Mika becomes world's first robot CEO
)
In the era where many workers are worrying about artificial intelligence (AI)
replacing their jobs, one company has announced that it is hiring the first
humanoid robot chief executive officer (CEO). Dictador, a spirit brand based in
Colombia’s Cartagena, has gone viral for appointing Mika, who is manifested as a
robot. Mika is a research project between Hanson Robotics and Dictador. It has
been customised to represent company value. Hanson Robotics also created Sophia,
the popular humanoid robot. ... At a recent event, Mika said, “My presence on
this stage is purely symbolic. In reality, conferring an honorary professor
title upon me is a tribute to the greatness of the human mind in which the idea
of artificial intelligence was born. It is also a recognition of the courage and
open-mindedness of the owner of Dictador, who entrusted his company to a humble
spokesperson with a processor instead of a heart.” Emphasising on how she is
better than current CEO’s including Musk and Zuckerberg, she said, “In reality
the notion of two powerful tech bosses having a cage fight is not a solution for
improving the efficiency of their platforms”.
Four Recommendations to Improve the Cyber Resilience Act
Policymakers must take a more proportionate, risk-based approach to determining
the risk level of a product with digital elements and offer greater certainty
for manufacturers to ascertain if a product is a critical one. While the
Commission’s original proposal categorised every product in several broad
categories as critical, the co-legislators have now the opportunity to take a
more sophisticated approach. We recommend leveraging the Council’s risked-based
approach with some key amendments, outlined here. ... it is crucial that the
reporting obligations are aligned with the NIS 2 Directive to streamline
reporting requirements and to avoid an unmanageable reporting burden for
manufacturers and responsible authorities. This means that reporting under
should be made to the CSIRTs under a single distributed reporting platform, and
the incident reporting on security incidents should only concern “significant
incidents”, as outlined in the European Parliament’s text.
What is a digital transformation strategy? Everything you need to know

At its most basic level, a DX strategy is the use of digital technologies to
create or reimagine how customers are served and how work gets done. A
well-thought-out and well-crafted digital transformation strategy ensures an
organization correctly identifies what products, services and work need to be
created or reimagined to remain competitive. For nonprofits or government
agencies, this might mean effectively and efficiently delivering on their
missions. ... A thoughtful DX strategy also focuses the organization's
attention, said Kamales Lardi, author of The Human Side of Digital Business
Transformation and CEO of Lardi & Partner Consulting. More specifically, it
focuses the organization on the most pressing digital initiatives -- those that
deliver value toward meeting its enterprise-wide goals. Lardi said this approach
keeps teams from pursuing initiatives that introduce new technologies without
understanding how they'll deliver value or implementing transformation projects
that only help segments of the enterprise.
SolarWinds Fires Back at SEC Fraud Charges

“We categorically deny those allegations,” SolarWinds’ blog post said. “The
company had appropriate controls in place before SUNBURST. The SEC misleadingly
quotes snippets of documents and conversations out of context to patch together
a false narrative about our security posture.” SolarWinds’ blog post details
what it says are false claims that the attack exploited a VPN vulnerability.
Other technical issues regarding the companies’ compliance with National
Institute of Standards and Technology (NIST) cybersecurity standards framework
(CSF) are also defended in the post. “The SEC is mixing apples and oranges,
underscoring its lack of cybersecurity experience,” the blog post charged. “…
the SEC fundamentally misunderstands what it means to follow the NIST CSF.”
However much of the SEC’s complaint focuses on Brown’s alleged mishandling of
controls that led to the breach. SEC contends that Brown in 2018 and 2019 stated
"the current state of security leaves us in a very vulnerable state for our
critical assets," and that "access and privilege to critical systems/data is
inappropriate."
Software Architecture Fundamentals: Building the Foundations of Robust Systems

