PayPal-backed blockchain aims to help banks verify digital IDs

Security is critical to a project like this. “You could in theory have some centralized database that would store all the personal information for a group of banks,” Commons said. “But it's very difficult to do that while getting the appropriate consent and making sure that the information is really being shared on a truly need to know basis.” CV Madhukar, investment partner at Omidyar Network and global leader of the firm's work on digital identity, sees the project as a means of enabling financial inclusion and helping cut the cost of know-your-customer compliance. “One of the biggest use cases for digital identity is in financial inclusion, and one of the biggest challenges for financial inclusion is getting the KYC process right,” he said. “For the most vulnerable populations, getting KYC documentation is such a big challenge. Every time they need documents supporting KYC, they run into trouble. So whatever can ease the burden of the KYC process has value.” “This makes it easier for individuals and companies to get this done quickly and most importantly puts the user data in a safe place to access,” Madhukar said. “This is very central to protecting individuals’ privacy.”
An IoT security maturity model for IT/OT convergence

"On the IT security side, we're used to operating in a certain way," Carielli said. "We're used to saying, 'One Sunday a month for a couple hours we're going to shut down and apply patches.' It's OK from an IT perspective, but those paradigms don't work for OT." Shutting down a plant or factory, even for a couple of hours on a Sunday, could cost millions of dollars in lost production. And shutting down utilities, such as a smart grid, simply isn't feasible. "It's incumbent upon security folks to start to understand how operational technologies need to do business and how those may differ from what they're used to," Carielli said. IT security teams must also accept the fact that OT system lifecycles are much longer than those of IT systems, Carielli noted. This introduces legacy and brownfield equipment and applications IT teams aren't familiar with -- some of which have been in place for decades. Additionally, OT systems generally never connected to the internet in the past as they do today, so security wasn't built in from the start. Many industrial systems must be retrofitted with security controls -- which requires OT teams to adapt.

"It was possible to download valid boarding passes - not belonging to the user - for future flights due to an insecure direct object reference weakness within the application," Stubley tells Information Security Media Group. "Insecure direct object reference or IDOR vulnerabilities occur when an application provides direct access to objects based on user-supplied input, bypassing expected authentication and user access controls." Amadeus develops travel industry software used by 500 airlines - including United Airlines and Air Canada - as well as hotels, rail and cruise lines, tour operators and others. "Amadeus recently became aware of a configuration flaw affecting its Altéa Self Service Check-In solution," a spokeswoman tells ISMG. "Our security teams took immediate action and the vulnerability is now fixed. We are not aware of there having been any further unauthorized access resulting from the vulnerability, beyond the activity of the security researcher. We regret any inconvenience this might cause to our customers."
DevOps, The SDLC, and Agile Development
DevOps has a mutually beneficial relationship with Agile development, thus offering more flexibility than the other rigid structures which were present in the IT arena. The whole idea is directed at people working together and accepting change. It is this which allows the release of high quality software, and at a faster delivery speed. In addition to the coordination, the people-centric culture of DevOps is built on a particular viewpoint. It encourages a culture of open-mindedness, predictability, cross-skill training, and trying to do something extra. Thus, there is a development of shared identity between different teams. ... Solutions which are reached evolve through coordination between various cross-functional teams which use proper practices for their context. The focus thus lies on collaboration and self-organization of teams as the team together decides the next approach on things. Agile is hence a mindset which is made up of values which are contained in the Agile Manifesto. The whole idea behind Agile can be deduced from the first sentence of the Agile Manifesto, which says, “We are uncovering better ways of developing software by doing it and adjust accordingly."
How a Big Rock Revealed a Tesla XSS Vulnerability
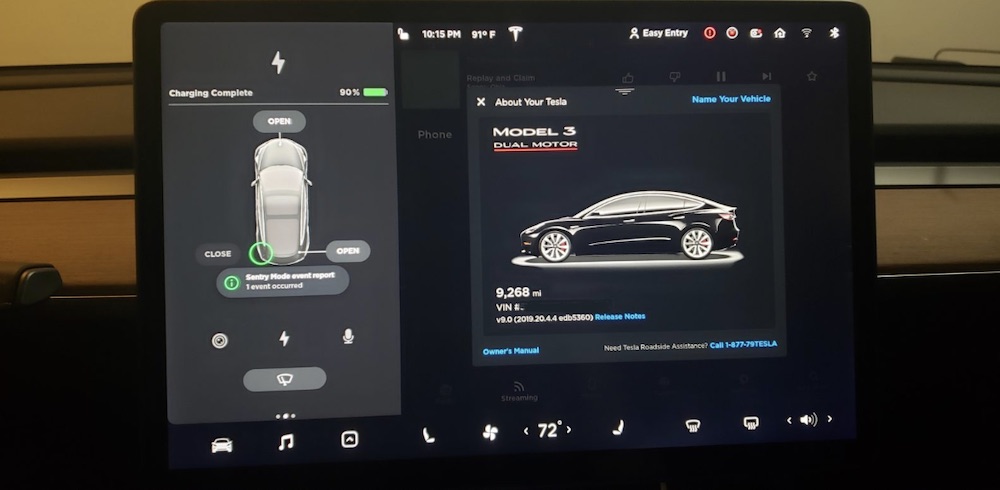
Curry writes in a blog post that he'd been trying to find a flaw within Telsa's web browser, which is a pared-down version of Google's Chromium. Then in April, he experimented with naming his Tesla. Owners can assign their car a nickname, which is displayed in the mobile app. Curry set his car's name to "%x.%x.%x.%x." That's a type of format string attack. A vulnerable application may try to execute the string, causing unintended consequences. At one time, BMW's 2011 330i was vulnerable to this kind of attack, which could remotely crash the multimedia software due to an issue with its Bluetooth stack , designated CVE-2017-9212. But the naming approach didn't work. So he decided to change the car's name to a cross-site scripting payload that came from XSS Hunter, a tool for finding these types of vulnerabilities. Nothing happened, or at least not right away. Curry says he had a month of free time earlier this year and decided to drive across the U.S. "I went on this super long - probably like 70 hours of driving - road trip," he says.
Ransomware attacks: How to get the upper hand

