Usability Testing: the Ultimate Guide [Free Checklist]
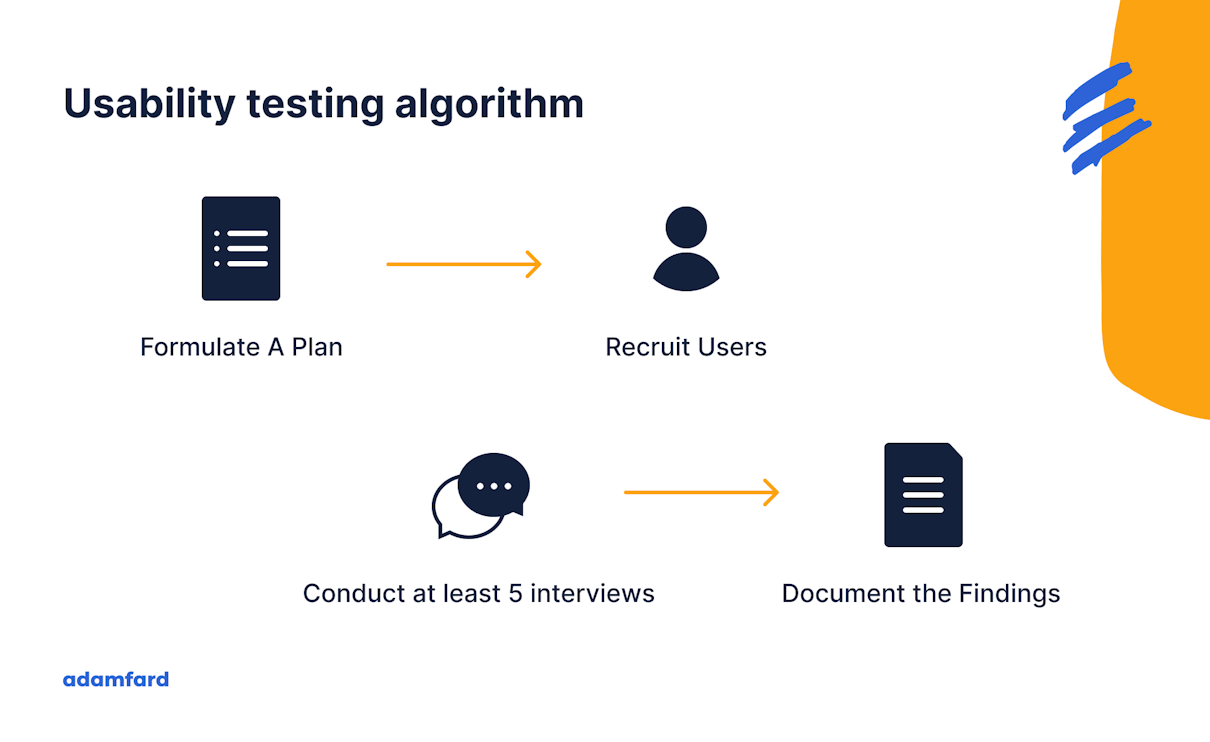
Generally speaking, usability testing comes in two types: moderated and
unmoderated. Moderated sessions are guided by a researcher or a designer, while
the unmoderated ones rely on users’ own unassisted efforts. Moderated tests are
an excellent choice if you want to observe users interact with prototypes in
real-time. This approach is more goal-oriented — it lets you confirm or
disconfirm existing hypotheses with more confidence. On the other hand,
unmoderated usability tests are convenient when working with a substantial pool
of subjects. A large number of participants allows you to identify a broader
spectrum of issues and points of view. However, it’s important to underline that
testing isn’t that black and white. It’s best to look at this practice as a
spectrum between moderated and unmoderated testing. Sometimes, during
unmoderated sessions, we like to nudge our subjects into the right direction
through mild moderation when necessary. Testing our prototypes can provide us
with a wide array of insights. Fundamentally, it helps us spot flaws in our
designs and identify potential solutions to the issues we’ve uncovered. We learn
about the parts of our product that confuse or frustrate our users. By
disregarding this step, we’re opening up to the possibility of releasing a
product that causes too much friction.
