4 Ways AI Should Be Playing a Role in Your DX Strategy
 The real value of AI lies in the data that it is able to process and analyze.
“The backbone of AI and ML is data and in order to get real business value out
of AI and ML, you need deep and broad data that covers your entire digital
experience ecosystem. Once that data is harnessed and correlated, AI and ML can
be a game changer for the enterprise with deep, contextual, and automated
insight into your digital experience. AI and ML can then be used to proactively
identify investments that will provide the most ROI, accelerate time intensive
efforts like root cause analysis, and reduce the workload on your IT team by
automating repetitive tasks.” Daniel Fallmann, CEO at Mindbreeze, an insight
engine provider, shared his thoughts on how AI is used to analyze data to drive
business process transformation. “...you can learn if a customer really needs a
specific product or service by using AI to review data from the past, such as
published press releases, subscriptions, form information on your website, and
more,” Fallmann said. Like Malloy, Fallmann reiterates the value of diving deep
and consolidating disparate data in order to reap the benefits of holistic
views.
The real value of AI lies in the data that it is able to process and analyze.
“The backbone of AI and ML is data and in order to get real business value out
of AI and ML, you need deep and broad data that covers your entire digital
experience ecosystem. Once that data is harnessed and correlated, AI and ML can
be a game changer for the enterprise with deep, contextual, and automated
insight into your digital experience. AI and ML can then be used to proactively
identify investments that will provide the most ROI, accelerate time intensive
efforts like root cause analysis, and reduce the workload on your IT team by
automating repetitive tasks.” Daniel Fallmann, CEO at Mindbreeze, an insight
engine provider, shared his thoughts on how AI is used to analyze data to drive
business process transformation. “...you can learn if a customer really needs a
specific product or service by using AI to review data from the past, such as
published press releases, subscriptions, form information on your website, and
more,” Fallmann said. Like Malloy, Fallmann reiterates the value of diving deep
and consolidating disparate data in order to reap the benefits of holistic
views.Tech Has Advanced Rapidly—And Cybersecurity Needs To Catch Up
 Data is any business’s most critical asset. Like the valuable and confidential
items in your home, it’s not easily retrieved once it’s in the wrong hands.
Ultimately, when it comes to cyberattacks, it will always be a case of not “if”
but “when” an SME will suffer a breach or fall foul to an attack. SMEs must
focus on understanding their risks, getting the basics right and creating a
strong “human firewall” as the foundation of their cybersecurity strategy. Ask
yourself: “Am I protecting my employees, my customers and my reputation? Am I
protecting my data and assets?” Starting here will help SMEs understand the
risks and focus on the basics that will have the biggest impact. This could
consist of installing phishing protection and firewalls across all devices,
investing in authentication methods or keeping software and anti-malware up to
date. Invest in training to ensure all employees have a true understanding of
the cybersecurity risks the business faces, including how to identify phishing
scams and what the process is on reporting them. Finally, keep security top of
mind, and don’t underestimate its importance.
Data is any business’s most critical asset. Like the valuable and confidential
items in your home, it’s not easily retrieved once it’s in the wrong hands.
Ultimately, when it comes to cyberattacks, it will always be a case of not “if”
but “when” an SME will suffer a breach or fall foul to an attack. SMEs must
focus on understanding their risks, getting the basics right and creating a
strong “human firewall” as the foundation of their cybersecurity strategy. Ask
yourself: “Am I protecting my employees, my customers and my reputation? Am I
protecting my data and assets?” Starting here will help SMEs understand the
risks and focus on the basics that will have the biggest impact. This could
consist of installing phishing protection and firewalls across all devices,
investing in authentication methods or keeping software and anti-malware up to
date. Invest in training to ensure all employees have a true understanding of
the cybersecurity risks the business faces, including how to identify phishing
scams and what the process is on reporting them. Finally, keep security top of
mind, and don’t underestimate its importance.Microsoft Office Users Warned on New Malware-Protection Bypass
 “The malware arrives through a phishing email containing a Microsoft Word
document as an attachment. When the document is opened and macros are enabled,
the Word document, in turn, downloads and opens another password-protected
Microsoft Excel document,” researchers wrote. Next, VBA-based instruction
embedded in the Word document reads a specially crafted Excel spreadsheet cell
to create a macro. That macro populates an additional cell in the same XLS
document with an additional VBA macro, which disables Office defenses. “Once the
macros are written and ready, the Word document sets the policy in the registry
to ‘Disable Excel Macro Warning,’ and invokes the malicious macro function from
the Excel file. The Excel file now downloads the Zloader payload. The Zloader
payload is then executed using rundll32.exe,” researchers said. Because
Microsoft Office automatically disables macros, the attackers attempt to trick
recipients of the email to enable them with a message appearing inside the Word
document. “This document created in previous version of Microsoft Office Word.
