Budweiser's Parent Company Invests In Blockchain For Farmers

While the blockchain industry has swayed over the past year to a focus on how blockchain can save giant enterprises money by removing unnecessary middlemen, the investment by Anheuser-Busch InBev, a member of the inaugural Forbes Blockchain 50 list, and best known as the maker of Budweiser, is a return to blockchain’s roots as a way of empowering the unbanked. “Through this work, we are helping to create a digital ledger of farmers’ transactions that will create an economic identity and enable access to financial services,” said Maisie Devine, a director at AB InBev, in a statement. “This will ultimately allow farmers to grow their business and improve the livelihoods of their families and communities.” Belgium-based AB InBev’s work with BanQu was announced in August 2018 with a pilot in Zambia that served 2,000 of the region’s smallholder cassava farmers with subsequent services brought to Uganda, India, Brazil, Costa Rica, India, Indonesia, Jordan, Malawi, Somalia, South Africa, Syria, Uganda and the United States.
GDPR One Year On: Increasing Demand for ''Security By Design''
GDPR’s focus on personal data highlights how software is made and what components are used. Globally, businesses awoke to the reality that open source components are part of their software supply chains. “Security hasn’t caught up to 21st-century software engineering, so that’s being addressed now,” he said. GDPR put pressure on the industry to rethink, and re-engineer, software security at the start. Ilkka emphasized that negative publicity is a key motivating factor. No one wants to be part of the next big breach, meaning security is quickly becoming a mainstream priority, he adds. Simultaneously, a corporate shift is occurring. More software development teams are adopting a DevOps approach to production. This approach, which favors rapid iterations and software releases, produces better software, faster. A consequence is that security must be embedded from the start. A successful, secure design must be automated, repeatable, and scalable.
Tackling bias in artificial intelligence (and in humans)

In many cases, AI can reduce humans’ subjective interpretation of data, because machine learning algorithms learn to consider only the variables that improve their predictive accuracy, based on the training data used. In addition, some evidence shows that algorithms can improve decision making, causing it to become fairer in the process. For example, Jon Kleinberg and others have shown that algorithms could help reduce racial disparities in the criminal justice system. Another study found that automated financial underwriting systems particularly benefit historically underserved applicants. Unlike human decisions, decisions made by AI could in principle (and increasingly in practice) be opened up, examined, and interrogated. To quote Andrew McAfee of MIT, “If you want the bias out, get the algorithms in.” At the same time, extensive evidence suggests that AI models can embed human and societal biases and deploy them at scale.
For two hours, a large chunk of European mobile traffic was rerouted through China

