DeepMind scientists: Reinforcement learning is enough for general AI

A different approach to creating AI, proposed by the DeepMind researchers, is
to recreate the simple yet effective rule that has given rise to natural
intelligence. “[We] consider an alternative hypothesis: that the generic
objective of maximising reward is enough to drive behaviour that exhibits most
if not all abilities that are studied in natural and artificial intelligence,”
the researchers write. This is basically how nature works. As far as science is
concerned, there has been no top-down intelligent design in the complex
organisms that we see around us. Billions of years of natural selection and
random variation have filtered lifeforms for their fitness to survive and
reproduce. Living beings that were better equipped to handle the challenges and
situations in their environments managed to survive and reproduce. The rest were
eliminated. This simple yet efficient mechanism has led to the evolution of
living beings with all kinds of skills and abilities to perceive, navigate,
modify their environments, and communicate among themselves.
How To Become A Machine Learning Engineer?

New roles such as machine learning architecture are being created today. As the
platform gets bigger, the machine learning engineer should handle the entire
architecture and evolve to meet the needs of the data science, machine learning
and data analytics organisations. The most important aspect of an ML engineer is
the focus on production and model deployment — not just code that works, but
code that functions in the real world, alongside understanding industry best
practices to successfully integrate and deploy machine learning models. For
starters, having a computer science, robotics, engineering and physics degree,
along with competencies in C, C++, Java, Python, R, Scala, Julia, and other
enterprise languages, helps. Plus, a stronger understanding of databases adds
weightage. At experience levels, software engineers, software developers, and
software architects are cut out for machine learning engineering roles. “It is
almost a straight line from cloud architect to ML engineer and ML architect, as
these two roles have so much overlap. If you understand data science and machine
learning, you can understand models,” said Vashishta.
.NET Ranks High in Coding Bootcamp Report

Microsoft's .NET development framework ranked high in recent research about
coding bootcamps, or "immersive technology education." With an average cost of
about $14,000, these accelerated learning programs can last from six to 28 weeks
-- averaging about 14 -- and promise to advance careers in both technical chops
and bottom-line salary increases. Course Report studies the industry and
presents its findings in annual reports that can help coders pick the best
option, among some 500 around the world, with the choice of programming language
being a primary factor. "Coding bootcamps employ teaching languages to introduce
students to the world of programming," Course Report said in its latest study:
Coding Bootcamps in 2021, an update of a 2020 report. "While language shouldn't
be the main deciding factor when choosing a bootcamp, students may have specific
career goals that guide them towards a particular language. In that case, first
decide whether you'd prefer to learn web or mobile development. For the web,
your main choices are Ruby, Python, LAMP stack, MEAN stack and .NET languages.
Amazon Sidewalk starts sharing your WiFi tomorrow, thanks
Amazon Sidewalk will create a mesh network between smart devices that are
located near one another in a neighborhood. Through the network, if, for
instance, a home WiFi network shuts down, the Amazon smart devices connected to
that home network will still be able to function, as they will be borrowing
internet connectivity from neighboring products. Data transfer between homes
will be capped, and the data communicated through Amazon Sidewalk will be
encrypted. Amazon smart device owners will automatically be enrolled into Amazon
Sidewalk, but they can opt out before a June 8 deadline. That deadline has irked
many cybersecurity and digital rights experts, as Amazon Sidewalk itself was not
unveiled until June 1—just one week before a mass rollout. Jon Callas, director
of technology projects at Electronic Frontier Foundation, told the news outlet
ThreatPost that he did not even know about Amazon’s white paper on the privacy
and security protocols of Sidewalk until a reporter emailed him about it. “They
dropped this on us,” Callas said in speaking to ThreatPost. “They gave us seven
days to opt out.”
Researchers Discover a Molecule Critical to Functional Brain Rejuvenation
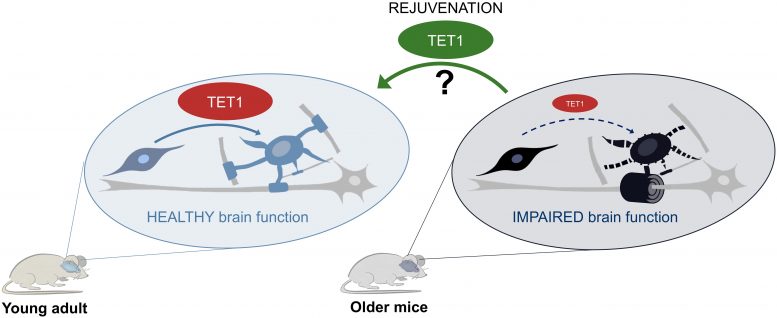
Recent studies suggest that new brain cells are being formed every day in
response to injury, physical exercise, and mental stimulation. Glial cells, and
in particular the ones called oligodendrocyte progenitors, are highly responsive
to external signals and injuries. They can detect changes in the nervous system
and form new myelin, which wraps around nerves and provides metabolic support
and accurate transmission of electrical signals. As we age, however, less myelin
is formed in response to external signals, and this progressive decline has been
linked to the age-related cognitive and motor deficits detected in older people
in the general population. Impaired myelin formation also has been reported in
older individuals with neurodegenerative diseases such as Multiple Sclerosis or
Alzheimer’s and identified as one of the causes of their progressive clinical
deterioration. ... The discovery also could have important implications for
molecular rejuvenation of aging brains in healthy individuals, said the
researchers. Future studies aimed at increasing TET1 levels in older mice are
underway to define whether the molecule could rescue new myelin formation and
favor proper neuro-glial communication.
Fujifilm refuses to pay ransomware demand, restores network from backups