"It's no different than a tornado or flood. Something happened. You assess the damage and if your recovery plan is solid, you're in good shape," he said, adding that the reverse is also true. If you haven't prepared and can't recover from ransomware, "you're screwed." Not only should an organization back up its files, but it should also place a layer between the server and its backup files so that a hacker won't see there are more assets to steal or freeze, Scott advised. Some ransomware attacks are sophisticated and can destroy metadata and passwords, he said, so it's best to preserve digital assets with a corresponding level of complexity. For instance, organizations could take the necessary disaster recovery steps now to perform a bare-metal restore -- essentially, a reinstall of operating systems and applications -- so that, later, all is not lost if ransomware locks out users. But even simple disaster recovery preparedness works as a defense against ransomware attacks.
Are CIOs Losing The Cyber Security Battle?

Despite taking tangible steps to reduce their cybersecurity risk, a question that comes to mind is, ‘Why are companies still getting hit and more than ever?’ The report clarifies that there are some security holes not being plugged and it is here that CIOs need to pay greater attention. For example, the report explains, an up-to-date malware signature list won’t stop attackers hijacking your accounts, while rock-solid authentication won’t help if you’re not protecting your computers from ransomware. “Good cybersecurity demands defense in depth and proper risk assessment so that you can protect your weakest spots from attack first,” says the report. The survey also revealed that companies are facing attacks via multiple channels, including email (33%) and web (30%) among others. Software vulnerabilities and unauthorized USB sticks or other external devices were also common attack vectors. Perhaps even more worrying is that 20% of CIOs didn’t know how their networks were compromised. With cyber threats coming from supply chain attacks, phishing emails, software exploits, vulnerabilities, insecure wireless networks, and much more, businesses need a security solution that helps them eliminate gaps and better identify previously unseen threats.
Building blocks of an IIoT security architecture
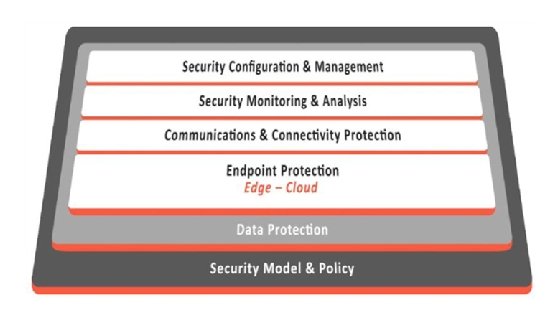
Since IIoT involves both IT and OT, ideally security and real-time situational awareness should span IT and OT subsystems seamlessly without interfering with any operational business processes. Average lifespan of an industrial system is currently 19 years. Greenfield deployments using the most current and secure technologies are not always feasible. Security technology must often be wrapped around an existing set of legacy systems that are difficult to change. In both greenfield and brownfield deployments, all affected parties -- manufacturers, systems integrators and equipment owner/operators -- must be engaged to create a more secure and reliable IIoT system. As there is no single "best way" to implement security and achieve adequately secure behavior, technological building blocks should support a defense-in-depth strategy that maps logical defensive levels to security tools and techniques. Due to the highly segregated nature of industrial systems, security implementation needs to be applied in multiple contexts.
Vulnerable firmware in enterprise server supply chain

The first vulnerability is a failure in the update process to perform cryptographic signature verification before accepting updates, while the second relates to command injection vulnerability in the code in the BMC that performs the firmware update process. Both of these issues allow an attacker running with administrative privileges on the host (such as through exploitation of a different host-based vulnerability) to run arbitrary code within the BMC, and malicious modifications to the BMC firmware can be used by an attacker to maintain persistence in the system and survive common incident response steps such as reinstallation of the operating system, the researchers found. An attack could also modify the environment within the BMC to prevent any further firmware updates through software mechanisms, thus enabling an attacker to disable the BMC permanently, and the update mechanism could be exploited remotely if the attacker has been able to capture the administration password for the BMC, the researchers said.
Martin Fowler Discusses New Edition of Refactoring, along with Thoughts on Evolutionary Architecture
Refactoring is the idea of trying to identify the sequence of small steps that allows you to make a big change. That core idea hasn’t changed. Several new refactorings in the book deal with the idea of transforming data structures into other data structures, Combine Functions into Transform for example. Several of the refactorings were removed or not added to the book in favor of adding them to a web edition of the book. A lot of the early refactorings are like cleaning the dirt off the glass of a window. You just need them to be able to see where the hell you are and then you can start looking at the broader ones. Refactorings can be applied broadly to architecture evolution. Two recent posts How to break a Monolith into Microservices, by Zhamak Dehghani, and How to extract a data-rich service from a monolith by Praful Todkar on MartinFowler.com deal with this specifically. Evolutionary architecture is a broad principle that architecture is constantly changing. While related to Microservices, it’s not Microservices by another name.
Quote for the day:
"It doesn't matter how much we know, what matters is how clearly others can understand what we know." -- Simon Sinek
No comments:
Post a Comment