet have the skills to do so productively. As Jean Neumann found in her research on participation in the manufacturing industry, various factors can lead individuals to rationally choose to “not” participate. Neumann further notes, as have others, that participation requires courage.How AutoML helps to create composite AI?
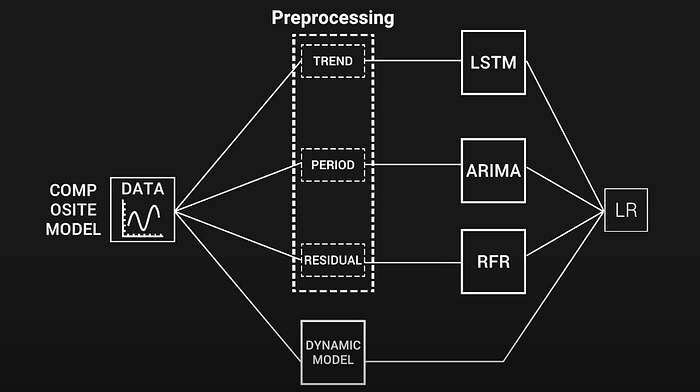 The most straightforward method for solving the optimization task is a random
search for the appropriate block combinations. But a better choice is
meta-heuristic optimization algorithms: swarm and evolutionary (genetic)
algorithms. But in the case of evolutionary algorithms, one should keep in mind
that they should have specially designed crossover, mutation, and selection
operators. Such special operators are important for processing the individuals
described by a DAG, they also give a possibility to take multiple objective
functions into account and include additional procedures to create stable
pipelines and avoid overcomplication. The crossover operators can be implemented
using subtree crossover schemes. In this case, two parent individuals are chosen
and exchange random parts of their graphs. But this is not the only possible way
of implementation, there may be more semantically complex variants (e.g.,
one-point crossover). Implementation of the mutation operators may include
random change of a model (or computational block) in a random node of the graph,
removal of a random node, or random addition of a subtree.
The most straightforward method for solving the optimization task is a random
search for the appropriate block combinations. But a better choice is
meta-heuristic optimization algorithms: swarm and evolutionary (genetic)
algorithms. But in the case of evolutionary algorithms, one should keep in mind
that they should have specially designed crossover, mutation, and selection
operators. Such special operators are important for processing the individuals
described by a DAG, they also give a possibility to take multiple objective
functions into account and include additional procedures to create stable
pipelines and avoid overcomplication. The crossover operators can be implemented
using subtree crossover schemes. In this case, two parent individuals are chosen
and exchange random parts of their graphs. But this is not the only possible way
of implementation, there may be more semantically complex variants (e.g.,
one-point crossover). Implementation of the mutation operators may include
random change of a model (or computational block) in a random node of the graph,
removal of a random node, or random addition of a subtree.AI is driving computing to the edge
Companies are adopting edge computing strategies because the cost of sending their ever-increasing piles of data to the cloud — and keeping it there — has become too expensive. Moreover, the time it takes to move data to the cloud, analyze it, and then send an insight back to the original device is too long for many jobs. For example, if a sensor on a factory machine senses an anomaly, the machine’s operator wants to know right away so she can stop the machine (or have a controller stop the machine). Round-trip data transfer to the cloud takes too long. That is why many of the top cloud workloads seen in the slide above involve machine learning or analysis at the edge. Control logic for factories and sensor fusion needs to happen quickly for it to be valuable, whereas data analytics and video processing can generate so much data that sending it and working on that data in the cloud can be expensive. Latency matters in both of those use cases as well. But a couple of other workloads on the slide indicate where the next big challenge in computing will come from. Two of the workloads listed on the slide involve data exchanges between multiple nodes.Data-Wiping Attacks Hit Outdated Western Digital Devices
 Storage device manufacturer Western Digital warns that two of its
network-attached storage devices - the WD My Book Live and WD My Book Live Duo -
are vulnerable to being remotely wiped by attackers and now urges users to
immediately disconnect them from the internet. ... The underlying flaw in the
newly targeted WD devices is designated CVE-2018-18472 and was first publicly
disclosed in June 2019. "Western Digital WD My Book Live (all versions) has a
root remote command execution bug via shell metacharacters in the
/api/1.0/rest/language_configuration language parameter. It can be triggered by
anyone who knows the IP address of the affected device," the U.S. National
Vulnerability Database noted at the time. Now, it says, the vulnerability is
being reviewed in light of the new attacks. "We are reviewing log files which we
have received from affected customers to further characterize the attack and the
mechanism of access," Western Digital says. "The log files we have reviewed show
that the attackers directly connected to the affected My Book Live devices from
a variety of IP addresses in different countries.
