Artificial Intelligence Is Smart, but It Doesn’t Play Well With Others

Humans hating their AI teammates could be of concern for researchers designing
this technology to one day work with humans on real challenges — like defending
from missiles or performing complex surgery. This dynamic, called teaming
intelligence, is a next frontier in AI research, and it uses a particular kind
of AI called reinforcement learning. A reinforcement learning AI is not told
which actions to take, but instead discovers which actions yield the most
numerical “reward” by trying out scenarios again and again. It is this
technology that has yielded the superhuman chess and Go players. Unlike
rule-based algorithms, these AI aren’t programmed to follow “if/then”
statements, because the possible outcomes of the human tasks they’re slated to
tackle, like driving a car, are far too many to code. “Reinforcement learning is
a much more general-purpose way of developing AI. If you can train it to learn
how to play the game of chess, that agent won’t necessarily go drive a car. But
you can use the same algorithms to train a different agent to drive a car, given
the right data” Allen says. “The sky’s the limit in what it could, in theory,
do.”
CDR: The secret cybersecurity ingredient used by defense and intelligence agencies
Employees in the defense and intelligence sector are in near-constant contact
with each other, sharing information often under challenging circumstances. They
move files and documents from low trust environments into networks that hold a
nation’s most sensitive data, where a data breach could have a serious impact on
national security. Consequently, when it comes to sharing any kind of document,
these teams cannot risk threats slipping through the net. Human attackers are
now using machines to engineer malware at a pace only imaginable a few years
ago. Today, it’s possible to engineer a new piece of malware and to make each
version of that file suitably different so that it’s almost impossible for
traditional malware protection solutions to identify. In the same way that
Facebook or Twitter use algorithms to create a truly unique social feed of
information that is tailored to the interests and tastes of a user, bad actors
can use similar algorithms to deploy essentially the same underlying threats but
packaged in ways that simply evade detection.
Gartner advises tech leaders to prepare for action as quantum computing spreads

Cambridge Quantum’s efforts to expand quantum infrastructure got significant
backing earlier this year when Honeywell said it would merge its own quantum
computing operations with Cambridge Quantum, to form an independent company to
pursue cybersecurity, drug discovery, optimization, material science, and
other applications, including AI. Honeywell said it would invest between $270
million – $300 million in the new operation. Cambridge Quantum said it would
remain independent, working with various quantum computing players, including
IBM. The lambeq work is part of an overall AI project that is the longest-term
project among the efforts at Cambridge Quantum, said Ilyas Khan, founder, and
CEO of Cambridge Quantum, in an e-mail interview. “We might be pleasantly
surprised in terms of timelines, but we believe that NLP is right at the heart
of AI more generally and therefore something that will really come to the fore
as quantum computers scale,” he said. Khan cited cybersecurity and quantum
chemistry as the most advanced application areas in Cambridge Quantum’s
estimation.
How to Not Lose Your Job to Low-Code Software
The amount of work you have is driven by the ability of software to make a
meaningful difference in your organization. Take a look at your current queue
of work. If your team is like most IT teams there will be a mountain of unmet
demand for new applications or additional functionality for existing
applications. Thinking that any amount of automation will reduce that demand
to zero is like thinking that a faster car will get you to Mars. If low code
software starts taking some of your work, there will likely be other projects
you can work on. If you handle this right, you can even shuffle some of the
painful projects over to the party-goers on the low code bus. ... Secondly,
and more fundamentally, there are certain aspects of software engineering that
are harder to automate than others - making it unsuitable terrain for the low
code party bus to drive across. For example, low code tools make it easy for
non-developers to create a table to store data. But they can't do much to help
the non-developer structure their tables to best map to the business problem
they are trying to solve.
API contract testing with Joi

