
The agility and flexibility to adjust sizing as needed are critical for resilience. "You can upscale or downscale based on growth, and this is why resilience is important. In case of any economic or external risks, we are prepared to run our operations, and our IT services are equipped to meet business demands," she said. ... Integrating technology to connect with suppliers and customers is crucial for mitigating risks and enhancing collaboration. "Accurate and agile information through integrations is crucial for resilience," Fernando said. Hela Clothing has automated plant and manufacturing flows to provide real-time visibility and efficiency, ensuring data availability for the business to recalibrate and move swiftly in response to capacity issues. "Security, data governance and skilled talent are the fulcrum of any resilient strategy," Najam said. Data is the new oil, but it needs to be refined to be valuable. Proper data governance and management are crucial for high-confidence analytics. Building strong partnerships with vendors and customers is also essential for a resilient organization.
The 10 biggest issues IT faces today

All the work around AI has further highlighted the value of data — for the organizations and hackers alike. That, along with the ever-increasing sophistication of the bad actors and the consequences of suffering an attack, has turned up the heat on CIOs. “Indications are that hackers/ransomware agents are becoming more aggressive. At the same time, operations and decision-making are increasingly dependent on data availability and accuracy. Meanwhile, the perimeter of exposure widens as remote workers and connected devices proliferate. This is an arms race, and the CIO must lead the charge by implementing better tools and training,” Carco says. ... Swingtide’s Carco sees a related issue that many CIOs face today, which is effectively managing vendors as the number of providers within the IT function dramatically grows. “CIOs are coming to recognize that an organization built for internal operations is not well-suited to managing dozens or hundreds of external providers, and the proliferation of contractual obligations can be overwhelming. In case of emergency, knowing who has your data, what their contractual obligations are to safeguard it, and how they are performing has become extremely difficult,” Carco says.
Solving the Challenges of Multicloud Cost Management

The issue starts with the mere task of importing billing data from cloud
providers. Although all major public clouds generate bills that detail what you
spent each month, they expose the billing data in a different way. Amazon Web
Services (AWS) generates a large CSV file... For its part, Azure expects
customers to import billing data using APIs. This means that simply getting all
of your billing data into a central location requires implementing multiple data
importation workflows. Once the data is centralized, comparing it can be
challenging because each cloud provider structures billing data a bit
differently. ... Consider, too, that GCP breaks cloud server spending into
separate costs for compute and memory. AWS and Azure don't do this; they report
billing information based only on the total resources consumed by a cloud
server. Thus, if you use AWS or Azure, you need to disaggregate the data
yourself if you want the level of granularity that GCP provides by default — and
doing so is important if you need to make an apples-to-apples comparison of what
you spend for both compute and memory across clouds.
The rise of SaaS security teams
The challenge of securing a SaaS environment demands a multifaceted security
strategy and that starts with a strong SaaS security team. Providing education
in line with employee’s job functions is essential. So, for security teams that
means ongoing training and professional development opportunities so they are
up-to-date on the latest threats and technologies. Training is particularly
important when it comes to the tools they’ll be utilizing in order to fully take
advantage of the capabilities offered. A security team is only as good as the
tools they are given to work with so companies need to make sure that they’re
deploying (and updating) advanced security tools that are tailored to cloud
applications. Teams also need standardized processes for incident response,
regular security assessments, and compliance monitoring as an established
workflow lends itself to consistency across an organization especially with the
diverse nature of the SaaS ecosystem. While not specific to setting up a
security team, once the team is in place zero trust’s principle of “never trust,
always verify” will go a long way to strengthening not only a SaaS security
posture but that of the entire organization.
Fostering tech innovators through entrepreneurial engineering education

Cultivating an entrepreneurial mind-set is critical in this educational
transformation. It encourages students to look beyond conventional career
paths and to consider how they can make societal impacts through innovation.
Entrepreneurial development cells and similar initiatives within universities
play a crucial role by providing mentorship, resources, and support systems
that propel students to explore innovative ideas and bring them to life. These
programs are pivotal in aiding students to launch their own ventures, thereby
enriching the start-up ecosystem directly. Moreover, there is a growing
emphasis on integrating emerging technologies such as artificial intelligence
(AI), machine learning, blockchain, and the Internet of Things (IoT) into the
engineering curriculum and to some extent this has already happened too. This
integration ensures that students are not only consumers of technology but
also its creators. Project-based problems utilizing these technologies to
address practical problems—such as developing AI-driven healthcare solutions
or blockchain-based supply chain enhancements—highlight the tangible impacts
of a robust educational framework.
Grooming Employees for Leadership Roles
Empathy is critical to fostering an inclusive work environment and building a
culture of trust. As a leader, one has to empower the team to have the courage
to take risks, make tough decisions in the face of adversity, and remove the
fear of failure. This is possible with open and honest communication with
teams and continuous encouragement to proactively drive ‘difficult’ projects.
Also, I believe a well-acknowledged team is a highly motivated team.
Recognising achievers in your team keeps them motivated to keep outperforming
and also fosters a culture of continuous improvement. While we keep achieving
new milestones and grow exponentially as an organisation, it is equally
important to recognise our talent and motivate them to grow. ... As a leader,
one has to set clear expectations with their teams, provide support and
mentoring, create a safe space for experimentation, encourage cross-functional
collaboration, empower teams to take decisions, and invest in technology and
infrastructure. As an organisation, Welspun Corp encourages its people to keep
acquiring new knowledge, refine their skills, and adapt to change.
Disaster recovery vs ransomware recovery: Why CISOs need to plan for both

