5 ways to avoid IT purchasing regrets

When it comes to technology purchases, another regret can be not moving fast
enough. Merim Becirovic, managing director of global IT and enterprise
architecture at Accenture, says his clients often wonder whether they’re falling
behind. “With the level of technology maturity today, it’s a lot easier to
make good decisions and not regret them. But what I do hear are questions around
how to get things done faster,” he says. “We’re getting more capabilities all
the time, but it’s all moving so quickly that it’s getting harder to keep
up.” A lag can mean missed opportunities, Becirovic says, which can produce
a should-have-done-better reproach. “It’s ‘I wish I had known, I wish I had
done,’” he adds. Becirovic advises CIOs on how to avoid such scenarios,
saying they should make technology decisions based on what will add value; shift
to the public cloud to create the agility needed to keep pace with and benefit
from the quickening pace of IT innovation; and update IT governance practices
tailored to overseeing a cloud environment with its consumption-based fees.
5 digital transformation metrics to measure success in 2023

If money (whether earned or saved) is the first pillar of most business metrics,
then time is another. That could be time spent or saved (more on that in a
moment), but it’s also in the sense of pure speed. "Time to market should be one
of the most critical digital transformation metrics right now for enterprises
across industries,” says Skye Chalmers, CEO of Image Relay. “The market impact
of a digital transformation project is all about its speed: If you don’t cross
the finish line first with compelling new customer [or] employee experiences or
other digital modernization initiatives, your competitors will.” So while an
overall digital transformation strategy may not have an endpoint, per se, the
goals or milestones that comprise that strategy should have some time-based
measurement. And from Chalmers’ point of view, the speed with which you can
deliver should be a key factor in decision-making and measurement. Focusing on
the time-to-market metric “will directly improve an enterprise’s competitive
position and standing with customers,” Chalmers says.
More Organizations Are Being Rejected for Cyber Insurance — What Can Leaders Do?

Before soliciting cyber insurance quotes, examine several areas of your
network security to understand what vulnerabilities exist. Insurers will do
just that, so anticipating gaps in your infrastructure, software, and systems
will provide you with a clearer idea of what your company needs. Start with
your enterprise network. Who has access and to what degree? Every person who
has access to your network provides an attack vector, increasing the
possibility of an attacker accessing more data through lateral movement. If an
outside agent can gain entry to your network, that person or bot can harvest
the most privileged credentials and move between servers and throughout the
storage infrastructure while continually exploiting valuable sensitive data.
That’s why most insurance audits consider privilege sprawl to be among the top
risks. It happens when special rights to a system have been granted to too
many people. It impacts the cost of premiums and could even lead to a loss of
coverage. Public cloud assets also present an opportunity for a strike. Is
access to that information secure?
Retirees Must Have These Four Key Components To Make A Winning Side Hustle
Since when does everything always go as planned? Spoiler Alert: It never does.
There’s even a saying for this: “Into each life, a little rain must fall.” And
when those rain clouds do appear, what do successful entrepreneurs do? They
don’t pack up their gear and head for shelter. No, they plant their feet
firmly into the (muddy) ground and start selling umbrellas. “When you study
success and read extensively about entrepreneurs, you realize that successful
people come from a variety of backgrounds and circumstances, but they have one
thing in common—they consistently do the work,” says Case Lane, Founder of
Ready Entrepreneur in Los Angeles. “The only talent needed is knowing you can
make that commitment to keep working to ensure business success.”
Entrepreneurs don’t fear change (see above); they see it as an opportunity. “I
knew how to solve a problem that many people were experiencing, and I knew I
could help those people,” says Chane Steiner, CEO of Crediful in Scottsdale,
Arizona.
Top 6 security risks associated with industrial IoT

