From Risk to Resilience: Safeguarding BFSI Against Increasing Threats

As financial transactions increasingly migrate to digital platforms,
safeguarding sensitive data and systems has become the linchpin for maintaining
trust and stability in the industry. Customer trust forms the bedrock of any
successful financial institution. With the advent of digital banking and the
proliferation of online transactions, customers expect their financial data to
be treated with the utmost confidentiality and security. A single breach can
erode trust irreparably, leading to customer attrition and reputational damage.
To uphold trust, BFSI organizations must adopt a proactive cybersecurity
posture. This entails not only implementing robust security measures but also
fostering a culture of cybersecurity awareness among employees and customers
alike. ... Converged IAM represents a paradigm shift in cybersecurity strategy.
It combines traditional IAM, which manages user identities and access to
resources, with Identity Governance and Administration (IGA), which ensures
compliance with internal policies and external regulations. This convergence
empowers organizations to have a unified view of user identities and their
associated access rights, thereby bolstering security measures.
Innovation in data centers: Navigating challenges and embracing sustainability
Navigating the challenge of finding solutions that meet all constraints is a
constant endeavour in the data center industry. Daily operations involve
continuous optimization efforts, where sustainability and cost-effectiveness
are pivotal considerations. Contrary to common perception, sustainable
solutions are not invariably more expensive; their cost-effectiveness depends
on the thorough assessment of environmental implications. Consider the
approach the industry has taken to battery technology optimization as an
example. Traditionally, lead batteries have been a standard industry solution.
However, exploring new technologies, such as lithium-ion batteries, introduces
a diverse range of options. While these batteries may be more intricate and
expensive in the production phase, a holistic lifecycle analysis reveals their
extended service life and lower total cost of ownership. This emphasises the
need to evaluate innovation not only in terms of initial costs but also in
terms of environmental impact and the overall project lifecycle.
Rise of the cyber CPA: What it means for CISOs

The biggest value-add these new talents are likely to deliver is in helping
CISOs sell security programs more effectively. "CISOs are not known to speak
in [terms of] ROI effectively, at least not in the practical ROI issues lines
of business executives care about. And after hearing these ineffective
arguments for years, many CFOs are eventually not listening," Yigal Rechtman,
managing partner of Rechtman Consulting, a New Jersey-based compliance and
forensic accounting firm, tells CSO. Even if the new cyber accountants don't
immediately deliver better ROI arguments, argues Phil Neray, the VP of cyber
defense security at Gem Security, their financial approach and different
mindsets might prove quite valuable. "Fighting our cyber adversaries requires
having different approaches and different viewpoints and different
worldviews," he tells CSO. "Therefore, having a diversity of perspectives on
your security team is going to make your team stronger. And these cyber
accountants might do just that."
Why it’s the perfect time to reflect on your software update policy
The foundation of a sound software update policy begins with thorough
pre-work. This involves setting the groundwork for delivering successful
updates, creating an inventory of devices, documenting baseline
configurations, and understanding the applications that are critical to
business operations. Organizations must establish baseline configurations and
communicate the requisite standards to users. A comprehensive inventory of all
devices used for work, including BYOD and unmanaged devices, is essential.
This also encompasses documenting the end of support for devices being phased
out, noting the critical business applications in use, and understanding which
devices and users depend on them. Identifying devices that are no longer
receiving security updates yet access critical applications should be a
priority. Similarly, sufficient staff must be allocated to the help desks to
cope with increased queries during update rollouts. Organizations should also
prepare a diverse group of informed early adopters and testers from across the
business spectrum to ensure that feedback is timely and representative.

It’s easy to predict a rosy future but far harder to deliver it. Gates can
gush that “agents will be able to help with virtually any activity and any
area of life,” all within five years, but for anyone who has actually used
things like Midjourney to edit images, the results tend to be really bad, and
not merely in terms of quality. I tried to make Mario Bros. characters out of
my peers at work and discovered that Caucasians fared better than Asians. ...
“The key to understanding the real threat of prompt injection is to understand
that AI models are deeply, incredibly gullible by design,” notes Simon
Willison. Willison is one of the most expert and enthusiastic proponents of
AI’s potential for software development (and general use), but he’s also
unwilling to pull punches on where it needs to improve: “I don’t know how to
build it securely! And these holes aren’t hypothetical, they’re a huge blocker
on us shipping a lot of this stuff.” The problem is that the LLMs believe
everything they read, as it were. By design, they ingest content and respond
to prompts. They don’t know how to tell the difference between a good prompt
and a bad one.
Scaling SRE Teams
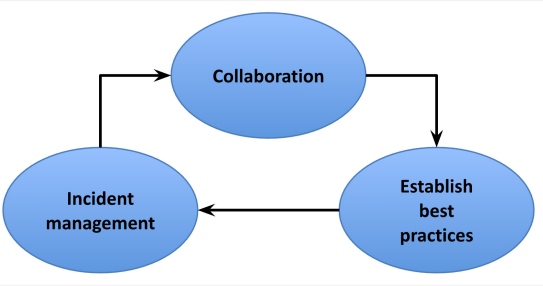
Scaling may come naturally if you do the right things in the right order.
First, you must identify what your current state is in terms of
infrastructure. How well do you understand the systems? Determine existing SRE
processes that need improvement. For the SRE processes that are necessary but
are not employed yet, find the tools and the metrics necessary to start.
Collaborate with the appropriate stakeholders, use feedback, iterate, and
improve. ... SLOs set clear, achievable goals for the team and provide a
measurable way to assess the reliability of a service. By defining specific
targets for uptime, latency, or error rates, SRE teams can objectively
evaluate whether the system is meeting the desired standards of performance.
Using specific targets, a team can prioritize their efforts and focus on areas
that need improvement, thus fostering a culture of accountability and
continuous improvement. Error budgets provide a mechanism for managing risk
and making trade-offs between reliability and innovation.
IT staff augmentation pros and cons

