Wanted: Millions of cybersecurity pros. Rate: Whatever you want

In the United States, there are around 879,000 cybersecurity professionals in
the workforce and an unfilled need for another 359,000 workers, according to a
2020 survey by (ISC)2, an international nonprofit that offers cybersecurity
training and certification programs. Globally, the gap is even larger at nearly
3.12 million unfilled positions, the group says. Its CEO, Clar Rosso, said she
thinks the need may actually be higher, given that some companies put off hiring
during the pandemic. The needs range from entry-level security analysts, who
monitor network traffic to identify potential bad actors in a system, to
executive-level leaders who can articulate to CEOs and board directors the
potential financial and reputational risks from cyber attacks. The US Bureau of
Labor Statistics projects "information security analyst" will be the 10th
fastest growing occupation over the next decade, with an employment growth rate
of 31% compared to the 4% average growth rate for all occupations. If demand for
cybersecurity professionals in the private sector increases dramatically, some
experts say talented workers could leave the government for more lucrative
corporate jobs
100 Days To Stronger Cybersecurity For The US Electric Grid

Regardless of company size or ownership status, all organizations that support
the BES are required to comply with a set of cybersecurity standards known as
the North American Electric Reliability Corporation Critical Infrastructure
Protection (NERC-CIP) standards. NERC-CIP defines the reliability requirements
for planning, operating and protecting the North American bulk power supply
system. It covers everything from identifying and categorizing assets, to
implementing physical and digital security controls, to dealing with incidents
and recovering from a cyber breach. As any security officer knows, “compliance”
does not guarantee “security.” Even if all companies that are part of the BES
are fully compliant with NERC-CIP — and that’s a big “if” — it’s still a good
idea to have a group of experts examine the security controls and bring them up
to date to be able to counter current threats from a variety of adversaries. The
DOE’s 100-day plan states that “the initiative modernizes cybersecurity defenses
and encourages owners and operators to implement measures or technology that
enhance their detection, mitigation, and forensic capabilities”
Facebook Launches AI That Understands Language Without Labels

In a recent blog post, Facebook revealed its new AI-based speech recognition
technology, wav2vec-Unsupervised (or wav2vec-U), which aims to solve the
problems posed by transcribing such languages. This is a method by which
individuals could build speech recognition systems that do not require
transcribed data. The ML algorithm still requires some form of training.
Wav2vec-U is trained purely through recorded speech audio and unpaired text.
This method entails first learning the structure of the target language’s speech
from unlabelled audio. Using wav2vec 2.0, Facebook’s self-supervised speech
recognition model, and a k-means clustering algorithm, wav2vec-U segments the
voice recording into speech units loosely based on individual sounds. For
instance, the word cat would correspond to the sounds: “/K/”, “/AE/”, and “/T/”.
This allows it to comprehend the structure of this speech. To recognise the
words in an audio recording, Facebook will use a generative adversarial network
(GAN) consisting of a generator and a discriminator network. The generator will
take each audio segment embedded in self-supervised representations and predict
a phoneme
Why cloud governance needs to be an open source affair

Keep in mind that Cloud Custodian emerged from work Thangavelu was doing at
Capital One, which is a big company with over 50,000 employees and tens of
billions in revenue. It was a laboratory primed to help Thangavelu "service the
different needs from different groups within the enterprise: audit, risk,
security, application teams, lines of business," he said. That helped make Cloud
Custodian incredibly useful within his enterprise. But just one enterprise. Open
source increased the scope and utility of Cloud Custodian beyond one company's
needs. "As we've gotten to open source, that pool of use cases simply expanded,"
he noted. No matter how creative your product managers, they're always
necessarily constrained by the needs of the business they're running. By
contrast, Thangavelu continued, "Open source is the strongest way to achieve
[expanded scope] because your usage and your users address a wider swath of
needs than any given company has. They represent the needs of a large diverse
set of interests. And they're all pulling in different directions." This
push-and-pull from a growing Cloud Custodian community has made it a useful tool
for organizations that may have thousands or even tens of thousands of diverse
policies to manage.
The Emerging Role of Artificial Intelligence in Human Lung Imaging
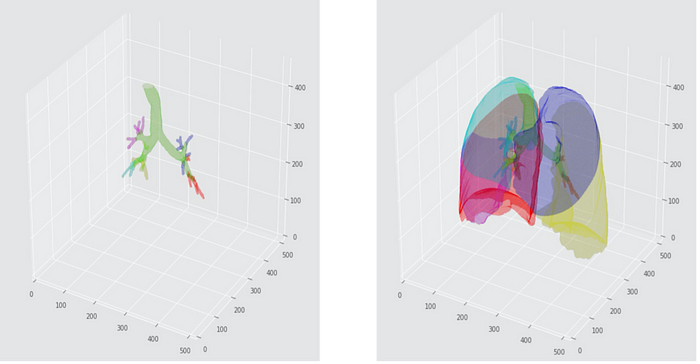
Recently risen to prominence, robust AI methods outline the onset of the new era
in lung image analysis. Adept at seeing and making sense of vital image-led
patterns, AI tools help make the respiratory field more effective — improving
diagnosis and therapeutic planning, letting pulmonologists spend extra time with
patients. Hence, various attempts have been made to develop automated
segmentation techniques lately. Yet, the strain on the healthcare and
particularly radiology system, following the pandemic, will remain until these
AI-based approaches are adopted. A major hurdle of lobe segmentation arises
because different respiratory diseases affect the lung architecture in different
ways. For example, COVID-19 pneumonitis would manifest on imaging very
differently from pulmonary emphysema. For respiratory physicians, accurate lobar
segmentations are vital in order to make treatment plans appropriately.
Inaccurate lobe segmentation can give misleading information about the disease
process, which can lead to erroneous treatment decisions.
Network Monitoring: The Forgotten Cybersecurity Tool

