Can you put your trust in AIops?

The objective was and is obvious. Since most of these tools have been data gathering tools and analytics tools from the beginning, adding AI allows them to learn from that data rather than just externalize issues with the services under management. In some cases, they can correct issues using preprogrammed routines, such as restarting a server or blocking an IP address that seems to be attacking one of your servers. Now that we’re a few years into this paradigm and its technology offerings, we’re starting to note some patterns—some good, and some not so good. Let’s explore both. As far as what’s working, AIops tools in many instances are ops tools in their fourth, fifth, or sixth generations. Moreover, most of them have had public cloud management in mind for a while and are able to bridge the gap between on-premises legacy system management and managing applications and services in the public clouds. They are capable tools for managing and monitoring cloud, multicloud, legacy, and even IoT and edge-based systems. This ability to support complex system heterogeneity is really the true value of the ops tools, and why they are important to those implementing cloud or noncloud systems.
Server sales projected to decline 10% due to coronavirus

Vladimir Galabov, principal analyst for data-center compute in Omdia’s cloud and data-center research practice, also expects to see server shipments impacted by the coronavirus driving a prolonged holiday period in China. “I think the majority of the hit will be in the Chinese market,” he said. “This does impact server shipments globally as China represents about 30% of server shipments worldwide. So, I expect the quarterly decline to be more significant than the seasonal 10%. I expect that China will have a 5% additional downward impact on the growth.” He added that Q4 of 2019 did significantly overachieve his expectations due to cloud service providers making massive purchases. Omdia expected servers shipped in 2019 to be flat compared to 2018 based on data from 1Q19-3Q19. Instead, it was up 2% to 3% for the year, thanks to the fourth-quarter spurt. And servers aren’t the only products taking a hit. DigiTimes says that should the outbreak of the coronavirus last until June, sales of smartphones in the country would be slashed by about 30%, from a projected 400 million units to 280 million units in 2020.
Ohio man arrested for running Bitcoin mixing service that laundered $300 million

The Bitcoin blockchain is a public database. In many cases, purchases of new Bitcoin funds aquired by a user can sometimes be linked to a credit card, bank account, or PayPal account. Helix functioned as a Bitcoin mixer (Bitcoin tumbler), a type of service that takes funds from a user, split the sum into small parts, and using thousands of transactions, sends and reassembles the original funds at a new Bitcoin address, in an effort to hide the original funds under a cloud of micro-transactions. "The sole purpose of Harmon's operation was to conceal criminal transactions from law enforcement on the Darknet, and because of our growing expertise in this area, he could not make good on that promise," Don Fort, Chief, IRS Criminal Investigation, said today in a DOJ press release. "Working in tandem with other sites, he sought to be the 'go-to' money launderer on the Darknet, but our investigators once again played the role of criminal disrupters, unraveling the interlinked web from one tentacle to another," Fort said.

With data projects - especially those which continuously output a data product - having metrics in place to fill this role is essential. The range of metrics helps elaborate on the general idea of the customer wanting to "improve" the quality of the data. With this in mind, projects of a certain scale should consider investing in a metrics team. This team needs to handle the collection of data, the (human) annotation of that data as well as the regular computation of metrics. We found that while it is useful to design a single metric that summarizes the quality and progress of the product, this is often of less value within the team and so we design a number of metrics as required by the components of the products and the dimensions that we wish to optimize for. We also innovated around the idea of a data wallow. This is a semi-structured meeting in which an engineer presents some data and the team as a whole provides feedback and insights into the characteristics of the data and the performance of any inference being made.
LokiBot Impersonates Popular Game Launcher and Drops Compiled C# Code File

LokiBot, which has the ability to harvest sensitive data such as passwords as well as cryptocurrency information, proves that the actors behind it is invested in evolving the threat. In the past, we have seen a campaign that exploits a remote code execution vulnerability to deliver LokiBot using the Windows Installer service, a Lokibot variant that uses ISO images, and a variant with an improved persistence mechanism using steganography. Recently, we discovered LokiBot (detected by Trend Micro as Trojan.Win32.LOKI) impersonating a popular game launcher to trick users into executing it on their machines. Further analysis revealed that a sample of this variant employs a quirky, installation routine that involves dropping a compiled C# code file. This unusual LokiBot variant, which uses a “compile after delivery” detection evasion technique, was proactively detected and blocked by machine learning detection capabilities built into Trend Micro solutions as Troj.Win32.TRX.XXPE50FFF034. The infection starts with a file that is supposedly the installer of the Epic Games store. This fake installer was built using the NSIS (Nullsoft Scriptable Install System) installer authoring tool.
Android facial recognition is more secure than you think

