Digital transformation strategy: 7 factors to re-examine about yours now

In the rush to adjust to work-from-home orders, seismic supply and demand
shifts, changing customer and partner needs, and a global health crisis, some
shortcuts may have been taken, or longer views set aside. Heading into 2021, IT
leaders can take a step back to reassess some important aspects of their digital
transformation efforts to make sure they’re on the right track not only for 2021
but beyond. ... While the urgency to transform was necessary, some initiatives
conceived or implemented in haste may deserve a second or even third look. “Some
may have implemented changes at a pace that didn’t allow for the standard level
of care and detail that would normally go into digital transformation projects.
Others pivoted away from their technical roadmap,” says Greg Stam, managing
director in the CIO advisory at digital business consultancy AHEAD. “It’s
critical to re-baseline your digital transformation strategy, starting with any
new business goals.” ... “As so many IT leaders scrambled to implement new
technologies to help employees remain productive and connected from home, some
may be starting to find that the tools they implemented aren’t really serving
their true purpose,” says Rob Wiley
Understanding Linus's Law for open source security
Some people assume that because major software is composed of hundreds of
thousands of lines of code, it's basically impossible to audit. Don't be fooled
by how much code it takes to make an application run. You don't actually have to
read millions of lines. Code is highly structured, and exploitable flaws are
rarely just a single line hidden among the millions of lines; there are usually
whole functions involved. There are exceptions, of course. Sometimes a serious
vulnerability is enabled with just one system call or by linking to one flawed
library. Luckily, those kinds of errors are relatively easy to notice, thanks to
the active role of security researchers and vulnerability databases. Some people
point to bug trackers, such as the Common Vulnerabilities and Exposures (CVE)
website, and deduce that it's actually as plain as day that open source isn't
secure. After all, hundreds of security risks are filed against lots of open
source projects, out in the open for everyone to see. Don't let that fool you,
though. Just because you don't get to see the flaws in closed software doesn't
mean those flaws don't exist. In fact, we know that they do because exploits are
filed against them, too. The difference is that all exploits against open source
applications are available for developers (and users) to see so those flaws can
be mitigated.
World Economic Forum calls cybersecurity one of the "key threats of the next decade"

The analysts behind the report called cybersecurity failure among the "highest
likelihood risks" of the next 10 years and IT infrastructure breakdown "among
the highest impact risks of the next decade." In a survey of experts included in
the report, 39% of respondents said cybersecurity failure was a critical threat
to the world right now and ranked as the most pertinent risk on the list after
infectious disease, extreme weather events, and livelihood crises. Nearly 50%
said it would be a concern for the next three to five years. The report suggests
that in order to make the transition to a fully digital world more smooth,
multiple things need to be changed, including "insisting on security and privacy
by design in the development of new technologies and digital services." Hitesh
Sheth, president and CEO at cybersecurity firm Vectra, said the only surprise in
the World Economic Forum Global Risks Report is that cybersecurity failure
wasn't ranked higher. "Without secure, high-functioning IT, addressing all the
other crises the report names, from climate to digital inequality, becomes much
harder. For years our well-understood cyber vulnerabilities have been met with
too much rhetoric, too little real action," Sheth said.
UK's leading AI startup and scaleup founders highlight the main pain points of running a fast growth business in the AI sector

“Finding enough time to really invest in strategy” is a significant challenge,
according to Miriam Cha, COO and co-founder at Rahko. “We work in two very
rapidly evolving areas — AI for drug/material discovery and quantum computing —
so developing and continually adapting and refining a strategy that will win
requires a lot of careful thought and deep discussion. “We have four founders at
Rahko, and we come together very regularly for strategy sessions that can last
several days, with the understanding that no one does anything else until we
have answered the questions we need answered. This has taken a huge amount of
discipline to maintain, but has meant that we are able to make really well
thought-out decisions and head in what we believe between us to be the right
direction.” Ky Nichol, CEO at Cutover, adds that “it’s hard to maintain
focus on strategic goals, with new opportunities and use cases for our
capabilities emerging constantly, it’s important to maintain a resilient
perspective and prioritise our strategic objectives.” Tim Weil, CEO at
Navenio, also agrees that developing a solid business strategy with a team that
is all moving in the right direction is essential for the success of any fast
growth business, in the AI sector or otherwise.
The future of work: Coming sooner than you think

Zero trust is a general framework in which every user and every system must
authenticate itself continually, so if a breach occurs, attackers can’t move
laterally to compromise other systems across the organization. SASE is a more
recent scheme that combines SD-WAN and security into a single, simplified cloud
service that can be scaled easily. Together, they can go a long way to reduce
the risks incurred by remote work at scale. But there’s more to a bright future
of work than technology solutions. Effective remote management, an area where
software development managers tend to have extensive experience, may be most
important of all. InfoWorld contributor and former CIO Isaac Sacolick has been
there, and in “7 best practices for remote development teams,” he outlines some
tried-and-true techniques – including continuous, transparent planning. Sacolick
also observes that automation can help simplify remote development, such as
automated testing and change management. It’s important to acknowledge, though,
that not all jobs can be remote. Network World contributor Zeus Kerravala
pinpoints the skills necessary to run the data center of the future in “How the
data center workforce is evolving,” which cites an Uptime Institute study
predicting a 15% rise in on-prem data center jobs over six years.
Quantum Leap: Scientists Build Chip That Can Handle Thousands Of Qubits