To view or edit this document, please click ‘Enable editing’ button on the top
bar, and then click ‘Enable content’,” the message reads.
“The malware arrives through a phishing email containing a Microsoft Word
document as an attachment. When the document is opened and macros are enabled,
the Word document, in turn, downloads and opens another password-protected
Microsoft Excel document,” researchers wrote. Next, VBA-based instruction
embedded in the Word document reads a specially crafted Excel spreadsheet cell
to create a macro. That macro populates an additional cell in the same XLS
document with an additional VBA macro, which disables Office defenses. “Once the
macros are written and ready, the Word document sets the policy in the registry
to ‘Disable Excel Macro Warning,’ and invokes the malicious macro function from
the Excel file. The Excel file now downloads the Zloader payload. The Zloader
payload is then executed using rundll32.exe,” researchers said. Because
Microsoft Office automatically disables macros, the attackers attempt to trick
recipients of the email to enable them with a message appearing inside the Word
document. “This document created in previous version of Microsoft Office Word.
To view or edit this document, please click ‘Enable editing’ button on the top
bar, and then click ‘Enable content’,” the message reads.How cybersecurity is getting AI wrong
 Unknown unknowns are so prevalent in cyberspace that many service providers
preach to their customers to build their security strategy on the assumption
that they’ve already been breached. The challenge for AI models emanates from
the fact that these unknown unknowns, or blind spots, are seamlessly
incorporated into the models’ training datasets and therefore attain a stamp of
approval and might not raise any alarms from AI-based security controls. For
example, some security vendors combine a slate of user attributes to create a
personalized baseline of a user’s behavior and determine the expected
permissible deviations from this baseline. The premise is that these vendors can
identify an existing norm that should serve as reference point for their
security models. However, this assumption might not hold water. For example, an
undiscovered malware may already reside in the customer’s system, existing
security controls may suffer from coverage gaps, or unsuspecting users may
already be suffering from an ongoing account takeover. Errors: It would not be
brazen to assume that even staple security-related training datasets are
probably laced with inaccuracies and misrepresentations.
Unknown unknowns are so prevalent in cyberspace that many service providers
preach to their customers to build their security strategy on the assumption
that they’ve already been breached. The challenge for AI models emanates from
the fact that these unknown unknowns, or blind spots, are seamlessly
incorporated into the models’ training datasets and therefore attain a stamp of
approval and might not raise any alarms from AI-based security controls. For
example, some security vendors combine a slate of user attributes to create a
personalized baseline of a user’s behavior and determine the expected
permissible deviations from this baseline. The premise is that these vendors can
identify an existing norm that should serve as reference point for their
security models. However, this assumption might not hold water. For example, an
undiscovered malware may already reside in the customer’s system, existing
security controls may suffer from coverage gaps, or unsuspecting users may
already be suffering from an ongoing account takeover. Errors: It would not be
brazen to assume that even staple security-related training datasets are
probably laced with inaccuracies and misrepresentations. What are the most common cybersecurity challenges SMEs face today?
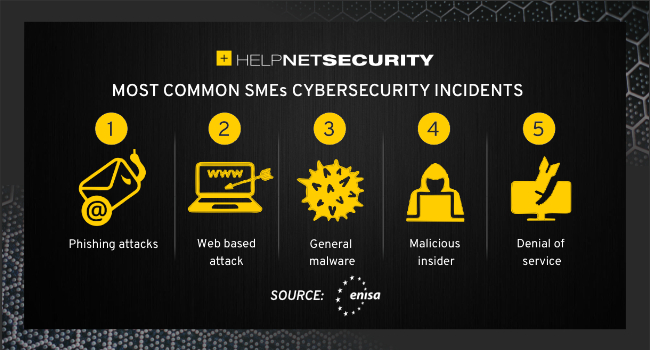 The ENISA report provides advice for SMEs to successfully cope with
cybersecurity challenges, particularly those resulting from the COVID-19
pandemic. With the current crisis, traditional businesses had to resort to
technologies such as QR codes or contactless payments they had never used
before. Although SMEs have turned to such new technologies to maintain their
business, they often failed to increase their security in relation to these new
systems. Research and real-life experience show that well prepared organizations
deal with cyber incidents in a much more efficient way than those failing to
plan or lacking the capabilities they need to address cyber threats correctly.
Juhan Lepassaar, EU Agency for Cybersecurity Executive Director said: “SMEs
cybersecurity and support is at the forefront of the EU’s cybersecurity strategy
for the digital decade and the Agency is fully dedicated to support the SME
community in improving their resilience to successfully transform digitally.” In
addition to the report, ENISA also publishes the Cybersecurity Guide for SMEs:
“12 steps to securing your business”.
