Data Science Is Now Bigger Than 'Big Data'

The now-ubiquitous term “big data” begins its meteoric rise in lockstep with cloud computing’s fall, suggesting that the public’s focus on hardware rental was rapidly replaced with how all of that computing power was being used: to analyze massive datasets. In contrast, “data science” and “deep learning” both take off in 2013 and accelerate over 2014. Interestingly, despite deep learning’s Cambrian Explosion over the past few years, search interest appears to have leveled off as of last January, perhaps suggesting that we are now searching more for the individual applications of deep learning rather than the phrase itself. Most significantly, as of January of this year, “data science” has surpassed “big data” in total search volume. Just as cloud computing’s hardware focus gave way to big data’s emphasis on what we do with all that hardware, so too has the focus shifted now from assembling huge piles of data to the people and processes making sense of all of that data. While it may be entirely coincidental, it is interesting to note that data science and deep learning burst into popularity in the immediate aftermath of Edward Snowden’s June 2013 disclosures, raising questions of whether vastly increased public awareness of data mining led to increased interest in those fields.
How to write a business continuity plan: the easy way
The most obvious reason to implement a BCP is to ensure that your organisation remains productive in the event of a disruption. Customers must still be able to use your services, employees must be able to continue doing their job and you can’t allow yourself to face a huge backlog of work as delays continue. But business continuity isn’t only about short-term goals. The cyber security landscape has become increasingly volatile in recent years, with cyber crime continuing to spiral and organisations’ reliance on technology leading to vast numbers of accidental and deliberate data breaches. As a result, organisations need to prove to customers and stakeholders that they are prepared for anything. Business continuity is especially important for OES (operators of essential services) and DSPs (digital service providers), as the delays could either be widespread or cause major headaches. To ensure that such organisations are sufficiently prepared for risks, the EU adopted the NIS Directive, which was transposed into UK law as the NIS (Network and Information Systems) Regulations 2018.
New Flat Lens Enables Focus-Free Cameras With Drastically Reduced Weight

“Our flat lenses can drastically reduce the weight, complexity and cost of cameras and other imaging systems, while increasing their functionality,” said research team leader Rajesh Menon from the University of Utah. “Such optics could enable thinner smartphone cameras, improved and smaller cameras for biomedical imaging such as endoscopy, and more compact cameras for automobiles.” In Optica, The Optical Society’s (OSA) journal for high impact research, Menon and colleagues describe their new flat lens and show that it can maintain focus for objects that are about 6 meters apart from each other. Flat lenses use nanostructures patterned on a flat surface rather than bulky glass or plastic to achieve the important optical properties that control the way light travels. “This new lens could have many interesting applications outside photography such as creating highly efficient illumination for LIDAR that is critical for many autonomous systems, including self-driving cars,” said Menon. Conventional cameras, whether used in smartphones or for microscopy, require focusing to ensure that the details of an object are sharp. If there are multiple objects at different distances from the camera, each object must be focused separately.
Open-source security: This is why bugs in open-source software have hit a record high

A large source of newly found bugs comes from Google's open-source fuzzing tools, such as OSS-Fuzz, which by 2018 had helped find 9,000 flaws in two years. As of January 2020, it's helped find 16,000 bugs in 250 open-source projects. WhiteSource found that 85% of open-source vulnerabilities are disclosed and have a fix already available. However, it notes that some users are not aware of these fixes because only 84% of known open-source bugs make it to the National Vulnerability Database (NVD). "Information about vulnerabilities is not published in one centralized location, rather scattered across hundreds of resources, and sometimes poorly indexed – often making searching for specific data a challenge," it notes. WhiteSource last year brought its vulnerability database to GitHub to support its security-alerts service. GitHub scans project dependencies for vulnerabilities in projects written in PHP, Java, Python, .NET, JavaScript and Ruby. It's helped developers find and fix millions of known flaws in dependencies. "Our concern is that, while these tools will help to report vulnerability issues in a proper manner, they will probably only aggravate the issue with software developers who are already struggling to keep up with the increased rate," WhiteSource notes.
Phishing attacks exploit YouTube redirects to catch the unwary

Attackers are increasingly exploiting the fact that email gateways turn a blind eye to links to popular sites such as YouTube, in order to phish passwords from unsuspecting computer users. Researcher Ashley Trans of Cofense highlighted the threat in a blog post describing a recent phishing campaign. In the attack, an unsuspecting user receives an email which purports to come from SharePoint, claiming that a new file has been uploaded to his company’s SharePoint site. ... Closer examination reveals that although the link in the email does indeed point initially at YouTube (youtube.com), it also sends a series of parameters telling YouTube to redirect any traffic to a URL at <companyname>[.]sharepointonline-ert[.]pw, which in turn ultimately takes the user’s browser to its final destination: a phishing page hosted on a legitimate Google site, googleapis.com. ... The disappointing truth is that YouTube provides a method for anyone to create a link at youtube.com, which automatically redirects browsers to third-party phishing sites without any warning.
CIO interview: Miguel Rio Tinto, Emirates NBD

It has been an enormous effort and a challenging journey, with the organisation completely changed to adopt agile practices. The company is about 65% and 75% into its digital transformation cycle. “We still have some important milestones to achieve but by the end of 2020, we will be working and using the same technologies as cloud-natives and we will be comprised of 100% cloud-enabled, agile teams who collaborate with the business.” To achieve his mission, Rio Tinto has a Dubai-headquartered technology operation of around 1,200 internal and external staff. “We brought in managers from banks in Australia, Canada, the US, Turkey, Europe, India and Dubai. Half of the managers are new to organisation and over the course of 18 months, half of our engineers were also replaced,” he says. The 1,200 IT staff are arranged into 60 different sets of “squads”, which directly collaborate with business units, including retail, wholesale and enterprise.
Want To Be A Cyber Security Pro? It Goes Way Beyond Learning To Code