Quantum computers are at a similar stage that classical computers were in their
40s when machines needed control rooms to function. However, this chip,
according to the scientists, is the most advanced integrated circuit ever built
to operate at deep cryogenic temperatures. “The quantum computers that we have
now are still lab prototypes and are not commercially relevant yet. Hence, this
is definitely a big step towards building practical and commercially relevant
quantum computers,” said Mr Viraj Kulkarni, “But I think that we are still far
away from it. “This is because of the ‘Error Correction’. Any computing device
always has errors in it and no electronic device can be completely perfect.
There are various techniques that computers use to correct those errors. “Now
the problem with quantum computing is that qubits are very fragile. Even a
slight increase in temperature, vibrations, or even cosmic rays can make qubits
lose their quantumness, and this introduces errors. So the key question of
whether we can really control these errors is still relevant.” Nivedita Dey,
research coordinator at Quantum Research and Development Labs, said the qubit
noise is still a roadblock in developing quantum computers.
A Beginners Guide to Using Django’s Impressive Data Management Abilities
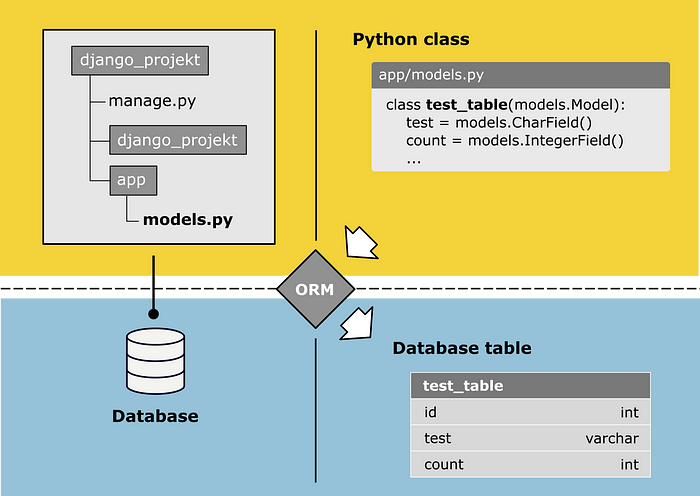
Django is a Python Web framework which helps developers to bring applications
from concept to completion as fast as possible.¹ A High-level framework like
Django offers a comprehensive set of features for web development like an HTTP
application server, a storage mechanism such as a database, a template engine, a
request dispatcher and an authentication module. As I mentioned before, I try to
focus on the part of Django that allows you to interact with your relational
databases, the Object-Relation Mapper (ORM).³ The ORM brings you all functions
to create and manipulate data and tables of your database without using any SQL
commands. What I tried to explain with the following image, each Django App
includes a module named mocels.py, which defines the structure of the database
tables you want to create. To translate the Python Objects into database tables,
the ORM comes into place. The ORM is responsible for the communication with your
database, which includes the translation of your defined models into the right
database structure and the execution of any database operations.
A Day with Intel on Hacking and Scaling Machine Learning with Open Source

Machine learning models are designed to be resilient, flexible and meet business
goals but often, engineers who build the product and algorithms face obstacles
to ensure that it works reliably, quickly and at scale. Frameworks are not easy
to use. As many of the world’s leading organizations embrace approaches to
scaling machine learning, Intel is offering the tools, applications and hardware
to make it easier for developers to build, deploy and manage artificial
intelligence and machine learning models that can be used by tens of thousands
of people instead of just a few. ... Join us on Feb. 10 at 9 a.m. PT for a live
Day of Machine Learning with Intel discussion, where we’ll dive deeper into
oneAPI. We’ll explore the software at scale issues with machine learning and the
hardware needed for it. We’ll look at the tools and the infrastructure that is
used for developing, deploying and managing the algorithms. We’ll also dive into
questions around how Intel’s oneAPI toolkit is a way to resolve problems that
teams face, and how oneAPI fits with existing frameworks such as PyTorch and
TensorFlow.
What's New in IT Security?

If the plan is to install a new software or security package, or to update
software from a vendor across a plurality of devices, the coordination of the
software or software upgrade release should be uniformly executed across all end
users and locations, and across all devices and platforms. Commercially
available software distribution platforms are available to assist with this
task. The preferred method of performing software and security upgrades is a
“push” distribution of any new software release in which IT pushes out the new
software or software upgrade to the end device, network or platform
automatically. This is in contrast to the “pull” method that notifies the user
that a new version of software is available, but that depends upon the user to
pull or download the new release onto his or her device or network. “Pull” is
the better methodology because you don’t have to worry about users failing to
perform a download, leaving themselves (and the company) open to security
vulnerabilities that a new software release can resolve. The SolarWinds
compromise occurred because malware had gotten embedded in a software release
that clients were installing. The lesson for IT is to vet your vendors’ security
practices as they pertain to data centers, operational software, business
partners and the end products that they are selling to you.
Hacker Breached Florida City's Water Treatment System
A hacker breached a Florida city's water treatment network on Friday, increasing
the amount of lye that would have been added to the water to a dangerous
level. But city officials in Oldsmar, Florida, say they were able to spot
the intrusion and quickly reverse the setting before it took effect. Reuters
reports that the intruder was able to access the water treatment network
software after first gaining access to TeamViewer remote access and control
software. "Importantly, the public was never in danger," Pinellas County Sheriff
Bob Gualtieri said during a Monday press conference. Oldsmar, Florida, which is
about 17 miles northwest of Tampa, has a population of about 15,000. In recent
years, officials have focused increasing attention on the security of industrial
control systems used to manage municipalities' electricity and water. Such
systems often are connected to the internet and could pose vast public safety
risks if infiltrated by hackers. Questions will likely now be raised about how
the city used and configured TeamViewer for remote access, including which
access controls were in place. TeamViewer has long been an attractive target
because it's designed to give administrators full, remote access to and control
of systems.
Quote for the day:
"At the heart of great leadership is a
curious mind, heart, and spirit." -- Chip Conley
No comments:
Post a Comment