The biggest data science trends in banking

Another rising data science trend within banking is the use of traceable timing
solutions. With timestamping regulations in financial services getting stricter,
and data scientists looking to maintain integrity of assets, these solutions
look to improve the accuracy of time sources. Richard Hoptroff, CTO and
founder of Hoptroff, said: “Network derived and precise traceable timing
solutions are an innovative aide which can be used to bolster data
infrastructure of banks. They are a growing alternative to traditional,
satellite dependant means of achieving time. Network derived time can be used to
optimise trade lifecycle management, improve transaction reporting and inform
strategic decisions. This enables the verification of transactions to become
more efficient and reliable and also opens up the possibility to identify
significant cost savings. “The implications of the Fourth Industrial Revolution
mean that traceable timing solutions are becoming increasingly relevant outside
of financial services – as posited by Brad Casemore, the vice-president of
Datacenter Networks at IDC, ‘Time and time services are more ubiquitous and more
valuable today than many business leaders realise’.”
5 things cybersecurity leaders need to know to make hybrid work safe
Companies need to buy into zero trust, or the philosophy that organizations
should not trust anything inside or outside their network. Even the savviest
internet users are targets for phishing scams and require constant education
to sidestep hackers targeting vulnerabilities. Zero trust can manifest as a
suite of programs to prevent phishing. Web users must keep up-to-date on
common scams, such as suspicious links and misspelled email addresses, to
avoid putting the workplace at risk. Companies can install software to block
downloading external software and monitor how devices can be used.
Cryptographic systems such as two-factor authentication (2FA) could be key to
staying secure, Cerf and Rashid agreed. That could take the form of an app on
a smartphone or a physical cryptographic device. Employers can also apply
these principles to working in the office. There may come a time where the
corporate network is compromised, and it is crucial that security teams assume
their networks could be exposed. Cerf predicts 2021 will bring expanded
internet coverage in rural areas and increased 5G speeds and
capabilities.
Vulnerability in Schneider Electric PLCs allows for undetectable remote takeover

Once leaked, attackers can use the stolen hash to take over the secure
connection that UMAS establishes between the PLC and its managing workstation,
allowing the attacker to reconfigure the PLC without needing to know a
password. Reconfiguration, in turn, allows the attacker to perform remote code
execution attacks, including installation of malware and steps to obfuscate
their presence. Schneider Electric said it applauds security researchers like
Armis and has been working with the company to validate its claims and
determine remediation steps. "Our mutual findings demonstrate that while the
discovered vulnerabilities affect Schneider Electric offers, it is possible to
mitigate the potential impacts by following standard guidance, specific
instructions; and in some cases, the fixes provided by Schneider Electric to
remove the vulnerability," Schneider said in a statement. Industrial control
systems vulnerabilities have been a rising problem in recent years, but it's
important to note that just because PLCs like Schneder's Modicon line are
vulnerable doesn't mean an attacker will have an easy time taking control of
them.
For The First Time, Scientists Have Connected a Superconductor to a Semiconductor
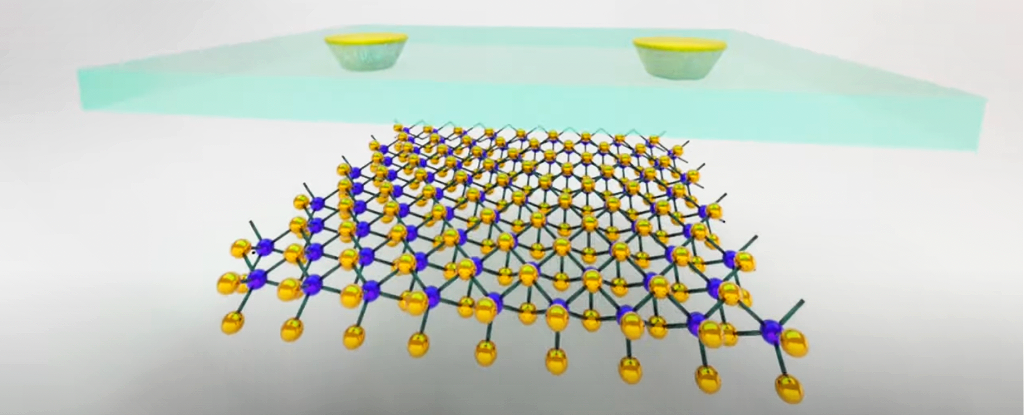
Ultrathin semiconductors like the one used here are currently a hot
investigation topic for researchers: they can be stacked together to form
entirely new synthetic materials known as van der Waals heterostructures.
These structures have a lot of potentially innovative uses, such as being able
to control electron magnetism with electric fields. However, a lot of this
potential is still theoretical, because scientists just don't know what
effects they're going to get yet and what devices they might be able to make.
Which is why succeeding in creating this latest combination is so important.
... Getting this semiconductor-superconductor link together isn't easy – as
you would expect, considering no one has done it before. The semiconductor is
placed in a sandwich, with insulating layers above and below, while holes
etched in the top of the insulating layer provide the electrical contact
access. The superconducting material fills the gaps left by the holes, and the
process is finished inside a nitrogen-filled glove box to protect the finished
system from damage. Remote-controlled micromanipulators are used to complete
the fabrication, under an optical microscope.
Financial services unchained: The ongoing rise of open financial data