Storage device manufacturer Western Digital warns that two of its
network-attached storage devices - the WD My Book Live and WD My Book Live Duo -
are vulnerable to being remotely wiped by attackers and now urges users to
immediately disconnect them from the internet. ... The underlying flaw in the
newly targeted WD devices is designated CVE-2018-18472 and was first publicly
disclosed in June 2019. "Western Digital WD My Book Live (all versions) has a
root remote command execution bug via shell metacharacters in the
/api/1.0/rest/language_configuration language parameter. It can be triggered by
anyone who knows the IP address of the affected device," the U.S. National
Vulnerability Database noted at the time. Now, it says, the vulnerability is
being reviewed in light of the new attacks. "We are reviewing log files which we
have received from affected customers to further characterize the attack and the
mechanism of access," Western Digital says. "The log files we have reviewed show
that the attackers directly connected to the affected My Book Live devices from
a variety of IP addresses in different countries. IoT For 5G Could Be Next Opportunity
 On the consumer front, a technology currently being planned for inclusion in the
forthcoming 3GPP Release 17 document called NR Light (or Lite), looks very
promising. Essentially functioning as a more robust, 5G network-tied replacement
for Bluetooth, NR Light is designed to enable the low latency, high security,
and cloud-powered applications of a cellular connection, without the high-power
requirements for a full-blown 5G modem. Practically speaking, this means we
could see things like AR headsets, that are tethered to a 5G connected
smartphone, use NR Light for their cloud connectivity, while being much more
power-friendly and battery efficient. Look for more on NR Light in these and
other applications that require very low power in 2022. At the opposite end of
the spectrum, some carriers are starting the process of “refarming” the radio
spectrum they’re currently using to deliver 2G and 3G traffic. In other words,
they’re going to shut those networks down in order to reuse those frequencies to
deliver more 5G service. The problem is, much of the existing IoT applications
are using those older networks, because they’re very well-suited to the lower
data rates used by most IoT devices.
On the consumer front, a technology currently being planned for inclusion in the
forthcoming 3GPP Release 17 document called NR Light (or Lite), looks very
promising. Essentially functioning as a more robust, 5G network-tied replacement
for Bluetooth, NR Light is designed to enable the low latency, high security,
and cloud-powered applications of a cellular connection, without the high-power
requirements for a full-blown 5G modem. Practically speaking, this means we
could see things like AR headsets, that are tethered to a 5G connected
smartphone, use NR Light for their cloud connectivity, while being much more
power-friendly and battery efficient. Look for more on NR Light in these and
other applications that require very low power in 2022. At the opposite end of
the spectrum, some carriers are starting the process of “refarming” the radio
spectrum they’re currently using to deliver 2G and 3G traffic. In other words,
they’re going to shut those networks down in order to reuse those frequencies to
deliver more 5G service. The problem is, much of the existing IoT applications
are using those older networks, because they’re very well-suited to the lower
data rates used by most IoT devices.Security and automation are top priorities for IT professionals
 Organizations across the globe have experienced crippling cyberattacks over the
past year that have significantly impacted the global supply chain. Due to the
growing number of threats, 61% of respondents said that improving security
measures continues to be the dominant priority. Cybersecurity systems topped the
list of what IT professionals plan to invest in for 2022, with 53% of
respondents planning to budget for email security tools such as phishing
prevention, and 33% of respondents investing in ransomware protection. Cloud
technologies were also top of mind this year, with 54% saying their IaaS cloud
spending will increase and 36% anticipating growth in spending on SaaS
applications. Cloud migration was also a high priority for respondents in 2021,
which accounted for migrations across PaaS, IaaS and SaaS software. IT
professionals also want to increase their productivity through automation, which
ranked second in top technologies for investment. Almost half of respondents
stated that they will allocate funds for this in 2021.
Organizations across the globe have experienced crippling cyberattacks over the
past year that have significantly impacted the global supply chain. Due to the
growing number of threats, 61% of respondents said that improving security
measures continues to be the dominant priority. Cybersecurity systems topped the
list of what IT professionals plan to invest in for 2022, with 53% of
respondents planning to budget for email security tools such as phishing
prevention, and 33% of respondents investing in ransomware protection. Cloud
technologies were also top of mind this year, with 54% saying their IaaS cloud
spending will increase and 36% anticipating growth in spending on SaaS
applications. Cloud migration was also a high priority for respondents in 2021,
which accounted for migrations across PaaS, IaaS and SaaS software. IT
professionals also want to increase their productivity through automation, which
ranked second in top technologies for investment. Almost half of respondents
stated that they will allocate funds for this in 2021.Making fungible tokens and NFTs safer to use for enterprises
One of the weaknesses of current token exchange systems is the lack of privacy protection they feature beyond a very basic pseudonymization. In Bitcoin, for example, transactions are pseudonymous and reveal the Bitcoin value exchanged. That makes them linkable and traceable, presenting threats that are inadmissible in other settings such as enterprise networks, in a supply chain or in finance. While some newer cryptocurrencies offer a higher degree of privacy, entirely concealing the actual asset exchanged and transaction participants, they retain the permissionless character of Bitcoin and others, which presents challenges on the regulatory compliance side. For enterprise blockchains, a permissioned setting is required, in which the identity of participants issuing and exchanging tokens is concealed, yet non-repudiatable, and transaction participants can be securely identified upon properly authorized requests. A big conundrum in permissioned blockchains exists in accommodating the use of token payment systems while at the same time preserving the privacy of the parties involved and still allowing for auditing functionalities.Quote for the day:
"The quality of a leader is reflected in the standards they set for themselves." -- Ray Kroc
No comments:
Post a Comment