As The Cloud Transforms Enterprises, Cybersecurity Growth Soars

Moving beyond password vaults and implementing cloud-based Identity Access
Management (IAM) and Privileged Access Management (PAM) solutions are proving
to be adaptive enough to keep up with cloud-based transformation projects
being fast-tracked to completion before the end of the year. Leaders in
cloud-based IAM and PAM include Centrify, who helps customers consolidate
identities, deliver cross-platform, least privilege access and control shared
accounts while securing remote access and auditing all privileged sessions.
Enterprise spending on cybersecurity continues to grow despite the pandemic,
driven by the compelling cost and time-to-market advantages cloud-based
applications provide. Gartner predicts end-user spending for the information
security and risk management market will grow at a compound annual growth rate
of 8.2% between 2019 and 2024, becoming a $207.7B market in four years. CIOs
and their teams say the pace and scale of cloud transformation in the latter
half of 2020 make cloud-based IAM and PAM a must-have to keep their cloud
transformation initiatives on track and secure.
Azure + Spring Boot = Serverless - Q&A with Julien Dubois
With “lift and shift”, one of the troubles you will have is that you will need
to port all your Spring MVC Controllers to become Spring Cloud functions.
There are different ways and tricks to achieve this, and you will have some
limitations, but that should work without spending too much money. Also, you
wouldn’t touch your business code too much, so nothing important should break.
Then, an Azure Function works in a very different way from a classical Spring
Boot application: you can still benefit from a Hibernate second-level cache or
from a database connection pool, but you can easily understand that they will
not be as efficient, as their time to live will be much lower. Using a
distributed cache will be a huge trouble here. Also, your function can scale
up a lot better than your one-node Tomcat server, so maybe your database will
not work as well as before, as it wasn’t built for that sort of load. You
could use instead of a database like CosmosDB, or a caching solution like
Redis, which are two very widely used options on Azure. This is a lot more
work, but that’s the only way to get all the benefits from a serverless
platform.
The power of feelings at work
Articulating feelings can also bring new understanding to apparent
insubordination or poor performance. For example, our firm was once engaged to
help an oil refinery stymied by a total lack of response from its employees
when it tried to elicit ideas for a cost-reduction effort. To understand what
was behind the disengagement, we held focus groups across functions and grades
and conducted one-on-one interviews with senior executives. We sought out
individuals whom others identified via a questionnaire (e.g., to whom do you
go within the organization if you have a problem?) as particularly in touch
with employee feelings and asked for their input on what was stopping action.
Across the sessions, an articulation of feelings — frustration, fear, and
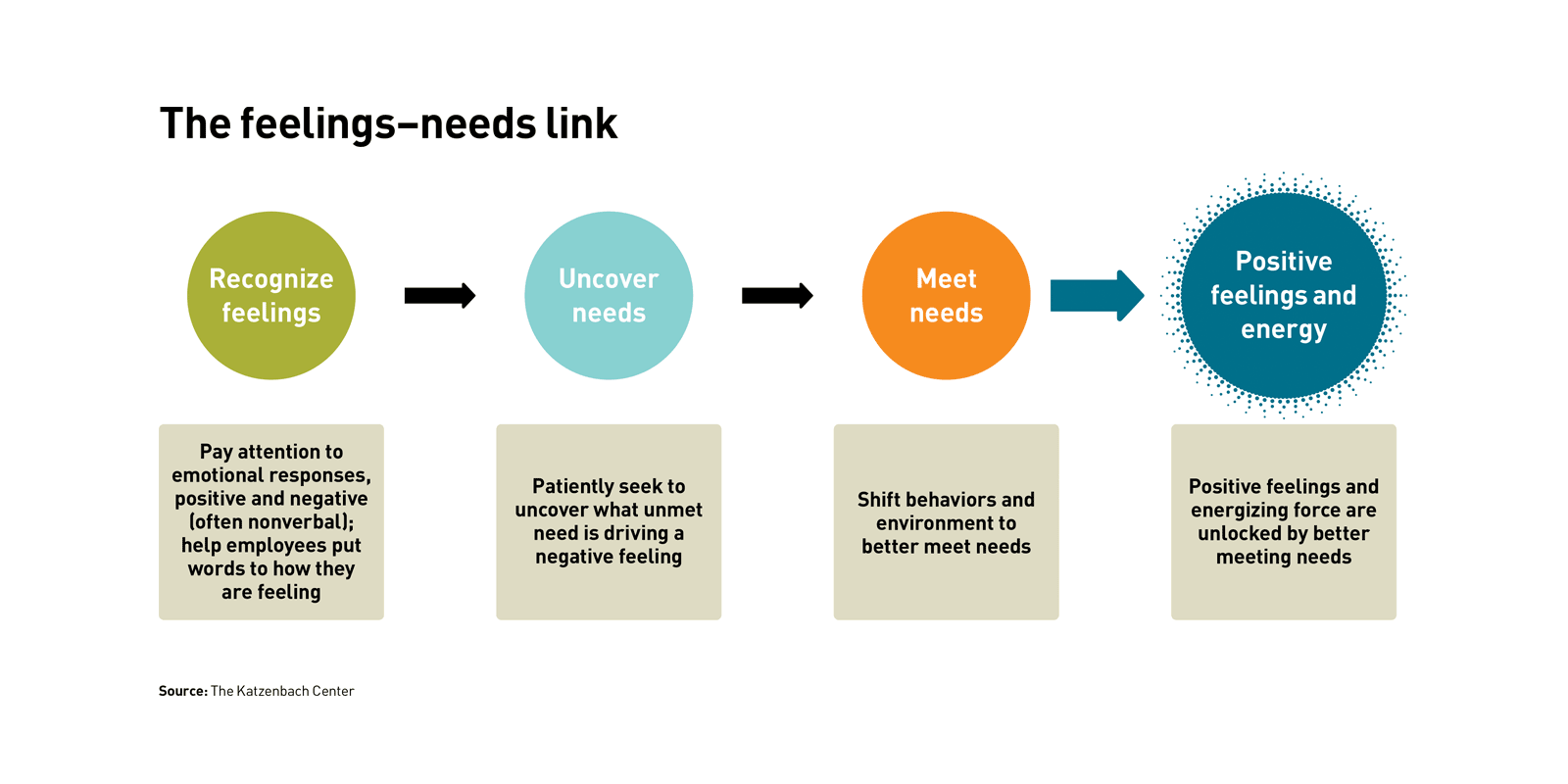
hopelessness — emerged. ... Because feelings are always messengers of needs,
