In the Race to Hundreds of Qubits, Photons May Have "Quantum Advantage"
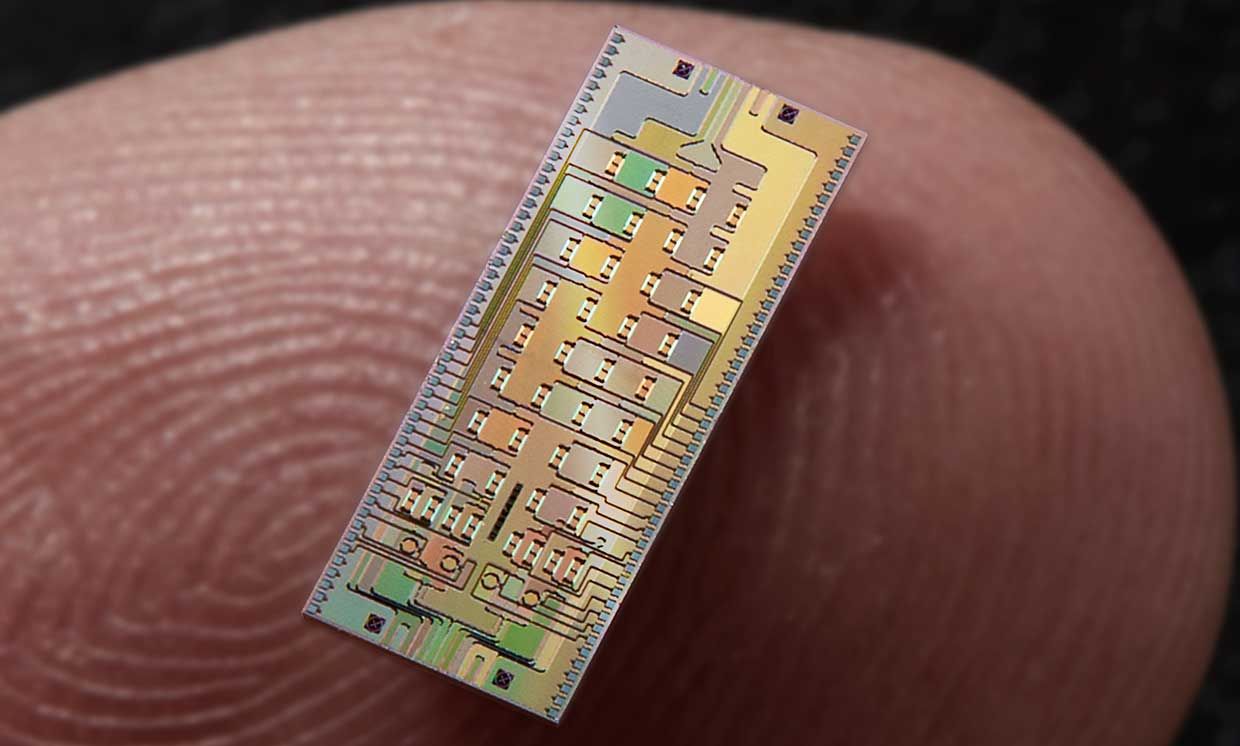
The more qubits are quantum-mechanically connected entangled together, the
more calculations they can simultaneously perform. A quantum computer with
enough qubits could in theory achieve a “quantum advantage” enabling it to
grapple with problems no classical computer could ever solve. For instance, a
quantum computer with 300 mutually-entangled qubits could theoretically
perform more calculations in an instant than there are atoms in the visible
universe. Ostensible quantum computing advantages aside, relative advantages
of one quantum computing platform versus another are less clear. The quantum
computers that tech giants such as Google, IBM and Intel are investigating
typically rely on qubits based either on superconducting circuits or trapped
ions. Those systems typically require expensive and elaborate cryogenics,
keeping them just a few degrees (sometimes mere fractions of a single degree)
above absolute zero. The expensive, bulky systems needed to keep qubits at
such frigid temperatures can make it extraordinary challenging to scale these
platforms up to high numbers of qubits.
Move Over Artificial Intelligence, There Is A New AI In Town