After careful consideration, I've drawn a conclusion that isn't meant to shame or blame but to highlight what I believe is at the heart of the concerns about the Android facial recognition system. The pushback to facial recognition isn't about the ability to crack it--it's about the ability to abuse it. I'm not talking about the ability of a rogue user being able to abuse your mobile phone via facial recognition; this is about companies and governments being able to use facial recognition in such a way that might invade citizens' privacy. I believe that is why so many people are concerned about how much facial recognition systems have improved. If the Android system is any indication, it is certainly ready for prime time. However, as far as a system to secure your mobile device? You shouldn't worry about it. Cracking the Android facial recognition system isn't easy--just short of someone taking your phone and forcing you to unlock it, chances are slim it's going to be cracked. Of course, if someone wants to get inside your phone that badly, it wouldn't matter if the device used facial recognition, fingerprint biometrics, or a password.
What’s next for serverless architecture?
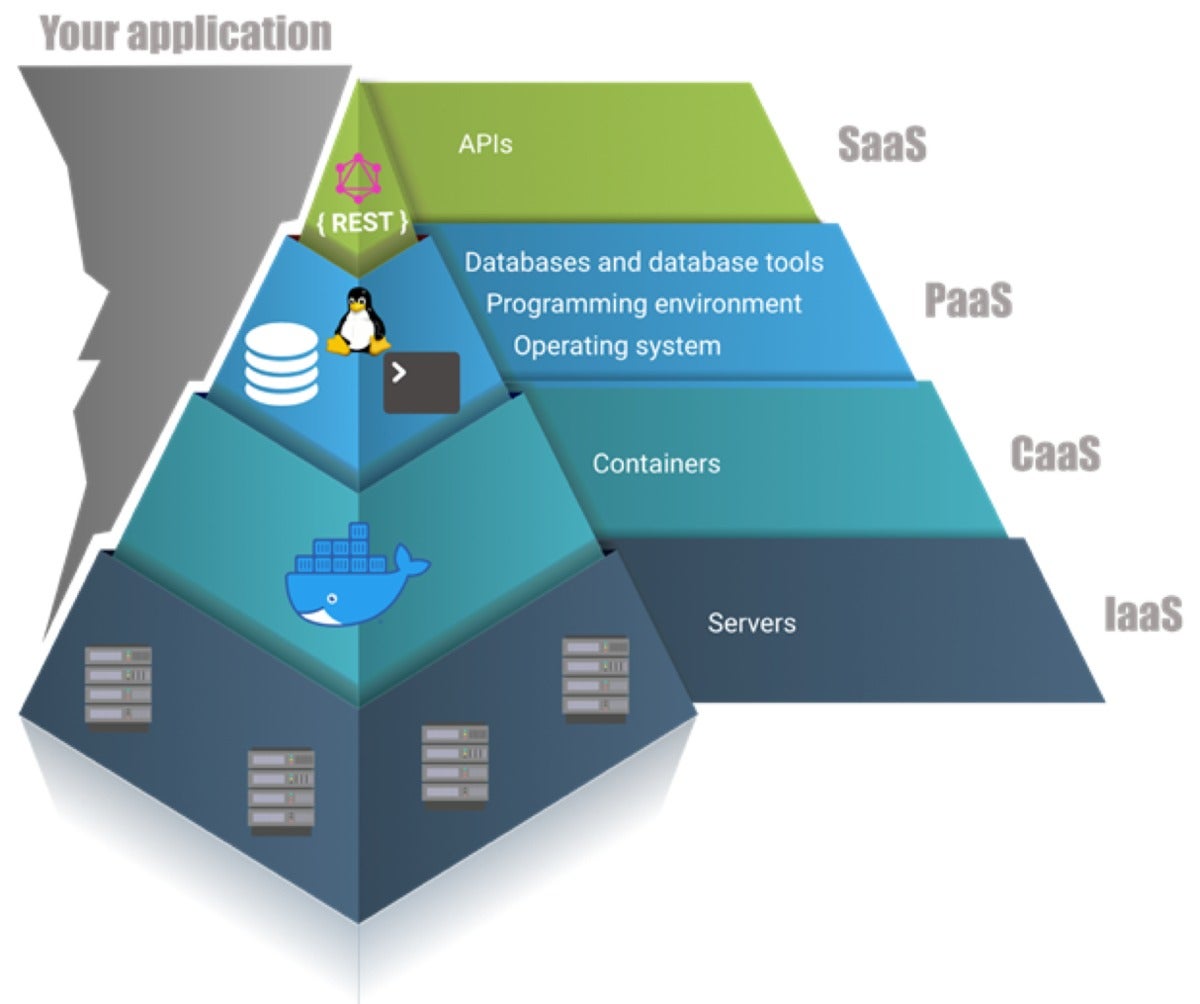
Container platforms are the latest incarnation of IaaS. Instead of offering full-blown server hosts, CaaS providers let you host your services or applications within containers, and manage the containers on your behalf. Containers are more efficient at utilizing underlying host resources than virtual machines. One can think of containers as “tiny machines.” They launch quickly, and multiple instances can run on a single server. CaaS providers offer tools to deploy containers on servers and to scale the number of container instances up and down. The most advanced offerings completely manage the underlying servers for you, allowing your company to focus on the code (or containers) instead of the infrastructure. CaaS has quickly become one of the building blocks for PaaS and SaaS, resulting in a layered architecture. There has been a shift toward developing applications as high on the pyramid as possible. Many complex applications are still a combination of SaaS, PaaS, and CaaS, since the available platforms are not flexible enough to deliver everything an application needs. By relying as much as possible on SaaS, you free yourself from provisioning and scalability concerns. For the remaining parts, companies typically resort to running containers, which means they still have configuration and provisioning concerns.
Serverless computing: Ready or not?
Serverless computing can lighten IT workloads in several ways, most noticeably by freeing staff from routinely managing server performance, reliability, maintenance and security tasks. "The need to implement health checks to ensure application uptime, managing the underlying OS in regard to applying the latest security patch, or ensuring the underlying infrastructure has been provisioned with enough capacity to handle peak workloads are all things that are essentially handled for you by the serverless platform," Austin says. Serverless also lightens developers' workloads. "Writing less code, particularly infrastructure code, is attractive to the IT bottom line," Austin notes. "Having more developers deploying business functionality, while letting the serverless technology handle infrastructure provisioning, is a powerful benefit to an IT organization." Accelerating development speed can also make organizations nimbler and more innovative. Serverless is the fastest way to turn an idea into a functional solution, Kralj says. "The approach is perfect for rapid application development; you can now achieve it with just a few lines of code."
Google to Samsung: Stop messing with Linux kernel code. It's hurting Android security