Linux malware backdoors supercomputers
ESET researchers have reverse engineered this small, yet complex malware that is
portable to many operating systems including Linux, BSD, Solaris, and possibly
AIX and Windows. “We have named this malware Kobalos for its tiny code size and
many tricks; in Greek mythology, a kobalos is a small, mischievous creature,”
explains Marc-Etienne Léveillé, who investigated the malware. “It has to be said
that this level of sophistication is only rarely seen in Linux malware.” Kobalos
is a backdoor containing broad commands that don’t reveal the intent of the
attackers. It grants remote access to the file system, provides the ability to
spawn terminal sessions, and allows proxying connections to other
Kobalos-infected servers, Léveillé notes. Any server compromised by Kobalos can
be turned into a Command & Control (C&C) server by the operators sending
a single command. As the C&C server IP addresses and ports are hardcoded
into the executable, the operators can then generate new Kobalos samples that
use this new C&C server. In addition, in most systems compromised by
Kobalos, the client for secure communication (SSH) is compromised to steal
credentials.
Disrupting the patent ecosystem with blockchain and AI

Applying the power of AI and blockchain to IP assets enables a paradigm shift in
how IP is understood and managed. Companies that understand and adopt this new
paradigm will be rewarded. Last year, we announced the inclusion of IPwe — the
world’s first AI and blockchain-powered patent platform, among our selection of
the next wave of enterprise blockchain business networks. The Paris-based
start-up has since deployed a suite of leading-edge IP solutions, removing
barriers by addressing fundamental issues within today’s patent ecosystem. IPwe
is partnering with IBM to accelerate its mission to address the inefficiencies
in the patent marketplace. IBM Cloud and IBM Blockchain teams are working
closely with IPwe on a multi-year project to assist IPwe in its mission to
deliver world class solutions to its enterprise, SME, university, law firms,
research institutions and government customers, with a heavy emphasis on meeting
the needs of financial, technology and risk management executives. In addition
to giving patent owners tools that provide greater visibility, effective
management, and ease of conducting transactions with patents, the IPwe Platform
reduces costs for innovators, and creates commercial opportunities for those
that wish to partner or engage in financial transactions.
Low-Code Platforms and the Rise of the Community Developer: Lots of Solutions, or Lots of Problems?
Most community developers will progress through three stages as they become more
capable of using the low-code platform. Many community developers won’t progress
beyond the first or second stage but some will go onto the third stage and build
full-featured applications used throughout your business. Stage 1—UI Generation:
Initially they will create applications with nice user interfaces with data that
is keyed into the application. For example, they may make a meeting notes
application that allows users to jointly add meeting notes as a meeting
progresses. This is the UI Generation stage. Stage 2—Integration: As users gain
experience, they’ll move to the second stage where they start pulling in data
from external systems and data sources. For example, they’ll enhance their
meeting notes application to pull calendar information from Outlook and email
attendees after each meeting with a copy of the notes. This is the Integration
stage. Stage 3—Transformation: And, finally, they’ll start creating applications
that perform increasingly sophisticated transformations. For example, they may
run the meeting notes through a machine learning model to tag and store the
meeting content so that it can be searched by topic. This is the Transformation
stage.
XOps: Real or Hype?

Like DevOps, the various types of Ops aim to accelerate processes and improve
the quality of what they're delivering: software (DevOps); data (DataOps); AI
models (MLOps); and analytics insights (AIOps). Some consider the different Ops
types important since the expertise required for each type differs. Others
believe it's just hype, specifically relabeling what already exists and/or
there's a risk that the fragmentation created by all the different groups may
create extra bureaucracy that frustrates faster value delivery. Agile software
development practices have been bubbling up to the business for some time. Since
the dawn of the millennium, business leaders have been told their companies need
to be more agile just to stay competitive. Meanwhile, many agile software
development teams have adopted DevOps and increasingly they've gone a step
further by embracing continuous integration/continuous delivery (CI/CD) which
automates additional tasks to enable an end-to-end pipeline which provides
visibility throughout and smoother process flows than the traditional waterfall
handoffs. Like DevOps, DataOps, MLOps, and AIOps are cross-functional endeavors
focused on continuous improvement, efficiency and process improvement.
Sigma Rules to Live Your Best SOC Life

In the Security Operations space, we have been using SIEM's for many years
with varying degrees of deployments, customization, and effectiveness. For the
most part, they have been a helpful tool for Security Operations. But they can
be better. Like any tool, they need to be sharpened and used correctly. After
a while, even a sharpened tool can become dull from too much use: and with a
SIEM that takes the form of too many events creating the dreaded ALERT
FATIGUE!!! This is real for security operations and must be addressed; because
the more alerts, the more an engineer must work on, and the more they will
miss. Insert Sigma Rules for SIEMS (pun intended); a way for Security
Operations to implement standardization into the daily tasks of building SIEM
queries, managing logs, and threat hunting correlations. What is a Sigma rule,
you may ask? A Sigma rule is a generic and open, YAML-based signature format
that enables a security operations team to describe relevant log events in a
flexible and standardized format. So, what does that mean for security
operations? Standardization and Collaboration are now more possible than ever
before with the adoption of Sigma Rules throughout the Security Operations
community.
