IT leadership: 3 ways to enable continuous improvement

"If technical leadership has one job, it is to tend to that socio-technical
system so that team members can spend as much time as possible on priorities
that move the business forward, not on trying to navigate or fix internal
systems. Pay really close attention to those feedback loops and make them tight.
Invest in the work where it makes sense – not just trying to fix everything and
make it perfect, but look for where you can get really big wins and not have to
reinvent the wheel. “It turns out we have the benefit of knowing all the science
that even just five to 10 years ago, we didn’t have. Read Accelerate, for
example. There used to be a lot of ‘I think’ statements, and while it worked, it
was very ‘cult-y’ and it was very based on osmosis. If you had been lucky enough
to work with one of the best engineers in the world, then you kind of knew this
stuff – it was all just contagious. Now, we have this freely available data, and
we should be using it.” ... “If your job is to align people, motivate, and
understand the friction points, you really have to walk a mile in their shoes,
and you have to find the outcomes that fix those problems,” says GitHub’s Dana
Lawson.
New SaaS Security Report Dives into the Concerns and Plans of CISOs in 2021

For years, security professionals have recognized the need to enhance SaaS
security. However, the exponential adoption of Software-as-a-Service (SaaS)
applications over 2020 turned slow-burning embers into a raging fire.
Organizations manage anywhere from thirty-five to more than a hundred
applications. From collaboration tools like Slack and Microsoft Teams to
mission-critical applications like SAP and Salesforce, SaaS applications act as
the foundation of the modern enterprise. 2020 created an urgent need for
security solutions that mitigate SaaS misconfiguration risks. Recognizing the
importance of SaaS security, Gartner named a new category, SaaS Security Posture
Management (SSPM), to distinguish solutions that have the capabilities to offer
a continuous assessment of security risks arising from a SaaS application's
deployment. To understand how security teams are currently dealing with their
SaaS security posture and what their main concerns are, Adaptive Shield, a
leading SSPM solution, commissioned an independent survey of 300 InfoSecurity
professionals from North America and Western Europe, in companies ranging from
500 to more than 10,000 employees.
How Enterprise Architects Can Evolve from Order Takers to Trusted Advisors

The value of strong interpersonal skills can’t be overstated when it comes to
building trust with executives. Persuasive advisors are those that are confident
and clever in how they communicate their ideas to others. That being said, there
are also tools EAs can leverage to appeal to executives and secure buy-in for
projects. Though they may propose and finance IT change projects, many
executives are focused on other areas of business besides IT logistics. As such,
EAs won’t get their ideas across by using heavily technical jargon or by
presenting complex spaghetti models to them. Instead, they need to address
executives’ personal priorities when detailing their proposed solutions: are
they looking to cut costs? Make their data stores more compliant? These are the
value points that EAs need to address when presenting their ideas. With a
platform that enables EAs to manipulate their organizational data to support
different viewpoints, EAs can speak to executives’ and stakeholders’ personal
interests, instead of turning them away.
Java on Visual Studio Code Update – June 2021
Remote Development has always been a popular feature in Visual Studio Code and
it allows developers to use a container for a full-feature development
environment. For the upcoming quarters, we are working on supporting more Java
versions as well as Spring framework in the containers so developers can access
those technology in their remote development scenarios. We have just released
support for Java 16 in the remote dev container which is shown in the later
sections of this post. In addition, Gtihub Codespaces is a configurable online
development environment that allows you to develop entirely in cloud. Visual
Studio Code plays a critical role in Codespaces as it provides the essential
code editing experience. In terms of Java, the team is working on providing the
support for Java language extensions in Codespaces so Java developers can find
all Java related tools they need. For details on how to request access for
Codespaces, please follow the official Codespaces documentation here. In terms
of testing, Visual Studio Code Java is targeting to adopt the new Testing APIs
introduced recently.
OpsRamp’s Ciaran Byrne on managing multicloud and hybrid environments

The biggest challenge is dealing with the complexity. It’s not just a matter of
cloud and on-premises; you have networks, servers, storage, virtual
environments, containers, and applications that you have to discover and collect
metrics on, and those are running in both cloud and on-premises environments. In
most cases, you’ll be managing these mixed environments with multiple monitoring
tools, leading to tool sprawl. You’ll have to make sense of large volumes of
data coming from these mixed environments managed by a diverse toolset. The
environments that are mixed will likely have inter-dependencies which may make
it difficult to be aware of and troubleshoot issues. Troubleshooting may also be
more complicated, as each of the environments will have their own nuances for
investigating and resolving issues that require operators and admins to have a
broad range of skills. Once you’ve “solved” the problem of monitoring these
hybrid environments, you have to understand which parts of this hybrid
infrastructure are supporting which application services.
How RPA-As-A-Service Can Power The Next Mid-Market Winner

