Cassandra and DataStax: Reunited, and it feels so good

While single-vendor open source projects are somewhat common, they’re verboten for ASF projects. This became an issue for Cassandra, given that years ago DataStax may have contributed as much as 85 percent of the Cassandra code, by one estimate, while also running a community content forum (Planet Cassandra), Cassandra events, and more. This led to ASF accusations that DataStax exercised (or had the potential to exercise) undue influence over Cassandra. In response, DataStax pulled back, leaving the Cassandra community to fend for itself. This didn’t dissuade companies from continuing to bet big on Cassandra. Apple, for example, had long embraced the highly scalable, high-performance distributed database, as I wrote in 2015. While the company is famously cagey about sharing how it uses technology, we do know that it runs more than 100,000 Cassandra nodes today. With such a big investment in Cassandra, Apple couldn’t afford to let it fail, so Apple worked hard to ensure that stability dramatically improved from the Cassandra 3.11 release to today’s Cassandra 4.0 release.
Russia's Cybercrime Rule Reminder: Never Hack Russians
On Tuesday, Russia's Federal Security Service, known as the FSB, announced that together with Russia's Ministry of Internal Affairs, it had detained more than 30 individuals across 11 regions of the country - including Moscow, Crimea and St. Petersburg. Subsequently, authorities charged 25 of them with selling stolen credit and debit card that traced to Russian as well as foreign financial institutions. Authorities have accused the individuals, who include Russian, Ukrainian and Lithuanian citizens, of creating more than 90 online stores to sell stolen data, as well as using the stolen card data to purchase and resell more than $1 million worth of goods. Authorities say that when they searched suspects' residences, they also seized firearms, illegal drugs, gold bars, precious coins, as well as cash: $1 million in U.S. dollars as well as 3 million rubles (worth $39,000). The infrastructure being used by the alleged criminal enterprise has been shuttered, authorities say. The FSB said one of the individuals it arrested had previously been jailed for similar offenses.
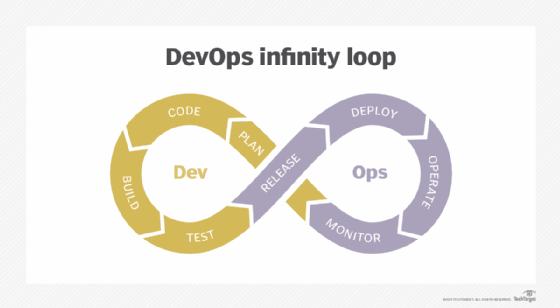
The First Way is to think about the performance of an entire system or process, rather than a specific silo or team. From the first line of code to successful deployment, IT departments must focus on the big picture, and emphasize larger organizational goals rather than smaller local ones. The Second Way focuses on feedback loops. A DevOps culture should accelerate and amplify feedback loops, enabling admins to identify and address any issues as quickly as possible. The Third Way fosters a culture of continual experimentation and learning, which requires IT teams to take risks and set aside time for innovation. In a DevOps culture, celebrate -- don't admonish -- rapid experimentation and rapid failure. It's this cycle of experimentation, failure and lessons learned that continually improves a DevOps practice over time. Naturally, DevOps will shake up the way any IT organization makes and measures progress. Encourage collaboration across department lines, and listen and take action on team feedback.

Don't neglect the bread-and-butter stuff, either. As Senior Reporter Gregg Keizer explains in "How businesses can save money when everyone needs Office to work from home," you can cut costs substantially by switching to the right Office flavor. Gregg's advice may hold beyond the short term, as businesses discover that employees can work just as well at home as they do in an office. So we're paying for office space...why? Cost savings sometimes arrive in the form of needed functionality you weren't aware you already had. In "10 SD-WAN features you're probably not using, but should be," Network World contributor Neil Weinberg clues in SD-WAN customers: You may not know this, but zero-touch provisioning, application-aware routing, microsegmentation, and a bunch of other stuff may already be part of your SD-WAN solution. If you were planning on procuring any of those things separately, you don't have to. Recommendations like these will sound familiar to those who have endured previous downturns. Prioritize. Cut bait on bloated projects with uncertain return. Consider free stuff, even if it might not have every feature you want.
Ministry of Defence releases defence data management strategy

