The IT Jobs AI Could Replace and the Ones It Could Create

Knowledge base managers and data scientists will be essential roles for
enterprises as more and more data is fed into large language models (LLMs).
“It's still a garbage in, garbage out problem, and if AI will now do more of our
work, what we feed them is more important than ever,” says Katz. De Ridder
expects to see prompt engineering to emerge as an important skill in the IT
field rather than a distinct job. He describes new jobs that could come of the
AI boom: agent and multiagent engineers. Agent engineers would maintain and
adjust the AI agent processes, while multi-agent system engineers would function
as project managers overseeing the complex processes and outcomes supported by
multiple AI agents. These jobs will have myriad specializations tied to
different fields, according to De Ridder. As more and more AI use cases emerge,
IT workers could increasingly be looked at as AI co-pilots. How will they work
alongside this technology to improve productivity, and how will they oversee AI
capabilities to ensure the desired outcomes?
Microsoft Zero-Days Allow Defender Bypass, Privilege Escalation

But as with every Microsoft monthly update, there are several bugs in the
latest batch that security experts agreed merit greater attention than others.
The three actively exploited zero-day bugs fit that category. One of them is
CVE-2023-36036, a privilege escalation vulnerability in Microsoft's Windows
Cloud Files Mini Filter Driver that gives attackers a way to acquire
system-level privileges. Microsoft has assessed the vulnerability as being a
moderate — or important — severity threat but has provided relatively few other
details about the issue. Satnam Narang, senior staff research engineer at
Tenable, identified the bug as something that is likely going to be of interest
to threat actors from a post-compromise activity standpoint. An attacker
requires local access to an affected system to exploit the bug. The exploitation
involves little complexity, user interaction, or special privileges. Windows
Cloud Files Mini Filter Driver is a component that is essential to the
functioning of cloud-stored files on Windows systems, says Saeed Abbasi, manager
of vulnerability and threat research at Qualys.
How to infuse strategy into everything your company does

The strategic goal-setting landscape is evolving, moving beyond global
companies like Patagonia. It’s shifting from top-down mandates to a dynamic,
bidirectional model that fosters ambition and collaboration at all levels. In
highly successful organizations like LeanIX, an enterprise architecture
management firm, we have watched how OKRs have been both a philosophy and a
recipe for success and growth. LeanIX’s use of OKRs is not just a way to break
down the company’s strategy and to agree on a common focus for the quarter;
it’s an integral part of adopting a growth mindset. This ensures that the
entire organization is continuously thinking big, aiming high, and trying out
new approaches to achieve the next significant leap. ... Contemporary
boardrooms have to echo the aspirations and values of Gen Z, emphasising both
diversity and innovation. Merely having organizational strategies and cultural
values framed and displayed on walls won’t suffice. They must be actively
lived and practiced. Over a third of Gen Z expect leaders to not just lead but
inspire. They demand a transparency that goes beyond open
communication.
The Art of Digital Continuity: Ensuring Data Availability in Disasters

During disasters, managers and IT employees bear the emotional burden of
maintaining a calm and efficient work environment. This emotional labor can
lead to stress and burnout, so managing it is key to maintaining productivity
and data security during disasters. Here are some ways these professionals can
cope with the emotional toll: Communication - Open and honest communication
about the disaster’s impact is key for managing emotions. Keeping employees
informed can help them feel more in control of the situation. Support -
Providing psychological support, such as counseling or mental health
resources, can help employees cope with stress and anxiety during a disaster.
Training - Prioritizing training on disaster response and emotional management
can prepare IT professionals for high-stress situations better. ... Remember
that disaster preparedness is not a one-time effort — it requires continuous
monitoring, testing, and adaptation to protect valuable data. When
disaster strikes and data is lost, the first step is to create a new and
improved information security plan.
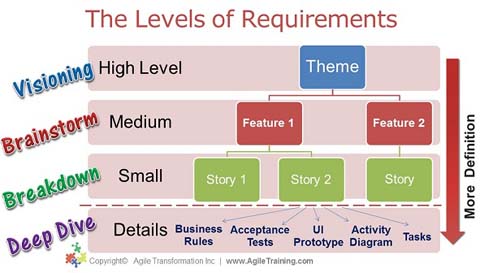
Four Levels of Agile Requirements