The lack of Data Scientists has caused many training efforts to focus on
teaching the core of algorithms and enabling people from all walks of life to
build artificial intelligence solutions via products that democratize or
automate data science. What we need for Augmented Intelligence is different. We
need people who are subject matter experts in their fields, like doctors, to
understand just enough Artificial Intelligence to work collaboratively with one.
This means they must have a level of Artificial Intelligence Literacy. AI
Literacy can help individuals understand the core concepts of how artificial
intelligence works, the context to understand its strengths and weaknesses in
their application, the capabilities to apply their understanding to solve
problems, and the creativity to see how to innovate with it for their domain.
Why are all four of these Cs important? Augmented Intelligence is about
combining the intelligence of humans and machines, where both contribute, rather
than humans becoming the caretakers of the machines. This requires the human to
not just understand the concepts and have the capability to apply them in a
specific context, but also to apply human creativity to envision new uses of the
human/machine combo.
Low-code and no-code is shifting the balance between business and technology professionals

IT departments are trying to balance two things. On one side, they see a growing
interest from business experts to solve their own workgroup-level problems
themselves. On the other hand, they want to maintain control and governance over
any software created in the organization. It's often the application development
managers, struggling with never-ending backlogs and short-staffing who are most
bullish on enterprise low-code -- they see a way to address both of these sets
of demands. With low-code and no-code, they can give business units
skill-appropriate tools to solve some of their own problems, while ensuring that
anything they build goes through a centralized process for quality and security
- the same process their enterprise software development goes through. ... This
wave of low-code adoption is nothing but good news for traditional software
developers. In our customer base, developers get to deliver solutions faster,
avoid rework and technical debt, and elevate the problem space they operate in.
That is, they get to work on harder, more interesting software problems - say
software architecture, or working through the creation of complex logic.
Cyber Extortion Thriving Thanks to Accellion FTA Hits
Some ransomware gangs run their own attacks, but many operations now function
using a ransomware-as-a-service model, in which operators develop code and
infrastructure and affiliates infect victims. For every victim who pays, the
operator and affiliate split the profits, with affiliates often keeping 60% to
70%. Experts say this division of labor has helped RaaS operations maximize
profits - especially if they can recruit highly skilled affiliates. The type of
ransomware most encountered by victims assisted by Coveware in Q1 was
Sodinokibi, aka REvil, followed by Conti, Lockbit, Clop and Egregor. All are
prolific RaaS operations. But competition remains fierce between RaaS operations
as they attempt to recruit top affiliates to maximize their paydays, including
via big game hunting, which is hitting larger victims for the prospect of bigger
ransom returns. Seeking fresh avenues for finding new victims, some RaaS
operations have begun running campaigns using malware written to crypto-lock
Unix and Linux systems. Defray777, Mespinoza, Babuk, Nephilim and Darkside have
already deployed such code, and Sodinokibi suggests it will do so, Coveware
says.
Lessons in simplicity strategy

Six, as I have written before, is a useful organizing number, and is the
smallest in a range of numbers described in mathematics as “perfect.” A number
is perfect if it is a positive integer that is equal to the sum of its divisors.
Six, of course, is the sum of one, two, and three. Six is also workable,
definable, measurable, and memorable. If you adopt a small-is-better mentality
(I love the two-pizza rule, which says if your working group can’t be fed by two
pizzas, it’s probably too large), six gives you a guideline that can be
established and maintained fairly quickly. The hexagon, nature’s diamond, lends
itself beautifully to organizational management because of the way it embodies
interconnection, resilience, and economy. Like the equilateral triangle and the
square, the hexagon tessellates, which is to say it can connect to the same
shape without gaps (unlike, say, circles, an all-too-popular PowerPoint
intersecting image). This is crucial, because so much of what people do
intersects and connects. The hexagon is a powerful visual aid and connects us to
network theory in which “edges” play a crucial role.
Lawmakers Seek to Expand CISA's Role
A five-year national risk management cycle review by CISA, as called for by
Hassan and Sasse, is needed to better address threats to critical
infrastructure, says Tim Wade, a former network and security technical manager
with the U.S. Air Force. He's now a technical director at the security firm
Vectra AI. "Failure to have a credible and timely recovery strategy places
nontrivial strain on detection and response requirements, whereas protecting and
enabling rapid recovery removes tension from the entire system," Wade says.
"This move marks a step in the right direction, and even as the road ahead is
long, we all have a vested interest in its success." The various Congressional
proposals regarding CISA could go a long way toward addressing threats to IT and
operation technology networks, says Joseph Carson, chief security scientist and
advisory CISO at security firm Thycotic. "One of the most vital areas to focus
on is regaining visibility and control of the network as a whole, including the
disparate IT and OT systems. In particular, this means having a firm command of
how systems are accessed," Carson says.

