Unlocking Enterprise Blockchain Potential with Low-Code Capabilities

Low-code development platforms allow enterprises to reap the benefits of complex code, without the need to dedicate valuable time and resources toward development from the ground-up. “Plug and play” customization allows them to address specific needs within their organization, and prioritize implementation on a smaller scale without the stress of diving head-first into an infrastructural overhaul. Especially during our ongoing COVID-19 crisis, low-code eliminates the need for large dev teams to develop new software applications, allowing for a streamlined, timely transition as organizations dedicate their valuable resources elsewhere to help minimize the negative impact of COVID-19 on their workforce and their surrounding communities. Beyond this epidemic, these benefits provide risk-averse C-level decision makers with an easy and confident investment opportunity, as well as disruptive tools that deliver on the growing need for constant innovation — in an era where agility and digital transformation are now a necessity.
Phishing Attack Bypassed Office 365 Multifactor Protections
The phishing attack started with an email that contains a malicious link that's designed to look like a SharePoint file, according to the report. The message in the email noted that the file relates to bonuses for the quarter - an effective lure to get a victim to click. If a targeted victim clicked the link, they were taken to the legitimate Microsoft Office 365 login page. But the URL had been subtly changed by the attackers to manipulate the authentication process. To log in to Office 365, a user typically needs permission from the Microsoft Graph authentication process and a security token from the Microsoft Identity Platform. This is where the OAuth 2.0 framework, which grants a user limited access to their resources from one site to another, and the OpenID Connect protocol, which helps devices verify a user, came into play in the scam. These are designed to allow a user to log in without exposing credentials, according to the report. The altered URL contained parameters that captured the security tokens and other authentication data and then sent that information back to the attackers. In one example, Cofense found a "redirect" parameter in the URL that sent authentication data to a domain hosted in Bulgaria.
Ionic vs. Xamarin

In the ordinary world of web development, applying custom styling is relatively easy. Just port your existing components over to your new project, or apply the specific CSS edits that you need to make your app look and feel the way you want it to. But in the mobile world, this becomes a lot harder. For example, Xamarin Native uses only the native components available on iOS and Android. You won’t be able to just copy over your existing component library, and the styling and theming options are extremely limited. This is where Ionic’s approach is most valuable. Ionic UI components are just Web Components. By default, they are designed to look and feel native to iOS and Android; but under the hood, they’re just Web Components. If you already have a React or Web Component library, you can easily port those over to your mobile project. Or, you can edit any aspects of the UI using CSS, just as you would for any web project. This level of design customizability is unparalleled in the world of mobile app development.
How Agile Can Work Together with Deadlines
When attempting to soften arbitrary deadlines, your stakeholder relationships are key. Often, the drivers behind a fixed deadline are a lack of detail, context, and trust. For stakeholders to trust that they are going to get something delivered, and more than that something that is valuable delivered, you have to look to build up that understanding and that trust. Once you have built that up, you are also more likely to gain flexibility in your delivery timelines. At Loyalty, we made sure that we had regular open dialogues with a wide stakeholder group via weekly demos. We talked through the challenges, showed off what had been worked on that week, and acted as a source of truth on our progress. This avoided rumours or corridor chat that can undermine delivery if stakeholders are getting a mixed message. The demos not only built trust, but also removed any rumours; we were regularly available for questions and to have an open dialogue. The other key factor that I have already alluded to is frank conversations.
Why the economic recovery post COVID-19 is not doom and gloom for tech talent

There is no doubt that the recovery will be a long road ahead, but as we look to the future there are some promising signs about the market for STEM talent. Our data suggests that the demand for contract placements has remained intact. Even in markets such as the US and UK, while there has been some drop-off in the volume of candidates placed, demand for contract placements has continued to remain consistent throughout March and April - because employers still need the right talent, but now more than ever they also need a flexible hiring approach that enables them to fill talent gaps on an ‘as-needed’ basis. Employers are also telling us that they will have significant talent gaps to fill upon an eventual recovery the economy. This demand for quick access to talent could in turn be turbocharged by tech - employers will be much more open to shifting to remote working if it means widening their talent pools to meet urgent business demand. The days of candidates needing to be localised to their employer may be gone for good in several sectors - many are now saying that they see the shift to remote, flexible working becoming entrenched within their industry as a lasting change.
The Need for Compliance in a Post-COVID-19 World
US and UK cybersecurity officials warn that state-backed hackers and online criminals are taking advantage of people's anxiety over COVID-19 to lure them into clicking on links and downloading attachments in phishing emails that contain malware or ransomware. Corporate networks could also be vulnerable to attacks if companies do not invest in providing their employees secure company laptops and set up virtual private networks (VPNs) or zero-trust access solutions. With all of this upheaval, business leaders need to keep their guard up. It's easy to lose focus and push off implementing security measures, managing risk, and keeping up with compliance requirements. But this would be a big mistake. Regulatory requirements are designed to ensure that organizations establish a solid cybersecurity program — and then monitor and update it on an ongoing basis. It's critical that organizations continue to stay compliant with applicable security standards and guidelines, especially those concerning policies and procedures, business continuity planning, and remote workers.
On Being (and Becoming) a Data Scientist