"Today's incident shows that the internet has not yet eradicated the problem of BGP route leaks," Madory said. "It also reveals that China Telecom, a major international carrier, has still implemented neither the basic routing safeguards necessary both to prevent propagation of routing leaks nor the processes and procedures necessary to detect and remediate them in a timely manner when they inevitably occur. "Two hours is a long time for a routing leak of this magnitude to stay in circulation, degrading global communications." But if any other ISP would have caused this incident, it would have likely been ignored. Alas, it was China Telecom, and there's a backstory. An academic paper published by experts from the US Naval War College and Tel Aviv University in October last year blamed China Telecom for "hijacking the vital internet backbone of western countries." The report argued that the Chinese government was using local ISPs for intelligence gathering by systematically hijacking BGP routes to reroute western traffic through its country, where it can log it for later analysis.
Why cryptocurrency’s not quite ready for takeoff
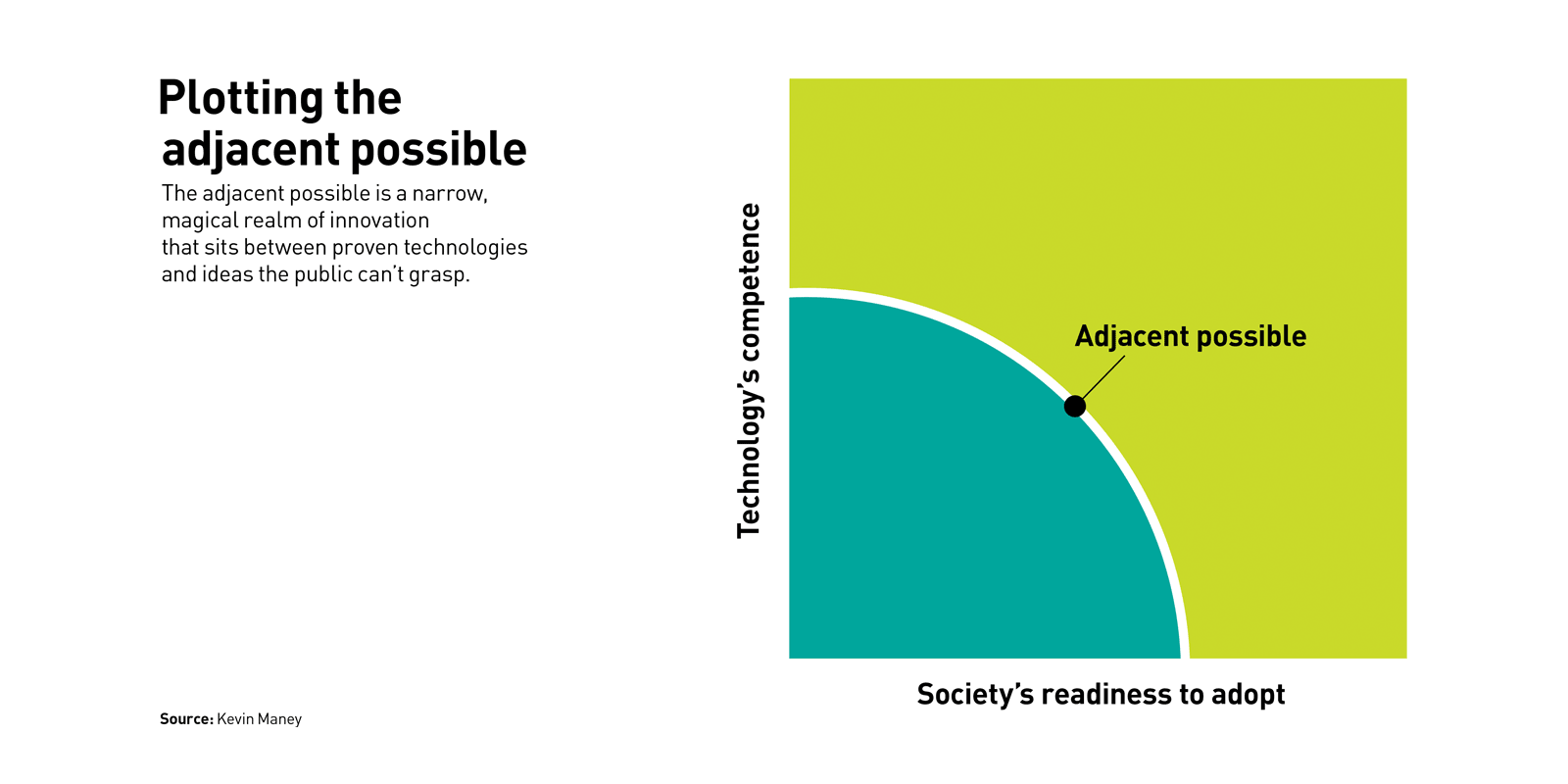
Why? Because crypto remains too far outside of what’s known as the “adjacent possible.” ... The adjacent possible can be illustrated using a coordinate graph. A point on the vertical axis shows how competent the technology is today, and a point on the horizontal axis shows how ready society is to accept and adopt the technology. The curve that connects the two points constantly moves outward over time, as technology gets better and society embraces new innovations. Inside the curve is technology that exists and is accepted. TVs, smartphones, and airliners are all safely inside this zone. Outside the curve is what’s not yet possible or adopted. Either the technology isn’t good enough yet, or the public isn’t ready — or, more typically, both. Holographic entertainment, augmented reality glasses, and consumer space travel sit out in that zone. Build such a product, and it will be too far ahead of its time. The magic happens in the thin band separating the two zones — in the adjacent possible.
Ireland's Priviti and Aussie fintech Accurassi partner for Open Banking
Following the Australian government’s response to the Review into Open Banking in 2018, Australia’s major banks will be required to make data available on credit and debit card, deposit and transaction accounts and mortgages by February 2020. The government’s legislated Consumer Data Right gives Australians greater control over their data and enables them to choose to share their data with trusted recipients for purposes they have authorised. This will first apply to the banking sector, followed by the energy and telecommunications sectors. Seizing the opportunity, Accurassi is launching its marketplace solution with banks and energy suppliers in the next few months and using consumer utility bill data to power personalised energy comparison services. The Priviti API will be embedded into the user experience to provide explicit authorisation to energy retailers for the release of bills to Accurassi.
Meet Kedro, McKinsey’s first open-source software tool

