Google says Microsoft Edge isn't secure.

"Google recommends switching to Chrome to use extensions securely," says a pop-up. Oh, so Edge is insecure? That's terrible. Oddly, when I tried the browser, I found it a touch faster and privacy-friendlier than Google's. It didn't seem so insecure. Why would Google be so worried on my behalf? Worse, Techdows reported that Google is also offering more desperate warnings for users of Google Docs, Google News and Google Translate. The essential message: don't pair these with Edge. This verged on terrible mean-spiritedness, I feared. After all, Edge is based on Google's own Chromium platform. Just as I was about to punish Google by using Bing for a day, another piece of troubling information assaulted me. According to PC World, Microsoft is apparently telling those who use Edge and go to the Chrome web store to get an extension: "Extensions installed from sources other than the Microsoft Store are unverified, and may affect browser performance." Can't we rely on anything these days? Naturally, I instantly contacted Google to ask in what way Edge was insecure. Without pausing for breath or to curse at the new space bar issues with my MacBook Air, I asked Microsoft why extensions from the Chrome store might make Edge a little edgy.
Multi-Runtime Microservices Architecture

One of the well-known traditional solutions satisfying an older generation of the above-listed needs is the Enterprise Service Bus and its variants, such as Message Oriented Middleware, lighter integration frameworks, and others. An ESB is a middleware that enables interoperability among heterogeneous environments using a service-oriented architecture. While an ESB would offer you a good feature set, the main challenge with ESBs was the monolithic architecture and tight technological coupling between business logic and platform, which led to technological and organizational centralization. When a service was developed and deployed into such a system, it was deeply coupled with the distributed system framework, which in turn limited the evolution of the service. This often only became apparent later in the life of the software. Here are a few of the issues and limitations of each category of needs that makes ESBs not useful in the modern era. In traditional middleware, there is usually a single supported language runtime, which dictates how the software is packaged, what libraries are available, how often they have to be patched, etc.
Intel takes aim at Huawei 5G market presence

Intel on Monday introduced a raft of new processors, and while updates to the Xeon Scalable lineup led the parade, the real news is Intel's efforts to go after the embattled Huawei Technologies in the 5G market. Intel unveiled its first ever 5G integrated chip platform, the Atom P5900, for use in base stations. Navin Shenoy, executive vice president and general manager of the data platforms group at Intel, said the product is designed for 5G's high bandwidth and low latency and combines compute, 100Gb performance and acceleration into a single SoC. "It delivers a performance punch in packet security throughput, and improved packet balancing throughput versus using software alone," Shenoy said in the video accompanying the announcement. Intel claims the dynamic load balancer native to the Atom P5900 chip is 3.7 times more efficient at packet balancing throughput than software alone. Shenoy said Ericsson, Nokia, and ZTE have announced that they will use the Atom P5900 in their base stations. Intel hopes to be the market leader for silicon base station chips by 2021, aiming for 40% of the market and six million 5G base stations by 2024.
Can Deutsche Bank’s PaaS help turn the bank around?

It’s a rapid success story for a highly leveraged and highly regulated international bank – which is in the midst of a turnaround effort and that registered a loss of €5.7 billion ($7.4 billion) last year – and one that even has management considering whether Fabric is good enough to sell to rival banks to eventually turn its technology investments into a revenue stream. A key problem Fabric helped solve was one that confronted the bank’s new leadership when it arrived in 2015: a sizeable virtual machine (VM) estate that was only being utilised at a rate of around eight percent. “The CIOs got together and realised they had a problem to fix because this is just money that’s bleeding out to the organisation,” platform-as-a-service product owner at Deutsche Bank, Emma Williamson, said during a recent Red Hat OpenShift Commons event in London. So the bank set out to drastically modernise its application estate around cloud native technologies like containers and Kubernetes, all with the aim of cutting this waste tied to its legacy platforms and help drive a broader shift towards the cloud.
The 9 Best Free Online Data Science Courses In 2020

You don't have to spend a fortune and study for years to start working with big data, analytics, and artificial intelligence. Demand for "armchair data scientists" – those without formal qualifications in the subject but with the skills and knowledge to analyze data in their everyday work, is predicted to outstrip demand for traditionally qualified data scientists in the coming years. ... Some of these might require payment at the end of the course if you want official certification or accreditation of completing the course, but the learning material is freely available to anyone who wants to level up their data knowledge and skills. ... As it is a Microsoft course, its cloud-based components focus on the company's Azure framework, but the concepts that are taught are equally applicable in organizations that are tied to competing cloud frameworks such as AWS. It assumes a basic understanding of R or Python, the two most frequently used programming languages in data science, so it may be useful to look at one of the courses covering those that are mentioned below, first.
Microsoft Makes Progress on PowerShell Secrets Management Module
The idea behind the module is that it has been difficult for organizations to manage secrets securely, especially when running scripts across heterogeneous cloud environments. Developers writing scripts want them to run across different platforms, but that might involve handling multiple secrets and multiple secrets types. The team sees PowerShell serving as a connection point between different systems. Consequently, it built an abstraction layer in PowerShell that can be used to manage secrets, both with local vaults and remote vaults, Smith explained in a November Ignite talk. The module helps manage local and remote secrets in unified way, Smith added. It might be used to run a script in various environments, where just the vault parameter would need to be changed. Scripts could be shared across an organization, and it wouldn't be necessary to know the local vaults of the various users. Keys could be shared with users in test environments, but deployment keys could be individualized. It would be less necessary to hard-code secrets into scripts. The PowerShell Secret Management Module is being designed to work with various vault extensions.
Facebook sues SDK maker for secretly harvesting user data

