What to Look Out For When Selecting a DRaaS Provider

Before exploring DRaaS, your organization should have a business impact analysis. In performing a current business impact analysis, you will be able to posit what would happen in the event of a disaster or disruption of business operations. ... When picking which DRaaS provider is right for you, use this information to determine if providers can accommodate your needs. After figuring out what your disaster recovery requirements are exactly, you can ask questions of providers in order to ascertain if they can support your needs. In the event that you were to experience data loss or corruption, learn the procedures of the providers in that situation by asking questions such as: How many copies of your backups are available? Where are those backups located? Is the provider able to recreate an image of your data at a specific, previous point from available backups? In calendar terms, how far back are backups accessible? What is the provider’s protocol when you perform a failover to DRaaS and are ready to go back to your standard environment afterward?
Google researchers disclose vulnerabilities for 'interactionless' iOS attacks

According to the researcher, four of the six security bugs can lead to the execution of malicious code on a remote iOS device, with no user interaction needed. All an attacker needs to do is to send a malformed message to a victim's phone, and the malicious code will execute once the user opens and views the received item. The four bugs are CVE-2019-8641 (details kept private), CVE-2019-8647, CVE-2019-8660, and CVE-2019-8662. The linked bug reports contain technical details about each bug, but also proof-of-concept code that can be used to craft exploits. The fifth and sixth bugs, CVE-2019-8624 and CVE-2019-8646, can allow an attacker to leak data from a device's memory and read files off a remote device --also with no user interaction. While it is always a good idea to install security updates as soon as they become available, the availability of proof-of-concept code means users should install the iOS 12.4 release with no further delay.
Top 5 financial services processes that are ripe for automation

Barely a day goes by without the launch of a new report extolling the potential benefits of artificial intelligence (AI) and automation in the financial services industry. These reports often refer to the potential for cost reduction, increased operational efficiency, improved customer experience and, ultimately, bottom-line growth. Indeed, analysts predict that AI will deliver a 22 percent reduction in operating costs (a saving of more than $1trn) across the global financial services industry by 2030 as business leaders look to transform both front and back-office functions. Demand for AI is coming from both ends of the market: established banks are recognising the need to respond to huge sector-wide disruption and to develop more agile operations in order to compete, while smaller fintech firms are looking to AI and automation as a way to scale quickly while keeping costs down. The scale of the opportunity is so vast that it can sometimes be a challenge for banks and insurance firms to know where to start or how to identify the process automations that will deliver most value.
Avoid chaos with an IT crisis management playbook

The second significant component of an IT crisis management playbook is a breakdown of common or reoccurring issues and their suggested fixes. Append the top resolution suggestions from the application vendors as well. Don't expect to create an exhaustive list, but describe coverage for five to 10 of the business's most critical applications. Create a comprehensive index for both vendors and IT operations staff to see quickly if they need to escalate an issue -- and to whom -- with internal contact information attached. A common question about crisis management playbooks is recommended format: paper or digital? If the modern paperless office is any indicator, create both. Paper binders require effort to update and store, but they also work without power -- something that's not a guarantee with a digital version.
Hackers target Telegram accounts through voicemail backdoor