When you sign a contract, you expect both parties to hold their end of the
bargain. The same can be true for testing applications. Contract testing is a
way to make sure that services can communicate with each other and that the
data shared between the services is consistent with a specified set of rules.
In this post, I will guide you through using Joi as a library to create API
contracts for services consuming an API. ... Before we get started, let me
give you some background about contract testing. This kind of testing provides
confidence that different services work when they are required to. Imagine
that an organization has multiple payment services that utilize an
Authentication API. The API logs in users into an application with a username
and a password. It then assigns them an access token when the log-in operation
is successful. Other services like Loans and Repayments require the
Authentication API service once users are logged in. ... Contract tests are
designed to monitor the state of an application and notify testers when there
is an unexpected result. Contract tests are most effective when they are used
by a tool that relies on the stability of other services.
Regulating Crypto: Is It Different – Or Is It the Same?
Regulators need to know what the technology is capable of, but they need not
know every technical detail just to make good law. “If you can understand
clearly what the technology is doing, I think that you can make pretty good
judgments about what the fundamental financial activity is and what regulatory
box that financial activity can or should fit in,” he told Webster. Strip
those technologies down a bit, and they boil down to some basic underpinning
concepts that lend themselves to governance. At the core of blockchain and
cryptos is database architecture, said Gerety. “It has some neat properties,
but nowhere else in the financial services industry do you get regulated
differently if you use SAP or Oracle,” he said. To get a sense of how one
might approach “newness” in a sector, he offered a concept of a matrix, with
axes denoting what the future “feels like” and might actually “be.” Babies
will pretty much always “be” and “feel” the same. Not much in the way of
technology will change the experience or feelings one will have with birthing
and raising a child, despite the newness of, well, becoming a parent.
Information Theory: Principles and Apostasy
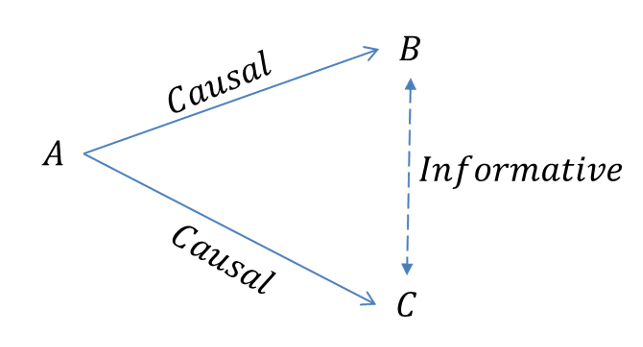
Let’s start with a data science interview question. Usually, as part of an
initial screening round for entry level candidate I like to find an example on
their CV of a project that used real life data. Real life data is much nastier
than academic and research data. Its chalked full of missing data, mixed
(integer and string) data and outliers that make consuming and modeling the
information grossly more difficult. Invariably most of the conversation
revolves around these real world considerations. How do you handle missing
data? Usual answers involve some sort of information replacement strategy like
replace them with the average value of the column. Fair and reasonable. How do
we deal with malformed or mixed data? Again usually a fair answer involving
mapping strings to numbers. Finally what did you do about the large outlier
events? Usually the answer is that they ‘removed them’ because you ‘can’t be
expected to predict rare events.’ The ultimate justification: it improved the
models accuracy. That’s good answer if building a forecast is a game or
contest, much worse if you want to use it.
The OCC Officially Recognizes the Critical and Permanent Role of Blockchain in Banking

This is noteworthy for a couple of reasons. First, it is a recognition that
many banks, along with a slew of other financial institutions, are adopting
DLT as a technology enabling better processes. Simply put, financial
institutions are moving past the exploratory phase of DLT and are now actually
implementing the technology into their operations. Secondly, the OCC is
declaring its intent to explore and define appropriate governance processes
for banks to deploy when such changes are implemented. In other words, the OCC
is defining its intent to regulate how such changes should take place. ... The
immutability of a distributed ledger provides a new level of security. It is
challenging to establish a single customer view across different jurisdictions
and business lines. With mutualized data management, DLT allows permitted
parties to share data securely and in real time, which could address
challenges of Know Your Customer (KYC) and Anti Money Laundering (AML). The
themes are clear – DLT injected into the banking and financial ecosystem is an
equalizer, a simplifier and a fortifier.
How data drives Air Canada’s cargo business

For business intelligence, the airline has been a long-term user of WebFocus
from Tibco. It also uses Microsoft PowerBI. Riboulet’s reason for using two BI
platforms is because “they complement each other”, each having different
functions it finds useful. For example, WebFocus offers Air Canada the ability
to push out reports via email, a feature not available in PowerBI. Riboulet
says this is useful for people working in operations, who may only have access
to their phone and need to see embedded reports. Also, the data team noticed
that many business users require similar datasets and attributes, which can be
pulled together into pre-built reports. The company also uses the data grid
feature in WebFocus to aggregate data in a way that can easily be customised
by users and can be exported to Microsoft Excel. It has also deployed WebFocus
Hyperstage, as a staging area for data, to avoid direct access to its
on-premise database systems. Riboulet views the data team at Air Canada Cargo
as internal consultants who discuss data requirements with
businesspeople.
How Much Power Should Finance Have Over Their Automations?

If you want to automate your finance function and bring lower costs to operate
the financing and accounting needs, taking control can provide you with
numerous benefits. This includes prioritization of your processes that align
with your strategic vision, controlling resource investments and commitments,
and insuring SOX control frameworks are adhered to at the onset. It’s not
surprising that some finance organizations can feel underserved by their IT
partners, as ITs responsible for supporting the whole organization and finance
operations can take a back seat to other priorities. This does not mean that
IT should be left aside. IT will have a role, even if you run your own
automation program end-to-end, and you will need them to have a seat at the
table. You will want to avoid creating a shadow IT group and truly focus your
financial resources on process improvement and automation. It’s best practice
to leverage your IT team for infrastructure, network security, understanding
ERP/system schedules, roadmaps, and disaster recovery processes (at a
minimum). It is also recommended to adopt the cloud version of the tools,
which can significantly reduce the needs of your IT org
Quote for the day:
"Problem-solving leaders have one
thing in common: a faith that there's always a better way." --
Gerald M. Weinberg
No comments:
Post a Comment