Qualcomm reveals tiny Linux-driven 5G NR chipset for IoT
The 315 5G chipset offers up to a 1.54Gbps data rate for 5G (3GPP Rel 15), while
the 4G mode goes to 400Mbps. Other features include antenna tuning support and a
dual-frequency GNSS location capability. The combination of 7nm technology,
Cortex-A7, and an efficient RF front-end design enables up to 50 percent smaller
modules than existing models, claims Qualcomm. Vanghi also touted the chipset
for its low power consumption and extended life maintenance through 2028 to
2030. The Qualcomm 315 5G IoT Modem-RF “can be easily fitted onto industrial
machines,” said Vanghi. “You can bolt it directly onto the chassis using
existing holes.” The small size will also make it easy for wireless module
manufacturers to upgrade existing 4G modules, said Vanghi, mentioning support
for 35 x 40mm module footprints. “The 315 is a pin-to-pin compatible solution
for LTE legacy modules,” he added. Vanghi noted that the chipset has all the
security features of Qualcomm’s premium 5G chipsets for smartphones, which would
include the Snapdragon X55 5G Modem-RF System. Security features include
hardware-based cryptography, TrustZone, Qualcomm TEE, secure boot, secure
storage and key provisioning, and debug security.
Keeping Technology Change Human
When users can accurately predict their efficiency with a tool, even when that
tool itself is inefficient, they can strongly resist a change. I worked on an
inflight commerce system, and our solution required a series of reconciliation
steps to be taken at the end of a flight. The crew instinctively know how long
this process takes through repetition of the process, and they set aside that
time - at what is generally a very stressful point in the flight. Coming in to
land is when everyone suddenly wants to be out of their seat! Changes to the
software (and hence the process) around reconciliation were always difficult to
achieve buy-in for, because the nervousness around trying something new at such
a critical point in the crew's operational life was always a tough sell. Our
software was one of the multiple tasks taking place at that time, and a change
to one can lead to underperformance in any of the others. Nobody wants
distracted staff on a plane. Changes to software or processes mean a risk to
their ability to deliver predictably to the business, and that could have
catastrophic consequences for a user's role.
The future of the IoT (batteries not required)

When the two technical co-founders looked to expand their startup, they tapped a
collection of their newly minted PhD students who had the expertise of
developing wireless system-on-chip technologies in the lab. Today, Everactive
has expanded into a team of nearly 90 industry veterans and technical experts,
including talented minds like Alice Wang, who joined up with Calhoun and
Wentzloff in 2018 after successful stints with industry giants Texas Instruments
and MediaTek. Another MIT alum, she now serves as VP of hardware for Everactive,
directing both silicon and hardware systems design. “We’re exceptionally proud
of the team that we’ve developed,” says Wentzloff. “I think a large part of why
we continue to succeed is that we’ve done a great job of surrounding our core
technology students with a broad set of talented industry leaders.” Thanks to
their advances in ultra-low-power circuits and wireless communication,
Everactive sells full-stack industrial IoT solutions powered by their always-on
Eversensors, harvesting energy exclusively from the surrounding environment. The
sensors can be deployed at a larger scale than battery-powered devices, and they
cost less to operate.
Can Nanotech Secure IoT Devices From the Inside-Out?

Sowder said that many times, “the challenge with these IoT devices is the
limited compute capability that they have on them. An IP camera can’t run a full
IPS protection suite against traffic to it. It has a job to record video and
send it upstream.” He pointed to the potential solution of nanotechnology:
Specifically, the concept of a nanoagent on each IoT node that inspects firmware
code to determine if it’s engaged in malicious behavior, such as memory
corruption. If so, the nanoagent can block it in real-time. The challenge is how
to do it with a small footprint, Sowder said: “A lot of devices don’t have a lot
of compute. Sticking a firewall in front of every IP camera simply isn’t
feasible. The solution is a very, very slight agent. It phones home to get a
device signature, including what kind of device it is and what can run on it.”
Nanoagents don’t put a lot of overhead on these devices, so the devices’
performance isn’t slowed down, Sowder noted: “There’s no overhead to prevent
them from performing their functions.” Check Point has been working on a
lightweight agent that relies on a cloud instance to pull down specific
protection details related to that device.
How Mirroring the Architecture of the Human Brain Is Speeding Up AI Learning

Several decades of neuroscience research suggest that the brain’s ability to
learn so quickly depends on its ability to use prior knowledge to understand new
concepts based on little data. When it comes to visual understanding, this can
rely on similarities of shape, structure, or color, but the brain can also
leverage abstract visual concepts thought to be encoded in a brain region called
the anterior temporal lobe (ATL). “It is like saying that a platypus looks a bit
like a duck, a beaver, and a sea otter,” said paper co-author Joshua Rule, from
the University of California Berkeley. The researchers decided to try and
recreate this capability by using similar high-level concepts learned by an AI
to help it quickly learn previously unseen categories of images. Deep learning
algorithms work by getting layers of artificial neurons to learn increasingly
complex features of an image or other data type, which are then used to
categorize new data. For instance, early layers will look for simple features
like edges, while later ones might look for more complex ones like noses, faces,
or even more high-level characteristics.
Developer burnout and a global chip shortage: The IoT is facing a perfect storm