Current RPAaaS offerings, including the solution we offer at AutomationEdge, are
low on code and high on “drag and drop” functionality, making the intuitive user
interfaces open to automation across the enterprise. With an RPAaaS solution
that has plug-ins that connect to the common systems of record in the
enterprise, RPA is no longer an island, but rather a means of intergalactic
travel across the enterprise galaxy. ... Full-blown, on-premise RPA
implementations come with mature governance models, which are unnecessary at the
start of a company’s life. A check-the-box approach to governance that meets all
mandatory legal, financial and accounting requirements is adequate for this
stage of growth. Not all processes need to be run every day; many are run once a
quarter or even annually. Employees can monitor these processes much easier.
Another advantage of RPAaaS is having access to a robust RPAaaS community that
can help developers keep in touch with the latest hacks, patches and previews
that they can then bring into their craft.
Top 10 Chrome Flags you should consider enabling in July 2021

Chrome Flags are basically experimental features that Google is currently
testing on either Chrome OS or the Chrome browser. It’s important to note some
Flags are exclusive to Chrome OS, while others work on Chrome browsers across
Android, iOS, macOS, and Windows. Eventually Flags will be removed as they
become part of either a stable Chrome release, or get absorbed into Chrome
developer tools. Once you enable a Flag, you need to restart your browser (or
restart your machine if you’re on Chrome OS) for the change to take effect. You
should realize that enabling Flags does carry some risk. Not all Flags are
stable and may cause some unintended behavior with your browser or device. It’s
also important to understand that browser-based Flags are not tested for online
security protocols. This means you carry some security risk when conducting
financial transactions online while using untested Chrome Flags. If you run
different versions of Chrome OS or Chrome browser, you can find different Flags
available.
Industrial cybersecurity: How to protect your assets in the digital transformation age
Industrial businesses that embrace transformation and have a holistic view of
cybersecurity are benefitting from diverse technology ecosystem development,
including connected devices, edge control, apps, analytics and cloud services,
which are enhancing business performance at an unprecedented pace. It’s vital
that your organization’s approach to security is part of the organizational
culture – using components that meet recognized standards and include encryption
by default. Security must be integral to the design of any process or operation
and fundamentally baked into the services that support the operation of your
systems and business objectives. The tsunami of risks focused on operating
technology (OT) ranges from the exposure of intellectual property and lost
production systems or data to serious fines and reputational loss. Cybersecurity
is a multi-faceted discipline requiring a proactive approach across the
business. For your business to be best prepared against threats, it’s important
to consider the following elements:
5 Skill Sets A Blockchain Developer Must Have

Data Structure is the first essential skill that a Blockchain programmer should
have. For the advancement and deployment of systems, blockchain engineers must
engage with the data structures skill promptly. The entire Blockchain system is
made up of data structures. Moreover, we can also say that a block is indeed a
data structure. Because of their encapsulating data structure and the public
ledger functioning as the Blockchain, blocks behave as groups of transaction
activities associated with the open register. ... Cryptography is a methodology
for designing procedures and algorithms to prevent a foreign entity from reading
and learning content from personal messages throughout a communication session.
Kryptos and Graphein are two old Greek concepts that mean “disguised” and “to
record,” respectively, are also used in cryptography. ... The potential to view
and collect information across many blockchain systems is known as
interoperability. For instance, if someone sends data to some other blockchain,
will the receiver read, understand, and respond to it with minimal effort?
5 elements of servant leadership
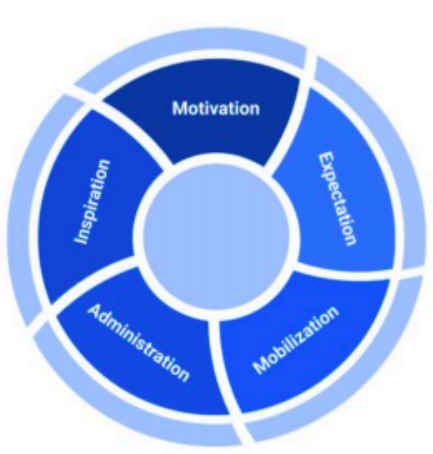
Setting expectations is quite simply clearly defining what is needed from each
individual in the performance of their assigned role. It is all of the what’s
and when’s of the position. In some roles and organizations, it may also
articulate the how’s. Expectations define the goals, activities, and behaviors
that drive the measurable results that the manager is charged with. For
employees, it clarifies their contribution to the organization - both what it is
and what it should be. It represents the outcomes to which they are being held
accountable and enables them to check the objective behaviors or metrics to
which they are held accountable. ... Mobilization is about skills and the
effective application of those skills to drive the team’s mission. Managers have
to ensure that their team is both equipped and deployed to most effectively
contribute to the organization. This includes matching team members’ strengths
with specific tasks or roles and constantly asking if there are other or
alternative contributions that could be made. The most effective managers hold
their directs responsible for skills development by setting a vision for what is
needed, suggesting methods, and making opportunities available.
Quote for the day:
"Leadership is particularly necessary to
ensure ready acceptance of the unfamiliar and that which is contrary to
tradition." -- Cyril Falls
No comments:
Post a Comment