How to become an entrepreneurial engineer and create your own career path

"To be a successful entrepreneurial engineer, you must wear two hats: one with
a deep technical focus and the other focused on the goals of the business," said
Loren Goodman, CTO and co-founder of InRule Technology. "This allows you to make
decisions in real-time leveraging your understanding of diminishing returns on
both fronts. The why, the what and the how are traditionally separated, and
small changes to any part can have exaggerated effects on the others. You bring
this thinking together—for example, knowing that a feature can be done in a
fraction of the time if a small part was removed from scope and also knowing
that that part is not core to the business need." Goodman stressed that
entrepreneurial engineers must be curious about the bigger picture and be
unafraid to take on challenging problems. They must also be success-focused,
with a relentless passion for achieving the best solution to difficult problems,
no matter how unrealistic things might seem. Finally, he said, a successful
entrepreneurial engineer must be scrappy: "You are going to have to be
comfortable working without all the necessary resources for a long time while
still staying focused on your objectives."
Forensic Monitoring of Blockchains Is Key for Broader Industry Adoption
In the event that an adversary corrupts more than 1/3 of the master nodes in the
BFT committee of any given epoch, it is then technically possible for said
adversary to violate the safety and jeopardize the consensus by creating forks,
resulting in two or more finalized blockchains. However, certain messages would
need to be signed and sent by these nodes to make this happen, which can then be
detected by the system immediately after a fork with a length of only one
appears. The signed messages can then be used as irrefutable proof of the
misbehavior. Those messages are embedded into the blockchain and can be obtained
by querying master nodes for forked blockchains. This is what enables the
forensic monitoring feature, which can identify as many Byzantine master nodes
as possible, all while obtaining the proof from querying as few witnesses as
possible. For example, two separate honest nodes, each having access to one of
the two conflicting blockchains respectively, is sufficient for the proof.
Infrastructure-as-Code: 6 Best Practices for Securing Applications

