TSA’s pipeline cybersecurity directive is just a first step experts say
 This new regulation requires that designated pipeline security companies report
cybersecurity incidents to the DHS's Cybersecurity and Infrastructure Security
Agency (CISA) no later than 12 hours after a cybersecurity incident is
identified. The TSA estimates that about 100 companies in the US would fall
under the directive's mandates. Pipeline owners and operators must also
designate a cybersecurity coordinator who is required to be available to TSA and
CISA 24/7 to coordinate cybersecurity practices and address any incidents that
arise. Finally, pipeline owners and operators must "review their current
activities against TSA's recommendations for pipeline cybersecurity to assess
cyber risks, identify any gaps, develop remediation measures, and report the
results to TSA and CISA." Although not appearing anywhere in the directive,
pipeline companies that fail to meet the security requirements would be subject
to financial fines, starting at $7,000 per day, government officials say. ... In
its press release announcing the directive, the TSA said "it is also considering
follow-on mandatory measures that will further support the pipeline industry in
enhancing its cybersecurity and that strengthen the public-private partnership
so critical to the cybersecurity of our homeland."
This new regulation requires that designated pipeline security companies report
cybersecurity incidents to the DHS's Cybersecurity and Infrastructure Security
Agency (CISA) no later than 12 hours after a cybersecurity incident is
identified. The TSA estimates that about 100 companies in the US would fall
under the directive's mandates. Pipeline owners and operators must also
designate a cybersecurity coordinator who is required to be available to TSA and
CISA 24/7 to coordinate cybersecurity practices and address any incidents that
arise. Finally, pipeline owners and operators must "review their current
activities against TSA's recommendations for pipeline cybersecurity to assess
cyber risks, identify any gaps, develop remediation measures, and report the
results to TSA and CISA." Although not appearing anywhere in the directive,
pipeline companies that fail to meet the security requirements would be subject
to financial fines, starting at $7,000 per day, government officials say. ... In
its press release announcing the directive, the TSA said "it is also considering
follow-on mandatory measures that will further support the pipeline industry in
enhancing its cybersecurity and that strengthen the public-private partnership
so critical to the cybersecurity of our homeland."
The Limits to Blockchain Scalability
Telcos back Artificial Intelligence, Internet of Things for 5G in India
 The drivers that may trigger IoT applications, according to him, include low
cost of storage and computing data on the cloud platform, emerging edge
computing trends, falling costs of data, sensors, devices, and availability of
mobile app development platforms. Following the Covid-19 pandemic, IoT is
expected to drive significant transformation in the healthcare sector. "Hospital
drug and waste management, robotic surgery, real-time health monitoring and
diagnostics via IoT will stand to witness increased adoption." Bharti Airtel is
working with the Swedish gear maker Ericsson on aerial drones for security and
surveillance purposes, and dropping of relief material in emergency situations.
Billionaire Mukesh Ambani-owned Reliance Jio together with Korean Samsung
Networks has been working on virtual classrooms, and previously demonstrated
high-definition content streaming. Kochhar feels that bringing futuristic
technologies such as AR and VR to classrooms may redefine education and skilling
of students. "AR and VR require higher bandwidth, lower latency and network
resiliency. ..."
The drivers that may trigger IoT applications, according to him, include low
cost of storage and computing data on the cloud platform, emerging edge
computing trends, falling costs of data, sensors, devices, and availability of
mobile app development platforms. Following the Covid-19 pandemic, IoT is
expected to drive significant transformation in the healthcare sector. "Hospital
drug and waste management, robotic surgery, real-time health monitoring and
diagnostics via IoT will stand to witness increased adoption." Bharti Airtel is
working with the Swedish gear maker Ericsson on aerial drones for security and
surveillance purposes, and dropping of relief material in emergency situations.
Billionaire Mukesh Ambani-owned Reliance Jio together with Korean Samsung
Networks has been working on virtual classrooms, and previously demonstrated
high-definition content streaming. Kochhar feels that bringing futuristic
technologies such as AR and VR to classrooms may redefine education and skilling
of students. "AR and VR require higher bandwidth, lower latency and network
resiliency. ..." Implementing a digital transformation at industrial companies
 Before pursuing digital opportunities, leaders must first develop and align on a
digital vision for their organization, looking at both the overall digital
strategy and value proposition for their companies. They should begin by
assessing their capabilities, estimating the resources required, and
contemplating potential partnerships that could help them achieve their goals.