"Android has been reducing the security impact of such code by locking down which processes have access to device drivers, which are often vendor-specific," explains Horn. An example is that newer Android phones access hardware through dedicated helper processes, collectively known as the Hardware Abstraction Layer (HAL) in Android. But Horn says vendors modifying how core parts of the Linux kernel work undermines efforts to "lock down the attack surface". Instead, he suggests handset makers use direct hardware access features already supported in Linux, rather than customizing Linux kernel code. Horn says some of the custom features that Samsung added are "unnecessary" and wouldn't affect the device if they were removed. He speculated that PROCA is meant to restrict an attacker who has already gained read and write access on the kernel. But he reckons Samsung could be more efficient by directing engineering resources to preventing an attacker from getting this access in the first place. "I believe that device-specific kernel modifications would be better off either being upstreamed or moved into userspace drivers, where they can be implemented in safer programming languages and/or sandboxed, and at the same time won't complicate updates to newer kernel releases," explained Horn.
Mono: From Xamarin to WebAssembly, Blazor, and .NET 5

With .NET 5, we are unifying the implementation of the class libraries, yet providing two options of runtimes for users. At a high-level, we have a high-throughput, high-performance runtime in CoreCLR, and we have the lightweight, (but not as fast) Mono runtime. Each runtime has been tuned for the workloads where they have been used the most — CoreCLR, for server and desktop applications, and Mono, for mobile and lightweight uses, such as WebAssembly. Also in .NET 5, we will have a unified runtime that can execute your C# or F# code on all the platforms that we support. On some of the platforms, users will be able to choose the runtime they want to use, and on other platforms, there will be a single runtime to use. For example, for desktop applications on Windows, only the CoreCLR runtime is suitable, and for iOS, only the Mono runtime is available. Now, historically, Mono has had two execution and code generation engines. One, we called the "mini" code generator, and it produced native code very quickly, but also without many optimizations.
Quote for the day:
"One measure of leadership is the caliber of people who choose to follow you." -- Dennis A. Peer
No comments:
Post a Comment