CISO position burnout causes high churn rate
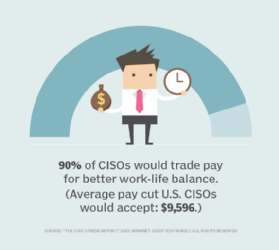
Even the most impressive professional pedigree can't guarantee a CISO's success. Those with technical backgrounds often find navigating the politics of the C-suite "extremely stressful," according to Budge. On the other hand, CISOs who come from management environments may be unprepared for the day-to-day grind of operational support, said Tony Buffomante, principal and cybersecurity leader at professional services firm KPMG. "Taking those calls and fixing systems in the middle of the night -- that's the part that drives burnout," he added. Budge suggested that problems arise when the right CISO takes the wrong job. "A lot of us are so eager for that title, we don't actually do the homework," she said, adding that she knows few security executives who conducted adequate due diligence before accepting job offers. In her research, Budge identified six distinct types of CISO, all with different backgrounds and abilities: transformational, post-breach, tactical/operational, compliance/risk, steady-state and customer-facing evangelist. Transformational CISOs, for example, tend to be energetic, business-oriented types with large appetites for change.
The home networks we need today are coming tomorrow

Recently, though, two wireless networking developments have paved the way to a future in which bandwidth-intensive applications from powerful client devices will have access to far greater spectrum than they ever have, while devices that need very little bandwidth -- but battery life that extends for months -- will be able to tap into an industry-shaping collaboration that will allow unprecedented interoperability. The first of these is the Wi-Fi 6E. Following a recent ruling by the FCC, Wi-Fi will soon be able to operate in the 6GHz range whereas today's Wi-Fi is limited to the heavily taxed 2.4GHz range and 5.8GHz range. This opens up more spectrum to Wi-Fi than the older two ranges have offered combined. Its impact will be felt particularly strongly once people start gathering again in venues such as conferences and arenas. However, it should also help improve network congestion in the home. There is a small catch. While new Wi-Fi standards have always required both the access point and client to be upgraded to take full advantage of what they can offer, backward compatibility has always been assumed.
AIOps 2020: IT Talent Is the Game-Changer

Automation is the backbone of technology, but true AIOps panacea is found when the right technologists know how to use the information AIOps provides. Think of a medical MRI: Once the technology identifies issues, human intervention steps in to determine how and when to improve and fix things. The same is true with AIOps. It frees an IT team to prioritize the most important items and who should tackle them, instead of combing through endless logs and wasting every developer’s time on break fixes. How a highly qualified, on-demand workforce makes a tangible, measurable difference here is a factor not to be underestimated. Talented technologists who can immediately ramp up on teams and systems—because it’s what they do day in and day out—seamlessly augment internal development staff and can address/remediate issues. The future of AIOps goes beyond the technology itself and rests in the hands of dynamically built, virtual teams that can address issues just as quickly as the AIOps platforms identify them.
Java Feature Spotlight: Text Blocks
A text block uses triple-quotes (""") as its opening and closing delimiter, and the remainder of the line with the opening delimiter must be blank. The content of the text block begins on the next line, and continues up until the closing delimiter. ... Java's string literals do not support interpolation of expressions, as some other languages do; text blocks do not either. (To the extent that we may consider this feature at some point in the future, it would not be specific to text blocks, but applied equally to string literals.) Historically, parameterized string expressions were built with ordinary string concatenation (+); in Java 5, String::format was added to support "printf" style string formatting. Because of the global analysis surrounding whitespace, getting the indentation right when combining text blocks with string concatenation can be tricky. ... What may be surprising is the number of different ways that such a feature is expressed in popular languages. It's easy to say "we want multi-line strings", but when we survey other languages, we find a surprisingly diverse range of approaches in both syntax and goals.
How much does it cost to launch a cyberattack?

Buying an individual piece of malware or even a full phishing kit isn’t enough to launch an attack: attacks require hosting, distribution channels, obfuscation for malware, account checkers and more. In a new report, Black-market ecosystem: Estimating the cost of “Pwnership,” Deloitte has gone beyond just listing the piecemeal costs and instead calculated the total cost of operations — from malware and keyloggers to things like domain hosting, proxies, VPNs, email distribution, code obfuscation and more — for threat actors to launch a full campaign against organizations. “The groups behind these types of large campaigns need multiple layers of services,” says Loucif Kharouni, threat intelligence leader at Deloitte Cyber Risk Services. For an operation to deliver a banking Trojan, you would need to use at least five or six services.” The report found that the dark web is awash with a variety of readily accessible services to suit the individual needs of the attacker, with pricing that accommodates all levels of investment.
Revealing leaders’ blind spots

