Internet of Things Applications
IoT applications can transform reactive medical-based systems into active
wellness-based systems. Resources that are used in current medical research
lack important real-world information. It uses controlled environments,
leftover data, and volunteers for clinical trials. The Internet of Things
improves the device's power, precision and availability. IoT focuses on
building systems rather than just tools. Here's how the IoT-enabled care
device works. ... Most of you have heard about the term smart city. Smart city
uses technology to provide services. The smart city includes improving
transportation and social services, promoting stability and giving voice to
their citizens. The problems faced by Mumbai are very different from Delhi.
Even global issues, such as clean drinking water, declining air quality, and
increasing urban density, occur in varying intensity cities. Therefore, they
affect every city. Governments and engineers use the Internet of Things to
analyze the complex factors of town and each city. IoT applications help in
the area of water management, waste control and emergencies. ... By the year
2050, the world's growing population is estimated to have reached about 10
billion. To feed such a large population, agriculture needs to marry
technology and get the best results.
Learning from Bugs and Testers: Testing Boeing 777 Full Flight Simulators
Every failure is an opportunity to learn something. Finding and fixing a bug
is great, but understanding why the bug is there is where you learn even more.
It might be a requirement that wasn’t properly formulated, implemented,
tested, or anything else. As a software tester, imagine that a bug you
have reported was caused by an untrapped exception in a division by zero. If
you saw that bug several times or if your software is mission-critical then it
is worth asking every team to check if they have encapsulated all code where
they perform a division with a “try catch” statement. The Ariane 5 Rocket blew
up because of untrapped exceptions: There go half-a-billion dollars and a dent
in reputation. The US Air Force almost lost an F-22 squadron
(state-of-the-art fighter jets valued $350 million a pop) when they flew over
the International Date Line (IDL) leaving the pilots with only flight controls
(dedicated and separated computers). When you cross the IDL the “time” skips
by one day depending on your direction of travel. A space probe crashed on
Mars because the software testers forgot to test what would occur when sensors
are sending erroneous data to the mission computer.
55 New Security Flaws Reported in Apple Software and Services

A team of five security researchers analyzed several Apple online services for
three months and found as many as 55 vulnerabilities, 11 of which are critical
in severity. The flaws — including 29 high severity, 13 medium severity, and 2
low severity vulnerabilities — could have allowed an attacker to "fully
compromise both customer and employee applications, launch a worm capable of
automatically taking over a victim's iCloud account, retrieve source code for
internal Apple projects, fully compromise an industrial control warehouse
software used by Apple, and take over the sessions of Apple employees with the
capability of accessing management tools and sensitive resources." The flaws
meant a bad actor could easily hijack a user's iCloud account and steal all
the photos, calendar information, videos, and documents, in addition to
forwarding the same exploit to all of their contacts. The findings were
reported by Sam Curry along with Brett Buerhaus, Ben Sadeghipour, Samuel Erb,
and Tanner Barnes over a three month period between July and September. After
they were responsibly disclosed to Apple, the iPhone maker took steps to patch
the flaws within 1-2 business days, with a few others fixed within a short
span of 4-6 hours.
An introduction to Windows 10’s new PowerToys
Over the past few months, PowerToys has really cleaned up its installation and
update capabilities. Versions 0.18.2 and earlier would require users to jump
into Task Manager and terminate various processes and applications before its
installation could complete. Via Twitter, one of team leader Clint Rutkas’
associates informed me this was because of the program’s inclusion of the Core
.NET DLLs into PowerToys. But as of release v0.20.1, PowerToys handles all
open applications without issue. Now, it simply asks for permission to restart
the Windows Explorer (process name: explorer.exe) as it finishes up updating
or installing itself. Speaking of updates, Rutkas and his programmers are
working hard to push frequent updates to PowerToys. A look at the Releases
page shows eight releases since early June, or about two per month. ...
Pressing and holding the Windows key causes an overlay showing a list of
Windows-key shortcuts to appear on the primary Windows display. Once shown,
that menu — a.k.a. the Shortcut Guide — persists as long as the winkey remains
depressed. These shortcuts, or key combos, require that the Windows key and
the named key be depressed together.
3 ways criminals use artificial intelligence in cybersecurity attacks

Generative Adversarial Networks (GANs) are basically two AI systems pitted
against each other—one that simulates original content and one that spots its
mistakes. By competing against each other, they jointly create content
convincing enough to pass for the original. Nvidia researchers trained a
unique AI model to recreate PAC-MAN simply by observing hours of gameplay,
without a game engine, as Stephanie Condon explained on ZDNet. Bandos said
that attackers are using GANs to mimic normal traffic patterns, to divert
attention away from attacks, and to find and exfiltrate sensitive data
quickly. "They're in and out within 30-40 minutes thanks to these
capabilities," he said. "Once attackers start to leverage artificial
intelligence and machine learning, they can automate these tasks." GANs also
can be used for password cracking, evading malware detection, and fooling
facial recognition, as Thomas Klimek described in the paper, "Generative
Adversarial Networks: What Are They and Why We Should Be Afraid." A PassGAN
system built by machine learning researchers was trained on an industry
standard password list and was eventually able to guess more passwords than
several other tools trained on the same dataset.
Serverless Horror Stories