the next step is to follow the feeling to the need. Needs are actionable and
often multidimensional. Taking action from an understanding of needs sidesteps
recrimination and invites compassion. Psychologist Marshall Rosenberg, founder
of the Center for Nonviolent Communication, which advocates speaking from
needs to navigate conflict, writes, “From the moment people begin talking
about what they need, rather than what’s wrong with one another, the
possibility of finding ways to meet everybody’s needs is greatly increased.”
Cybersecurity Bounces Back, but Talent Still Absent
Leave it to a global pandemic to disrupt industries many of us have assumed to
be stalwart. Companies fortunate enough not to traffic in hard goods are
realizing they can survive (and cut significant costs) by moving to
work-from-home workforces. This shift, with an estimated 62% of the workforce
now working from home, demonstrates the increased need in hiring for
cybersecurity personnel required to manage these new business models. At
first, this sounds great for the resilience of the cybersecurity sector — but
this means the already existent skills shortage for security professionals is
about to get a lot worse. The result is that the lines between what have been
considered "pure" cybersecurity roles and, well, everything else are becoming
blurred. A recent (ISC)² survey shows that many security professionals are
being leveraged to support general IT requirements to accommodate different
needs for work at home amid the pandemic. That makes sense. Companies need to
have the infrastructure in place to support these new remote workers logging
in from their home ISPs while also ensuring the security of sensitive data and
intellectual property.
Secondary DNS - Deep Dive
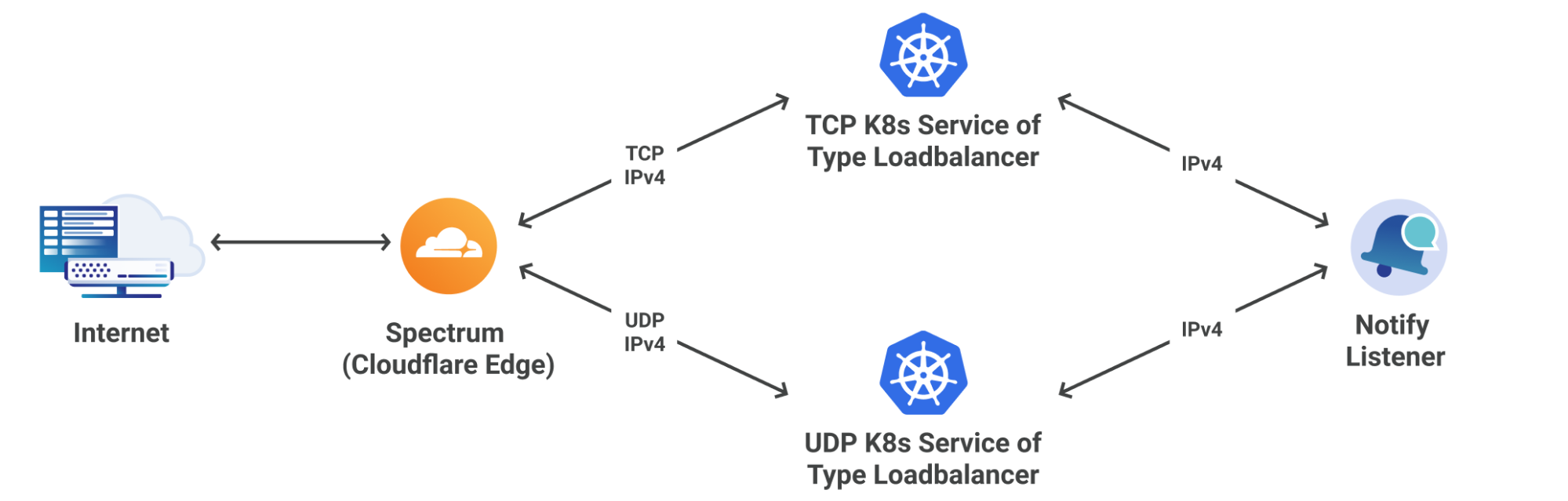
Secondary DNS has many use cases across the Internet; however, traditionally,
it was used as a synchronized backup for when the primary DNS server was
unable to respond to queries. A more modern approach involves focusing on
redundancy across many different nameservers, which in many cases broadcast
the same anycasted IP address. Secondary DNS involves the unidirectional
transfer of DNS zones from the primary to the Secondary DNS server(s). One
primary can have any number of Secondary DNS servers that it must communicate
with in order to keep track of any zone updates. A zone update is considered a
change in the contents of a zone, which ultimately leads to a Start of
Authority (SOA) serial number increase. The zone’s SOA serial is one of the
key elements of Secondary DNS; it is how primary and secondary servers
synchronize zones. Below is an example of what an SOA record might look like
during a dig query. ... In addition to serial tracking, it is important to
ensure that a standard protocol is used between primary and Secondary DNS
server(s), to efficiently transfer the zone. DNS zone transfer protocols do
not attempt to solve the confidentiality, authentication and integrity triad
(CIA); however, the use of TSIG on top of the basic zone transfer protocols
can provide integrity and authentication.
Leadership lessons from Accenture’s CIO
The only certain thing about technology is that what we use today is not what
we will use tomorrow. In my senior team, I look for a mindset of flexibility,