If you step back and think about the conversation as an opportunity to learn
versus the need to defend, it helps open the aperture into a dialogue vs a
debate. Somewhere along life’s path (we usually refer to this as getting older)
learning is replaced with knowledge, yet if we make the choice to continuously
learn from other’s perspectives, learning can be lifelong, and knowledge can
grow vs. sustain. Consider that openness to experience—the degree to which you
are interested in exploring new ideas, nurturing your hungry mind, and replacing
routine with unconventional and unfamiliar adventures—decreases as we get older.
The more we know, the less interested we are in learning something new. As Lisa
Feldman Barrett notes in her recent book, our brains are not for thinking: they
are for saving energy and turning decision into autopilot mode. It’s okay to
want to listen and learn and still hold onto your own beliefs and values. The
act of listening doesn’t indicate agreement. In fact, it is a lot easier to
agree when we don’t listen to one another. Remember that the difference between
judging and pre-judging is understanding and that in order to understand you
really need to be willing to listen and learn.
Australia's eSafety and the uphill battle of regulating the ever-changing online realm

Appearing before the Parliamentary Joint Committee on Intelligence and Security
as part of its inquiry into extremist movements and radicalism in Australia,
Inman Grant said while the threshold is quite high in the new powers around
take-down requests, it will give her agency a fair amount of leeway to look at
intersectional factors, such as the intent behind the post. "I think that the
language is deliberately -- it's constrained in a way to give us some latitude
... we have to look at the messenger, we have to look at the message, and we
have to look at the target," she said on Thursday. The Act also will not apply
to groups of people, rather simply individuals. The commissioner guessed this
was due to striking a balance on freedom of expression. "To give us a broader
set of powers to target a group or target in mass, I think would probably raise
a lot more questions about human rights," she said. She said it's a case of
"writing the playbook" as it unfolds, given there's no similar law
internationally to help guide the Act. Inman Grant said she has tried to set
expectations that she isn't about to conduct "large scale rapid fire".
Corporate e-waste: The unfashionable global crisis

Ensuring redundant business technology is reused is an important way to reduce
our environmental impact. When a device reaches the end of its first lifecycle
and a business needs to upgrade, that device still holds value, both to the
company and to a second user. Giving a device a second life reduces carbon
emissions and electronic waste. Every laptop that is reused, displaces the need
to remanufacture a new one, also saving natural resources. We like to say that
every time we rehome a device, we’re saving the planet one laptop at a time.
Dumping old devices also represents a wasted opportunity to help people access
used IT equipment at more affordable prices. Not everyone needs or can afford
new tech, so a vibrant secondhand market is crucial to closing the digital
divide. Plus, while the disposal of IT equipment is hassle and an expense for
businesses, ensuring old devices are reused gives equipment extra value – a
value which can be used against the cost of purchasing new IT devices. With
organisations faced with accelerating the shift to mobile devices, this could
free up much needed cash to fund digital transformation projects
The Biggest Data Management Mistake Chief Data Officers Make

Most advice to Chief Data Officers in these situations comes down to this:
Ensure that your data strategy provides business value — e.g., increasing
revenue and improving cost control — and risk management – e.g., inclusive of
compliance and privacy. While this may seem like the right advice, it puts the
onus on the CDO to propose business value to the rest of the C-suite instead of
supporting the initiatives in which leaders already have invested. These
business initiatives require data and analytics that the CDO can provide. But if
CDOs initiate their own projects and separate business value propositions, the
existing business initiatives are often left without the data management
platform they require. This results in a divergence of projects that don’t
support each other: the business initiatives will continue to generate data
while the CDO builds a “foundation” of data, creating yet another silo. The
difference between proposing and supporting business value may seem subtle, but
it’s actually profound. Most IT leaders running enterprise database management
today are building up programs that have value independent of major business
initiatives.
Quote for the day:
"Every great leader can take you back to
a defining moment when they decided to lead." -- John Paul Warren
No comments:
Post a Comment