Open financial data could put powerful non-bank companies in a stronger
position to become financial-services players. With digital adoption leaping
ahead by years in just several months,4 many ecommerce, tech, and social-media
companies have accumulated a massive lead in customer attention. This opens
the possibility for them to be the first port of call for new financial
products and services to their user bases, similar to what Google now enables
customers to do with its “Plex” product, connected to the Google Pay app.
According to the Google web site, Plex is offered in partnership with 11 banks
and credit unions and includes physical and virtual debit cards, peer-to-peer
payments, and an associated checking account. In Singapore, the government
recently issued banking licenses to five nonbanking players, including the
consumer ecosystem Grab (200 million users in eight countries) and the
consumer internet company Sea. The surge in online activity and digital
behaviors has also opened up new avenues for companies to integrate financial
services directly into customers’ daily activities, such as online shopping
and the management of payments related to cars.
Dutch prosecutor ordered to give evidence on EncroChat hack

The decision is the first time an official has been required to explain the
role of the Netherlands in the operation to hack EncroChat, which has led to
arrests worldwide of hundreds of members of organised crime groups. The Dutch
Public Prosecution Service’s public position is that it was not involved in
the development or deployment of a “software implant” used by the French
Gendarmerie to harvest 120 million messages from the phones, which were
largely used by organised criminal groups. Dutch prosecutors argue that it is
not up to the Dutch courts to assess the legality of the French police
operation to intercept messages from EncroChat, which were subsequently shared
with the Netherlands, the UK, Sweden and other countries. But the claim has
been questioned by defence lawyers in the Netherlands, who point to evidence
from the UK and elsewhere that suggests the Dutch and French Gendarmerie
worked closely together on the operation. A court in Den Bosch ruled last week
that a public prosecutor involved in the Dutch investigation into EncroChat,
codenamed 26Lemont, should give evidence on the Dutch judiciary’s role in the
operation with the French.
Moving away from ReactJs and VueJs on front-end using Clean Architecture

One of the biggest problems when it comes to evolving an application is the
coupling to the UI framework. On the front-end little by little due to the
responsibilities that applications of this type have been gained over time, it
makes more and more sense to develop in a more structured way and the problems
to be solved are very similar to those that exist on other fronts such as
backend or mobile development. There are frameworks like ReactJs and VueJs
that make life easier for us to take on these challenges on the front-end. A
front-end application today is an independent application of the backend in
many cases and therefore needs to have its own architecture. ... Using the UI
framework for what is strictly necessary allows us to better adapt to changes
in future versions of the framework. This is because the code that contains
the application logic, which is the most important part, that changes less
over time, and is the code potentially to be shared between two versions of
the same app as in this example, it’s uncoupled without depending on the UI
framework.
Data Scientists and ML Engineers Are Luxury Employees
First, machine learning and data science are fascinating fields. Mostly
because they sit at the crossroad of computer science, mathematics, and
business understanding. This means that there is way more room for personal
growth. When switching from software engineering to machine learning
engineering, my backyard suddenly tripled in size. I could continue to craft
beautiful and complex systems with my hands (and become the great engineer I
wanted to be) and at the same time satisfy (way more) my intellectual
curiosity. Now every day, I get to learn and sit on the shoulder of giants!
Apart from the interest in the field, another main reason is a bit more
practical. I have spent so much time and energy learning the necessary topics
(think probability, statistics, calculus, linear algebra, distributed
computing, machine learning, deep learning…) that I want this knowledge to
stick in. And we are all humans. Even if you are a genius, if you don’t
practice what you learn, the knowledge goes away. So when your boss asks you
(for the tenth time in a row) to create a piece of software or an analysis
that has nothing to do with machine learning, what is that you think? Are you
happy?
Blockchain 'Immutability' Dispute Sparked by Ethereum Request for Reorg Contract

Conversations and debates concerning blockchain immutability have been taking
place for years, and a fresh new discussion has ignited over a tweet and smart
contract published on Github by the developer Bunny Girl. On July 10, Bunny
Girl explained that the smart contract aims to enhance systematic chain
reorganizations. A blockchain reorganization is a contentious subject and
basically occurs when a chain of recorded blocks is invalidated.
Reorganizations have taken place on various blockchains when a mining entity
or group of miners controls more than 51% of the hashrate. Blockchain
reorganizations force miners (not participating in the reorg) back to a point
where they have to start again from a specific block height. It’s akin to
rolling back a recorded history of transactions and then re-recording them
again, but of course, the new transactions would never be the same as the ones
that were erased. ... The RFR thread was followed by an extremely mixed
reception. “So we just ignoring immutability now?” asked one person in
response to Bunny Girl’s tweetstorm.
IOTA - The Most Accessible DLT Network for NFTs
In recent months, NFTs have been a major talking point among tech heads,
industry experts and the art world. Even traditional, non-industry media has
covered the feverish debate surrounding the possibility of digitally
representing assets on a distributed ledger and trading them as so-called NFTs
on dedicated platforms. NFTs are cryptographic tokens that represent something
unique (or ‘non-fungible’) in digitized form. Virtually anything can be
digitized and represented as an NFT. You can represent and trade digital
assets such as digital artworks, video clips, music or gaming items as NFTs,
as well as physical assets such as real estate, paintings, or vintage cars.
Thanks to the underlying DLT, ownership of an NFT is digitally certified and
can only be changed (either by transferring it or destroying it) by the owner.
Many new use cases are only possible by means of the digitized representation
of digital asset ownership. .., NFTs maintain their uniqueness, which makes
them an excellent solution for digitizing the collectibles market, where there
is proof of ownership and protection from copyright infringement.
Quote for the day:
"The meeting of two personalities is
like the contact of two chemical substances: if there is any reaction, both
are transformed." -- Carl Jung
No comments:
Post a Comment