Athenahealth CISO describes the company’s new ‘internal offense’ security strategy

The platform serves as a virtual mirror for nation-state actors and cybercriminals and unlike a simulation, which replays historical attacks inside artificial boundaries, it provides the ability to safely launch real-world attacks against production assets, he added. “Athenahealth uses Randori’s reconnaissance capabilities to understand the accessibility and value of assets that could be attacked and make determinations on how best to prioritize and protect them,” Hazzard continued. “The company’s tooling helps us identify internet-facing systems – where we are, how we appear to attackers on the internet, what avenues to access are available, and what data exists in the internet that could be used to acquire access.” Much of the reconnaissance is conducted automatically in the same way threat actors conduct such activities, he explained. “We’ve found opportunities in using the company’s data to improve our security posture and make certain attacks less possible, more difficult, or require a much higher level of sophistication to execute,” he said.
Reinventing tech finance: The evolution from IT budgets to technology investments

Agile and other flexible delivery styles are on the rise—the CIO survey found that 56 percent of CIOs expect to implement Agile, DevOps, or a similar flexible IT delivery model to increase IT responsiveness. But these efforts could be stymied by traditional budgeting processes, which aren’t optimized for the Agile development environment. Rather than promoting cross-functional teaming, iterative sprints, and the customer- and product-oriented mindset—the hallmarks of Agile development—fixed IT budgets are typically structured to provide incremental annual increases and encourage functional silos, inflexible requirements, and a project-focused mindset. Agile’s laissez-faire approach to project scope and requirements dictates more flexible timelines, processes, and financing, which fly in the face of the fixed annual budget’s insistence on predictable costs and resources. ... To cultivate the most diverse set of investments, many CIOs are managing technology portfolios, allocating funding across various time horizons and according to potential risk, reward, and value. Depending on corporate strategy and competitive and market factors, CIOs look for the right balance of technology investments in three areas: existing business operations, business capability enhancements, and adjacent and new capabilities.
DeepCode taps AI for code reviews
DeepCode learns from open source code bases and has built up a knowledge base to make suggestions on improving code. Code is analyzed with each change. The DeepCode cloud service integrates with code hosting platforms GitHub and Bitbucket, and supports on-premises deployments to watch over Bitbucket Server or GitLab. Core features of DeepCode include: AI QA Audits. DeepCode analyzes any branch of a repository and displays results in a web browser; and AI Code Reviews including commit analysis and pull request analysis. DeepCode analyzes all code commits and pull requests and notes any issues. DeepCode also offers semantic analysis, which examines changes before and after problems and understands context. Security and performance bugs are analyzed, as well as logical mistakes made by developers. Compatibility issues, such as when a new version of a language is being used, also are assessed. Formatting and API issues are checked as well. Other items looked for include resource leakage, null pointer exceptions, and date formatting issues.
Microsoft is expanding its antivirus software to iOS and Android

With the new release, Microsoft is staking out its place in a growing market of antivirus providers compatible with smartphones - and it's pitching its own security tech as a one-stop provider for companies with employees that use multiple devices and operating systems on the job (the newly announced software will be available for businesses, but not individual consumers). Microsoft engineers and executives who spoke to Business Insider about the offering said Defender primarily aims to prevent employees from falling for phishing scams and to detect insider threats, a rising security concern for companies. Corporate Vice President for cybersecurity solutions Ann Johnson touted Defender's features that give companies tools to more closely oversee individuals who might pose an insider threat. "Let's say I resigned from Microsoft tomorrow, and I give my two weeks notice," Johnson told Business Insider. "Insider risk management gives the organization, with the right HR and legal permissions, the ability to monitor me much more closely."
Security leaders can no longer adopt the role of enforcer, but rather need to pivot to a new role: the enabler. CISOs today have the opportunity to help enable the organization to grow by delivering a digital experience that delights customers while mitigating digital risk. This requires the CISO to advise the business about when and where cyber risks could manifest. Security leaders must now be able to transform their security practices in lockstep with all the other changes wrought by business-wide digital transformation. Today’s CISO needs to be able to provide advice to the business to help it understand the risk landscape so that it can then make informed decisions about which risks are tolerable and which ones to avoid at all costs. In addition to providing this counsel, security leaders must be able to implement the technology to mitigate risks and protect the business as it continues on the path to digitally transform. As part of this change in mindset, security leadership needs to take into account the impact of friction on the user experience as it can “break or make” security initiatives.
Infosys CISO: Being good at technology is no longer enough