How AI Is Radically Changing Cancer Prediction & Diagnosis

Risk modelling includes assessing risks at different time points, which can
determine the preventive measures that need to be taken at different stages.
This can provide insight into the risk of developing cancer at a time point
compared to the other, which is not useful. Hence, scientists trained Mirai to
have an ‘additive hazard layer’. This layer can predict a patient’s risk at a
time point, let’s say four years, as an extension of the risk at a previous
time point, say three years, instead of comparing two different time points.
This can help the model learn to make self-consistent risk assessments even
with variable amounts of follow-ups as inputs. Secondly, the model includes
non-image risk factors like age and hormonal variables but does not
necessarily require them at the test time, since a trained network can extract
this information from mammograms. Hence, this model can be adopted globally.
Lastly, standard training models do not work even with minor variations, such
as a change in the mammography machine used. Mirai used an ‘adversarial’
scheme, to de-bias such models to learn from mammogram representations
agnostic to the source clinical environment.
How To Port Your Web App To Microsoft Teams
While there are many different paths to building and deploying Teams apps, one
of the easiest is to integrate your existing web apps with Teams through what
is called “tabs.” Tabs are basically embedded web apps created using HTML,
TypeScript (or JavaScript), client-side frameworks such as React, or any
server-side framework such as .NET. Tabs allow you to surface content in your
app by essentially embedding a web page in Teams using <iframes>. The
application was specifically designed with this capability in mind, so you can
integrate existing web apps to create custom experiences for yourself, your
team, and your app users. One useful feature about integrating your web apps
with Teams is that you can pretty much use the developer tools you’re likely
already familiar with: Git, Node.js, npm, and Visual Studio Code. To expand
your apps with additional capabilities, you can use specialized tools such as
the Teams Yeoman generator command line tool or Teams Toolkit Visual Studio
Code extension and the Microsoft Teams JavaScript client SDK. They allow you
to retrieve additional information and enhance the content you display in your
Teams tab.
How AI Can Read Your Brain Waves
:max_bytes(150000):strip_icc():format(webp)/GettyImages-1223790532-b9202544771f4246912063b14cc0e41a.jpg)
The music study is only one of many recent efforts to understand what people
are thinking using computers. The research could lead to technology that one
day would help people with disabilities manipulate objects using their minds.
For example, Elon Musk’s Neuralink project aims to produce a neural implant
that allows you to carry a computer wherever you go. Tiny threads are inserted
into areas of the brain that control movement. Each thread contains many
electrodes and is connected to an implanted computer. "The initial goal of our
technology will be to help people with paralysis to regain independence
through the control of computers and mobile devices," according to the
project’s website. "Our devices are designed to give people the ability to
communicate more easily via text or speech synthesis, to follow their
curiosity on the web, or to express their creativity through photography, art,
or writing apps." Brain-machine interfaces might even one day help make video
games more realistic. Gabe Newell, the co-founder and president of video game
giant Valve, said recently that his company is trying to connect human brains
to computers. The company is working to develop open-source brain-computer
interface software, he said.
Q&A: Dataiku VP discusses AI deployment in financial services
AI is also a real revolution within risk assessment, notably through the enhanced use of alternative data. This is true both for traditional risks and emerging risks such as climate change, helping all financial players — banks and insurers alike — to reconsider how they price risks. Those who have developed a strong expertise in leveraging alternative data and agile modeling have been able to truly benefit from their investment during the ongoing health crisis, which has deeply challenged traditional models. Lastly, the positive impact of AI on customers should not be underestimated. Financial services are confronted with an aggressive competitive landscape as well as demand from customers for improved personalisation, driving improved customer orientation in these organisations. The capacity to build 360° customer views and optimise customer journeys, notably on claims management, are two examples of areas where AI has significantly supported deep transformation within banks and insurance companies, with yet much more to be delivered.
Quote for the day:
"Leadership is a potent combination of
strategy and character. But if you must be without one, be without the
strategy." -- Norman Schwarzkopf
No comments:
Post a Comment