Part of the problem stems from unprecedented demand for IoT devices. There are
already more connected things than people in the world, and the trend isn't
showing any sign of slowing down. In fact, it's quite the contrary: tech analyst
company IDC recently estimated that there will be a total 41.6 billion connected
devices by 2025. Consumers are particularly interested in using smart products
in their homes – think connected plugs, lightbulbs, thermostats and even
fridges. Forrester forecast that by 2025, the average US household will have 20
internet-connected devices. In this context, it won't be enough for
manufacturers to produce more of the same old things. Buyers' expectations are
growing: they want easy-to-use devices with new, exclusive features, which will
be continuously improved; and crucially, consumers expect that their connected
products work together across different platforms and operating systems. More
than eight in ten respondents to Forrester's survey said that they need to
rapidly manufacture new smart products and services to maintain or grow their
market position – meaning, in most cases, that a new cycle of research and
development is necessary.
Developing an api architecture
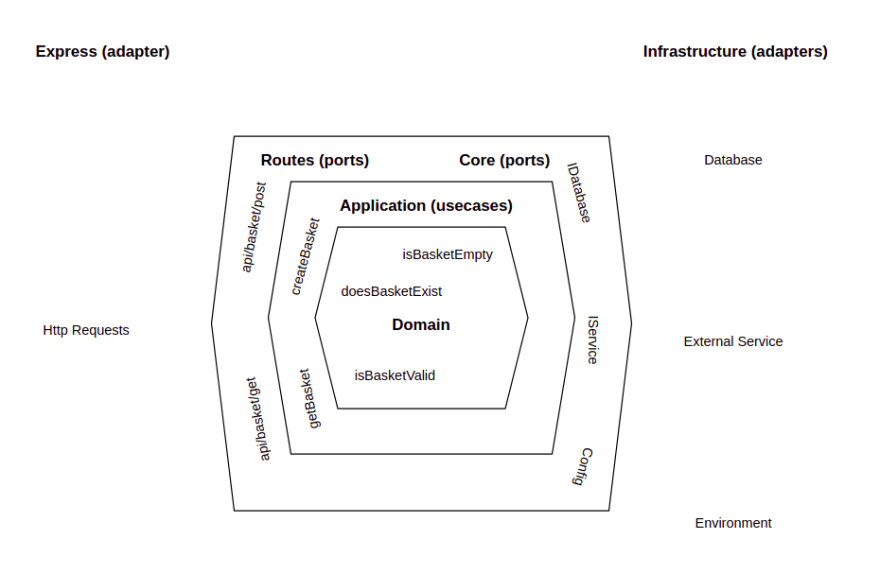
There is almost always a 1:1 relationship between the api layer and the
application layer. An api endpoint will only call one usecase, and a usecase
will most likely only be used by one api endpoint. Why not just combine them
into a single function? Loose coupling. For example, although I am using express
for my server, I may want certain use cases to be accessed via a CLI instead/as
well. The application layer does not care if a request comes via the web api, or
the cli, or some other method. It just cares about the arguments it receives.
The application, core, and infrastructure layers are hard to talk about in
isolation (which is ironic) so the next few sections will be a bit
intertwined... How does the application layer actually "do stuff" though? If we
want to get the basket, for example, how does it do this? We wouldn't want the
application layer to import the database and query it directly, this would
couple our low level implementation too tightly to the high level use case. The
core layer holds interfaces for all of the things the application can do. When I
say interfaces, I mean typescript interfaces, there is no actual javascript
here, purely types and interfaces.
4 Of The Fastest Growing Cyber Security Skills In-Demand By Business In 2021
Application development security is analyzing vulnerabilities in the app,
developing and adding security features to protect it from hackers. As the field
of modern software development catch up speed, more threat actors exploit the
rapid production of application as a chance to attack vulnerabilities in your
code. Fortunately, there are application development security experts to protect
your data and digital assets from a hacker. Application security is no more
an afterthought. To build a secure application, one must integrate security
measures in all software development life cycle parts. Burning glass report
makes this evident with demand in Application development security skills to
increase 164%, topping the list among other cybersecurity skills. ... Cloud
security refers to all the measures, policies, and rules implemented to protect
the data in the cloud from hackers. On account of businesses making a shift to
the cloud, robust cloud security is necessary. Security threat is continually
evolving and becoming more complex, which means cloud computing is at no less
danger than the on-premises environment.
What’s next: Machine learning at scale through unified modeling

Model unification can be useful for many types of machine learning problems. Our
experience with predictive models, which are widely used by organizations across
industries, has shown three important conditions that should be met for taking a
unified modeling approach: A prediction is needed for the same target variable
across a large number of related entities, or partitions; Each partition
uses the same set of features; The models need to be refreshed on a
frequent basis. ... With unified models, teams lose some flexibility for
addressing problems since it is not possible to pick and choose individual
partitions to roll back (or roll forward). A team can address this issue by
retraining the unified model outside of the regular refresh cycle.
Alternatively, if necessary, the model can be reverted for all partitions at
once, across the board. For example, if you’ve created a unified model to
predict demand for the full range or a set of your company’s products, you may
find, after deploying the model, issues with the results for one product. You
will then need to either roll back or retrain the full model.
Digital Transformation: The value of intelligent operations versus business process outsourcing
Companies that have adopted intelligent operations within their processes are
viewed as moving up their operational maturity level from “stable” to
“efficient”. Once operational efficiency is achieved, the next step is to
include data-driven insights into the decision-making process, putting the
companies at the “predictive” maturity level. Companies that go beyond this
stage are called “future-ready”. In these companies, artificial intelligence,
blockchain, cloud and various forms of intelligent operations are used to drive
and grow the company. According to the report, only 7% of organisations globally
fall into the “future-ready” category, and these are mostly in the insurance and
high-tech sectors. On average, “future-ready” organisations showed a 2.8 times
boost in corporate profitability and 1.7 times increase in operational
efficiency compared with companies in the lower maturity levels. Accenture
Operations associate director Pankaj Jain says when new technologies are
introduced, the way a company runs its operations changes dramatically.
Quote for the day:
"What lies behind us & what lies
before us are tiny matters compared to what lies within us." -- Ralph Waldo Emerson
No comments:
Post a Comment