The discipline of data science includes a set of technical skills with broad applications that have grown in demand with the advent of “Big Data”. Data science now has too many use cases to count: epidemiology, pharmaceuticals, finance and banking, media and advertising. Even ‘Money Ball’. We are needed most everywhere. The number of applications is both a blessing and a curse, however. As data scientists, we may understand the challenges at work in technical terms but lack an understanding of the broader context important to comprehending and solving problems in a meaningful, practical way. In establishing and building a career as a data scientist, domain matters. Unless you’re an industry expert who becomes a data scientist along the way, it takes time to be of use. We learn as we go, off and on, and not just when it comes to the stack, finding our way around the data. At some point, you’ll have to figure out whether the industry you’re in is something of interest to you beyond data science (unless, that is, it picks you). That’s the big, fundamental question.
There is a common misconception that remote workers won’t build strong relationships and company productivity will suffer as a result. The good news is this doesn’t appear to be true. In a remote world, bonding may take longer, but it does happen and can even “reach levels present in face-to-face communication,” according to a 2013 study published in Cyberpsychology. In fact, remote communication could actually be better for business, because it can bring a team closer together. “For strangers meeting for the first time, digital communication has been shown to enhance the intimacy and frequency of self-disclosure,” according to the researchers. They noted that “strangers meeting in text-based environments show higher affinity for one another than strangers meeting one another face to face.” Perhaps more importantly, study participants reported the same level of bonding after video chats as they did after in-person interactions. The level of bonding did decrease, however, with audio and instant message communication.
Using the 'Zero Trust' Model for Remote Workforce Security
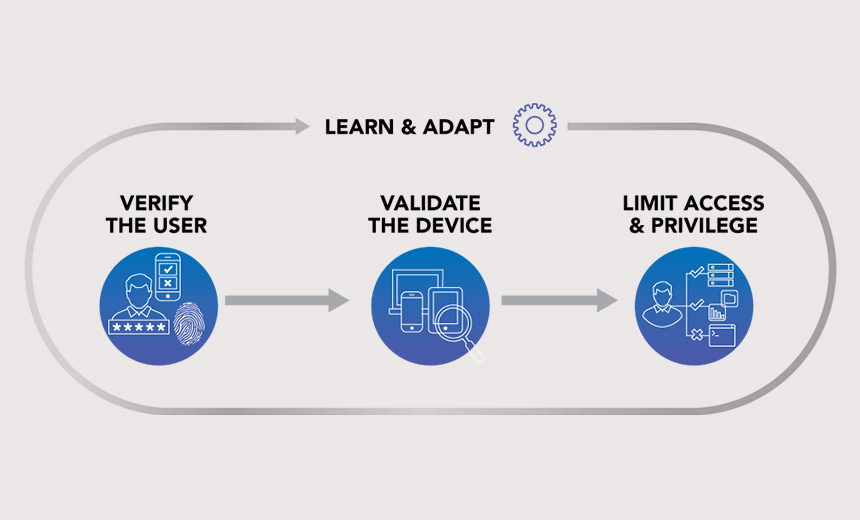
An essential component of the zero trust model is verifying devices from where data is getting accessed using technologies such as CASB and Web DLP. "If an employee is accessing my database through a personal device, the zero trust approach helps me check the device security posture," Khanna says. "Only after these verifications is the device allowed to access the database." Gary Hayslip, director of information security at SoftBank Investment Advisers in California, says the zero trust approach fits his company's 100% cloud approach. "For us it was all about having a proper control over access. We wanted to have a control and know about who is accessing what kind of data," Hayslip says. "Now, whether workers are travelling or at home, we know the device, we know the user, we know the geo location and we know what data the user accessed." When building a zero trust framework, Panchal says, it's critical to "capture every physical and digital footprint of the users' access to the enterprise applications and services using AI on top of every log to understand the user behavior in the system and grant access accordingly.
Microsoft supercomputer looks to create AI models in Azure
While launching into the supercomputer market could give Microsoft's overall AI initiative a boost, one consultant said Microsoft still trails a few competitors, such as Google, in terms of general AI innovation. The best way for Microsoft to catch up is with a series of acquisitions of smaller AI companies. "Microsoft has made some acquisitions in this [AI] space, but they are still playing catch-up," said Frank Dzubeck, president of Communications Network Architects in Washington, D.C. "They are still focusing on application-specific algorithms for certain industries. They have made some headway but aren't there yet where the Googles of the world are." There will be a "changing of guard" in the AI market, Dzubeck said, led by a raft of both known and unknown fledgling AI companies, similar to what happened in the world of social networking 10 and 15 years ago. It is from among these companies that Microsoft, through acquisitions, will grow its fortunes in the AI market, he predicted.
Quote for the day:
"To get a feel for the true essence of leadership, assume everyone who works for you is a volunteer." -- Kouzes and Posner
No comments:
Post a Comment