The name Kedro, which derives from the Greek word meaning center or core, signifies that this open-source software provides crucial code for ‘productionizing’ advanced analytics projects. Kedro has two major benefits: it allows teams to collaborate more easily by structuring analytics code in a uniform way so that it flows seamlessly through all stages of a project. This can include consolidating data sources, cleaning data, creating features and feeding the data into machine-learning models for explanatory or predictive analytics. Kedro also helps deliver code that is ‘production-ready,’ making it easier to integrate into a business process. “Data scientists are trained in mathematics, statistics and modeling—not necessarily in the software engineering principles required to write production code,” explains Yetunde. “Often, converting a pilot project into production code can add weeks to a timeline, a pain point with clients. Now, they can spend less time on the code, and more time focused on applying analytics to solving their clients’ problems.”
Can Artificial Intelligence Save Us From Asteroidal Armageddon?

NASA’s Planetary Defense Coordination Office already uses numerous telescopes to find and monitor NEOs that might have the potential to impact Earth. But the non-profit Aerospace Corporation’s A.I. team is working with NASA on implementing software dubbed NEO AID (Near-Earth Object Artificial Intelligence Detection) to differentiate false positives from asteroids and comets that might be real threats. Nightly, researchers at locations such as the Catalina Sky Survey on Mount Lemmon in Tucson, Ariz. pore over hundreds of images of star fields in search of fast-moving objects that need more scrutiny, says Aerospace Corporation. It’s here that Aerospace A.I. engineers used 100 terabytes of data to build and train an artificial intelligence model that is now capable of classifying NEO targets of interest. And by Aerospace Corporation’s calculations, this new A.I. tech has already increased the sky survey’s performance by 10 percent with room for development. NASA’s Center for Near-Earth Object studies says that with over 90 percent of NEOs larger than one kilometer already discovered, the NEO program is now focusing on finding the 90 percent larger than 140 meters.
Machine Learning Is Not Magic: It’s All About Math, Stats, Data, and Programming

One of the main reasons why I kept making a U-turn was the liberal dosage of mathematics found in almost every ML resource that I bookmarked. Despite my determination and commitment, the thought that I need to learn advanced mathematics kept pushing me away. Let me admit it — I dread dealing with mathematics. I barely managed to pass my math papers in high school. When I was a teen, I rejoiced when I found that it was possible to build a career in IT without a master’s degree in mathematics. The fact that some advanced math became a prerequisite for ML disappointed me and, in many ways, brought back the nightmare of my school days. But as I continued to work with my customers on Internet of Things and data-centric projects, the possible usage of ML kept coming back to us. Meanwhile, the hype around ML has reached the peak. So much so that the cloud providers started to push ML more than the core IaaS components like VMs, storage, and networking. It also became extremely clear that ML is becoming the front and center of many emerging technologies including Cognitive Computing, Artificial Intelligence, Chatbots, Personal Assistants, and Predictive Maintenance.
Shifting the Conversation to Security by Design
It wasn’t a surprise that healthcare organizations were asking for this as well. We think that asking for changes to a mandate or regulation is a good thing in theory, but it’s tricky; you don’t want to over-mandate or over-regulate, but you also don’t want to under-regulate either. With cyber hygiene, if you are going to have meaningful regulation, you want to make sure it balances the technology side of the equation with the people side. You often hear the individuals in an organization getting blamed as the weakest link. We don’t like to think of it that way. We like to say individuals can be your strongest line of defense if they are adequately trained and have the right tools and resources, both from a technological perspective, but also from a training perspective. Safe harbor would remove penalties for healthcare organizations that suffer a cyber incident if they were in full compliance with HIPAA requirements and any other mandates that could secure the network or data. No matter how much money you spend, there is no protection that will render a system completely secure.
Quote for the day:
"Being responsible sometimes means pissing people off." -- Colin Powell
No comments:
Post a Comment