The ENISA report provides advice for SMEs to successfully cope with
cybersecurity challenges, particularly those resulting from the COVID-19
pandemic. With the current crisis, traditional businesses had to resort to
technologies such as QR codes or contactless payments they had never used
before. Although SMEs have turned to such new technologies to maintain their
business, they often failed to increase their security in relation to these new
systems. Research and real-life experience show that well prepared organizations
deal with cyber incidents in a much more efficient way than those failing to
plan or lacking the capabilities they need to address cyber threats correctly.
Juhan Lepassaar, EU Agency for Cybersecurity Executive Director said: “SMEs
cybersecurity and support is at the forefront of the EU’s cybersecurity strategy
for the digital decade and the Agency is fully dedicated to support the SME
community in improving their resilience to successfully transform digitally.” In
addition to the report, ENISA also publishes the Cybersecurity Guide for SMEs:
“12 steps to securing your business”. Your dev team lead is not controlling enough
When I first got promoted to team lead I was highly controlling. I literally did most of my team's work for them. I worked seventeen hours a day six days a week to ensure every single task was completed to my exact specification. The people that worked for me were unhappy (some actively disliked me personally) but we got results that the CEO cared about so it went unnoticed. And I was good at managing up, so I actually got promoted for this behavior! I was in my early twenties and motivated by the wrong things (power, money, and, of course, control). I look back on the period with embarrassment and I've actually apologized to many of the people who worked for me back then. ... when I realized micro-management was wrong, I naturally swung the pendulum in the exact opposite direction. I told myself I was hiring smart people and I should leave them alone. I'm good at hiring so it kind of worked. But, again, the people who worked for me suffered -- this time in a way that they noticed much less. Good people actually want feedback! It's not good for their work to go unchallenged because then it's harder to improve.Cyber security too often takes back seat in C-Suite
 Chief information security officers are studying these threats daily and are
in the best position to communicate what they’ve learned to decision makers.
But too often, Hamilton said, CISOs have trouble translating their technical
findings for board room audiences. While the top executives could often use
with a little more training on the ins and outs of technological threats,
information security executives also need to do a much better job of reading
the room. CISOs must present their information in terms of risk to the bottom
line. “Scary Russian cyber buffer overflow SQL injection ... nobody cares,”
Hamilton said. ... “It’s more about being able to say something like, ‘we have
1 million records meeting the definition of personally-identifiable
information, and we know that they’re worth about $200 apiece if you’ve got to
clean up a data breach. That’s $200 million in potential liability. Can I have
$50,000 for controls to reduce that risk in half?” While the knee-jerk
reaction with cyber security may be to name an organization’s best technical
expert the CISO, that can end up backfiring unless that person is willing to
sharpen their understanding of the business they’re trying to protect.
Chief information security officers are studying these threats daily and are
in the best position to communicate what they’ve learned to decision makers.
But too often, Hamilton said, CISOs have trouble translating their technical
findings for board room audiences. While the top executives could often use
with a little more training on the ins and outs of technological threats,
information security executives also need to do a much better job of reading
the room. CISOs must present their information in terms of risk to the bottom
line. “Scary Russian cyber buffer overflow SQL injection ... nobody cares,”
Hamilton said. ... “It’s more about being able to say something like, ‘we have
1 million records meeting the definition of personally-identifiable
information, and we know that they’re worth about $200 apiece if you’ve got to
clean up a data breach. That’s $200 million in potential liability. Can I have
$50,000 for controls to reduce that risk in half?” While the knee-jerk
reaction with cyber security may be to name an organization’s best technical
expert the CISO, that can end up backfiring unless that person is willing to
sharpen their understanding of the business they’re trying to protect.The Rise of the ML Engineer
 Just fifty years ago, machine learning was a new idea. Today it’s an integral
part of society, helping people do everything from driving cars and finding
jobs to getting loans and receiving novel medical treatments. When we think
about what the next 50 years of ML will look like, it’s impossible to predict.
New, unforeseen advancements in everything from chips and infrastructure to
data sources and model observability have the power to change the trajectory
of the industry almost overnight. That said, we know that the long run is just
a collection of short runs, and in the current run, there is an emerging set
of tools and capabilities that are becoming standards for nearly every ML
initiative. We have written about the 3 most important ML tools: a feature
Store, a model store, and an evaluation store. Click here for a deeper
dive. Beyond the tools that power ML initiatives, the roles that shape
data teams are also rapidly evolving. As we outline in our ML ecosystem
whitepaper, the machine learning workflow can be broken into three stages —
data preparation, model building, and production and at every step of the
process, the skills and requirements are different:
Just fifty years ago, machine learning was a new idea. Today it’s an integral
part of society, helping people do everything from driving cars and finding
jobs to getting loans and receiving novel medical treatments. When we think
about what the next 50 years of ML will look like, it’s impossible to predict.
