Sparking the next cycle of IT spending

The past cycles were driven by vendors, by a shift in technology that created a
new productivity paradigm. In fact, we could fairly say that every past cycle
was driven by a single vendor, IBM. They popularized and drove commercial
computing in the first cyclic wave. Their transaction processing capability
(CICS, for those interested in the nitty gritty) launched the second wave, and
their PC the third. Can IBM, or any vendor, pull together the pieces we need?
These days, for something like contextual computing, we’re probably reliant on
open-source software initiatives, and I’m a believer in them, with a
qualification. The best open-source contextual computing solution wouldn’t
likely be developed by a community. It would be done by a single player and
supported and enhanced by a community. Open-source simplifies the challenge that
being the seminal vendor for contextual computing would pose, but some vendor is
still going to have to build the framework and make that initial submission.
Otherwise we’ll spend years and won’t accomplish anything in the end.
Hackers Crack Pirated Games with Cryptojacking Malware
Dubbed “Crackonosh,” the malware — which has been active since June 2018 — lurks in pirated versions of Grand Theft Auto V, NBA 2K19 and Pro Evolution Soccer 2018 that gamers can download free in forums, according to a report posted online Thursday by researchers at Avast. The name means “mountain spirit” in Czech folklore, a reference to the researchers’ belief that the creators of the malware are from the Czech Republic. Cracked software is a version of commercial software that is often offered for free but often with a catch — the code of the software has been tampered with, typically to insert malware or for some other purpose beneficial to whoever cracked it. In the case of Crackonosh, the aim is to install the coinminer XMRig to mine Monero cryptocurrency from within the cracked software downloaded to an affected device, according to the report. So far, threat actors have reaped more than $2 million, or 9000 XMR in total, from the campaign, researchers said. Crackonosh also appears to be spreading fast, affecting 222,000 unique devices in more than a dozen countries since December 2020. As of May, the malware was still getting about 1,000 hits a day, according to the report.
Cryptocurrency Blockchains Don’t Need To Be Energy Intensive

Blockchain is a generic term for the way most cryptocurrencies record and share their transactions. It’s a type of distributed ledger that parcels up those transactions into chunks called “blocks” and then chains them together cryptographically in a way that makes it incredibly difficult to go back and edit older blocks. How often a new block is made and how much data it contains depends on the implementation. For Bitcoin, that time frame is 10 minutes; for some cryptocurrencies it’s less than a minute. Unlike most ledgers, which rely on a central authority to update records, blockchains are maintained by a decentralized network of volunteers. The ledger is shared publicly, and the responsibility for validating transactions and updating records is shared by the users. That means blockchains need a simple way for users to reach agreement on changes to the ledger, to ensure everyone’s copy of the ledger looks the same and to prevent fraudulent activity. These are known as consensus mechanisms, and they vary between blockchains.
Quantum computers just took on another big challenge.

Classical computers can only offer simplifications and approximations. The
Japanese company, therefore, decided to try its hand at quantum technologies,
and announced a partnership with quantum software firm CQC last year.
"Scheduling at our steel plants is one of the biggest logistical challenges we
face, and we are always looking for ways to streamline and improve operations
in this area," said Koji Hirano, chief researcher at Nippon Steel. Quantum
computers rely on qubits – tiny particles that can take on a special, dual
quantum state that enables them to carry out multiple calculations at once.
This means, in principle, that the most complex problems that cannot be solved
by classical computers in any realistic timeframe could one day be run on
quantum computers in a matter of minutes. The technology is still in its
infancy: quantum computers can currently only support very few qubits and are
not capable of carrying out computations that are useful at a business's
scale. Scientists, rather, are interested in demonstrating the theoretical
value of the technology, to be prepared to tap into the potential of quantum
computers once their development matures.
Why Agile Fails Because of Corporate Culture
In most companies, however, providing creative space and encouraging to fail aren't really core values, are they? Therefore, it's the creation of this awareness which is is a fundamental obstacle and the only real reason why agility fails because of corporate culture. The weirdest fact about all this: The failure of agility in the company is itself a failure from which companies learn nothing. Why? Because failure is not seen as an opportunity for improvement, but as failure. And so it goes on and on; a vicious circle from which companies can only break out through a culture change. This change requires certain skills from all those involved. For some, these skills have yet to be awakened; for others, they're probably present and may only just need to be fostered. But all of those involved will need to be coached, on a long-term basis. Becoming agile is an evolutionary process and it can't just be avoided or saved-upon by taking advantage of the wisdom of others or applying arbitrary agile frameworks from a consultant's shelve to be agile. And let me stress that: Evolution. That means it's ever-ongoing. It's not a one-off big bang thing and whoohoo you're agile. As a C-level guy or gal, as a board member or shareholder it will take loads of guts to go that way.
Ag tech is working to improve farming with the help of AI, IoT, computer vision and more

