What To Look At When Assessing Your Cybersecurity Vulnerability Risk

Each asset vulnerability is assigned a CVSS score that describes the technical
risk. This score is a common, neutral framework based on the ease of
exploitation and potential impact on confidentiality, integrity and
availability. But CVSS scores alone don’t consider the asset’s value to the
business. You should also ask the following three questions: 1. Is the asset the
most important server in the organization (i.e., where critical data is
stored)?; 2. Is it an application that processes business transactions
(e.g., e-commerce)? Business criticality is a factor that must be considered and
weighed in determining whether to prioritize the asset; 3. What is the
threat level associated with the vulnerability? This is based on assessing
activity by hackers around the vulnerability. Solution providers monitor this
activity to provide threat intelligence data feeds to mature security
organizations. All three factors need to be put together and correlated into a
cyber risk score for the asset. A score like this allows the security teams to
apply data-driven judgment to their prioritization and remediation of
vulnerabilities found.
Creating a Data Advantage: CIOs Discuss Best Practices

Nick Heudecker, Former VP of Data and Analytics at Gartner, claims “CIOs are at
a strange crossroads with data today. They are both competing and collaborating
with CDOs that may be taking their budget and staff, but they’re still
ultimately responsible for data infrastructure.” Some, says Microsoft Security
Architect Wayne Anderson, believe, unfortunately, that the CDO is a yellow flag
to the CIO to look at their role in the organization.” Without questions, CIOs
need to make IT a better partner. To do this, they need to connect with the
business. They need to make data transformative happen and need to become a data
champion. Former CIO Joanna Young argues for data to win there needs to be
collaboration between technology functions. She says, however, “I have yet to
see an organization with CIO, CTO, and CDO where the sum is greater than the
parts, as roles and responsibilities get murky how can they be effective?” With
this said, IT typically does not own the corporation’s data. For this reason,
Sacolick says, “a key responsibility of the CIO and/or CDO is defining owners
and educating them on their responsibilities especially for data quality.
Dear enterprise IT: Cybercriminals use AI too

AI-powered cyberattacks are conventional cyberattacks augmented with AI and
machine learning technologies. Take phishing, for example — a type of social
engineering where an attacker sends a message designed to trick a human into
revealing sensitive information or installing malware. Infused with AI, phishing
messages can be personalized to target high-profile employees at enterprises
(like members of the C-suite) in a practice known as “spear phishing.” Imagine
an adversarial group attempting to impersonate board members or send fake
invoices claiming to come from familiar suppliers. Sourcing a machine learning
language model capable of generating convincing-sounding emails, the group could
fine-tune a system to generate replies that adopt the tone and tenor of the
impersonated sender and even make references to previous correspondences. That
might sound far-fetched — but there’s already growing concern among academics
that tools like GPT-3 could be co-opted to foment discord by spreading
misinformation, disinformation, and outright lies. Phishing emails need not be
highly targeted to present a threat to organizations.
Cisco Smart Switches Riddled with Severe Security Holes

There are also multiple other security flaws in the same web-management
interface. For instance, the bug tracked as CVE-2021-1541 is an arbitrary
code-execution vulnerability that would allow an authenticated, remote attacker
to execute arbitrary commands as a root user on the underlying operating system.
“This vulnerability is due to a lack of parameter validation for TFTP
configuration parameters,” according to Cisco. “An attacker could exploit this
vulnerability by entering crafted input for specific TFTP configuration
parameters. A successful exploit could allow the attacker to execute arbitrary
commands as a root user on the underlying operating system.” The attacker must
have valid administrative credentials on the device in order to exploit the
issue, so the CVSS score comes in at 7.2 rather than critical. The issue tracked
as CVE-2021-1543, meanwhile, allows cross-site scripting from an
unauthenticated, remote attacker (CVSS score: 6.1). “This vulnerability is due
to insufficient validation of user-supplied input by the web-based management
interface of the affected device,” according to Cisco. “An attacker could
exploit this vulnerability by persuading a user to click a malicious link and
access a specific page. ...”
How to Solve Kubernetes Persistent Storage Challenges

By design, containers work best with stateless applications. Kubernetes is able
to create and remove containers in a rapid and dynamic manner because the
applications within those containers come packaged with all of the dependencies
they need to run. Regardless of where a new container is spun up — the same
cluster or a different cloud provider — Kubernetes ensures that the application
has access to the fundamental resources it needs to operate. The dynamic
creation and deletion of containers doesn’t work well for applications that need
to persistently store data. As a stateful, containerized application is created
or destroyed across a Kubernetes cluster, it must always know where its data is,
have a high degree of access to that data and be able to ensure its integrity.
This isn’t possible if an application’s stored state is destroyed every time its
container is spun down. Developers and platform managers want the best of both
worlds: They want the fast failover, easy deployment and the efficiency of
containers with the persistence of stateful workloads.
Mathematicians Prove 2D Version of Quantum Gravity Really Works