Other practical issues include the feasibility of the proposed initiatives and
their potential value. The basic question underlying all strategic plans is
this: How can digital help us transform core business processes or generate new
opportunities? When developing the road map, industrial companies should
consider the strategic implications for the incumbent business, including
disruptions to any offline distribution channels as digital sales grow.
Companies should also address the inevitable channel conflicts in the strategic
road map by acknowledging the risks, evaluating the potential impact, and
creating a path forward to mitigate any issues. For instance, companies should
determine what roles they expect the distributors to play with the new digital
channels. Some may decide to eliminate distributors and conduct all business
through e-commerce while others may keep offline and online channels.
Before pursuing digital opportunities, leaders must first develop and align on a
digital vision for their organization, looking at both the overall digital
strategy and value proposition for their companies. They should begin by
assessing their capabilities, estimating the resources required, and
contemplating potential partnerships that could help them achieve their goals.
Other practical issues include the feasibility of the proposed initiatives and
their potential value. The basic question underlying all strategic plans is
this: How can digital help us transform core business processes or generate new
opportunities? When developing the road map, industrial companies should
consider the strategic implications for the incumbent business, including
disruptions to any offline distribution channels as digital sales grow.
Companies should also address the inevitable channel conflicts in the strategic
road map by acknowledging the risks, evaluating the potential impact, and
creating a path forward to mitigate any issues. For instance, companies should
determine what roles they expect the distributors to play with the new digital
channels. Some may decide to eliminate distributors and conduct all business
through e-commerce while others may keep offline and online channels. Can You Build a Machine Learning Model to Monitor Another Model?
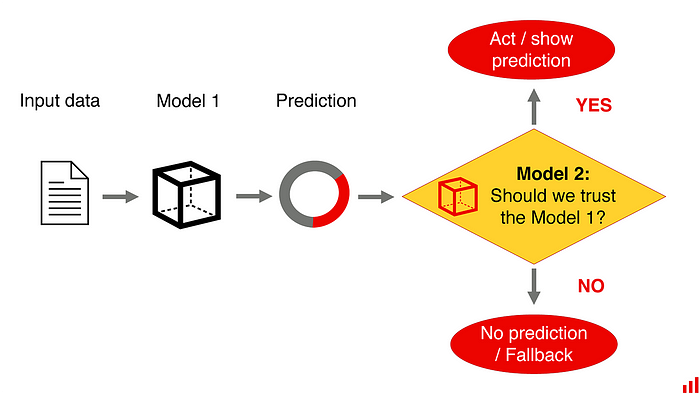 Can you train a machine learning model to predict your model’s mistakes? Nothing
stops you from trying. But chances are, you are better off without it. We’ve
seen this idea suggested more than once. It sounds reasonable on the surface.
Machine learning models make mistakes. Let us take these mistakes and train
another model to predict the missteps of the first one! Sort of a “trust
detector,” based on learnings from how our model did in the past. ... In
regression problems, sometimes you can build a “watchdog” model. This happens
when your original model optimizes the prediction error, taking into account its
sign. If the second “watchdog” model is predicting an absolute error instead, it
might get something more out of the dataset. But here is a thing: if it works,
this does not tell that the model is “wrong” or how to correct it. Instead, it
is an indirect way to evaluate the uncertainty of data inputs. (Here is a whole
paper that explores this in detail). In practice, this returns us to the same
alternative solution. Instead of training the second model, let’s check if the
input data belongs to the same distributions!
Can you train a machine learning model to predict your model’s mistakes? Nothing
stops you from trying. But chances are, you are better off without it. We’ve
seen this idea suggested more than once. It sounds reasonable on the surface.