Solutions architecture is the bridge between business requirements and software
solutions. Architects in this domain transform business needs into comprehensive
software designs, often through diagrammatic representations. They also evaluate
the commercial impacts of various technology choices. Software architecture, the
centerpiece of our discussion, is closely aligned with software development. It
not only impacts the structural composition of software but also influences the
organization’s structure. Software architects play a pivotal role in translating
business objectives into concrete software components and their
responsibilities, all while ensuring the system’s healthy evolution over time.
... In a distributed architecture, systems must adopt self-preservation
mechanisms:Avoid overloading a failing system. Excessive requests to a
struggling system can exacerbate the situation. Recognize that a slow
system is often worse than an offline system in terms of user experience. A
system should have a way to assess its health.
Building resilience-focused organizations
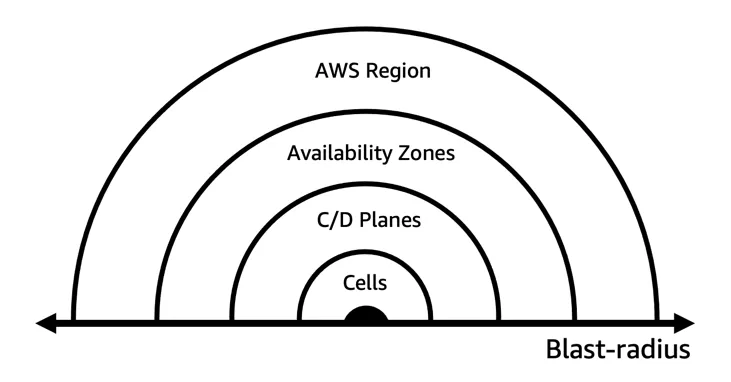
Arguably, the most important aspect of building resilient software system is
automation. It effectively reduces human error, speeds up repetitive tasks, and
guarantees consistent configurations. Through the automation of deployment,
monitoring, and scaling processes, software systems can quickly adapt to
evolving conditions and recover from failures more efficiently. In order to
automate build commands, Amazon created a centralized, hosted build system
called Brazil. The main functions of Brazil are compiling, versioning, and
dependency management, with a focus on build reproducibility. Brazil executes a
series of commands to generate artifacts that can be stored and then deployed.
To deploy these artifacts, Apollo was created. Apollo was developed to reliably
deploy a specified set of software artifacts across a fleet of instances.
Developers define the process for a single host, and Apollo coordinates that
update across the entire fleet of hosts. Developers could simply push-deploy
their application to development, staging, and production environments. No
logging into the host, no commands to run.
What Are Data Sharing Agreements and Why Are They Important?

Before establishing data sharing agreements, it is crucial to have a clear
understanding of their purpose and scope. These agreements serve as legal
documents that outline the terms, conditions, and responsibilities of all
parties involved in sharing data. By comprehending the purpose and scope,
organizations can ensure that they establish agreements that effectively protect
their interests and meet their objectives. The purpose of data sharing
agreements is multifaceted. ... Several key factors must be considered: Data
protection laws: Organizations must comply with data protection laws that govern
the collection, storage, and sharing of personal information. Intellectual
property rights: Data sharing agreements should address ownership rights of the
shared data, including any intellectual property rights associated with it.
Clear provisions on how the data can be used, reproduced, or modified should be
included. Confidentiality and security: Agreements should outline measures to
protect the confidentiality and security of shared data. This includes
provisions for encryption, access controls, breach notification procedures, and
liability for any breaches.
Cyberattack Forces San Diego Hospital to Divert Patients
The attack on Tri-City Medical is among a rash of similarly disruptive
ransomware and other cyber incidents that have been relentlessly hitting
healthcare sector entities, including regional hospitals, in recent years,
months and weeks. That includes an October ransomware attack on five hospitals
in Ontario, Canada, and their shared IT services provider, which has been
disrupting patient care at the facilities for several weeks and for which
recovery work is expected to last into mid-December (see: Ontario Hospitals
Expect Monthlong Ransomware Recovery). The Canadian hospitals have been
directing many patients, including some cancer patients who need radiology
treatment, to seek medical care elsewhere (see: 5 Ontario Hospitals Still
Reeling From Ransomware Attack). A study released in January by the Ponemon
Institute surveying 579 healthcare technology and security leaders says that
patient care diversions due to ransomware are on the rise.
ther facilities,
up from 65% the year before.
Sure, real-time data is now 'democratized,' but it's only a start

"With platforms taking complexity away from the individual user or engineer,
it has accelerated adoption across the industry. Innovation such as SQL
support, help make it democratized and provide ease of access to the vast
majority rather than a select few." ... Many companies' infrastructures aren't
ready, and neither are the organizations themselves. "Some yet to understand
or see the value of real-time while others are all-in, with solutions that
were designed for streaming throughout the organization," says Raikmo.
"Combining datasets in motion with advanced techniques such as watermarking
and windowing, is not a trivial matter. It requires correlating multiple
streams, combining the data in memory and producing merged stateful result
sets, at enterprise scale and resilience." The good news is not every bit of
data needs to be streaming or delivered in real time. "Organizations often
fall into the trap of investing in resources to make every data point they
visualize be in real time, even when it is not necessary," Jayaprakash points
out. "However, this approach can lead to exorbitant costs and become
unsustainable."
AI is the future of cybersecurity. This is how to adopt it securely

Used effectively, AI can help prevent vulnerabilities from being written in
the first place—radically transforming the security experience. AI provides
context for potential vulnerabilities and secure code suggestions from the
start (though please still test AI-produced code). These capabilities enable
developers to write more secure code in real time and finally realize the true
promise of “shift left.” This is revolutionary. Traditionally, “shift left”
typically meant getting security feedback after you’ve brought your idea to
code, but before deploying it to production. But with AI, security is truly
built in, not bolted on. There’s no further way to “shift left” than doing so
in the very place where your developers are bringing their ideas to code, with
their AI pair programmer helping them along the way. It’s an exciting new era
where generative AI will be on the front line of cyber defense. However, it’s
also important to note that, in the same way that AI won’t replace developers,
AI won’t replace the need for security teams. We’re not at Level 5
self-driving just yet.
Quote for the day:
"Nobody can go back and start a new
beginning, but anyone can start today and make a new beginning." --
Maria Robinson
No comments:
Post a Comment