5 ways CIOs will disappoint their CEOs in 2023

Promise #1: The cloud will save money. Disappointment: It never did, and still
won’t Why it won’t: You can buy servers as cheaply as the cloud providers, and
they need to add a profit margin when they charge you for using them. What you
should promise instead: Unlike on-premises infrastructure, the cloud lets IT
easily add capacity in small increments when demand requires it. And — and this
is the biggie — it also lets IT shed capacity when it’s no longer needed. The
result? When demand is seasonal or unpredictable the cloud truly does save
money. But when demand is steady, or increases in demand are predictable,
on-premises infrastructure costs less. In the cloud, fixed costs are small but
incremental costs are big. The costs of on-premises systems are the opposite.
... Promise #4: ‘Agile’ means no more big-project
failures. Disappointment: Your name will be on some miserable Agile project
failures this year What’s going to go wrong: Your company is going to make
three Agile mistakes. The first, and worst, is that it won’t lose the habit of
insisting on multitasking — developers will still be asked to juggle multiple
competing projects, and their top priority will still be the next phone call.
Digital transformation: 4 security tips for 2023

Cybersecurity training keeps employees, customers, and vendors safe from
cyberattacks. Take the initiative to seek out top-of-the-line training resources
that will walk you through every aspect of promoting a secure environment.
Training does not need to be expensive. Learn how to avoid data breaches,
cultivate a security-first mindset, and maintain airtight security. While no
measure can prevent a cyberattack entirely, proper training can help minimize
your risk and reduce the chance of a breach. In addition, continue to sweat the
small stuff. While one weak password or phishing email may not seem like a big
deal, it’s in your best interest to take every threat seriously. Implement
strong password complexity controls and policies, develop and maintain phishing
campaigns, track user activity, and create policies for sharing information on
the internet. For example, posting information on social media could reveal
answers to common security questions. Staying vigilant will help your
organization avoid trouble in the future.
Wireless electronics can power trillions of IoT sensors. Here's how
/2022/12/28/image/jpeg/H0Q6wcA1EMGi3SIiMcxr9RP6Iq9ELfyA8ye28NkF.jpg)
We are yet to witness the full potential of IoT, but before that, we need to
overcome a big challenge. The sensors that make IoT networks possible require
power to stay functional, and unfortunately, our existing energy solutions are
not enough to support this demand. A team of researchers at King Abdullah
University of Science and Technology (KAUST) in Saudi Arabia has been working on
this problem and in their latest study, they propose an interesting solution.
The authors reveal details about wireless-powered electronics that promise to
meet the energy demands of IoT networks in a sustainable and eco-friendly
manner. Sensors are currently powered by technologies like Li-ion batteries.
Although batteries can power a large network of devices, they need to be
replaced again and again. Therefore a battery-based approach is expensive,
unsustainable, and harmful to the environment. For instance, conventional
batteries are made of metals that are procured through mining activities
resulting in air and soil contamination. Plus, when these batteries are not
carefully disposed of, they release toxic chemicals into our environment.
Agile vs. waterfall: Comparing project management cultures

Waterfall and agile culture are different forms of managing software projects,
but they are made of the same constituent concept: people managing people. The
values we covered, on the other hand, are not interchangeable. They are
different in kind, they are indeed the quintessential difference between agile
and waterfall. Following the scrum guide by the book, having squads, agile
coaches, dailies, and meetups might make you show up as agile, but unless your
values are aligned with the Manifesto, you’re just dressing waterfall as
agility. This is precisely the scenario we have been witnessing in the last few
years. As more and more companies see the results of strong agile culture
creating unicorns and industry juggernauts, more of them want a quick way to
execute digital transformation. What happens is that they start practicing
agile, but keep the waterfall values of control with a lack of flexibility and
hierarchy. Even worse, since the number of successfully transformed companies is
way smaller than those who just pretend to have transitioned, more and more
people have no experience with agile values, leading them to believe that doing
agile with waterfall values is perfectly normal.
What Rust Brings to Frontend and Web Development

