Security flaws in a popular smart home hub let hackers unlock front doors

The researchers conceded that their findings weren’t a perfect skeleton key into everyone’s homes. In order to exploit the flaws, an attacker would need to be on the same Wi-Fi network as the vulnerable smart hub. Dardaman said any hub connected directly to the internet would be remotely exploitable. The researchers found five such vulnerable devices using Shodan, a search engine for publicly available devices and databases. Zipato says it has 112,000 devices in 20,000 households, but the exact number of vulnerable hubs isn’t known. We asked SmartRent, a Zipato customer and one of the largest smart home automation providers, which said fewer than 5% of its apartment-owning customers were affected by the vulnerable technology. A spokesperson wouldn’t quantify the figure further. SmartRent said it had more than 20,000 installations in mid-February, just weeks before the researchers’ disclosure. For its part, Zipato fixed the vulnerabilities within a few weeks of receiving the researchers’ disclosure.
The big question now is whether this is a one-time breather in the "Windows as a service" schedule or whether it becomes the new normal for Windows 10 releases. The timing is certainly no accident. The 19H2 Windows 10 feature update is the last Windows 10 release before the end of free support for Windows 7 on January 14, 2020. The last thing Microsoft wants is any kind of discouraging publicity about negative upgrade experiences in those final few months before the free support window closes. This week's announcement is the latest in a series of major changes to the Windows 10 release schedule, including some that represent a 180-degree turnaround from the original "Windows as a service" model. The new rules depend on which Windows edition you've deployed. For OEM and retail Windows editions, even the lowly Windows 10 Home, feature updates are no longer mandatory. Instead, the twice-yearly feature updates are offered on PCs that Microsoft's algorithms deem suitable;
Mac Malware Pushed via Google Search Results, Masquerades as Flash Installer
The malware was discovered by researchers being distributed via numerous sites – some of which popped up on Google search results. One such site, called “GetComics,” purported to share digital copies of new comic books for free. The malware was also spread via high-ranking Google search results, which were observed redirecting users to multiple sites. “We were actually in the process of coming up with a name for CrescentCore, and searched for ‘CrescentCore’ in quotation marks, and one of the links in the first page of search results redirected to a page that happened to be distributing a new sample of CrescentCore,” Long said. The researcher said that oftentimes malware distributors will find vulnerable blogs or other sites with high Google search engine rankings, and add a redirection mechanism that bounces through a number of affiliate links – ultimately redirecting users to a fake Flash Player landing page. “So if a result for a previously almost unused word like CrescentCore happened to show up in search results, it’s extremely likely that other search results are poisoned with redirections to this malware as well,” he said.
The Future of Anti-Fraud Technology

Technological advancements present opportunities for both fraud perpetrators and those trying to stop them. As criminals find new ways to exploit technology to commit their schemes and target new potential victims, anti-fraud professionals must ensure they are likewise adopting new technologies that are the most effective in navigating the evolving threat landscape. But which technologies are most effective in helping organizations manage their fraud risk? Which tools provide benefits that outweigh the costs? How are organizations successfully harnessing the power of data and technology as part of their anti-fraud programs? These issues were discussed in today’s roundtable session, “Benchmarking Your Use of Anti-Fraud Technology.” The answers to those and other questions can be crucial in gaining management buy-in and successfully implementing new anti-fraud technologies. Luckily, attendees were able to review the recently released Anti-Fraud Technology Benchmarking Report. A publication of the ACFE, the report was developed in partnership with SAS and serves as a road map to what the future technological landscape will hold.
Neuroscience Is Going to Change How Businesses Understand Their Customers