One of the well-known challenges of event-driven serverless architectures is
the difficulty in tracing requests end-to-end, in order to investigate
performance issues. A case in point is when the Segment company encountered a
problem with a popular serverless service, DynamoDB. Segment was experiencing
a serious performance issue with their DynamoDB instances that was slowing
down their entire system. To mitigate this, the company had to increase the
provisioned throughput of DB instances, but this in turn vastly increased
their AWS bill. When Segment’s own troubleshooting efforts failed to uncover
the problem, they asked AWS support for help. Using internal tools, AWS
generated a partition heatmap of DynamoDB instances. Although the heatmap was
not very readable, they were able to spot a single DB partition that was
having performance issues, clearly indicating that their workload was not
distributed evenly across partitions. It was still, however, not clear which
records or keys were problematic. So Segment continued to investigate the
issue and found a relatively trivial bug that was very hard to spot but which,
when fixed, reduced their DynamoDB capacity by a factor of four and saved them
$300,000 annually.
Travelex Cyber-attack Timeline

We have compiled a detailed timeline of the Travelex cyber-attack based on
information that's available freely on the internet and in media reports. Our
objective is to simply present this information in an easy-to-consume visual
guide that can help cybersecurity practitioners and enthusiasts to get further
clarity on what went wrong and how. ... The idea of us creating this timeline
is not to vilify/defame any business or victims of a cyber-attack. However,
from every cyber incident there is something all of us can learn about
covering our bases when it comes to being truly cyber-resilient. In this
case, it appears that the cyber-criminals managed to attack Travelex thanks to
the unpatched critical vulnerabilities in its Pulse Secure VPN servers. Hence,
the lesson here would be to always ensure that your cybersecurity
infrastructure is as updated and foolproof as possible. Regular review of the
IT infrastructure is also imperative to ensure that your business is as secure
as is possible. ... Amar insists that this initiative isn't aimed at attacking
Travelex or any organisation. Our objective to create these attack timelines
is purely for educational purposes. Amar has been in the thick of many
cyber-attacks and he absolutely understands the pressure, the chaos and the
collective desire to do the right thing when in the midst of a major crisis.
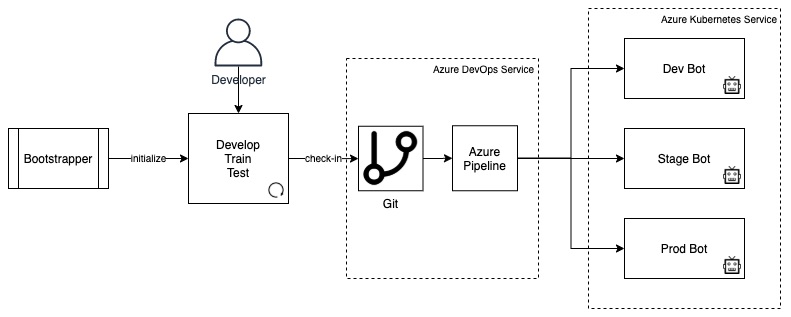
How to Build, Deploy, and Operationalize AI Assistants
Some of the issues with non-linear conversations, where the user introduces a
new topic in the middle of the conversation or modifies a previous statement,
remained. These types of multi-turn conversations are particularly
challenging, and they also happen to be the way that most users actually talk.
In an effort to resolve some of these issues, the team experimented with
Rasa’s TED (Transformer
Embedding Dialogue) policy. Using a transformer architecture, the TED policy
can selectively pick which conversation turns to pay attention to, and which
conversation turns to ignore. Additionally, and perhaps, distinctively in
comparison to recurrent neural network architectures, transformers use a
self-attention mechanism, by which they’re able to choose which elements in a
conversation to pay attention to, in order to make an accurate prediction. In
other words, transformers are uniquely equipped to handle non-linear
conversations where a user might change topics, engage in chitchat in the
middle of a conversation, because they’re less likely to become perplexed when
a user does something unexpected. In addition, it provides hyperparameters
that can be used to fine-tune the model.
The next frontier for risk tech should be in the cloud

Risk management technology moving to the cloud allows organizations to better
incorporate their entire technology stack into their GRC processes. With more
available integrations, data can be exchanged more securely and can result in
more impactful business insights. And, when information moves seamlessly
between applications and platforms, it’s also easier to incorporate more
employees and managers into a company’s risk culture and processes. Investing
in agile technology gives companies the opportunity to scale, and scale
quickly. In a space like GRC and risk management, which relies on data and
insights garnered through data, it’s important to not only invest in agile
technology but also in software built on a graph database. Graph databases,
compared to relational databases, are much more flexible and offer greater
user-visibility. Information is more easily stored and the infrastructure
allows it to generate relationships between data sets so solutions can unlock
more insights and functionality. Now, a cloud-based risk management solution
can align with and improve pre-existing processes. As a result, Gartner
predicted 100% annual growth through 2022, when naming graph databases one of
its biggest data trends.
Data localisation in emerging markets: The case of Turkey

Data localisation requirements under Turkish law have so far been
sector-specific and, hence, limited in scope. Several sectors are already
under obligation to keep primary and secondary data in Turkey: banking, e-sim
technology companies, finance, healthcare and energy. When the social media
law discussed above was formally enacted in July 2020, the Turkish ID number
requirement for social media logins was dropped and the data localisation
measure became a request to the outlets “to take the necessary measures
towards hosting Turkey-based users’ data in Turkey” without enforcement. With
no clear enforcement mechanism for the data localisation requirement in the
Turkish social media law, Turkey diverged from the Russian approach of forced
data localisation in social media and approximated to the social media
regulation approaches of other G20 member emerging markets such as South
Africa and India. Yet another blow towards forced data localization came from
the “Personal Data Protection Board” in September 2020, rendering the
Convention No. 108 of the Council of Europe (to which Turkey is a signatory)
on cross-border transfers of personal data not applicable for Turkey.
Quote for the day:
"Leadership is intangible, and therefore no weapon ever designed can replace it." -- Omar N. Bradley
No comments:
Post a Comment