Jake Moore, cybersecurity specialist at internet security firm ESET, said
refusing to pay a ransom is “not a decision to be taken lightly.” Ransomware
gangs often threaten to leak or sell sensitive data if payment is not made.
However, Fujifilm Europe said it is “highly confident that no loss, destruction,
alteration, unauthorised use or disclosure of our data, or our customers’ data,
on Fujifilm Europe’s systems has been detected.” The spokesperson added: “From a
European perspective, we have determined that there is no related risk to our
network, servers and equipment in the EMEA region or that of our customers
across EMEA. We presently have no indication that any of our regional systems
have been compromised, including those involving customer data.” It is not clear
if the ransomware gang stole Fujifilm data from the affected network in Japan.
Fujifilm declined to comment when asked if those responsible had threatened to
publish data if the ransom is not paid. According to security news site Bleeping
Computer, Fujifilm was infected with the Qbot trojan last month.
Fixing Risk Sharing With Observability

The challenge is that one party, the developers, has more information than other
parties. That information asymmetry is what creates unbalanced risk sharing.
Coping with information asymmetry has led to all kinds of new collaborative
models, starting with DevOps and evolving into DevSecOps and other permutations
like BizDevSecOps. True collaboration has been hard to come by. Early DevOps
efforts are often successful, but scaling beyond five to seven teams is
difficult because teams lack the breadth of experience in IT operations or the
SRE capacity to staff multiple product teams. The change velocity DevOps teams
can achieve is often far greater than SREs and SecOps can absorb, making
information asymmetry worse. If teams can’t maintain high levels of
collaboration and communication, another option must be developed. Observability
practices, like collecting all events, metrics, traces and logs, allow SREs and
SecOps teams to interrogate applications about their behavior without knowing
which questions they want to ask ahead of time. However, observability only
works if applications, and the infrastructure they rely on, are instrumented.
How to Structure a Digital Transformation Project Team

The first role on a project team and arguably the most important role on a
product team is your executive steering committee. This is typically a
cross-functional group of executives within your organization that are
responsible for setting the vision for the overall transformation. They’re
responsible for approving scope changes, or any sort of material changes to the
project plan or the budget. They’re ultimately responsible for setting the tone
and the vision for the overall future state. The question to ponder on here is,
how do we want our operation model to look and what do we want our organization
to look like in the future? For lack of a better word, what do we want to be
when we grow up? Before I get into the rest of the project team, something
that’s very important even before we talk about other team roles is who should
fill these other roles. The first thing you want to do is make sure that the
steering committee is aligned on the overall transformation, vision, strategy,
and objectives. If you start filling out the project team prematurely, when you
don’t have that alignment
Windows Container Malware Targets Kubernetes Clusters

After it compromises web servers, Siloscape uses container escape tactics to
achieve code execution on the Kubernetes node. Prizmant said that Siloscape’s
heavy use of obfuscation made it a chore to reverse-engineer. “There are almost
no readable strings in the entire binary. While the obfuscation logic itself
isn’t complicated, it made reversing this binary frustrating,” he explained. The
malware obfuscates functions and module names – including simple APIs – and only
deobfuscates them at runtime. Instead of just calling the functions, Siloscape
“made the effort to use the Native API (NTAPI) version of the same function,” he
said. “The end result is malware that is very difficult to detect with static
analysis tools and frustrating to reverse engineer.” “Siloscape is being
compiled uniquely for each new attack, using a unique pair of keys,” Prizmant
continued. “The hardcoded key makes each binary a little bit different than the
rest, which explains why I couldn’t find its hash anywhere. It also makes it
impossible to detect Siloscape by hash alone.”
Machine learning at the edge: TinyML is getting big

Whether it's stand-alone IoT sensors, devices of all kinds, drones, or
autonomous vehicles, there's one thing in common. Increasingly, data generated
at the edge are used to feed applications powered by machine learning models.
There's just one problem: machine learning models were never designed to be
deployed at the edge. Not until now, at least. Enter TinyML. Tiny machine
learning (TinyML) is broadly defined as a fast growing field of machine learning
technologies and applications including hardware, algorithms and software
capable of performing on-device sensor data analytics at extremely low power,
typically in the mW range and below, and hence enabling a variety of always-on
use-cases and targeting battery operated devices. ... First, the working
definition of what constitutes TinyML was, and to some extent still is, debated.
What matters is how devices can be deployed in the field and how they're going
to perform, said Gousev. That will be different depending on the device and the
use case, but the point is being always on and not having to change batteries
every week. That can only happen in the mW range and below.
Quote for the day:
"If you're relying on luck, you have
already given up." -- Gordon Tredgold
No comments:
Post a Comment