The future is going to be about cyber resilience, and CISOs need to lead the charge to recalibrate how security teams and entire companies think about security. Security leaders have to engage board members and team members in the right way and drive the shift to a new mindset about security. "A truly effective CISO can shape the thinking of the organization, and that's where influence comes in," he said. Salvi said that the pressure to shift to a secure-by-design approach is not yet as powerful as the need to get a product on the market as quickly as possible. "You need a leader who is willing to take the business loss for two weeks to make sure the product is secure," he said. Salvi spends a lot of time cultivating a secure-by-decision mindset in the industry and internally at Infosys. "You have to drive that thinking on an ongoing basis, it's not something that is easy because it is not natural," he said. Salvi's team at Infosys includes three direct reports, a leadership team of 50 people, and about 300 staff members. "The average tenure on the leadership team is 10 years, so compared to them, I am a newbie," Salvi said.
Bringing A Concierge Approach To Cyber Risk Management

Suhs’s experience with concierge medicine formed his vision for a new delivery model for cyber risk management, which today exists as Concierge Cyber®. Here’s how it works: “In return for a set annual membership fee, my firm provides businesses and individuals guaranteed quick and easy access to cyber risk resources,” explains Suhs, founder and managing director of Cyber Special Ops, LLC, which offers the product. “These include same-day appointments and phone or email access on evenings and weekends, information security policy templates, and pre- and post-breach services, as needed, at pre-negotiated rates. “We work with a respected and highly credentialed group of legal, information security, credit and identity restoration, and public relations specialists from firms located around the globe to deliver advanced cyber risk management services,” he adds. “The specialists operate under the umbrella of My-CERT™ which stands for My-Cyber Emergency Response Team; they provide what we describe as ‘expertise, experience and agility to effectively respond to a cyber incident under the protection of attorney-client privilege.’”
Massive DoD DevSecOps standards push may aid enterprise IT
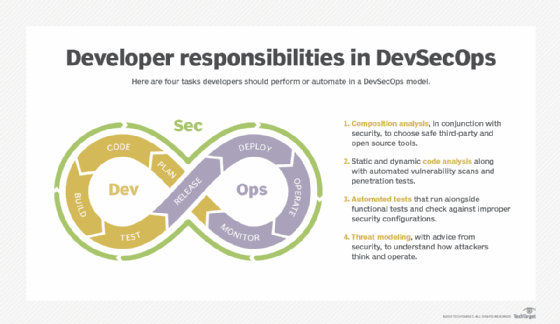
As government agencies and private-sector enterprises increasingly use the same open source technologies, many commercial companies look to the government, particularly the DoD, as the gold standard for cybersecurity, one IT consultant said. "There's a saying, 'Nobody ever got fired for using IBM,'" said Jeremy Pullen, principal technical consultant at Polodis, a digital transformation consulting firm in Atlanta, who's closely following the DoD's DevSecOps work, including a recently published repository of hardened container images for general use. "There's a similar confidence in using systems hardened to the standards of the US government." Pullen said the breadth of the collaboration will also help legitimize the DevSecOps concept as a set of practices, rather than tying it to any particular tool, vendor or method used by specific household-name enterprise IT teams. "The last two years, I've had to educate people about what DevSecOps is and isn't -- it's not just using a tool from White Hat, Sonatype or Veracode," he said. "This paints a better picture of DevSecOps as an area of practice rather than just implementing somebody's product."
One in four Americans won’t do business with data-breached companies

This study included data breaches that occurred from Jan. 1, 2018, to Dec. 31, 2018, regardless of the public reporting date. Only breaches leaking over 500,000 consumer records that affected consumers on a national scale were included. It found that most people were only loosely familiar with the total number of corporate breaches that occurred in 2018. Though the majority of people admitted to losing trust in corporations that experienced data breaches, most were unwilling to cut ties with these companies. To counter this, most people made their account passwords harder to guess and were more selective with whom they gave their financial information after learning of a breach, even though one in three people who experienced a data breach ultimately weren't sure which information was targeted. The findings showed that almost one in four Americans stop doing business with companies who have been hacked, and more than two in three people trust a company less after a data breach. Almost all respondents (92%) agree that companies are financially liable to their customers after a breach and over one in five people are unwilling to give their financial information to a company who's been hacked
Malaysia: A Flourishing Fintech Ecosystem
Developments in Malaysian fintech are altering the country’s financial sector landscape. For example, while fintech products offered by traditional financial institutions expand, the number of physical commercial bank branches is declining, and the number of automated teller machines has fallen over the last two years. Traditional Malaysian banks continue to dominate in deposits, lending, and raising capital while, at the same time, adopting new technologies and either competing or collaborating with new tech startups. As of April 2019, there were close to 200 startups in Malaysia in a range of fintech areas, including payments, lending, and blockchain. Of course, the rapidly evolving technology—alongside new consumer habits—is not without risk or challenges. Malaysia has been a leader on regulations to ensure that the financial system remains safe amid the possibility of cybersecurity incidents. Well aware that cyberattacks can undercut customer confidence and inflict widespread damage, Malaysian banks and regulators list cybersecurity among their issues of top concern.
Quote for the day:
"What I've really learned over time is that optimism is a very, very important part of leadership." -- Bob Iger

No comments:
Post a Comment