which not everyone has. In my interviews I assess the candidate’s willingness
to rotate to the new and untried, while at the same time protecting our core
systems. The second competency stems from the fact that we live in a world of
publicity and social media, where people are always watching what you are
doing. When you live in this world, and represent your company, you need an
identifiable personal brand. I’m not talking about a being a big shiny icon
and writing a lot of white papers. It’s about having the confidence in who you
are and communicating, in a few simple words, your unique value. My
responsibility is to help people recognize their personal brand and to use it
as the foundation of their confidence to lead. We put out a capability called
ALICE (Accenture Legal Intelligent Contract Exploration), which uses applied
intelligence and machine learning for natural language processing across all
of our contracts.
TOGAF and the history of Enterprise Architecture

TOGAF assumes it will be used by companies with many departments and that are
hierarchical in terms of structure and decision-making. Thus, the framework
maps directly onto these types of organizational structures. For example, a
whole chapter is devoted to describing how to establish and operate an
Architectural Board. An Architectural Board is a central planning committee
that oversees the design and implementation of the Enterprise Architecture.
There're chapters about Risk Management, Architecture Partitioning, and
Architectural Contracts. Remember, as mentioned earlier, TOGAF has 52
chapters. It's exhaustive. However, while TOGAF is highly structured, it can
accommodate other methodologies, such as Agile and DevOps. TOGAF understands
it's best for companies that are highly structured organizations, but it also
understands that no two companies are alike. TOGAF supports versatility. TOGAF
accepts the iterative model, which is a critical component of Agile. In fact,
there is a chapter in TOGAF titled "Applying Iteration to the ADM" that
discusses the nature and implementation of iteration in the Application
Development Model. Also, DevOps can be accommodated by TOGAF.
Renault’s blockchain project aims at vehicle compliance
Deployed in collaboration with IBM, XCEED is based on ‘Hyperledger Fabric’
blockchain technology. It is designed to track and certify the compliance of
components and sub-components. The tool looks to enable greater responsiveness
and efficiency at a time of what Renault believes is ‘ever-greater regulatory
stringency.’ Here, the carmaker is referring to the European Parliament’s new
market surveillance regulations which came into effect at the start of
September. These rules mean enhanced controls for vehicles already on the
market. Therefore, the production chain must adjust its structure to respond
to regulations within shorter timeframes. With XCEED, blockchain is used to
create a trusted network for sharing compliance information between
manufacturers. Each party maintains control and confidentiality over its data,
without compromising its integrity, while also increasing security and
confidentiality. Testing was conducted at Renault’s Douai plant, with over one
million documents archived and a speed of 500 transactions per second.