New, unforeseen advancements in everything from chips and infrastructure to
data sources and model observability have the power to change the trajectory
of the industry almost overnight. That said, we know that the long run is just
a collection of short runs, and in the current run, there is an emerging set
of tools and capabilities that are becoming standards for nearly every ML
initiative. We have written about the 3 most important ML tools: a feature
Store, a model store, and an evaluation store. Click here for a deeper
dive. Beyond the tools that power ML initiatives, the roles that shape
data teams are also rapidly evolving. As we outline in our ML ecosystem
whitepaper, the machine learning workflow can be broken into three stages —
data preparation, model building, and production and at every step of the
process, the skills and requirements are different:Cloud computing's destiny: operating as a single global computer, enabled by serverless
 For all the progress of what's happening on cloud, we have to "get to the
point where we get the cloud to work as if it was a single infinitely powerful
computer," says Nagpurkar. Right now, there are too many obstacles in the way,
she adds. "Think about the simplicity of just working on your laptop. You have
a common operating system tools you you're familiar with. And, most
importantly, you're spending most of your time working on code. Developing on
the cloud is far from that. You have to understand the nuances of all the
cloud providers -- there's AWS, Azure, GCP, IBM, and private clouds. You have
to provision cloud resources that might take a while to get online. And you
have to worry about things like security, compliance, resiliency, scalability,
and cost efficiency. It's just a lot of complexity." Proprietary software
stacks from different vendors "not only add to all this complexity but they
stifle innovation," she says. "Key software abstractions start with the
operating system. Linux as the operating system for the data center era
unleashed this proliferation of software, including virtualization
technologies like containers. That ushered in the cloud era."
For all the progress of what's happening on cloud, we have to "get to the
point where we get the cloud to work as if it was a single infinitely powerful
computer," says Nagpurkar. Right now, there are too many obstacles in the way,
she adds. "Think about the simplicity of just working on your laptop. You have
a common operating system tools you you're familiar with. And, most
importantly, you're spending most of your time working on code. Developing on
the cloud is far from that. You have to understand the nuances of all the
cloud providers -- there's AWS, Azure, GCP, IBM, and private clouds. You have
to provision cloud resources that might take a while to get online. And you
have to worry about things like security, compliance, resiliency, scalability,
and cost efficiency. It's just a lot of complexity." Proprietary software
stacks from different vendors "not only add to all this complexity but they
stifle innovation," she says. "Key software abstractions start with the
operating system. Linux as the operating system for the data center era
unleashed this proliferation of software, including virtualization
technologies like containers. That ushered in the cloud era."
'Barely able to keep up': America's cyberwarriors are spread thin by attacks
 Cybersecurity professionals can barely keep up despite significant industry
growth in recent years — and plenty more money is pouring in. That money is
chasing a limited talent pool, with almost a half-million cybersecurity jobs
unfilled, according to CyberSeek, a project that tracks the industry and is
sponsored by the federal National Institute of Standards and Technology. The
government is also on a massive hiring spree, with the Department of Homeland
Security racing to fill more than 2,000 cybersecurity jobs. Secretary
Alejandro Mayorkas called it a victory last week that it had recently
onboarded almost 300 new employees and offered jobs to 500 more. It’s a
problem that some in the cybersecurity industry are hoping to address even in
the years to come. The National Cryptologic Foundation, a nonprofit affiliate
for the National Security Agency, offers free educational materials to middle
schools. The Center for Infrastructure Assurance and Security at the
University of Texas at San Antonio has produced free cybersecurity educational
games for students in an effort to inspire young people to consider careers in
the industry.
Cybersecurity professionals can barely keep up despite significant industry
growth in recent years — and plenty more money is pouring in. That money is
chasing a limited talent pool, with almost a half-million cybersecurity jobs
unfilled, according to CyberSeek, a project that tracks the industry and is
sponsored by the federal National Institute of Standards and Technology. The
government is also on a massive hiring spree, with the Department of Homeland
Security racing to fill more than 2,000 cybersecurity jobs. Secretary
Alejandro Mayorkas called it a victory last week that it had recently
onboarded almost 300 new employees and offered jobs to 500 more. It’s a
problem that some in the cybersecurity industry are hoping to address even in
the years to come. The National Cryptologic Foundation, a nonprofit affiliate
for the National Security Agency, offers free educational materials to middle
schools. The Center for Infrastructure Assurance and Security at the
University of Texas at San Antonio has produced free cybersecurity educational
games for students in an effort to inspire young people to consider careers in
the industry.Quote for the day:
"The great leaders have always stage-managed their effects." -- Charles de Gaulle
No comments:
Post a Comment