According to court documents obtained by ZDNet, the SDK was embedded in shopping, gaming, and utility-type apps, some of which were made available through the official Google Play Store. "After a user installed one of these apps on their device, the malicious SDK enabled OneAudience to collect information about the user from their device and their Facebook, Google, or Twitter accounts, in instances where the user logged into the app using those accounts," the complaint reads. "With respect to Facebook, OneAudience used the malicious SDK – without authorization from Facebook – to access and obtain a user's name, email address, locale (i.e. the country that the user logged in from), time zone, Facebook ID, and, in limited instances, gender," Facebook said. Twitter was the first to expose OneAudience's secret data harvesting practices on November 26, last year. Facebook confirmed on the same day. In a blog post at the time, Twitter also confirmed that beside itself and Facebook, the data harvesting behavior also targeted the users of other companies, such as Apple and Google.
Product Development with Continuous Delivery Indicators

Software product delivery organizations deliver complex software systems on an evermore frequent basis. The main activities involved in the software delivery are Product Management, Development and Operations (by this we really mean activities as opposed to separate siloed departments that we do not recommend). In each of the activities many decisions have to be made fast to advance the delivery. In Product Management, the decisions are about feature prioritization. In Development, it is about the efficiency of the development process. And in Operations, it is about reliability. The decisions can be made based on the experience of the team members. Additionally, the decisions can be made based on data. This should lead to a more objective and transparent decision making process. Especially with the increasing speed of the delivery and the growing number of delivery teams, an organization’s ability to be transparent is an important means for everyone’s continuous alignment without time-consuming synchronization meetings.
Can Machines And Artificial Intelligence Be Creative?
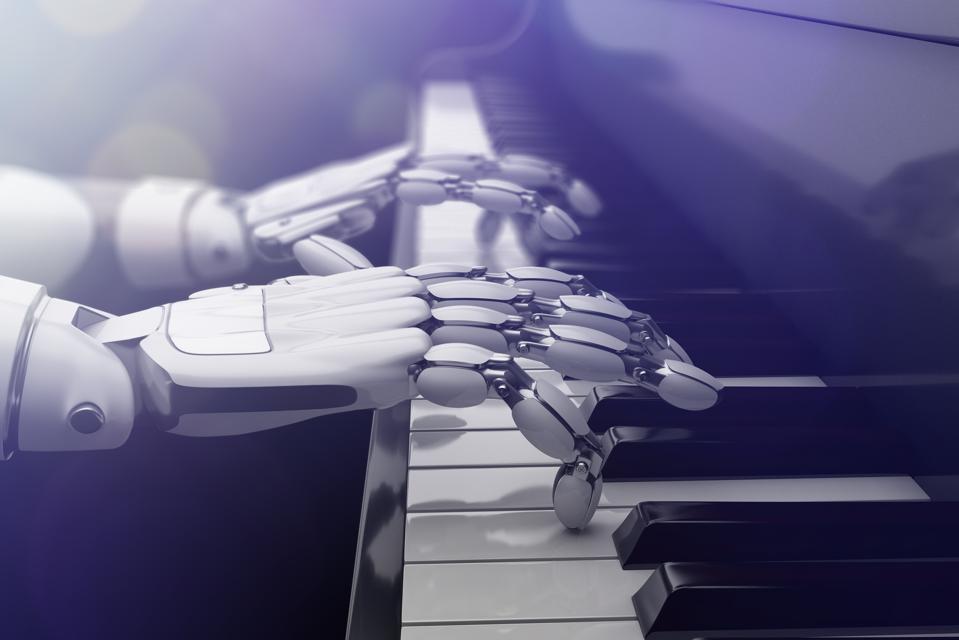
If AI can enhance creativity in visual art, can it do the same for musicians? David Cope has spent the last 30 years working on Experiments in Musical Intelligence or EMI. Cope is a traditional musician and composer but turned to computers to help get past composer’s block back in 1982. Since that time, his algorithms have produced numerous original compositions in a variety of genres as well as created Emily Howell, an AI that can compose music based on her own style rather than just replicate the styles of yesterday’s composers. In many cases, AI is a new collaborator for today’s popular musicians. Sony's Flow Machine and IBM's Watson are just two of the tools music producers, YouTubers, and other artists are relying on to churn out today's hits. Alex Da Kid, a Grammy-nominated producer, used IBM’s Watson to inform his creative process. The AI analyzed the "emotional temperature" of the time by scraping conversations, newspapers, and headlines over a five-year period. Then Alex used the analytics to determine the theme for his next single.
Educating Educators: Microsoft's Tips for Security Awareness Training
The key challenge is creating an engaging, relatable training course that effectively teaches employees the concepts they need to know, Sexsmith said. Sexsmith pointed to a few tricks he uses in his programs. One of these is the "Social Proof Theory," a social and psychological concept that describes how people copy other people's behavior – if your colleagues are doing a training, you'll do it, too. Gamification also helps: "People want to learn; people want to master skills, but there's also a competitive nature around that," he said. Some trainings use videos that make security concepts more accessible. One problem, he said, is lessons that aren't reinforced aren't retained. Humans forget half of new information learned within an hour and 70% of new information within a day. "By lunchtime, you're going to forget 50% of the stuff I'm up here saying," he joked to his morning audience. To fight this, Microsoft uses a training reinforcement platform called Elephants Don't Forget to help employees build muscle memory around new concepts. During the gap between trainings, the program sends participants two daily emails with a link to questions tailored to the course.
Quote for the day:
"Eventually relationships determine the size and the length of leadership." -- John C. Maxwell
No comments:
Post a Comment