Blockchain in Mortgages – Adopting the New Kid on the Block
The world is fast progressing within the technology domain and digital
services have penetrated to the unexplored corners of life. Digital
transformation has become the backbone of companies and industries throughout
the planet. Traditional banking and lending which were thriving a couple of
years back, are dying a quick death. Post the pandemic the banks and other
financial institutions have increased the push on digital channels for
acquisition and customer servicing. Agile and scalable lending platforms are
cutting acquisition costs and convey in growth in loan volumes. India’s eleven
largest banks namely ICICI Bank Ltd, Axis Bank Ltd, Kotak Mahindra Bank, HDFC
Bank, Yes Bank, Standard Chartered Bank, RBL Bank, South Indian Bank, etc.
have come together to form a consortium for leveraging the blockchain
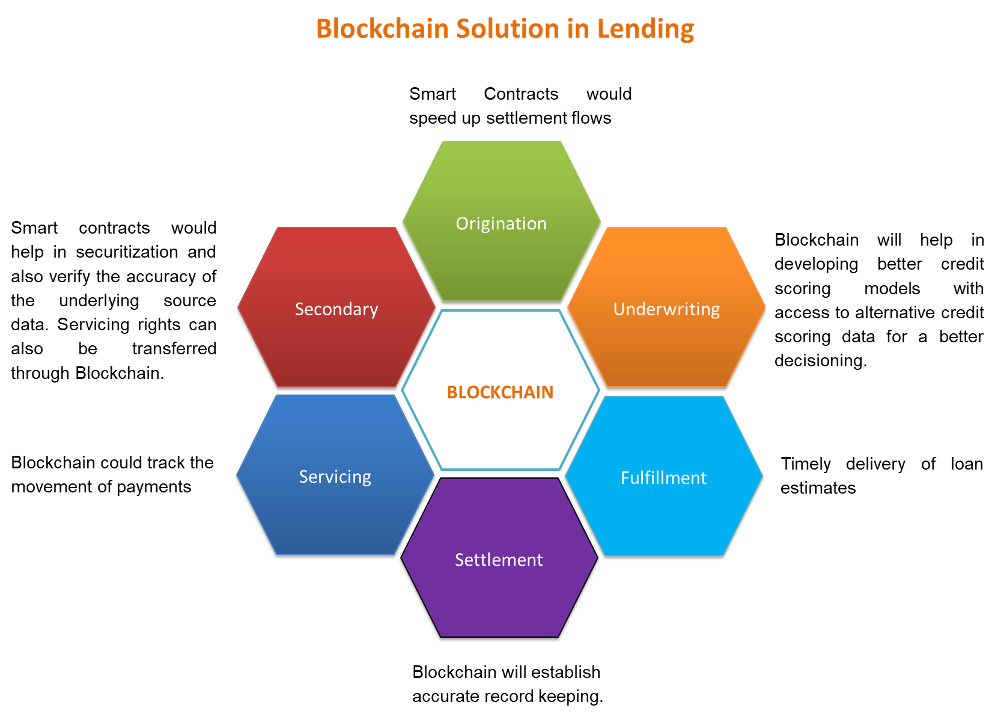
technology. Blockchain solutions will help increase operational efficiency,
faster TAT, enhanced customer delight, increase transparency, and authenticity
of transactions. Banks are going to be ready to make better credit decisions
thanks to the globally shared and distributed network and increased
communication between banks. Blockchain will reduce fraud and data
manipulation and can deliver better portfolios.
How Microsoft is looking to MetaOS to make Microsoft 365 a 'whole life' experience

Microsoft's highest level MetaOS pitch is that it is focused on people and not
tied to specific devices. Microsoft seems to be modeling itself a bit after
Tencent's WeChat mobile social/payment app/service here, my sources say.
Microsoft wants to create a single mobile platform that provides a consistent
set of work and play services, including messaging, voice and video, digital
payments, gaming, and customized document and news feeds. The MetaOS consists
of a number of layers, or tiers, according to information shared with me by my
contacts. At the lowest level, there's a data tier, which is implemented in
the Office substrate and/or Microsoft Graph. This data tier is all about
network identity and groups. There's also an application model, which includes
work Microsoft is doing around Fluid Framework (its fast co-authoring and
object embedding technology); Power Apps for rapid development and even the
Visual Studio team for dev tools. Microsoft is creating a set of services and
contracts for developers around Fluid Core, Search,
personalization/recommendation, security, and management. For software vendors
and customers,
Quote for the day:
"As a leader, you set the tone for your entire team. If you have a positive attitude, your team will achieve much more." -- Colin Powell
No comments:
Post a Comment