Networks can be very complex, and many are segmented into VLANs to segregate
traffic. What’s more, there are many devices on the network that can shape or
route traffic depending on how the network infrastructure has been configured.
“Today, networks are highly segmented, yet still interconnected; there are
numerous devices, such as content filtering appliances, load balancers and so
on, that all work together to shape and control network traffic,” Gridelli said.
“Here, active network monitoring can verify whether or not security policies are
properly in effect, and detect unauthorized changes to the network
infrastructure.” Active network monitoring tools often deploy sensors, which can
look into a network and report on what is happening on that network.
Administrators can define policies that verify network segmentation, segregation
and even the functionality of content filtering devices. By running end-to-end
active network monitoring tests, it’s possible to also verify whether certain
security policies, such as compliance requirements, are working as intended.
Sensors can be installed on protected networks, such as those used for
compliance (PCI, HIPAA, etc.)
Graphs as a foundational technology stack: Analytics, AI, and hardware

Interest is expanding as graph data takes on a role in master data management,
tracking laundered money, connecting Facebook friends, and powering the search
page ranker in a dominant search engine. Panama Papers researchers, NASA
engineers, and Fortune 500 leaders: They all use graphs. According to Eifrem,
Gartner analysts are seeing explosive growth in demand for graph. Back in 2018,
about 5% of Gartner’s inquiries on AI and machine learning were about graphs. In
2019, that jumped to 20%. From 2020 until today, 50% of inquiries are about
graphs. AI and machine learning are in extremely high demand, and graph is among
the hottest topics in this domain. But the concept dates back to the 18th
century, when Leonhard Euler laid the foundation of graph theory. Euler was a
Swiss scientist and engineer whose solution to the Seven Bridges of Königsberg
problem essentially invented graph theory. What Euler did was to model the
bridges and the paths connecting them as nodes and edges in a graph. That formed
the basis for many graph algorithms that can tackle real-world problems.
Google’s PageRank is probably the best-known graph algorithm, helping score web
page authority.
Adam Grant on leadership, emotional intelligence, and the value of thinking like a scientist
One of the things that scares me in a lot of organizations is how attached
people become to best practices. They might’ve been the best at the time that
you created them. But as the world around you changes, as your culture evolves,
what was best five years, 10 years ago may not be what’s most productive today.
I think the language of best practices creates this illusion that there’s an end
point, that we’ve already reached perfection. And so we don’t need to change
anything. What I would love to see more organizations do instead is to strive
for better practices, right? To say, “Okay, you know what? No matter how good a
practice becomes it can always be improved. And we’re open to trying whatever
ideas you have for trying to evolve the way that we do things around here.” ...
When you see what other people are feeling, that’s information about what their
motivations are, what’s occupying a lot of their energy and attention. Without
that information, you’re actually handicapped as a leader.
Not as complex as we thought: Cyberattacks on operational technology are on the rise

The "low-hanging fruit" many attackers are going for are graphical user
interfaces (GUI) -- including human machine interfaces (HMI) -- which are, by
design, intended to be simple user interfaces for controlling complex industrial
processes. As a result, threat actors are able to "modify control variables
without prior knowledge of a process," Mandiant says. Another trend of note is
hacktivism, propelled by widely available and free tutorials online. Recently,
the researchers have seen hacktivist groups bragging in
anti-Israel/pro-Palestine social media posts that they have compromised Israeli
OT assets in the renewable and mining sectors. Other low-skilled threat actors
appear to be focused on notoriety, however, with little knowledge of what they
are targeting. In two separate cases, threat actors bragged about hijacking a
German rail control system -- only for it to be a command station for model
train sets -- and in another, a group claimed they had broken into an Israeli
"gas" system, but it was nothing more than a kitchen ventilation system in a
restaurant.
Evolutionary Architecture from an Organizational Perspective
Business and IT must work together to understand the business environment and
adapt the architecture accordingly. Only then is the feedback loop between the
new customer’s needs and a created solution short enough to evolve architecture
in the right direction. The delivery team directly listens to the client’s needs
and proposes a solution. Therefore, our architecture evolves naturally with the
overall business. There isn’t an additional layer of communication that slows
down accommodating the change. When the architecture doesn’t correspond to the
business environment, we can remodel architecture much more quickly.
Additionally, the delivery team works more closely with the clients. They
understand their needs. Based on that, the evolution of the system becomes more
business-oriented. We don’t create architecture for the sake of the architecture
-- we create a spine for the overall business goal. This idea of empowered teams
is shown in detail in the book Empowered by Marty Cagan and Chris Jones. A team
is responsible for gathering clients’ needs, discovering the right solution,
implementing it, and gathering feedback.
Quote for the day:
"Leaders must know where they are going
if they expect others to willingly join them on the journey." --
Kouzes & Posner
No comments:
Post a Comment