The future of AI regulation is up in the air: What’s your next move?

The problem is, Jones says, is that lack of regulations boils down to a lack of accountability, when it comes to what your large language models are doing — and that includes hoovering up intellectual property. Without regulations and legal ramifications, resolving issues of IP theft will either boil down to court cases, or more likely, especially in cases where the LLM belongs to a company with deep pockets, the responsibility will slide downhill to the end users. And when profitability outweighs the risk of a financial hit, some companies are going to push the boundaries. “I think it’s fair to say that the courts aren’t enough, and the fact is that people are going to have to poison their public content to avoid losing their IP,” Jones says. “And it’s sad that it’s going to have to get there, but it’s absolutely going to have to get there if the risk is, you put it on the internet, suddenly somebody’s just ripped off your entire catalog and they’re off selling it directly as well.” ... “These massive weapons of mass destruction, from an AI perspective, they’re phenomenally powerful things. There should be accountability for the control of them,” Jones says. “What it will take to put that accountability onto the companies that create the products, I believe firmly that that’s only going to happen if there’s an impetus for it.”
Leading VPN CCO says digital privacy is "a game of chess we need to play"

Sthanu calls VPNs a first step, and puts forward secure browsers as a second.
IPVanish recently launched a secure browser, which is an industry first, and
something not offered by other top VPN providers. "It keeps your browser
private, blocking tracking, encrypting the sessions, but also protecting your
device from any malware," Sthanu said. IPVanish's secure browser utilises the
cloud. Session tracking, cookies, and targeting are all eliminated, as web
browsing operates in a cloud sandbox. ... Encrypting your data is a vital part
of what VPNs do. AES 256-bit and ChaCha20 encryption are currently the standards
for the most secure VPNs, which do an excellent job at encrypting and protecting
your data. These encryption ciphers can protect you against the vast majority of
cyber threats out there right now – but as computers and threats develop,
security will need to develop too. Quantum computers are the next stage in
computing evolution, and there will come a time, predicted to be in the next
five years, where these computers can break 256-bit encryption – this is being
referred to as "Q-day." Quantum computers are not readily available at this
moment in time, with most found in universities or research labs, but they will
become more widespread.
Kintsugi Leaders: Conservers of talent who convert the weak into winners

Profligate Leaders are not only gluttonous in their appetite for consuming
resources, they are usually also choosy about the kind they will order. Not
for them the tedious effort of using their own best-selling, training cookbook
for seasoning and stirring the youth coming out from the country’s stretched
and creaking educational system. On the contrary, they push their HR to queue
up for ready-cooked candidates outside the portals of elite institutes on day
zero. ... Kintsugi Leaders can create nobility of a different kind if they
follow three precepts. The central one is the willingness to bet big and take
risks on untried talent. In one of my Group HR roles, eyebrows were raised
when I placed the HR leadership of large businesses in the hands of young,
internally groomed talent instead of picking stars from the market. ... There
is a third (albeit rare) kind of HR leader: the Trusted Transformer who can
convert a Profligate Leader into the Kintsugi kind. Revealable corporate
examples are thin on the ground. In keeping with the Kintsugi theme, then, I
have to fall back on Japan. Itō Hirobumi had a profound influence on Emperor
Meiji and played a pivotal role in shaping the political landscape of
Meiji-era Japan.
4 North Star Metrics for Platform Engineering Teams