“Rust to WebAssembly is one of the most mature paths because there’s a lot of
overlap between the communities,” Gardner told The New Stack. “A lot of people
are interested in both Rust and WebAssembly at the same time.” It’s not an
either “Rust or JavaScript” or even “WebAssembly or JavaScript” situation, he
said. It’s possible to blend WebAssembly with JavaScript. “You’re going to see
some people rewrite for WebAssembly, but you’re going to see some people take
advantage of WebAssembly where appropriate, and then use JavaScript for
connecting the various pieces under the hood, and maybe running portions of the
application as necessary,” he said. ... Chris Siebenmann, a Unix systems
administrator at the University of Toronto’s CS Labs, has a theory about that:
Languages spread when developers like using the language to accomplish things
that matter to them. Right now, that language is Rust. “Rust is a wave of the
future because a lot of people are fond of it and they are writing more and more
things in Rust, and some of these things are things that matter to plenty of
people,” Siebenmann wrote in 2021.
An Entity to DTO
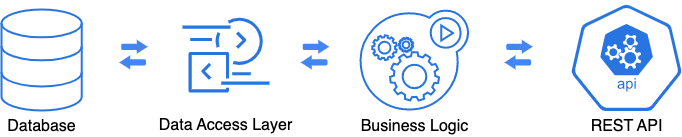
According to Martin Fowler, DTO is: “An object that carries data between
processes in order to reduce the number of method calls. When you're working
with a remote interface, such as Remote Facade, each call to it is expensive. As
a result, you need to reduce the number of calls. The solution is to create a
Data Transfer Object that can hold all the data for the call.” So, initially,
DTOs were intended to be used as a container for remote calls. In a perfect
world, DTOs should not have any logic inside and be immutable. We use them only
as state holders. Nowadays, many developers create DTOs to transfer data between
application layers, even for in-app method calls. If we use JPA as a persistence
layer, we can read an opinion that it is a bad practice to use entities in the
business logic, and all entities should be immediately replaced by DTOs. We
recently introduced DTO support in the JPA Buddy plugin. The plugin can create
DTOs based on JPA entities produced by data access layer classes and vice versa
– create entities based on POJOs. This allowed us to look at DTOs closer and see
how we can use them on different occasions.
Blockchain & Internet Of Things Are A Perfect Match

It won’t all be plain sailing if we’re to migrate IoT workloads to a
blockchain-based infrastructure. There are some key issues that need to be
overcome, but luckily a number of interesting solutions are already being built.
One of the main challenges with blockchain is that it’s not a low-latency
protocol. As such, most blockchains process a very low number of transactions
per second, and that presents issues for large-scale IoT device networks, as
these require extremely rapid rates of data transfer to keep up. Ethereum, the
world’s most popular smart contract blockchain, is only capable of processing
around seven transactions per second, for example. Moreover, the Ethereum
network is often congested, leading to high transaction costs. In its natural
state, it’s not a realistic platform for large-scale IoT deployments. The answer
to this problem may lie in scaling solutions like Boba Network, which is a
Layer-2 network and hybrid compute platform that powers lightning fast
transactions with much lower costs than traditional Layer-1 networks. Boba
Network relies on a technology called optimistic rollups, which enable multiple
transactions to be bundled into one and processed simultaneously.
Getting data loss prevention right
DLP is not a plug-and-play solution. There is considerable prep work that must
take place before anything is deployed. Reliable processes must exist for
identifying data, performing continuous inspections, and verifying results.
There must be a clear framework that identifies how data is classified, what
gets blocked, and who is responsible for ultimately setting policies.
Historically, many DLPs have relied on data access pattern recognition (REGEX),
which offers mediocre insights into how data is used. In other words, even with
the right people at the helm, the tools may be lackluster. DLP’s middling
capabilities, often wielded by untrained IT departments, have given it a
reputation for over-promising and under-delivering. Without a strong ability to
apply context to data, many DLPs are glorified string-matching tools that
overwhelm analysts with false positives. ... Much of DLP’s shortcomings are
attributable to untrained staff or poor implementations. Some DLPs are built
upon frameworks with functional limitations that may negatively impact their
effectiveness.
Ransomware ecosystem becoming more diverse for 2023

The ransomware ecosystem has changed significantly in 2022, with attackers
shifting from large groups that dominated the landscape toward smaller
ransomware-as-a-service (RaaS) operations in search of more flexibility and
drawing less attention from law enforcement. This democratization of ransomware
is bad news for organizations because it also brought in a diversification of
tactics, techniques, and procedures (TTPs), more indicators of compromise (IOCs)
to track, and potentially more hurdles to jump through when trying to negotiate
or pay ransoms. ... "Fast forward to this year, when the ransomware
scene seems as dynamic as ever, with various groups adapting to increased
disruptive efforts by law enforcement and private industry, infighting and
insider threats, and a competitive market that has developers and operators
shifting their affiliation continuously in search of the most lucrative
ransomware operation." ... This trend is likely to continue in 2023 with
ransomware groups expected to come up with new extortion tactics to monetize
attacks on victims where they're detected before deploying the final ransomware
payload.
Driving Employee Retention and Performance Through Recruiting
When the job market reopened as the pandemic wound down, there simply weren’t
enough workers to fill jobs. Recruiters and hiring managers were under a lot of
pressure to fill roles and fill them fast. The Muse CEO and founder Kathryn
Minshew explains it this way: With companies desperate to hire and HR pros
stretched thin, recruiters may be going rogue and stretching the truth to fill
roles. Or, they could say things they think are true, but they don’t have the
full picture of the workplace experience. She advises companies to be honest
about what it’s like to work there, including successes as well as areas for
improvement. Interviews should be a two-way street, and you must give candidates
enough time to ask questions about company culture. "When people feel like they
have opted into a situation with eyes wide open," Minshew says, "they’re much
more likely to accept the good and the bad, and to show up as engaged,
productive, satisfied employees. Rather than fluffy mission statements, what if
you were able to openly and transparently connect candidates to their personal
purpose from their first connection to your employer brand?
Quote for the day:
"A lot of people have gone farther than
they thought they could because someone else thought they could. " --
Zig Zigler
No comments:
Post a Comment