Neuroscience, it turns out, can help change how companies think about new opportunities, and specifically, within the emerging field of applied neuroscience. Applied neuroscience is best described as the use of neuroscience tools and insights to measure and understand human behavior. Using applied neuroscience, leaders are able to generate data about critical moments of decision making, and then use this data to make confident choices that help to navigate the future of an initiative. Studies using applied neuroscience are often conducted outside of a lab context, and therefore rarely use large, stationary MRI (magnetic resonance imaging) scanners. Instead, these studies focus on using more mobile solutions such as EEG (electroencephalograph) headsets, combined with eye-tracking technology to capture precise data on how the brain reacts when presented with certain scenarios. Because of this, applied neuroscience is used primarily during one of two points in a new project — either at the onset while defining the business problem, or later in the cycle while seeking new solutions for users.
AI Differential Privacy and Federated Learning
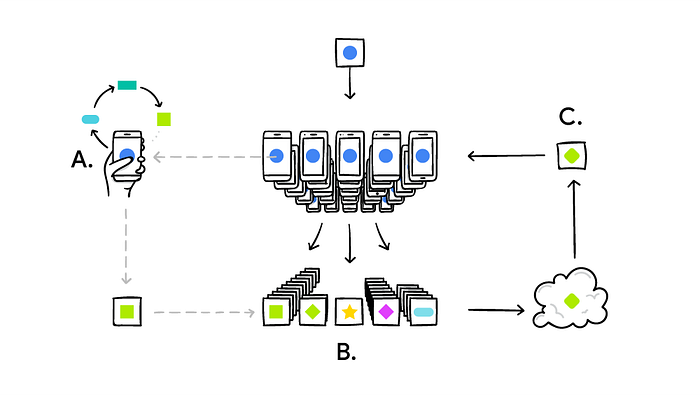
Differential Privacy enables us to quantify the level of privacy of a database. This can help us to experiment with different approaches in order to identify which is best to preserve the user’s privacy. By knowing our data privacy level we can then quantify the likelihood that someone might be able to leak sensitive information from the dataset and how much information can be leaked at most. ... Machine Learning models which make use of a large amount of data are traditionally trained using online servers. Companies like Google and Apple used to take the data records activity of the users of their mobile devices and then store them in their cloud services to create a centralized Machine Learning model able to improve the performances of their mobile services. Nowadays, these big companies are moving instead towards using a decentralized model approach called Federated Learning. Using Federated Learning, the Machine Learning model is trained on the data source and its output is then moved on the cloud for further analysis. This means that companies like Google and Apple no longer need to access their user's data to improve their services
Open Banking is less about technology, more about people