Many organizations approach disaster recovery and cyber incident response
measures from a compliance perspective. They want to check all the required
boxes, which means that sometimes, “they do the bare minimum,” says Igor
Volovich, vice president of compliance strategy at Qmulos. While doing this is
necessary, it is not sufficient. The better approach, he suggests, would be to
treat compliance requirements as a detailed guide and adopt a more holistic
view based on data that is automatically collected, analyzed, and reported in
real time. This involves, of course, strengthening the security posture, as
well as developing or updating a thorough disaster recovery plan. ... When it
comes to creating the resilience strategy, Ramakrishnan recommends having
separate plans for different potential crises and storing them in physical
folders in the network operations center, in addition to electronic copies.
“While electronic access is crucial, physical documentation provides a
tangible backup and is easily accessible in situations where digital systems
may be compromised,” he says.
Preparing Your DevOps Workforce for the Shifting Landscape of Tech Talent
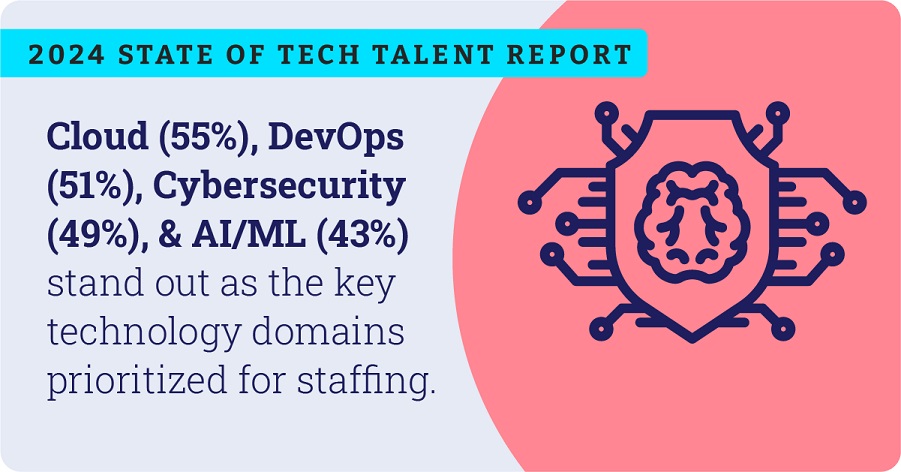
Traditionally, the tech industry placed a high value on academic degrees.
However, as the pace of technological change accelerates, the skills required
to succeed in this field are evolving rapidly. ... The move towards
skills-based hiring is a response to the pragmatic needs of the industry.
Hiring managers are increasingly prioritizing candidates with tangible skills
and certifications directly applicable to the projects and technologies at
hand. This approach opens up opportunities for a wider pool of talent,
including those who may have taken non-traditional paths to acquire their
skills. ... By prioritizing upskilling and cross-skilling initiatives,
companies can cultivate a versatile and adaptable workforce ready to tackle
the challenges of emerging technologies. It is much like applying DevOps
practices to staff development - being agile with iterative learning and
adaptation and continuously updating your skills. ... As we look to the
future, one thing is clear: the tech industry's approach to talent is
undergoing a profound transformation. Yesterday's methods won't train
tomorrow's workforce.
Here’s When To Use Write-Ahead Log and Logical Replication in Database Systems

Logical replication provides benefits compared to methods such as WAL.
Firstly, it offers the advantage of replication, allowing for the replication
of tables or databases rather than all changes, which enhances flexibility and
efficiency. Secondly, it enables replication, facilitating synchronization
across types of databases, especially useful in environments with diverse
systems. Moreover, logical replication grants control over replication
behavior including conflict resolution and data transformation, leading to
accurate data synchronization management. Depending on the setup, logical
replication can function asynchronously or synchronously, providing options to
prioritize performance or data consistency based on requirements. These
capabilities establish replication as a robust tool for maintaining
synchronized data in distributed systems. Logical replication presents a level
of adaptability for administrators by allowing them to select which data to
replicate for targeted synchronization purposes. This feature streamlines the
process by replicating tables or databases and reducing unnecessary
workload.
When to ignore — and believe — the AI hype cycle

Established tech incumbents and startups are transforming their technology
platforms simultaneously and big technology platform providers are also
displaying an incredible amount of agility in adapting. This translates into a
much more rapid evolution of the build with gen AI stacks compared to what we
saw in the early days of the build with the cloud. If compute and data are the
currency of innovation in gen AI, we have to ask ourselves where are startups
sustainably positioned versus established tech incumbents who have structural
advantages and more access to compute. Higher up in the stack, the opportunity
in applications seems quite vast — but given where we are in the hype cycle,
the reliability of AI outputs, the regulatory landscape and advancements in
cybersecurity posture are key gating factors that need to be addressed for
commercial adoption at scale. Lastly, foundation models have achieved the
performance they have due to pre-training on internet scale datasets. What
still lies ahead to realize the benefits of AI is the ability to assemble
large, high-quality datasets to build models in more industry-specific
domains.
Quote for the day:
“If you're doing your best, you won't
have any time to worry about failure.” -- H. Jackson Brown, Jr.
No comments:
Post a Comment