“It took us 40 years in math to make sense of four pages,” said Vincent Vargas,
a mathematician at the French National Center for Scientific Research and
co-author of the research with Rémi Rhodes of Aix-Marseille University, Antti
Kupiainen of the University of Helsinki, François David of the French National
Center for Scientific Research, and Colin Guillarmou of Paris-Saclay University.
... “Quantum gravity basically means random geometry, because quantum means
random and gravity means geometry,” said Sun. Polyakov’s first step in exploring
the world of random surfaces was to write down an expression defining the odds
of finding a particular spiky planet, much as the bell curve defines the odds of
meeting someone of a particular height. But his formula did not lead to useful
numerical predictions. To solve a quantum field theory is to be able to use the
field to predict observations. In practice, this means calculating a field’s
“correlation functions,” which capture the field’s behavior by describing the
extent to which a measurement of the field at one point relates, or correlates,
to a measurement at another point. Calculating correlation functions in the
photon field, for instance, can give you the textbook laws of quantum
electromagnetism.
DevSecOps: An open source story

DevSecOps adds security into DevOps, further refining the concept to address
code quality, security, and reliability assurance through automation, enabling
continuous security and compliance. Organizations seeking to comply with
Sarbanes Oxley (SOX), Payment Card Industry Data Security Standard (PCI DSS),
FedRAMP, and similar programs are candidates for implementing DevSecOps. ... The
more you move security mitigation to the left to tackle these issues in
development, the more money you save. You also avoid potential negative
headlines because your teams don't have to respond to issues in production,
where remediation costs can soar way higher than if you caught them in your
development environment. You can treat the move from DevOps to DevSecOps as
another step in the DevOps journey. ... Even if you treat DevSecOps as another
step in your DevOps journey, you can expect changes to your toolchain, roles on
your DevOps and security teams, and how your groups interact. Over 60% of the
respondents to GitLab's 2021 Global DevSecOps Survey report new roles and
responsibilities because of DevOps, so prepare your people upfront and keep
surprises to a minimum.
Thought Leadership Strategy: A Key ingredient for Professionals Who Want More Success
We’ve discussed personal branding extensively on this blog. And you can think of
thought leadership as an extension of your personal brand — it can even become a
goal in your branding and content marketing strategy. But what is it? Thought
leadership taps into your industry expertise, your passion, and your talent, all
to connect you with your audience. A thought leader produces valuable content
that not only addresses the pain points of his/her audience but also delivers
key insights and advice on industry trends that aren’t available elsewhere. One
of the most advantageous benefits of thought leadership is that it is accessible
to anyone. It doesn’t matter your background or degrees. If you have knowledge
and expertise, you can become a thought leader! But there’s one caveat. While
you can become a thought leader, it is not something that you can force. You
can’t just label yourself as a “thought leader” and expect everyone to get the
memo. This title has to be earned through great content, proven ability, and
visibility.
What Is Blockchain?

How these new blocks are created is key to why blockchain is considered highly
secure. A majority of nodes must verify and confirm the legitimacy of the new
data before a new block can be added to the ledger. For a cryptocurrency, they
might involve ensuring that new transactions in a block were not fraudulent, or
that coins had not been spent more than once. This is different from a
standalone database or spreadsheet, where one person can make changes without
oversight. “Once there is consensus, the block is added to the chain and the
underlying transactions are recorded in the distributed ledger,” says C. Neil
Gray, partner in the fintech practice areas at Duane Morris LLP. “Blocks are
securely linked together, forming a secure digital chain from the beginning of
the ledger to the present.” ... “As a reward for their efforts in
validating changes to the shared data, nodes are typically rewarded with new
amounts of the blockchain’s native currency—e.g., new bitcoin on the bitcoin
blockchain,” says Sarah Shtylman, fintech and blockchain counsel with Perkins
Coie.
How Workplace Culture Affects Workplace Performance
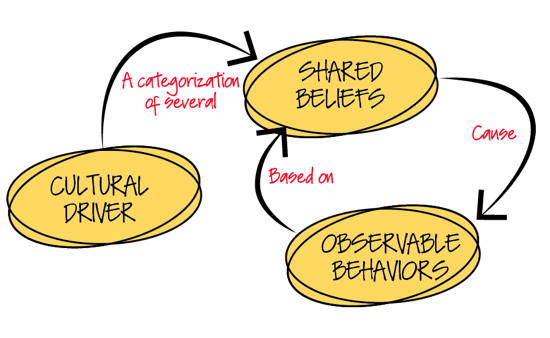
If you have ever visited a software shop where they turn out great products, you
will have noticed the enthusiasm of the people for their work. You will also
have noticed that these skilled people are given a working atmosphere that is
conducive to their work. They feel safe to argue if they think they have a
better answer; they are valued by their organisation, they are given an
appropriate amount of time to do their tasks This is workplace culture. For the
last two years, we, along with our partners in The Atlantic Systems Guild, have
been writing a book on workplace culture. It is not the intention of this
article to sell you a book (of course we would be delighted if you buy it) but
to demonstrate some findings from our work. To have a useful view of culture, we
identified six drivers of workplace culture. It is worth having a quick look at
these drivers, because even a superficial glance will show you areas that you
might work on to improve your own workplace culture, and thereby performance of
the workplace.
Quote for the day:
"To do great things is difficult; but to
command great things is more difficult." -- Friedrich Nietzsche
No comments:
Post a Comment