“Acknowledging that DORA, SPACE and DevEx provide different slivers or
different perspectives into the problem, our goal was to create a framework
that encapsulates all the frameworks,” Noda said, “like one framework to rule
them all, that is prescriptive and encapsulates all the existing knowledge and
research we have.” DORA metrics don’t mean much at the team level, but, he
continued, developer satisfaction — a key measurement of platform engineering
success — doesn’t matter to a CFO. “There’s a very intentional goal of making
especially the key metrics, but really all the metrics, meaningful to all
stakeholders, including managers,” Noda said. “That enables the organization
to create a single, shared and aligned definition of productivity so everyone
can row in the same direction.” The Core 4 key metrics are:An average of diffs
per engineer is used to measure speed. The Developer Experience Index, or
homegrown developer experience surveys, is used to measure effectiveness. A
change failure rate is used to measure quality. The percentage of time spent
on new capabilities to measure impact. DX’s own DXI, which uses a standardized
set of 14 Likert-scale questions — from strongly agree to strongly disagree —
is currently only available to DX users.
The future of data: A 5-pillar approach to modern data management
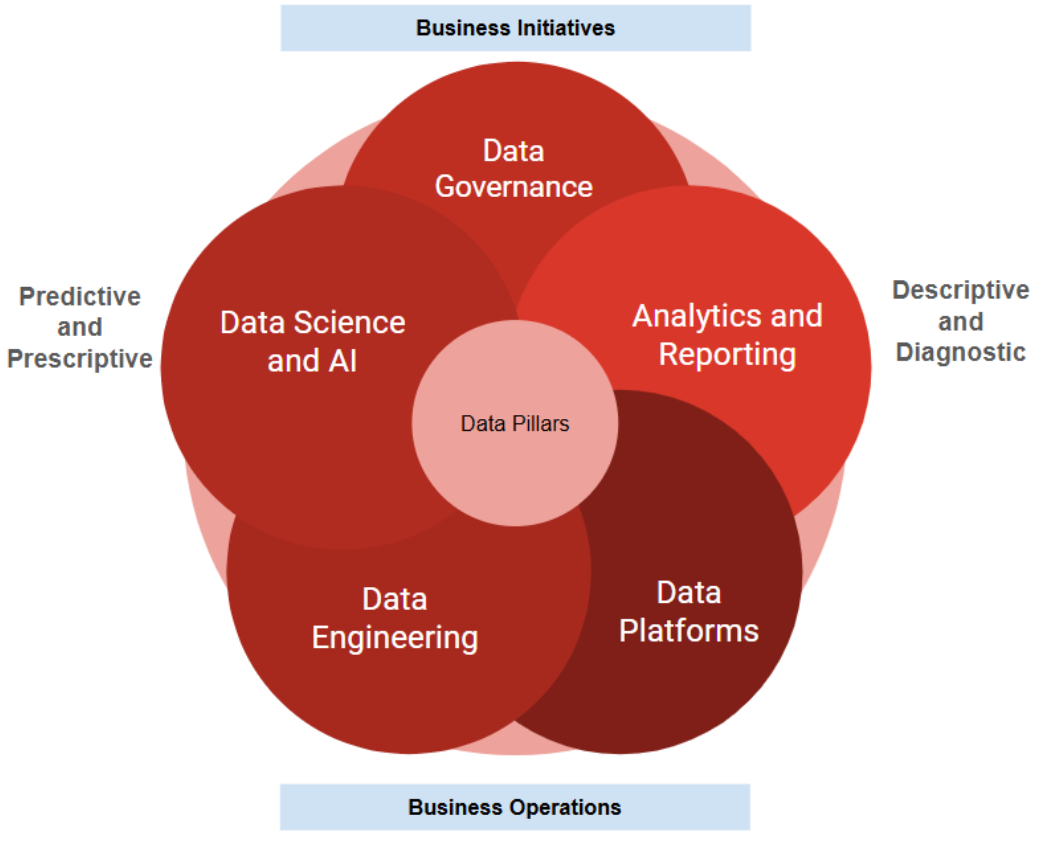
To succeed in today’s landscape, every company — small, mid-sized or large —
must embrace a data-centric mindset. This article proposes a methodology for
organizations to implement a modern data management function that can be
tailored to meet their unique needs. By “modern”, I refer to an
engineering-driven methodology that fully capitalizes on automation and
software engineering best practices. This approach is repeatable, minimizes
dependence on manual controls, harnesses technology and AI for data management
and integrates seamlessly into the digital product development process. ...
Unlike the technology-focused Data Platform pillar, Data Engineering
concentrates on building distributed parallel data pipelines with embedded
business rules. It is crucial to remember that business needs should drive the
pipeline configuration, not the other way around. For example, if preserving
the order of events is essential for business needs, the appropriate batch,
micro-batch or streaming configuration must be implemented to meet these
requirements. Another key area involves managing the operational health of
data pipelines, with an even greater emphasis on monitoring the quality of the
data flowing through the pipeline.
How and Why the Developer-First Approach Is Changing the Observability Landscape
First and foremost, developers aim to avoid issues altogether. They seek
modern observability solutions that can prevent problems before they occur.
This goes beyond merely monitoring metrics: it encompasses the entire software
development lifecycle (SDLC) and every stage of development within the
organization. Production issues don't begin with a sudden surge in traffic;
they originate much earlier when developers first implement their solutions.
Issues begin to surface as these solutions are deployed to production and
customers start using them. Observability solutions must shift to monitoring
all the aspects of SDLC and all the activities that happen throughout the
development pipeline. This includes the production code and how it’s running,
but also the CI/CD pipeline, development activities, and every single test
executed against the database. Second, developers deal with hundreds of
applications each day. They can’t waste their time manually tuning alerting
for each application separately. The monitoring solutions must automatically
detect anomalies, fix issues before they happen, and tune the alarms based on
the real traffic. They shouldn’t raise alarms based on hard limits like 80% of
the CPU load.
We must adjust expectations for the CISO role