Research from security platform provider Snyk reveals that many companies are
only starting out on their IaC journey, with 63% just beginning to explore the
technology and only 7% stating they’ve implemented IaC to meet current
industry standards. And with this practice comes changes in responsibility:
IaC further extends developers’ responsibility to include securing their code
and infrastructure. Misconfigurations can easily introduce security risks if
best practices are not followed. In fact, according to Gartner, “70% of
attacks against containers will be from known vulnerabilities and
misconfigurations that could have been remediated.” Often, security trails
behind the usage of IaC, resulting in configuration issues that are only
detected after applications are deployed. That doesn’t have to be the case. In
fact, the best way to ensure every configuration is secure, while still
benefiting from the speed and repeatability of IaC, is to build security
testing for IaC into developers’ workflows, the same as other forms of code.
The shift from DevOps and security to DevSecOps: 5 key roadblocks
There is DevOps plus security, and then there’s DevSecOps. What’s the
difference? In the first case, security is a third wheel. In the second,
it’s the third leg of the stool—an integral part of the system that’s almost
unnoticeable unless or until it disappears. Indeed, to be effective,
security must be everywhere—throughout the pipeline used to build and deploy
as well as the runtime environment. In the DevSecOps model, security is a
shared responsibility for development, security and operations teams and
throughout the entire IT lifecycle. However, many organizations are
challenged to integrate, rather than just tack on, security measures. This
is a huge issue when a company’s own security is at stake, but an increasing
number of attacks on the software supply chain is leaving tens, hundreds,
even thousands of organizations vulnerable. There are many granular
recommendations for achieving DevSecOps. Here are the bigger-picture issues
that your organization must address to move beyond security as an
afterthought.
Agile Architecture - What Is It?
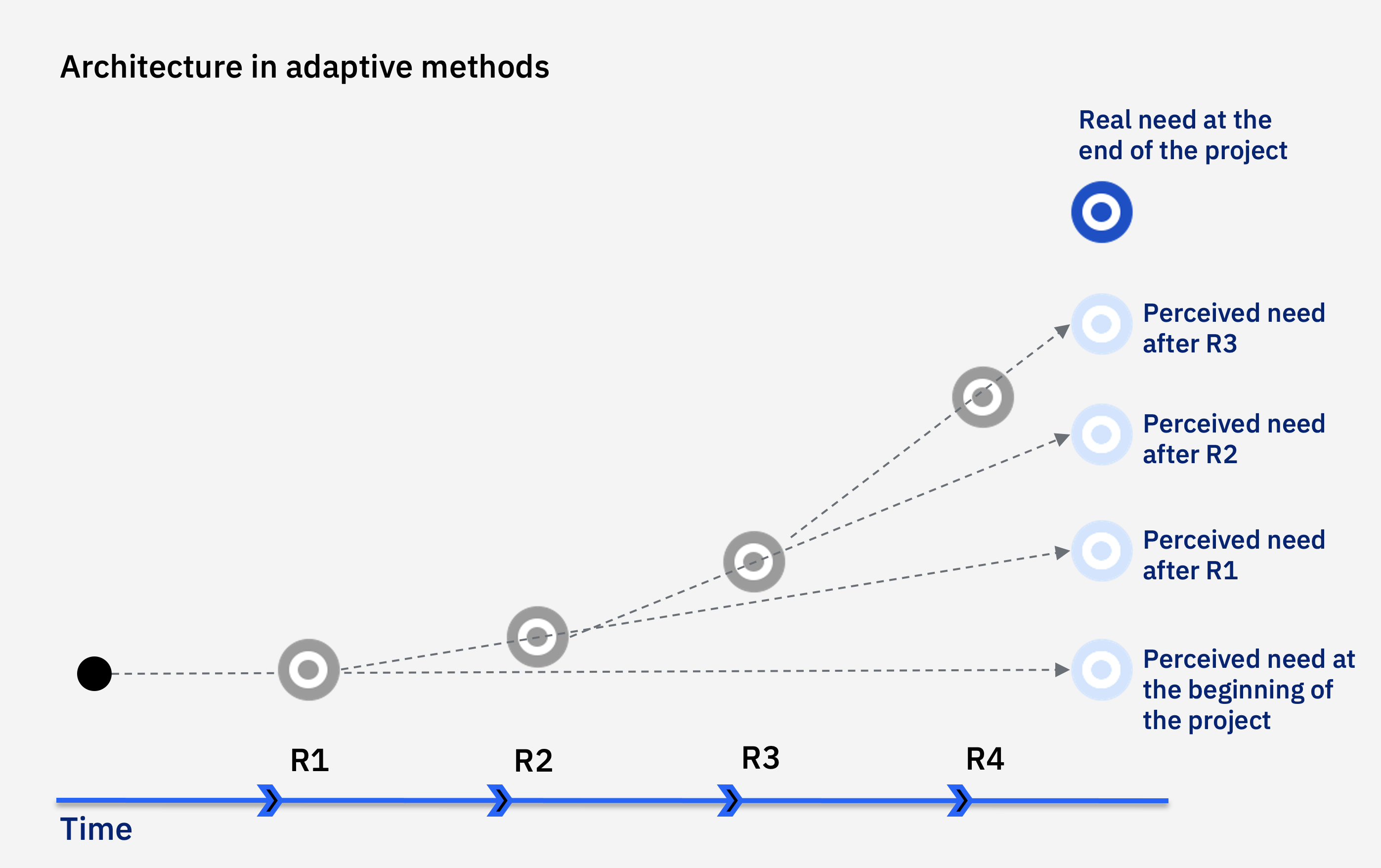
From the definition, the two very important terms emerge including, Emerging
Design and Intentional Architecture. Emergent Design is the process of
analyzing and extending the architecture just enough to implement and
validate the next increment in the development cycle. Intentional
Architecture is about seeing the big picture. Large corporations need to
simultaneously respond to new business challenges with large-scale
architectural initiatives. On large scale we can understand that to meet the
business objective, multiple teams, products, and systems will be involved.
In this case, Emergent Design is not enough as it is circumscribed in a
single team. Without Intentional Architecture, we can have several problems
such as difficulty integrating, validate and maintaining the fulfillment of
non-functional system requirements, low reuse, redundancy of solutions, etc.
The intentional architecture will give the teams a common
objective/destination to be reached, allowing the alignment of efforts and
the parallelization of the work of independent teams. In other words, it
will be the guiding track, the glue between the teams' work.
NRA Reportedly Hit By Russia-Linked Ransomware Attack

The NRA did not immediately respond to Information Security Media Group's
request for comment. But Andrew Arulanandam, managing director of public
affairs for the NRA, took to Twitter to say: "NRA does not discuss matters
relating to its physical or electronic security. However, the NRA takes
extraordinary measures to protect information regarding its members, donors,
and operations - and is vigilant in doing so." Allan Liska, a ransomware
analyst at the cybersecurity firm Recorded Future, told NBC that Grief is
"the same group" as Evil Corp. The news outlet verified that the information
in the leaked files includes grant proposal forms, names of recent grant
recipients, an email sent to a grant winner, a federal W-9 form and minutes
from the organization's virtual meeting in September. Sam Curry, CSO of
Cybereason, tells ISMG, "It's unlikely this is a strategic attack, but time
will tell. The way it would be strategic is to further divide the left from
the right in the U.S. … The most likely scenario is that it's motivated by
greed, and it has the potential to inadvertently explode politically. The
next move is in the NRA's hands."
Is the Indian SaaS Story Overhyped?