Device hijacking is one of the common security challenges of IIoT. It can
occur when the IoT sensor or endpoint is hijacked. This can lead to serious
data breaches depending on the intelligence of the sensors as well as the
number of devices the sensors are connected to. Sensor breaches or hijacks can
easily expose your sensors to malware, enabling the hacker to have control of
the endpoint device. With this level of control, hackers can run the
manufacturing processes as they wish. ... IIoT deals with many physical
endpoint devices that can be stolen if not protected from prying eyes. This
situation can pose a security risk to any organization if these devices are
used to store sensitive information. Organizations with endpoint devices in
great use can make arrangements to ensure that these devices are protected,
but storing critical data in them can still raise safety concerns due to the
growing number of endpoint attacks. For organizations to minimize the risk
associated with device theft, it’s expedient to avoid storing sensitive
information on endpoint devices. Instead, they should use cloud-based
infrastructure to store critical information.
Cloud security starts with zero trust
Generally speaking, the best way for an organization to approach zero trust is
for security teams to take the mindset that the network is already compromised
and develop security protocols from there. With this in mind, when
implementing zero trust into a cloud environment, organizations must first
perform a threat assessment to see where their biggest vulnerabilities lie.
Zero trust strategy requires an inventory of every single item in a company’s
portfolio, including a list of who and what should and should not be trusted.
Additionally, organizations must develop a strong understanding of their
current workflows and create a well-maintained inventory of all the company’s
assets. After conducting a thorough threat assessment and developing an
inventory of key company information, security controls must be specifically
designed to address any threats identified during the threat assessment to
tailor the zero trust strategy around them. The nature of zero trust is
inherently complex due to the significant steps that a company has to take to
achieve a true zero trust atmosphere, and this is something that more
businesses should take into account.
How to Not Screw Up Your Product Strategy
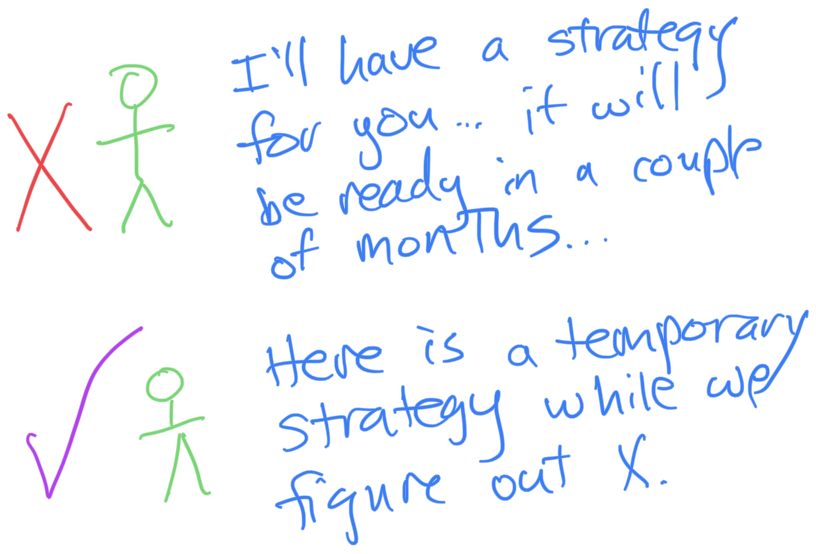
Creating the strategy also requires influencing and collaborating with many people. All of these interactions require time to get people on the same page, discuss disagreements, and incorporate improvements or changes. Finally, your market can change quickly. New competitors can emerge, technologies change, and customer feedback can shift. These all can result in changes in perspective or emphasis, which can further slow down putting together a product strategy. And finally, even after you’ve done all the hard work putting the strategy together, you have a lot of work to do communicating that strategy and getting people to understand it. This also takes a lot of time. The end result of all these steps is that a common failure mode is “the product strategy is coming." My recommendation is to always have a working product strategy. Because strategy work takes time, you shouldn’t make people wait for it. If you don’t have a real strategy, start with a temporary, short-term strategy, based on your best thinking at the moment.
Why Microsegmentation is Critical for Securing CI/CD
While cloud-native application development has many benefits, traditional
network architectures and security practices cannot keep up with DevOps
practices like CI/CD. Microsegmentation reduces network risk and prevents
lateral movement by isolating environments and applications. However, it can
be a challenge to implement segmentation in a cloud-native environment.
Typical network security teams use a centralized approach with one SecOps team
responsible for all security management. For example, some networks have
ticket-based approval systems where the central team reviews each request
based on access policies. However, this system is slow and prone to human
error. Teams can use DevOps methods to operationalize microsegmentation,
implementing policy as code. You can also leverage a microsegmentation
solution that helps automate and secure the process. The security team
enforces basic segmentation policies, while application owners create more
granular policies. This decentralized security approach preserves the agility
of DevOps.
Data Strategy: Synthetic Data and Other Tech for AI's Next Phase

Synthetic data is one of several AI technologies identified by Forrester as
less well known but having the power to unlock significant new capabilities.
Others on the list are transformer networks, reinforcement learning, federated
learning and causal inference. Curran explains that transformer networks use
deep learning to accurately summarize large corpuses of text. “They allow for
folks like myself to basically create a pretty concise slide based off of a
piece of research I’ve written,” he says. “I already use AI-generated images
in probably 90% of my presentations at this point in time.” The same base
technology of transformer networks and large language models can be used to
generate code for enterprise applications, Curran says. Reinforcement learning
allows tests of many actions in simulated environments, enabling a large
number of micro-experiments that can then be used for constructing models to
optimize objectives or constraints, according to Forrester. ... Such a
simulation would let you account for your big order, the cost of shutting down
at peak season, and other factors in your decision of whether to take that
piece of equipment down for maintenance.
Smart office trends to watch

A growing number of office buildings now have an effective Building Management
System (BMS). Ideally this will be combined with energy generation and storage
and water management systems, which can deliver huge cost, resource and
emissions savings, but a good BMS is a good start. It can optimise energy use
through smart lighting and temperature systems, controlled by software which
draws information from Internet of Things (IoT) or Radio Frequency
Identification (RFID) sensors throughout the building. Energy and cost savings
are also improved by smart LED lighting, controlled by sensors that ensure it
is only used as and when needed. Providers of BMS and related solutions
include Smarter Technologies, which uses RFID sensors to monitor energy and
water use, temperature, humidity, air quality, room or desk occupancy and even
whether bins need emptying. SP Digital’s GET Control system offers IoT and
AI-based temperature control, dividing open plan offices into microzones,
through which air flow is regulated based on occupancy and both conditions
inside and ambient weather conditions outside the building.
Quote for the day:
"In simplest terms, a leader is one
who knows where he wants to go, and gets up, and goes." --
John Erksine
No comments:
Post a Comment