Achieve Defense-in-Depth in Multi-Cloud Environments

Many organizations are adopting log-based solutions (from endpoint to perimeter
security), which is a good first step, but logs can be bypassed or disabled.
Even worse, hackers can manipulate logs to give the appearance that “everything
is fine,” when in fact, they are moving between users, resources and
exfiltration. The solution to this problem is to normalize visibility across the
locations where your organization’s data lives – from the cloud to on-prem, and
data centers. Knowing that IT and Security teams rely on logs makes them
attractive targets for hackers today. However, taking a defense-in-depth
approach versus logs alone is now critical to ensuring that every single entry
point to your organization is secure. Network intelligence plays a huge role in
gaining visibility – it is the only way to ensure visibility into all of the
data in motion across your entire infrastructure and prevent risks. ... Just
like cloud infrastructure management is a shared responsibility within the
organization, so must enterprise security including data security be a shared
responsibility.
A Serverless-First Mindset in an Evolving Landscape
A serverless-first mindset is no doubt beneficial in a number of ways, but some
businesses may have reservations in terms of the potential for vendor lock-in,
the security offered by the cloud provider, existing sunk costs and other issues
in debugging and development environments. However, even among the most
serverless-adverse, this mindset can provide benefits to a select part of an
organisation. When looking at a bank’s operations for example, the continued
uptime of the underlying network infrastructure is crucial for database access,
and with a serverless-first mindset, employees have the flexibility to develop
consumer-facing apps and other solutions as consumer demand increases. While the
maintenance of a traditional network infrastructure is crucial for uptime of the
underlying database, with a serverless approach they have the freedom to
implement an agile mindset with consumer-facing apps and technologies as demand
grows. Agile and serverless strategies typically go hand-in-hand, and both can
encourage quick development, modification and adaptation.
IT talent: The 3 C's for life/work balance

Compensation and benefits are not just lifestyle issues. Although these have
virtually nothing to do with how much we enjoy our time at work or how far and
fast we advance our careers, they carry a lot of psychological value in our
culture because they feed ego and self-esteem. Few people who love their job,
have great career prospects, work for a wonderful boss, and have a short commute
will move simply for the money. Conversely, many are looking to leave
high-paying jobs because their boss is a jerk, the commute is too long, or their
skills are outdated. Many candidates initially cite compensation as their top
criterion to make a move. Still, I have yet to meet a candidate who would accept
a position sight unseen without knowing specific details of the job’s other C's.
Big money or great benefits have never made a bad job good.
Compensation comes to mind first because it is tangible, measurable, and
has psychological power, but underlying its number-one ranking is the assumption
that all the other criteria are met. Like everything else, compensation and
benefits for a specific role are determined by an ever-changing marketplace.
Extortion Economics: Ransomware's New Business Model
This industrialization of cybercrime has created specialized roles in the RaaS
economy. When companies experience a breach, multiple cybercriminals are often
involved at different stages of the intrusion. These threat actors can gain
access by purchasing RaaS kits off the Dark Web, consisting of customer service
support, bundled offers, user reviews, forums, and other features. Ransomware
attacks are customized based on target network configurations, even if the
ransomware payload is the same. They can take the form of data exfiltration and
other impacts. Because of the interconnected nature of the cybercriminal
economy, seemingly unrelated intrusions can build upon each other. For example,
infostealer malware steals passwords and cookies. These attacks are often viewed
as less serious, but cybercriminals can sell these passwords to enable other,
more devastating attacks. However, these attacks follow a common template. First
comes initial access via malware infection or exploitation of a vulnerability.
Then credential theft is used to elevate privileges and move laterally.
7 Microservice Design Patterns To Use
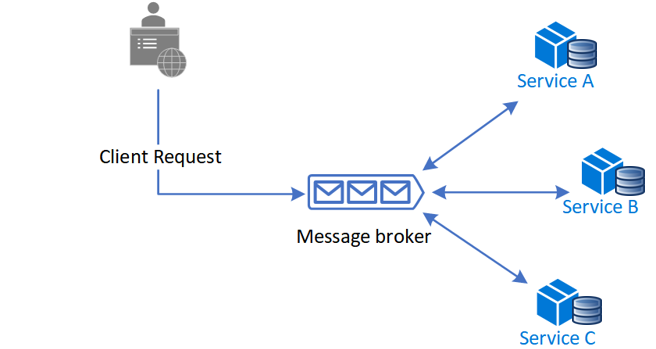
Saga pattern - This microservice design pattern provides transaction
management using a sequence of local transactions. Each operation part of a saga
guarantees that all operations are complete, or that the corresponding
compensation transactions are run to undo the previously done work. Furthermore,
in Saga, a compensating transaction should be retriable and idempotent. The two
principles ensure that transactions can be managed without manual intervention.
The pattern is also a way of managing data consistency across microservices in
distributed transaction instances. ... Event Sourcing - Event sourcing
defines an approach to handling data operations driven by a sequence of events,
each of which is recorded in an append-only store. The app code sends a series
of events that describe every action that happened on the data to the event
store. Typically, the event store publishes these events so consumers can be
notified and handle them if required. For instance, consumers could initiate
tasks that apply the events operations to other systems or do any other action
associated needed to complete an operation.
Enterprises embrace SD-WAN but miss benefits of integrated approach to security