Machine learning models make mistakes. Let us take these mistakes and train
another model to predict the missteps of the first one! Sort of a “trust
detector,” based on learnings from how our model did in the past. ... In
regression problems, sometimes you can build a “watchdog” model. This happens
when your original model optimizes the prediction error, taking into account its
sign. If the second “watchdog” model is predicting an absolute error instead, it
might get something more out of the dataset. But here is a thing: if it works,
this does not tell that the model is “wrong” or how to correct it. Instead, it
is an indirect way to evaluate the uncertainty of data inputs. (Here is a whole
paper that explores this in detail). In practice, this returns us to the same
alternative solution. Instead of training the second model, let’s check if the
input data belongs to the same distributions!4 robotic process automation project fails to avoid
Blue Prism 7 shifts focus from RPA to programmable digital workers
 “Scaling intelligent automation within the cloud and enabling increased demand
will be the ultimate differentiator in a year of significant growth for the
market,” Blue Prism CEO and chair Jason Kingdon told VentureBeat. While other
RPA vendors have aimed to improve the technical characteristics of RPA
infrastructure, Blue Prism has focused on improving the programmability,
manageability, and integration of RPA infrastructure. Technical infrastructure
efforts are important, as RPA’s original focus on making it easier to simulate
user interaction with applications often incurred infrastructure scaling
liabilities. Focus is shifting, however, as the major RPA vendors explore
different approaches to scaling people’s ability to quickly create new
automations with appropriate guardrails. That is key to Blue Prism’s recent
efforts. A pointed criticism of traditional approaches to RPA — despite what the
name implies — has centered around their focus on automating tasks rather than
processes. “We looked at how to automate the process of programming not just
tasks, but an entire digital workforce end-to-end, and that guided our redesign
of Blue Prism’s platform for V7,” Kingdon said.
“Scaling intelligent automation within the cloud and enabling increased demand
will be the ultimate differentiator in a year of significant growth for the
market,” Blue Prism CEO and chair Jason Kingdon told VentureBeat. While other
RPA vendors have aimed to improve the technical characteristics of RPA
infrastructure, Blue Prism has focused on improving the programmability,
manageability, and integration of RPA infrastructure. Technical infrastructure
efforts are important, as RPA’s original focus on making it easier to simulate
user interaction with applications often incurred infrastructure scaling
liabilities. Focus is shifting, however, as the major RPA vendors explore
different approaches to scaling people’s ability to quickly create new
automations with appropriate guardrails. That is key to Blue Prism’s recent
efforts. A pointed criticism of traditional approaches to RPA — despite what the
name implies — has centered around their focus on automating tasks rather than
processes. “We looked at how to automate the process of programming not just
tasks, but an entire digital workforce end-to-end, and that guided our redesign
of Blue Prism’s platform for V7,” Kingdon said.SolarWinds hackers resurface to attack government agencies and think tanks
 The group behind the infamous SolarWinds hacks is on another cyberattack spree,
this time targeting not just government agencies but others as well. In a report
published Thursday, Microsoft revealed that the threat actor Nobelium launched a
series of attacks this past week against government agencies, think tanks,
consultants, and non-governmental organizations. More than 25% of the victims
were involved in international development, humanitarian and human rights work,
according to Microsoft. Affecting more than 150 different organizations, the
attacks targeted 3,000 separate email accounts. Many of the attacks were blocked
automatically by security software, with Microsoft's Windows Defender catching
the malware used to try to compromise the organizations. Identifying the culprit
as Nobelium, Microsoft pointed out that this is the same group behind the
SolarWinds hack in 2020. Those attacks, which exploited a security hole in a
SolarWinds monitoring tool, hit different government agencies and were deemed to
be sponsored by Russia. Microsoft called the latest incident a continuation of
different information gathering efforts by Nobelium to target government
agencies involved in foreign policy.