Learning Linux for the basics, such as terminal usage, SSH (Secure Shell), users and permissions, processes, networking, databases could be very handy as well. Those not accustomed to the Linux environment and its command line, etc. can first learn them using a bunch of web resources and tutorials to begin. Core Linux commands, input/output redirecting and piping, file manipulation, basic network configuration and user account management are some of the key things to focus here, which can be incredibly useful for security expertise later on. But as cybersecurity is a broad field, experts need to have a solid grasp on networking also and for this learner may have to spend hundreds of hours learning the nitty-gritty of company networks, and how hackers may break them to gain access to sensitive data. According to many security experts, professionals in the space may also choose to learn more about how networks and systems operate and less programming. Network security specialists identify, anticipate and fix security threats to computer networks. They additionally perform an essential function in keeping the integrity and secrets of a company’s data and knowledge systems.
Microsoft: WSL2's Linux kernel will be delivered to Windows 10 users via Windows Update

Specifically, Microsoft has decided to remove the Linux kernel from the Windows OS image with WSL2. Instead, the company will deliver it to users' machines using Windows Update. Users will be able to manually check for new kernel updates by clicking the "Check for Updates" button or by waiting for Windows to do this automatically. "Our end goal is for this change to be seamless, where your Linux kernel is kept up to date without you needing to think about it. By default this will be handled entirely by Windows, just like regular updates on your machine," said Microsoft Program Manager Craig Loewen in a blog post today outlining the coming change. Loewen noted that initially, Windows 10 2004 users and Insider testers using Slow Ring preview builds will temporarily need to manually install the Linux kernel. They'll receive within "a few months" an update that will add automatic install and servicing capabilities. (In fact, Slow Ring testers just got today, March 13, a new Windows 10 2004 test build, 19041.153, which includes this servicing change to WSL2.)
Commission Calls for Revamping US Cybersecurity
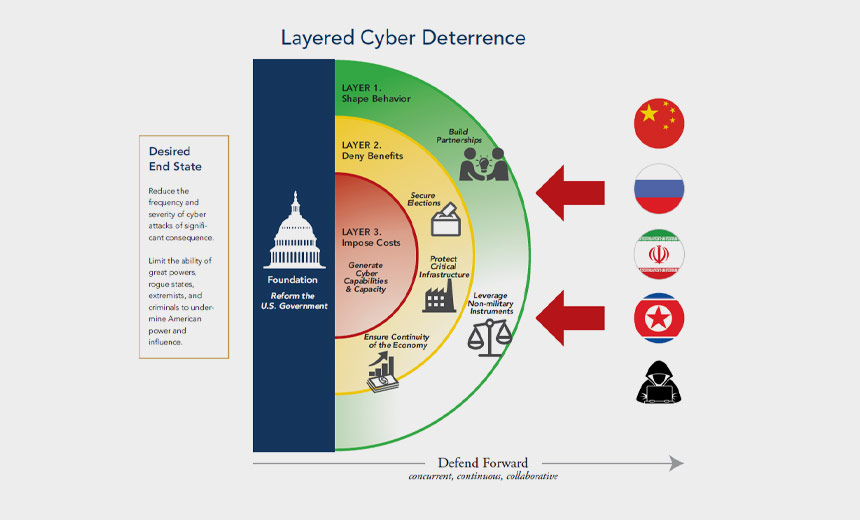
The commission, which was mandated under the 2019 National Defense Authorization Act, is co-chaired by Sen. Angus King, I-Maine, and Rep. Mike Gallagher, R-Wis. It also includes Trump Administration officials. Its mission is to develop "a consensus on a strategic approach to defending the United States in cyberspace against cyberattacks of significant consequences," according to the report. The report lists China, Russia, Iran and North Korea as major threats to cybersecurity in the U.S., pointing at intellectual property theft carried out by Chinese operators and the election meddling carried out by Russian actors that has damaged public trust in the integrity of American elections. The report puts much of its emphasis on election security and how other countries are attempting to manipulate the vote through hacking and disinformation. "If we don't get election security right, deterrence will fail and future generations will look back with longing and regret on the once powerful American Republic and wonder how we screwed the whole thing up," King and Gallagher note in the report.
Maintaining Mental health on Software Development Teams
Work-related anxiety and mental disorders are becoming a common challenge among tech companies. According to the International Journal of Social Sciences, software developers have a considerably higher chance of experiencing fatigue, burnout, anxiety, and stress, compared to their colleagues who perform mechanical tasks. Deteriorating mental health not only threatens the wellbeing of employees, but the companies’ overall productivity. Researchers from the Institute of Software Technologies in Stuttgart found that mentally-exhausted or depressed developers produce a lower quality of code and tend to miss deadlines. Today, tech companies are realizing the importance of mental health and taking action to ensure their dedicated development teams stay healthy and sane. Here, at Beetroot, we strive to create a homely and comfortable atmosphere that minimizes the pressure felt on our teams. However, despite our best efforts, there are still challenging times. We recently spoke with our HR representative and psychologist, Vova Vovk, about mental health.
Quote for the day:
"If you are not willing to give a less experienced qualified professional a chance, don't complain you are charged double for a job worth half." -- Mark W. Boyer
No comments:
Post a Comment