As much as executives try to be self-aware, gaps — often big ones like Stephen’s — inevitably appear between how they think they are showing up in the world and how people perceive them. What is noteworthy is how widespread these misperceptions are. An analysis by Merryck & Co. and the Barrett Values Centre of the self-assessments of 500 leaders and then 10,000 of their peers over a period of 16 years offers a humbling insight for any senior executive who aspires to be self-aware: The top areas leaders identified in themselves as needing work barely ever overlapped with what their peers and key colleagues saw as areas that needed improvement. The conclusion is that leaders are mostly oblivious to the way their colleagues view their weaknesses. And these disconnects have consequences. Leaders’ blind spots can limit their opportunities, impede their performance, and ultimately drag down their career. For executives in the most critical roles, these limitations can also hamper their organization’s ability to execute its strategy, as was the case with Stephen.
Determined AI makes its machine learning infrastructure free and open source

“Machine learning is going to be a big part of how software is developed going forward. But in order for companies like Google and Amazon to be productive, they had to build all this software infrastructure,” said CEO Evan Sparks. “One company we worked for had 70 people building their internal tools for AI. There just aren’t that many companies on the planet that can withstand an effort like that.” At smaller companies, ML is being experimented with by small teams using tools intended for academic work and individual research. To scale that up to dozens of engineers developing a real product… there aren’t a lot of options. “They’re using things like TensorFlow and PyTorch,” said Chief Scientist Ameet Talwalkar. “A lot of the way that work is done is just conventions: How do the models get trained? Where do I write down the data on which is best? How do I transform data to a good format? All these are bread and butter tasks. There’s tech to do it, but it’s really the Wild West. And the amount of work you have to do to get it set up… there’s a reason big tech companies build out these internal infrastructures.”
Data Science for analytical minds | Introduction
Data science requires a lot of data wrangling, multiple model testing and optimisation along with visualisation to draw right insights, make inferences, do predictions or enable decisions. What’s more is that this needs to be done every day with varying data scale and capacity within the organisation. Therefore, knowing scripting programming languages that can best automate and optimise the work — from data cleaning to visualisation — is essential for any data scientist. R and python are most famously used programming languages used by data scientists but there are a lot more which we will discuss in detail in the coming section. Economists or statisticians are mostly taught STATA and basics of R or python in some universities, which is a good stepping stone but there is a long road ahead in learning how to write R or python scripts that are optimised for agility and speed.
YubiKey hands-on: Hardware-based 2FA is more secure, but watch out for these gotchas

Hardware-based security, on the other hand, is much more difficult to successfully attack remotely. To sign in, you have to insert the key and then tap it in response to a prompt to submit the proof of identity. The Yubikey devices I tested support hundreds of services that use a handful of standards, including FIDO2 Web Authentication (WebAuthn). A full list of supported services is available on the Yubico website, where you can search and filter to find the ones that interest you. It's worth noting that support for hardware-based authentication is considered a premium feature for many services; for example, if you use the password managers LastPass, Dashlane, or Bitwarden, you must upgrade to a Business, Premium, or Enterprise plan to enable a security key as a second factor. I tested both YubiKey devices with a representative sample of the kind of services you're likely to use regularly, including 1Password, Dropbox, Namecheap, GoDaddy, and Twitter. I also used the hardware key to secure Microsoft and Google accounts, as well as to sign in to a local account on a MacBook Pro.
Successful Transformation: Challenge the Status Quo

“The organization needs a shift in culture to encourage all employees to become more open to changes in their daily processes and tools–digital transformation is largely about creating a culture of constant learning. Without the pressure to provide perfect continuity in current technologies, IT leaders can become more comfortable trying new things,” said Stringer. “This is one of the reasons why it’s common to see large organizations collaborate with smaller companies for projects,” said Hennelund. “In the financial sector we see a flourishing fintech and insurtech market around established banks and insurance companies. Companies successful in challenging their status quo are those that can navigate between these collaborations or even small in-house sub-divisions that develop new digital IT-based projects,” added Hennelund. “Putting into place a quick decision-making process is also critical.” This could include making it possible for stakeholders to hold meetings and move forward with their consensus without always having to get board approval. Such shifts in behavior require culture change. So, how do organizations and IT leaders get there?
Quote for the day:
"Without courage, it doesn't matter how good the leader's intentions are." -- Orrin Woodward
No comments:
Post a Comment