Experts watching the SaaS space opine that after Freshworks recent listing,
global perception towards Indian SaaS companies has changed. Last month,
Freshworks became the first Indian software maker to list on Nasdaq. “SaaS
companies in India are gaining acceptance and attention from investors.
Initially, investors were slow due to the nature of revenue which is a money
sucker but as the customer base grew with a lower drop, the revenue started
to look good. Things have changed a lot after Postman and Freshworks. Indian
SaaS companies are now seriously looked at as potential unicorns,” said Anil
Joshi, managing partner, Unicorn India Ventures. The SaaS ecosystem is
relatively nascent in India and is led by players such as Freshworks,
Capillary, Eka, etc., said Anurag Ramdasan, partner, 3one4 Capital. “While
there are double-digit unicorns in Indian SaaS today, it’s still a very
early ecosystem and we are seeing a lot of innovative SaaS in the seed to
series A stage in India,” he said. Many companies that have become
soonicorns and unicorns have great consumer stories and investors today look
at India as a huge consumer story.
How do I select an SD-WAN solution for my business?
Network security is also gaining greater importance as cyber-security
threats multiply, leading to cloud-based security techniques converging with
SD-WAN in the SASE framework. But the transition to these technologies can
be challenging, with significant support required from the SD-WAN partner.
Therefore, enterprises need to evaluate SD-WAN providers based on three
principal criteria. First, does the provider’s network reach align with the
enterprise’s geographic locations and does the provider offer a Tier 1 IP
backbone to realize the full performance advantages of SD-WAN? Second, does
the provider offer a managed SD-WAN, including local internet or MPLS
access, with end-to-end delivery, technical implementation support, and
service assurance to help manage complexity? Third, does the provider have a
clear SASE roadmap integral to its SD-WAN vision? This includes services
like zero-trust network access (ZTNA) and cloud access security broker
(CASB) for remote workers and cloud firewall and secure web gateway (SWG) to
support the branch level.
The Rise of Event-Driven Architecture

In the REST framework, an API isn’t aware of the state of objects. The
client queries the API to find out the state, and the role of the API is to
respond to the client with the information. However, with an event-driven
API, a client can subscribe to the API, effectively instructing it to
monitor the state of objects and report back with real-time updates.
Therefore, behavior shifts from stateless handling of repeatable,
independent requests to stateful awareness of the virtual objects modeled on
real-world operations. Event-driven APIs are a great way to meet the demands
of modern end-users who expect customized and instantaneous access to
information. Applying these APIs is easy to do in one-off, bespoke
environments. However, things get more complicated when you need to offer
this level of service at scale, and not every enterprise is ready to handle
that level of complexity. To avoid amassing significant technical debt,
organizations and developers should offload this complexity to a third party
with the capabilities to synchronize digital experiences in real-time and at
scale.
We Are Testing Software Incorrectly and It's Costly
The tests you write are tightly coupled to the underlying design of your
code. Design is constantly evolving. You now not only have to refactor the
designs of your production code — you have to change your tests, too! In
other words, your tests should help you with the refactoring, giving
confidence, but instead, it is only making you work harder and it's giving
no confidence of things still working correctly. I will not even mention the
mock hell for brevity (please Google about it). But instead of abandoning
refactoring or unit tests, all you need to do is free yourself from the
mistaken definition of "unit testing." Focus on testing behaviors! Instead
of writing unit tests for every public method of every class, write unit
tests for every component (i.e., user, product, order, etc.), covering every
behavior of each component and focusing on the public interface of the unit.
To achieve that, you will need to learn how to structure your code properly.
Please don't package your code by technical concerns (controllers, services,
repositories, etc.). Senior devs structure their code by domain.
Quote for the day:
"The world's greatest achievers have
been those who have always stayed focussed on their goals and have been
consistent in their efforts." -- Roopleen
No comments:
Post a Comment