Harvesting is a great example of AI on the farm. A combine is used to separate
grain from the rest of the plant without causing damage to corn kernels. "That
separation process is not perfect, and it's impossible for a farmer to see
every kernel as it makes its way through the different sections of the
machine," Bonefas explained. "AI enables the machine to monitor the separation
process and to make decisions based on what it's seeing. If the harvest
quality degrades, the AI-enabled system automatically optimizes the combine's
settings or recommends new settings to the farmer to achieve more favorable
results." In other farming operations, AI uses computer vision and machine
learning to detect weeds and precisely spray herbicides only where needed.
This results in significant cost reductions for farmers, who in the past used
sprays across entire fields, even in areas where sprays were not needed. The
weed detection technology works because it integrates AI with IoT devices such
as cameras that can take good pictures regardless of weather conditions.
Computers process imagery from the cameras and use sophisticated machine
learning algorithms that detect the presence of weeds and actuate the required
nozzles on sprayers at the exact moment needed to spray the weeds.
Architecture is theory
For organisation versus enterprise, one of the common assumptions is that the
two terms are synonyms for each other: that the organisation is the
enterprise, that the enterprise is the organisation. In reality,
‘organisation’ and ‘enterprise’ denote two different scope-entities (in
essence, ‘how’ versus ‘why’) whose boundaries may coincide – but that
special-case is basically useless and dangerously misleading, because it
represents a context in which the sole reason for the organisation’s existence
is to talk only with itself. The simplest summary here is that the enterprise
represents the context, purpose and guiding-story for the respective
organisation (or ‘service-in-focus’, to use a more appropriate context-neutral
term): we develop an architecture for the organisation, about the enterprise
that provides its context. In practice, the scope of enterprise we’d typically
need to explore for an enterprise-architecture would be three steps ‘larger’
than the scope for the organisation – the organisation plus its transactions,
direct-interactions and indirect-interactions – and also looking ‘inward’ to
perhaps the same depth:
Cisco ASA Bug Now Actively Exploited as PoC Drops

In-the-wild XSS attacks have commenced against the security appliance
(CVE-2020-3580), as researchers publish exploit code on Twitter. Researchers
have dropped a proof-of-concept (PoC) exploit on Twitter for a known
cross-site scripting (XSS) vulnerability in the Cisco Adaptive Security
Appliance (ASA). The move comes as reports surface of in-the-wild exploitation
of the bug. Researchers at Positive Technologies published the PoC for the bug
(CVE-2020-3580) on Thursday. One of the researchers there, Mikhail
Klyuchnikov, noted that there were a heap of researchers now chasing after an
exploit for the bug, which he termed “low-hanging” fruit. ... “Researchers
often develop PoCs before reporting a vulnerability to a developer and
publishing them allows other researchers to both check their work and
potentially dig further and discover other issues,” Claire Tills, senior
research engineer at Tenable, told Threatpost. “PoCs can also be used by
defenders to develop detections for vulnerabilities. Unfortunately, giving
that valuable information to defenders means it can also end up in the hands
of attackers.”
How edge will affect enterprise architecture: Aruba explains
Logan reckons IoT at edge growth will be significant as enterprise
organizations are now starting to look at the network as a far more important
component than they did four or five years ago, “where it might [then] have
just been four bars of Wi-Fi or connectivity from branch to headquarters,”
Logan said. New requirements on the architectures will be an end result of
this shift. It will include data-intensive workloads caused by AI and so on.
“We are going to find over the next 10 years that a significant amount of the
data that is born at the edge and the experiences that are delivered at the
edge need a local presence of computer and communications,” Logan added. As
far as enterprise architecture evolving, he uses the example of a healthcare
environment, such as a hospital: Patient telemetry has to be collected from
the bedside. But “what if the point of patient care is in the patient’s home?”
he asked. This is a realistic proposition, as we’ve seen during the pandemic
with the escalation of remote doctor care. “That’s a completely different set
of circumstances, physically and logically from an enterprise architecture
perspective,” Logan said.
Integrating machine learning and blockchain to develop a system to veto the forgeries and provide efficient results in education sector
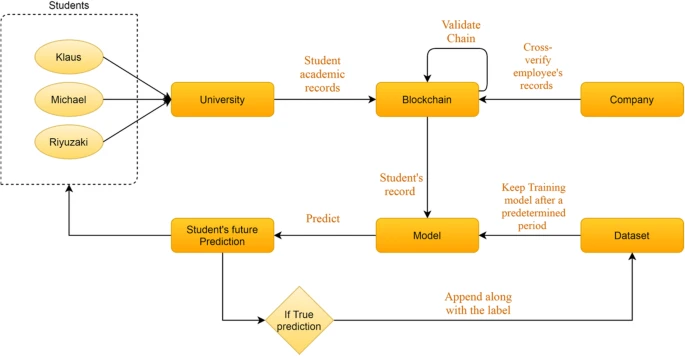
The advancement of blockchain technology in terms of validation and data
security has also been applied in the educational sector, with the validation
and security of student data being considered prime aspects. Various systems
providing such validation and security have been developed. For example, Li
and Wu proposed the idea of flashing the system, through which the
counterfeiting of student degrees can be avoided. Such a program has to some
degree remedied the defects found in current solutions, making the use of a
blockchain-based certificate a more feasible theory. Many types of
certificates of success, grades, and diplomas, among other documents, can
become a valuable tool in finding a new school or job. Gopal and
Prakash proposed a blockchain-based digital certificate scheme based on
the immutable properties of blockchain. This scheme preserves the essential
data and eliminates the chance of any company with a job offering distrusting
a student’s certification. Individual learning records are important for
the professional careers of individuals. Certificates support the achievement
of learning outcomes in education.
Quote for the day:
"Energy and persistence conquer all
things." -- Benjamin Franklin
No comments:
Post a Comment