Key element is to be able to translate the opportunities of new technology to all stakeholders in the ecosystem. No, a bank will not become an ecosystem… it is an integral part of it. This means that collaboration is an essential part of the success, not imposing partnerships. This balanced partnership will (1) allow more creative thinking and (2) facilitate change management, as people are more open to change when dialogue is not top-down. To come back to the idea of the customer challenge: with partnerships I do not only mean technology partners, but also for example merchants and other parties that can help in convincing the end-customer to adapt to the new world of digital banking. Financial education is a key aspect of getting the market ready for Open Banking. You don’t need to explain what Open Banking is, but it may be useful to show the advantages of the new way of banking. Banks no longer have a monopoly on this financial education. To take the example of the wearables: it is good to have banks promoting it, but if the merchant does not promote it, the bank will get nowhere in volumes: it is a two-way street.
Thousands of Facebook Users Hit in Malware Distribution Campaign
Researchers from Check Point Software uncovered the campaign recently when investigating a Facebook page impersonating Khalifa Haftar, commander of the Libyan National Army. The page, created in April, offered posts about airstrikes, terrorists being captured, and other content likely of interest to people in Libya. With more than 11,000 followers, the page contained URLs for downloading files that were often described as documents containing evidence of countries like Qatar and Turkey conspiring against Libya, or containing photos of pilots captured when bombing Tripoli and other lures. Some URLs purported to be to sites where citizens could sign up for the army. Facebook users on mobile and desktop devices who clicked on these links ended up downloading a variety of known remote administration tools used for spying and stealing data. Check Point's investigation of the fake Khalifa Haftar Facebook page shows that the individual behind it had been distributing malicious links through more than 30 other Facebook pages since at least 2014.
The Role of Big Data Analytics and AI in the Future of Healthcare
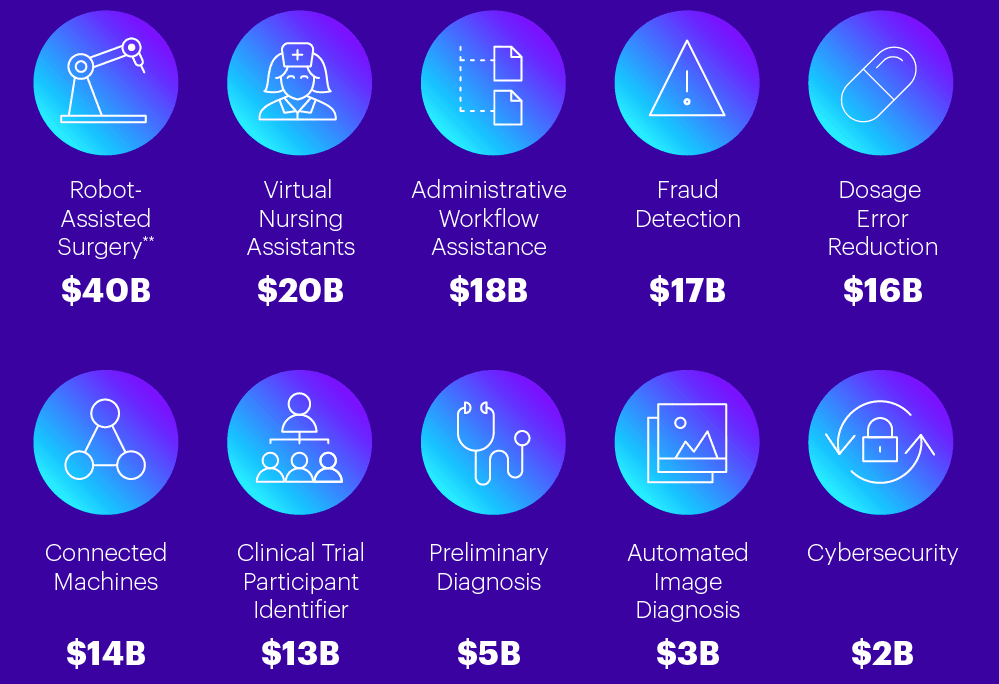
Machine learning algorithms can identify patterns and make predictions using cloud computing data lakes and data warehouses that clean (creating a single ‘source of truth’ in the data) and store huge amounts of data which enables the integration of multiple health care systems together. For the purpose of providing better and more targeted care to an individual’s electronic health record. Oncology and cancer research have gotten the most investment into precision medicine by studying cancer genetics. In some instances, cancer treatments can be suggested based on genetic drivers of the cancer and not on the physical location of the cancer itself within the patient’s body. Moffitt Cancer Centerin Tampa, FL has been working on incorporating molecular genomics, demographics and trial outcomes to develop models for each patient. The use case. Of precision medicine will not only lower the risks of using sometimes incompatible treatments and medicines but it also building a new solutions for fighting disease and delivering healthcare. A startup called Deep Genomics uses (AI) and the genome to determine the best drug therapies for each individual.
How DHL is securing 'the world's most international company'
The aim? To "integrate and interoperate" with critical security technology components to better “identify, visualise and prioritise” critical security information in near real-time, in addition to providing timely remediation and responses to reduce possible business disruptions from cyber attacks. “With an influx of emerging and disruptive technologies such as ML, AI and the Internet of Things (IoT), organisations need to attain high levels of confidence in cybersecurity to compete and dominate in the digital space,” explained Chim. “Cybersecurity, rather than being a blocker or damage controller, has become a prioritised commercial investment for several businesses." “Organisations dealing with digital transformation in any form are enforcing cybersecurity in every technology surface to ensure secure operations and meeting data privacy compliance.” At the same time, Chim said cybersecurity industries are also adopting AI, sensor and blockchain solutions to collect, analyse and enrich significant number of events and intelligence to better prevent, detect and respond to security threats.
Quote for the day:
"Managers work to see numbers grow. Leaders work to see people grow." -- Simon Sinek


No comments:
Post a Comment