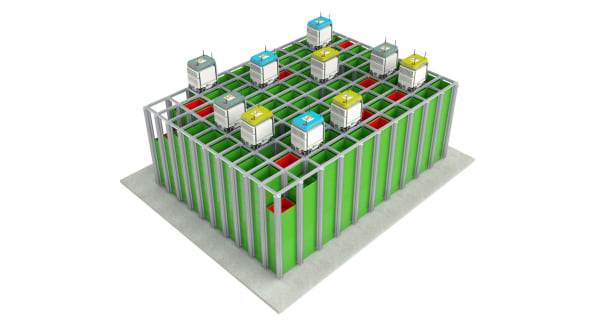
“Because the robots are brand new, it looks like a render but in fact it’s 100% real,” answers Alex Voica, the head of technology PR and communications at Ocado, a British online-only supermarket that delivers orders to customers straight from its warehouses. Ocado sells everything you can find in a brick-and-mortar supermarket–from meat, dairy, and produce to its own brand of home products, third-party goods, and even flowers, toys, and magazines. When it comes to online delivery, speed and efficiency are paramount, which is why the company has been working on automation since it was founded in 2000. While other companies rely on human workers to find and buy all of the items on an online customer’s shopping list, Ocado is using a new kind of robot–or, more specifically, a swarm of them.
Accountability is not the problem you’re looking to solve

Perceived lack of accountability is a symptom of a larger problem in the organization. If the organization believes their people are not accountable or responsible, that points directly to a deficit in trust. We see both in Patrick Lencioni’s hierarchy of the 5 dysfunctions of a team, though avoidance of accountability is not the root problem, absence of trust is. ... One way management often hinders teams in in forming trust is by frequently changing their members around, thus causing them to have to re-form relationships. How can we expect people to be accountable to people they have never worked with before and immediately deliver on everything that is expected of them? Those are unfair expectations and teams are at a disadvantage from their inception
Commanding Large Datasets With Ease
You would think that since data integration is something every successful dashboard deployment requires, most dashboards would come with software that would allow such integration out of the box. Far from it. Most dashboards ship with very basic Extract-Transform-Load (ETL) functions, if any. Such simple ETL works great for demo software but fails miserably when presented with real-world challenges. The Syncfusion Dashboard Platform is unique in this respect. Not only is it one of the most powerful, elaborate, and mobile-enabled dashboard platforms available (at any price), it is complemented by a complete data integration platform. Syncfusion's Data Integration Platform allows you to easily integrate data from multiple data sources. You can perform complex integration tasks without writing any code. There are out-of-the-box processors for all your data handling needs. There is also support for custom processors.
Severe shortage of cyber skills poses data security threat

“The cyber-security skills shortage represents an existential threat to our national security, and this year-over-year comparison data bears out this fact,” says Jon Oltsik, an ESG analyst and the report’s author. “We are not making progress, cyber-security professionals can’t scale, and the implications of the skills shortage are becoming more pervasive and ominous. “It is clear that the solution must be about more than filling jobs,” he adds. “It is about creating an environment from the top down of cybersecurity as a priority.” In the report, Oltsik also identifies the five most important investment mistakes that businesses make with regards to cybersecurity and suggests remedies based on the study: Failing to align cybersecurity and business goals: To correct this, 43 percent of the survey respondents suggest establishing security-related goals and metrics for IT and business managers.
Proactively Managing Data Compliance With Encryption Strategies
There is a perception problem with encryption, where companies consider it to be a time-consuming process that is not worth the effort when compared to the perceived risk of being hacked. The “it won’t happen to us” mentality is pervasive, despite the industry predictions that cybercrime damages will cost the world $6 trillion annually by 2021 (according to Cybersecurity Ventures). Whether a firm believes their current safeguards are sufficient, or that hackers won’t target their business, they avoid encryption until it’s simply too late. They are not performing the usual risk/reward that organizations should consider when weighing the value of data and the downsides of a breach. Encryption is also not as mysterious and complex as many believe. It simply involves taking data and translating it into a different form that requires an access key to read, share and edit.
Big Data, IoT and the need for high density and ultra high density computing

IoT and big data put intense pressure on the security, servers, storage and network of any organisation - and the impact of these demands is being felt across the entire technological supply chain. IT departments need to deploy more forward-looking capacity management to be able to proactively meet the business priorities associated with IoT connections. And big data processing requires a vast amount of storage and computing resources. All this means that, ultimately, the data centre now sits firmly at the heart of the business. Apart from being able to store IoT generated data, the ability to access and interpret it as meaningful actionable information - very quickly - is vitally important, and will give huge competitive advantage to those organisations that do it well.
How better data governance can help banks keep pace with the rising tide of regulations

In the case of GDPR, for example, Australian banks operating in Europe will need to implement a personally identifiable information (PII) data hub where they can pull all relevant data together in one place. They will also need to reconcile and harmonise disparate PII data into a “single version of the truth” using data quality and master data management (MDM) together with metadata management to establish data lineage. Data lineage is frequently seen as the first step towards good data governance. In fact, data governance effectively takes data lineage one stage further by outlining a full set of processes that ensure important data assets are formally managed across the entire enterprise. Having in place the right data governance systems and solutions is vital in delivering a fully secure, well-managed and compliant data environment within banks.
Best Practices to Help Safeguard Your Organization for the Internet of Things

First of all, because advanced threats like Hajime and WannaCry were so successful at targeting known vulnerabilities, this has become an increasingly popular attack vector for cybercriminals. As a result, patch management is essential. WannaCry targeted a vulnerability for which a patch had been available for more than two months. ... And the new Reaper IoT botnet can simultaneously target multiple vulnerabilities across a number of manufacturers using a constantly updated vulnerability list. Organizations that are spared the effects of these sorts of attacks all have one thing in common - a strong cyber-hygiene policy that includes applying patches as soon as they're available. But physical patching is only part of the solution. There are billions of vulnerable devices out there with no patches in sight. This is where intrusion-prevention systems (IPS) are essential.
What's Worse for Your Account: a Data Breach or a Phishing Attack?

The good news is that data breaches tend to only contain username and password information, which is sometimes not enough to break into an account. For instance, Google has protections in place to also analyze where a login takes place and from what device. Any deviations found can prompt Google to verify your identity. Attacks from phishing kits, on the other hand, can be designed to extract more detailed information from their victims, including geo-location data, the login device, and even account recovery questions. "Our findings indicate that while credential leaks may expose the largest number of passwords, phishing kits and keyloggers provide more flexibility to adapt to new account protections," the study said. Google has forced a password reset for the company users found in the sample datasets.
New age insurers are technology and data driven
Insurers might have to do a cost-benefit analysis to finalise build or buy decisions. Once a data infrastructure is in place, data can be tapped and insights can be generated using advanced analytics algorithms. These insights can then further fine-tune data needs, which can again enhance/update data collection and aggregation. Whether an insurer begins this process on a small or large scale, the deployment of big data and advanced analytics in business decisions is a complex undertaking which requires a structured approach with multiple dimensions. We believe that a framework for such a transformation involves interdependent components, each of which adds distinctive characteristics. It starts with the source of value, accordingly deriving the needed data ecosystem and modelling insights, further moving on to workflow integration and adoption.
Quote for the day:
"Leadership is a privilege to better the lives of others. It is not an opportunity to satisfy personal greed." -- Mwai Kibaki
No comments:
Post a Comment