According to the report, the MoD sees more effective use of data, information and the systems that manage and process data as “vital enablers of both operational advantage and business transformation”. “New and emerging technologies can provide better capabilities to our operations and greater efficiency in our supporting functions, but success will require us to consider data differently,” it noted. “If we are to deliver improvements at speed and scale, then we must start with managing our data far more effectively than we do today,” the report added. A set of seven strategic objectives is outlined in the document. These goals relate to areas such as improvements of the availability and accessibility of defence data and implementation of data governance across the MoD, so the department can ensure the accountabilities and responsibilities for its data management. The document also outlines goals such as improving the quality and veracity of the data at the MoD, ensuring the integrity, confidentiality and security of data, and driving the consistent use of decision-making data across the department to improve coherency in the information produced from it.
Adventures in Graph Analytics Benchmarking
With all the attention graph analytics is getting lately, it’s increasingly important to measure its performance in a comprehensive, objective, and reproducible way. I covered this in another blog, in which I recommended using an off-the-shelf benchmark like the GAP Benchmark Suite* from the University of California, Berkeley. There are other graph benchmarks, of course, like LDBC Graphalytics*, but they can’t beat GAP for ease of use. There’s significant overlap between GAP and Graphalytics, but the latter is an industrial-strength benchmark that requires a special software configuration. Personally, I find benchmarking boring. But it’s unavoidable when I need performance data to make a decision. Obviously, the data has to be accurate. But it also has to be relevant to the decision at hand. It’s important that my use of a particular benchmark is aligned with its intended purpose. That’s why the performance comparison shown in Figure 1 had me scratching my head. It compares the PageRank performance of RAPIDS cuGraph* and HiBench*. The latter is a big data benchmark developed by some of my Intel colleagues to measure a wide range of analytics functions—not just PageRank.
This 5G smartphone comes with Android, Linux - and a keyboard.

London-based Planet Computers is on a mission to reinvent the iconic Psion Series 5 PDA for the smartphone age. Although mobile professionals -- especially those old enough to remember the 1997 Series 5 with affection -- are often open to the idea, the company's previous efforts, the Gemini PDA and Cosmo Communicator, have had their drawbacks. The Gemini PDA, for example, is a landscape-mode clamshell device that, despite a great keyboard, is difficult to make and take calls on and only has one camera -- a front-facing unit for video calling. The Cosmo Communicator adds a small external touch screen for notifications and some basic functions plus a rear-facing camera, but you still have to open the clamshell to do anything productive. The Astro Slide, announced today via a crowdfunding campaign on Indiegogo, has a new design with one large (6.53-inch) screen that slides open to reveal the keyboard, transforming the device from a portrait smartphone to a landscape PDA via a patented RockUp mechanism.
A Practical Guide to Data Obfuscation
The simplest way to obfuscate data is by masking out or redacting characters or digits with a fixed symbol. This is often used for credit card numbers where either the leading or the tailing digits are crossed out with an “X”. ... For more advanced anonymization, we need to look at functions that support something called differential privacy. The goal here is to apply statistical methods to modify content at a larger scope, like at the table level. Imagine, say, that you need to analyze customer data but require the birthday in order to group customers by demographics. Randomizing this piece of PII is not a good idea, as it would change the overall composition of data, often making it equally distributed across the possible value range. Instead, what is needed is a function that changes every birthday so the overall distribution stays nearly the same, but individuals are no longer identifiable. It may mean adding a few days or a few weeks to each date, but is a factor of the number of overall datasets. Query engines may offer the diff_privacy() function (or something with a similar name) for that purpose, allowing you to introduce uncertainty or jitter into your sensitive data so that the above requirement can be fulfilled.

Many of DuckDB’s features are counterparts to what’s found in bigger OLAP products, even if smaller in scale. Data is stored as columns rather than rows, and query processing is vectorized to make the best use of CPU caching. You won’t find much in the way of native connectivity to reporting solutions like Tableau, but it shouldn’t be difficult to roll such a solution manually. Aside from bindings for C++, DuckDB also connects natively to two of the most common programming environments for analytics, Python and R. ... The goal behind HarperDB is to provide a single database for handling structured and unstructured data in an enterprise—somewhere between a multi-model database like FoundationDB and a data warehouse or OLAP solution. Ingested data is deduplicated and made available for queries through the interface of your choice: SQL, NoSQL, Excel, etc. BI solutions like Tableau or Power BI can integrate directly with HarperDB without the data needing to be extracted or processed. Both enterprise and community editions are available.
Slack redesigns app as Microsoft Teams hits 44 million users

The Slack redesign contains several elements that make the product look more like Teams. The top of the app now features a search bar and navigation buttons. Slack also added tabs for files and notifications, such as when a user tags someone in a message. Even more significant, Slack now lets paid users place channels within folders. For example, a user could put several channels in a "marketing team" folder. The setup is similar to how Teams groups channels -- except in Slack, each user gets to customize the layout. The inability to organize channels into groups had been a stumbling block for many Slack users, said Irwin Lazar, analyst at Nemertes Research. Slack should be able to get some companies to switch from free to paid plans with the introduction of folders as a premium service, he said. The redesign also lays the groundwork for Slack to introduce more real-time communications features. A newly reorganized sidebar within channels features a prominent phone icon that lets users begin a video call.
Quote for the day:
"Leadership offers an opportunity to make a difference in someone's life, no matter what the project." -- Bill Owens

No comments:
Post a Comment