When asked to list the challenges they faced when taking a do-it-yourself (DIY)
approach to SD-WAN, respondents cited difficulties related to hiring and
retaining a skilled in-house workforce, keeping up with technology developments
and the ability to negotiate favourable terms with technology vendors. “Now that
SD-WAN has matured and has been widely adopted, the complexity of deployments
has grown, challenging enterprises on multiple fronts and compromising their
ability to realise the full benefits of the technology,” said James Eibisch,
research director, European infrastructure and telecoms, at IDC, commenting on
the study. “Enterprises are increasingly reliant on the resources and expertise
of a managed service provider to ensure they deploy SD-WAN in a way best suited
to their meet their organisations’ objectives. Security approaches like secure
access service edge (SASE) that combine the benefits of SD-WAN with zero-trust
network access and content filtering features are well poised to dominate the
next phase of SD-WAN enhancements as enterprises continue to enable the cloud IT
model and a hybrid workforce,” he added.
Quantum computing: Should it be on IT’s strategic roadmap?

Quantum computing is a nascent field. Few companies are planning to purchase
quantum computers, but there are companies that are starting to use them for
competitive advantage. For this reason alone, quantum computing should have a
place on IT strategic roadmaps. Financial services institutions like banks and
brokerage houses are beginning to experiment with quantum computing as a way to
process large volumes of financial transactions quicker. Quantum computing can
also be used for financial risk analysis, as financial services companies are
using quantum computing for fraud detection. Quantum computing can be used to
determine worldwide supply chain risks such as weather, strikes and political
unrest, with an eye toward eliminating supply chain bottlenecks before they
happen. Pharmaceutical companies are experimenting with quantum computing as a
way to assess the viability of new drug combinations and their beneficial and
adverse effects on humans. The goal is to reduce R&D costs and speed new
products to market. They are also to customize drugs to each individual
patient’s situation.
Big Tech Layoffs: A Flood of Talent vs the Hiring Crisis

There has been a sea change in the prospects certain big tech players
anticipated would continue to buoy their sector. Sachin Gupta, CEO of
HackerEarth, says many big tech and social media platforms saw explosive growth
when the pandemic changed spending patterns and drove moves to work remotely and
conduct more activities online. “What the businesses started thinking was this
was going to last forever, which is very natural,” he says. It is very difficult
to be in the midst of such a wave, he says, and then predict that it would not
continue. The reasons behind the recent layoffs and firings differ, of course.
Meta’s troubles include not seeing expected traction -- such as its exploration
of the metaverse. Meanwhile, Twitter is in the throws of a regime change that
has been acrimonious for at least some of the rank and file of the company,
which has seen sweeping layoffs, resignations, and outright firings of personnel
new CEO Elon Musk no longer wanted to darken the company’s door -- office doors
that Musk abruptly ordered to be shut (temporarily) and locked last week even to
remaining employees.
Creating an SRE Practice: Why and How
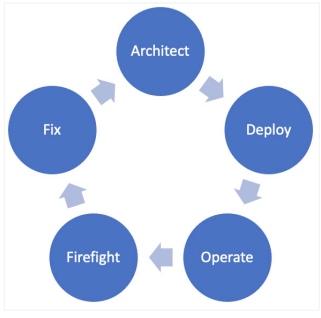
The most important first step is to adopt the SRE philosophies mentioned in the
previous section. The one that will likely have the fastest payoff is to strive
to eliminate toil. CI/CD can do this very well, so it is a good starting point.
If you don't have a robust monitoring or observability system, that should also
be a priority so that firefighting for your team is easier. ... You can't boil
the ocean. Everyone will not magically become SREs overnight. What you can do is
provide resources to your team (some are listed at the end of this article) and
set clear expectations and a clear roadmap to how you will go from your current
state to your desired state. A good way to start this process is to consider
migrating your legacy monitoring to observability. For most organizations, this
involves instrumenting their applications to emit metrics, traces, and logs to a
centralized system that can use AI to identify root causes and pinpoint issues
faster. The recommended approach to instrument applications is using
OpenTelemetry, a CNCFsupported open-source project that ensures you retain
ownership of your data and that your team learns transferable skills.
The Challenge of Cognitive Load in Platform Engineering
You must never forget that you are building products designed to delight their
customers - your product development teams. Anything that prevents developers
from smoothly using your platform, whether a flaw in API usability or a gap in
documentation, is a threat to the successful realisation of the business value
of the platform. With this lens of cognitive load theory, delight becomes a
means of qualifying the cognitive burden the platform is removing from the
development teams and their work to accomplish their tasks. The main focus of
the platform team, as described by Kennedy, is "on providing “developer delight”
whilst avoiding technical bloat and not falling into the trap of building a
platform that doesn’t meet developer needs and is not adopted." She continues by
noting the importance of paved paths, also known as Golden Paths: By offering
Golden Paths to developers, platform teams can encourage them to use the
services and tools that are preferred by the business.
Quote for the day:
"Leadership is familiar, but not well
understood." -- Gerald Weinberg
No comments:
Post a Comment