The group behind the infamous SolarWinds hacks is on another cyberattack spree,
this time targeting not just government agencies but others as well. In a report
published Thursday, Microsoft revealed that the threat actor Nobelium launched a
series of attacks this past week against government agencies, think tanks,
consultants, and non-governmental organizations. More than 25% of the victims
were involved in international development, humanitarian and human rights work,
according to Microsoft. Affecting more than 150 different organizations, the
attacks targeted 3,000 separate email accounts. Many of the attacks were blocked
automatically by security software, with Microsoft's Windows Defender catching
the malware used to try to compromise the organizations. Identifying the culprit
as Nobelium, Microsoft pointed out that this is the same group behind the
SolarWinds hack in 2020. Those attacks, which exploited a security hole in a
SolarWinds monitoring tool, hit different government agencies and were deemed to
be sponsored by Russia. Microsoft called the latest incident a continuation of
different information gathering efforts by Nobelium to target government
agencies involved in foreign policy.Surviving Automation: It's Now Coming for White-Collar Workers
 Adapting and expanding one’s skillset is one tactic for avoiding redundancy via
automation. “Seek out any training available, either internally — many firms
provide internal training — or via well-regarded sites such as Coursera, Data
Camp, etc.,” Coker of the University of Westminster suggested. Pay attention to
news and developments in your field, he said, and keep your own skills up to
date accordingly. Also, the tools that allow automation to happen must be
created, Edge pointed out. That involves software developers, coders, UI/UX
professionals, yes — but it also requires expertise from those with deep
experience in a given field. One of the best ways of surviving automation in
your field is to find a way to get in front of the people designing automation
software in order to help them do their jobs better, Edge said. “That requires a
little understanding of how software works — but more importantly, to move into
those product design roles, we need to think more deeply about what we do and
why.” Additionally, as companies invest more in digital transformation, there
will be increased demand for professionals with experience in what that looks
like in their particular industries.
Adapting and expanding one’s skillset is one tactic for avoiding redundancy via
automation. “Seek out any training available, either internally — many firms
provide internal training — or via well-regarded sites such as Coursera, Data
Camp, etc.,” Coker of the University of Westminster suggested. Pay attention to
news and developments in your field, he said, and keep your own skills up to
date accordingly. Also, the tools that allow automation to happen must be
created, Edge pointed out. That involves software developers, coders, UI/UX
professionals, yes — but it also requires expertise from those with deep
experience in a given field. One of the best ways of surviving automation in
your field is to find a way to get in front of the people designing automation
software in order to help them do their jobs better, Edge said. “That requires a
little understanding of how software works — but more importantly, to move into
those product design roles, we need to think more deeply about what we do and
why.” Additionally, as companies invest more in digital transformation, there
will be increased demand for professionals with experience in what that looks
like in their particular industries.Building a better you
 A healthy dose of common sense — and humanity — helps when making changes. Grit
and persistence only go so far. Milkman advises that “when you keep hitting a
wall on a particular goal, it’s time to step back, reassess, and think about the
bigger picture instead of making yourself miserable.” Don’t overengineer the
solutions, either. For example, although we know that forming stable routines is
key to habit formation, you must build in sufficient buffers for life events or
hiccups that may make it difficult to follow your plan. Otherwise, you’ll end up
disappointed and less likely to sustain your new behaviors. In one experiment,
those who were rewarded for exercising on a more flexible schedule kept working
out a lot more at other times, too — not only at the time they’d said was most
convenient. In this instance, a more flexible approach wound up embedding a new
behavior. The others, who had agreed to exercise at a fixed time and day,
Milkman writes, transformed from “Routine Rachels” into “Rigid Rachels.” That
is, when events made it impossible to exercise at the regular time, they didn’t
compensate by exercising at other times.
A healthy dose of common sense — and humanity — helps when making changes. Grit
and persistence only go so far. Milkman advises that “when you keep hitting a
wall on a particular goal, it’s time to step back, reassess, and think about the
bigger picture instead of making yourself miserable.” Don’t overengineer the
solutions, either. For example, although we know that forming stable routines is
key to habit formation, you must build in sufficient buffers for life events or
hiccups that may make it difficult to follow your plan. Otherwise, you’ll end up
disappointed and less likely to sustain your new behaviors. In one experiment,
those who were rewarded for exercising on a more flexible schedule kept working
out a lot more at other times, too — not only at the time they’d said was most
convenient. In this instance, a more flexible approach wound up embedding a new
behavior. The others, who had agreed to exercise at a fixed time and day,
Milkman writes, transformed from “Routine Rachels” into “Rigid Rachels.” That
is, when events made it impossible to exercise at the regular time, they didn’t
compensate by exercising at other times.Quote for the day:
"People buy into the leader before they buy into the vision." -- John C. Maxwell
No comments:
Post a Comment