According to the testimony of one of the arrested suspects, Walter Delgatti Neto, there’s another, potentially more vulnerable, way to get those verification messages – via voicemail. Accessing voicemail boxes turns out to be easier than it should be. Some people forget to set four-digit codes and those that don’t can potentially be undone by crooks cycling through the 10,000 possibilities. Many voicemail systems fight back by checking that the number making an access call belongs to the subscriber, but these numbers can easily be spoofed if the attacker knows the correct number. If an attacker can access voicemail they can access verification messages, such as Telegram’s, which are sent to voicemail if the hacker’s target is on a call or doesn’t answer three times in a row. Apparently, news of the weakness has spread on forums, leading to leaks of attacks on other valuable targets, including Puerto Rico Governor Ricardo Roselló, whose position became untenable after his Telegram chats were recently leaked.
Strategy For and With AI
Our research strongly suggests that in a machine learning era, enterprise strategy is defined by the key performance indicators (KPIs) leaders choose to optimize. (See “About the Analysis.”) These KPIs can be customer centric or cost driven, process specific or investor oriented. These are the measures organizations use to create value, accountability, and competitive advantage. Bluntly: Leadership teams that can’t clearly identify and justify their strategic KPI portfolios have no strategy. In data-rich, digitally instrumented, and algorithmically informed markets, AI plays a critical role in determining what KPIs are measured, how they are measured, and how best to optimize them. Optimizing carefully selected KPIs becomes AI’s strategic purpose. Understanding the business value of optimization is key to aligning and integrating strategies for and with AI and machine learning. KPIs create accountability for optimizing strategic aspirations. Strategic KPIs are what smart machines learn to optimize.
The Case For Transforming Banking (Even When Profits Are Strong)
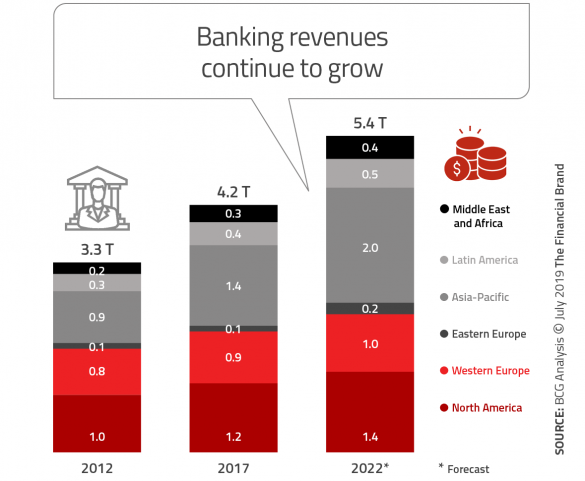
Many financial institutions are saying the right things more than doing what is needed. Often, what is being done is in the context of banking from the past, as opposed to being recreated from the bottom up as you would if you were building a digital banking organization from scratch. And many of these initiatives are still moving at a snails pace. Organizations are building digital account opening, loan application and new customer onboarding processes, but the majority of these processes still require the consumer to come into the branch or have way too many steps similar to the paper-based processes of the past. And, while almost all organizations know the benefits of expanded data, advanced analytics and AI, very few have used these tools to personalize experiences or proactively offer solutions in real time. As stated in the BCG report, banking organizations must look at digital transformation in a holistic manner rather than fragmented components that are not seamlessly integrated. More importantly, the direction for this transformation must come from the organization’s senior leadership and be supported by a culture that encourages innovation, digital customer experiences and aggressive market positioning.
Cyber security leadership in the age of fast and continuous delivery

Addressing the need for agile methods and the need to sustain adequate cyber security presents certain challenges for the CISO navigating a transforming business landscape. Here are the top six key triggers and challenges organizations are grappling with today. ... Cyber security usually has predefined contact points within a team's detailed planning and work schedule. These typically occur during initial software architecture definition and validation, with a couple of checkpoints ending with late testing and acceptance of the solution. Today, modern application security replaces the typically predefined interactions in the software lifecycle with more frequent interations that increase dialogue, collaboration and efficiency. How do organizations re-organize cyber security to support this interaction, either through staffing, automation or clever methodological work-arounds? ... It's not rare today to see cyber departments hiring software developers possessing a strong understanding of modern dynamics and training them in cyber security.
Capital One’s breach was inevitable, because we did nothing after Equifax

This time it’s the financial giant and credit card issuer Capital One, which revealed on Monday a credit file breach affecting 100 million Americans and 6 million Canadians. Consumers and small businesses affected are those who obtained one of the company’s credit cards dating back to 2005. That includes names, addresses, phone numbers, dates of birth, self-reported income and more credit card application data — including over 140,000 Social Security numbers in the U.S., and more than a million in Canada. The FBI already has a suspect in custody. Seattle resident and software developer Paige A. Thompson, 33, was arrested and detained pending trial. She’s been accused of stealing data by breaching a web application firewall, which was supposed to protect it. Sound familiar? It should. Just last week, credit rating giant Equifax settled for more than $575 million over a date breach it had — and hid from the public for several months — two years prior. Why should we be surprised? Equifax faced zero fallout until its eventual fine. All talk, much bluster, but otherwise little action.
Is The Future Of Artificial Intelligence Tied To The Future Of Blockchain?

There is no doubt that blockchain is a disruptive technology and will give nations and all its components the foundation to the decentralized future. While blockchain is a disruptive technology, the way it is being used and applied has enormous energy and environmental impacts. The reason behind this is the process that is at the core of blockchain systems. The security of blockchain technology comes from its encryption, and the consensus mechanism of blockchain necessitates that all users require permission to write on the chain. Each of these requirements individually and collectively involves the intricate use of algorithms and enormous amounts of computing power. As the computing power needed to keep the current applications of blockchain running is not sustainable, it is one of the critical challenges facing the future of blockchain. It is not only blockchain and artificial intelligence, but all existing and emerging technologies, that are accelerating global computing power consumption. As a result, there is a visible need for increased computing power.
Quote for the day:
"Leaders stuck in old cow paths are destined to repeat the same mistakes. Change leaders recognize the need to avoid old paths, old ideas and old plans." -- Reed Markham
No comments:
Post a Comment