IT staff augmentation does have aspects that organisations will need to
consider before they decide to adopt it. James suggests there can be an impact
on workplace culture, which is often overlooked by organisations. “Certain
contractors, particularly those who frequently work for the same company or
who are contracted on a longer-term basis, will ingratiate themselves into the
fabric and culture of a team, while others simply want to get in, get their
work done and get out,” says James. “This could affect internal staff,
employee relations and damage company culture.” Temporary team members could
also feel left out and be less motivated than in-house employees, suggests
Martin Hartley, group CCO of emagine Consulting, which can cause issues if
they then decide to leave. “If you put the time into bringing someone into
your team and they don’t work out, businesses are forced to repeat the process
and go back out to the market to find a person with the right skills to
replace that role, which takes time,” he warns. There can also be legal issues
to think about.
10 things keeping IT leaders up at night

Many CIOs are troubled by a similar, related issue — a lack of full knowledge
of and visibility into what they have in their IT environments. “It’s not
knowing what you don’t know,” says Laura Hemenway, president, founder, and
principle of Paradigm Solutions, which supports large enterprise-wide
transformations. Many IT departments lack strong documentation around their
code, processes, and systems, says Hemenway, who also serves as a fractional
CIO and is a leader with the Arizona SIM chapter. Additionally, they don’t
know all the places where their organization’s data lives, who touches it, and
why. “CIOs went through so much so quickly in the past few years, that there
is no transformation project that’s not full of data unknowns, process gaps,
broken interfaces, or expired programs,” she says, calling them “all ticking
time bombs.” “And unless CIOs take the time to create a solid foundation, this
is going to be pulling at them, rolling around in the back of their head,” she
says.
How To Prepare Your Organization for AI’s Impact on Data Processes and Products

In many ways, the advanced data literacy trend is connected to the growth of
AI technologies. However, beyond the need for users to understand the breadth
and power of AI, advanced data literacy requires users know the related
terminologies, KPIs, and metrics connected with AI. Data literacy is not just
about how data is consumed. It's about how it is classified within your data
ecosystem. You should focus on the literacy needs of each user and train them
to understand the parts of your data ecosystem they will need to access to
contribute to AI product development. You must implement a solid,
comprehensive framework that informs when and how you roll out data literacy
programs in the various departments and teams in your organization. ... You
will also need a compliance strategy that incorporates all the latest
requirements and includes processes for implementation. The best way to ensure
this is through a dedicated data governance tool. The tool should be
configured to ensure that only verified users can access specific data assets
and that data is only made available for usage according to compliance
regulations.
Unlocking Business Growth: A Strategiv Approach To Tackling Technical Debt

Tech debt is like a time bomb ticking within an organisation. While short-term
solutions may work at first, they often crumble over time, causing costly
rework and inefficiencies. A series of trade-offs and technical workarounds
begin to compromise the long-term health of an organisation’s technological
infrastructure. Although it is distinct from obsolescence or depreciation, its
consequences are far-reaching: loss of systemic intelligence, compromised
operational advantage and ineffective use of capital. In the simplest terms,
it causes organisations to pay 20-40% to manage this inefficiency; it also
consumes as much as 30% of the IT team’s talent. ... The first step is to
reframe tech debt as a component of modernisation. This pivot refocuses the
organisations on a clear and shared vision for modernisation efforts. It is an
opportunity for candid executive conversations to assess the existing tech
debt and strategies for the future. Step two gets to the business benefits of
modernisation. These extend beyond the IT department, so the effort to support
and manage modernisation does as well.
Quote for the day:
When the sum of the whole is greater
than the sum of the parts that's the power of teamwork --
Gorden Tredgold
No comments:
Post a Comment