The sense of vulnerability CISOs feel today is compounded by a shifting
accountability model in the boardroom. As cybersecurity incidents make
front-page news more frequently, boards and executive teams are paying closer
attention. This increased scrutiny is a double-edged sword: on the one hand,
it can mean greater support and resources; on the other, it often translates
to CISOs being in the proverbial hot seat. What’s more, cybersecurity is still
a rapidly evolving field with few long-standing best practices. It’s a space
marked by constant adaptation, bringing a certain degree of trial and error.
When an error occurs—especially one that leads to a breach—the CISO’s role is
scrutinized. While the entire organization might have a role in cybersecurity,
CISOs are often expected to bear the brunt of accountability. This dynamic is
unsettling for many in the position, and the 99% of CISOs who fear for their
job security in the event of a breach clearly illustrates this point. So, what
can be done? Both organizations and CISOs are responsible for recalibrating
expectations and addressing the root causes of these pervasive job security
fears. For organizations, a starting point is to shift cybersecurity from a
reactive to a proactive stance. Investing in continuous improvement—whether
through advanced security technologies, employee training, or cyber
insurance—is crucial.
Bug bounty programs can deliver significant benefits, but only if you’re ready

The most significant benefit of a bug bounty program is finding
vulnerabilities an organization might not have otherwise discovered. “A bug
bounty program gives you another avenue of identifying vulnerabilities that
you’re not finding through other processes,” such as internal vulnerability
scans, Stefanie Bartak, associate director of the vulnerability management
team at NCC Group, tells CSO. Establishing a bug bounty program signals to the
broader security research community that an organization is serious about
fixing bugs. “For an enterprise, it’s a really good way for researchers, or
anyone, to be able to contact them and report something that may not be right
in their security,” Louis Nyffenegger, CEO of PentesterLab, tells CSO.
Moreover, a bug bounty program will offer an organization a wider array of
talent to bring perspectives that in-house personnel don’t have. “You get
access to a large community of diverse thinkers, which help you find
vulnerabilities you may otherwise not get good access to,” Synack’s Lance
says. “That diversity of thought can’t be underestimated. Diversity of thought
and diversity of researchers is a big benefit. You get a more hardened
environment because you get better or additional testing in some cases.”
Harnessing SaaS to elevate your digital transformation journey
/dq/media/media_files/2024/12/12/igcw1FiS1zYQyuu2A0a8.png)
The impact of AI-driven SaaS solutions can be seen across multiple industries.
In retail, AI-powered SaaS platforms enable businesses to analyze consumer
behavior in real-time, providing personalized recommendations that drive
sales. In manufacturing, AI optimizes supply chain management, reducing waste
and increasing productivity. In the finance sector, AI-driven SaaS automates
risk assessment, improving decision-making and reducing operational costs. ...
As businesses continue to adopt SaaS and AI-driven solutions, the future of
digital transformation looks promising. Companies are no longer just thinking
about automating processes or improving efficiency, they are investing in
technologies that will help them shape the future of their industries. From
developing the next generation of products to understanding their customers
better, SaaS and AI are at the heart of this evolution. CTOs, like myself, are
now not only responsible for technological innovation but are also seen as key
contributors to shaping the company’s overall business strategy. This shift in
leadership focus will be critical in helping organizations navigate the
challenges and opportunities of digital transformation. By leveraging AI and
SaaS, we can build scalable, efficient, and innovative systems that will drive
growth for years to come.
What makes product teams effective?

More enterprises are adopting a cross-functional team model, yet many still
tend to underinvest in product management. While they make sure to fill the
product owner role—a person accountable for translating business needs into
technology requirements—they do not always choose the right individual for the
product manager role. Effective product managers are business leaders with the
mindset and technical skills to guide multiple product teams simultaneously.
They shape product strategy, define requirements, and uphold the bar on
delivery quality, usually partnering with an engineering or technology lead in
a two-in-a-box model. ... Unsurprisingly, when organizations recognize
individual expertise, provide options for career progression, and base
promotions on capabilities, employees are more engaged and satisfied with
their teams. Similarly, by standardizing and reducing the overall number of
roles, organizations naturally shift to a balanced ratio of orchestrators
(minority) to doers (majority), which increases team capacity without hiring
more employees. This shift helps ensure teams can meet their delivery
commitments and creates a transparent environment where individuals feel
empowered and informed.
Quote for the day:
“Things come to those who wait, but
only the things left by those who hustle” -- Abraham Lincoln
No comments:
Post a Comment