Visioning: This is the initial step of gathering requirements. The goal is to
help identify all the Themes and some features desired. This exercise begins
to define the scope of what is expected. Brainstorming: The goal of this step
is to identify all the features and stories desired. The key here is Breadth
First, Depth Later. So instead of discussing the details of each feature and
story, our main goal is to FIND all the features and stories. Breakdown: The
goal of this step to break down and slice the stories that are still too large
(EPICs) into smaller chunks. You probably have already done a lot of slicing
during brainstorming, but as you comb your backlog, the team will realize that
some stories are still too large to be completed within an iteration. Slicing
stories is an art and I will dedicate an entire blog to it! Deep Dive: This is
the step everyone wants to jump into right away! Yes, finally, let’s talk
about the details. What will be on the screen, what are the exact business
rules and how will we test them, what will the detailed process look like,
what are the tasks we need to get done to complete this story.
Dynamic Availability: Protocol-Based Assurances
The distinctive feature of proof-based consensus protocols is the fact that the
protocol continues to function even when there is only one miner. Therefore
miner nodes are free to leave and re-enter the competition at any time. Thus,
the protocol maintains availability even under undesirable network conditions.
To deal with cases where there are multiple leaders (concurrent solvers of the
puzzle), honest nodes follow a simple rule: select the ledger with the highest
number of blocks (i.e., the longest chain). In cases where chains have equal
lengths, pick the one that you witnessed the earliest. Note that, in the given
scenario, there is no way to determine whether there is a set of adversaries
that are processing a parallel ledger without informing the rest of the network
until their ledger becomes longer than the chain of the benevolent node. When
they have a longer chain, they reveal their chain, waiting for the rest of the
network to adapt to it, thus effectively ignoring all transactions that were in
the neglected blocks. Due to this, one can never be sure whether a transaction
is irreversible.
Are firms using mergers and acquisitions to inherit talent?

“I don’t think there’ll be an explosion in the number of acquisitions over the
year ahead, but the people and team acquisition element will play a bigger role
than in the past,” she says. “Technology is moving so fast that if you acquire a
team already working well together on bleeding-edge technology, you can be up
and running from day one.” But purchasing a business to get hold of talent is
one thing. Holding onto that talent to deliver on the hoped-for value from the
acquisition is quite another. The problem here is that if employees are unhappy
with the move, feel uncertain about the future, or cannot see any post-deal
career progression opportunities, they will simply vote with their feet. ... A
key problem with the way many M&A transactions are conducted though, he
believes, is that “people tend to come last on the priority list after financing
and geography” - even though “you’re asking them to do the equivalent of move
home, which because the decision isn’t theirs, can feel threatening”. But
Robbins warns: “You fundamentally need to retain people, skills and capabilities
if the deal is going to be a success. The business depends on two things - its
customers and its staff, and if you’re not giving them what they want, it’s not
going to go well.”
Why the Future for Enterprise Success Has to be Agile
Agile solutions enable enterprises to mitigate risks and reduce project
failures, gaining a competitive edge and seize new opportunities in the digital
age. Through iterative development and continuous feedback cycles, organizations
can identify and address potential issues early on. This piece-by-piece approach
minimizes the likelihood of costly mistakes and allows for corrections and
updates in real-time, ensuring successful project delivery. Working in an Agile
way also means that enterprises can be better prepared for the hype points in
technology, such as the boom of generative AI this year. Agile enterprises are
much better positioned to react and readjust their offerings in real time,
addressing the interests of their market, than those with lengthy, drawn-out
development timelines. This isn’t to say that Agile enterprises aren’t planning
ahead, but instead that they follow a test-and-learn approach, with their plans
being flexible and malleable to the ebbs and flows of the market.
Developer Empowerment Via Platform Engineering, Self-Service Tooling

“As a developer the way we build, test and deploy has gotten more complex,”
Medina said, in her role play as a developer, lamenting her loss of autonomy in
this time of public cloud, serverless workloads and Kubernetes. “Unfortunately
that means that, as a developer, if I want to have access to the things that I
need when I want them, I’m at the mercy of other teams to bring things up for
me. I’m at the mercy of the platform engineering team and I hate waiting for
people to do things for me,” she said. Indeed a platform engineering team never
is short on backlog items. But often they are stuck performing the operations
role so much that they aren’t able to build those golden paths and automation.
“OK, as platform engineers, we have the keys to the so-called cloud kingdom,
but, listen, it’s not all about you. It’s not all about DevEx. We also have to
maintain reliable systems. And it’s too much work and we are super stressed. We
are at the point where we are drowning in Jira tickets,” Villela replied,
wearing the hat of a platform engineer.
Understanding OWASP’s Bill of Material Maturity Model: Not all SBOMs are created equal

Much as with other industry efforts such as zero trust, the journey towards
establishing widespread mature BOMs with sufficient detail and depth will be
just that — a journey. That said, resources such as OWASP's SBOM Guide and the
BOM Maturity Model can serve as great tools that organizations, software
suppliers and consumers can use to mature their implementation of SBOMs and
ensure they are providing sufficient insight and details to be used in
activities such as software asset inventory, vulnerability management and
software supply chain security. ... While the journey may seem daunting, the
alternative is continuing the historical status quo of blind software
consumption with limited transparency and insight into the software we are
consuming, its lineage, who's been involved in it and what has occurred to it
along the way. We wouldn't settle for this level of opaque risky consumption in
other industries such as food and pharmaceuticals and with software increasingly
driving nearly every aspect of society, we shouldn't settle for a lack of
transparency here either.
Quote for the day:
"Difficulties strengthen the mind, as
labor does the body." -- Seneca
No comments:
Post a Comment