
Underlying all this likely nonsense is the obvious fact that almost every computer chip in the world is made outside of the U.S., often in Asian locations. I used to laugh when I was told that I couldn’t bring my Lenovo laptop in, but I could bring in my Dell laptop, which itself was full of nothing but Asian-made chips. If you are worried about supply chain threats, and you should be, it’s not just one little purported spy chip you should be worried about. You can’t find a computerized device in the U.S. that doesn’t have foreign-made chips. There isn’t some secret U.S. government agency that goes around inspecting all those chips for security holes or backdoors before they get put into all our computers. To me it is a hilarious idea that the Chinese would have to insert a specialized, tiny spy chip when it would be far easier to put an intentional weakness or backdoor into any of the hundreds of chips that are used in every computer on the planet. It would be far easier to hide in the weeds than to create a dedicated spy chip that any hardware expert would notice and question.
Overcoming the top obstacles to digital transformation success
You should begin developing a solid digital transformation strategy by first establishing a small, integrated governance team with equal representation and influence from the business and IT, including security. The governance team will enable a clear line of communication between digital and legacy IT teams and ensure initiatives are synchronized so appropriate investments are made to harden core systems while securely exposing functionality that enables digital initiatives. While security was not cited as one of the top three barriers, it remains a concern. With the highly-fragmented state of data across most enterprises today, exposing data sources to new digital systems creates yet another opportunity for attack. IT and security are integral to governance to limit risk exposure as new digital capabilities are introduced. As you launch digital initiatives, especially if you are behind the digital curve, partner with digital leaders who can provide the capabilities you need to get your products to market securely while you continue learning and developing internally.
IT departments struggle to balance innovation with everyday IT operations

“Organisations have become acutely aware of the critical role technology now plays in overall business strategy, from enabling a more productive and connected workforce to increasing market share and customer loyalty,” she said. “The Insight Intelligent Technology Index signifies how competing demands on IT are inhibiting their ability to plan and innovate.” The index, which queried 200 IT professionals, also found 79% of IT decision makers felt there were not enough resources to effectively support the demand for innovation, with another 33% saying innovation was expected of them despite existing processes, practices and business operations not evolving in ways that allowed them to do so. Another 30% cited a lack of clearly defined roles and responsibilities in the organisation as a reason for the lack of innovation.
CEO Fraud: Barriers to Entry Falling, Security Firm Warns
To hide their efforts, attackers may alter the rules for a compromised email account to divert copies of their fraudulent messages - and potentially replies - to other, attacker-controlled accounts, Digital Shadows notes. Such fraud can take the form of false invoices or modifying legitimate ones, but swapping in details for accounts controlled by attackers. Because BEC scams typically exploit weak corporate controls, organizations can use many actions to better defend themselves, Digital Shadows says. One of the most basic steps is to ensure that email accounts always have two-step verification enabled. That at least prevents an attacker that has the login credentials from accessing the account. Controls around wire transfers can also be shored up, Digital Shadows says. Fraudsters have had success, for example, by compromising the email account of a CEO and then sending an email to the finance department saying a payment needs to be made.
Discovering Blind Spots in the Data

Usually, there’s a trade-off between precision and recall. Improving precision can drop the recall and vice-versa. It’s up to the business stakeholders to tell the data scientists, which is more important: identifying more actual escalations at the cost of having more false escalations classified as escalations (high recall, low precision)? Or minimizing false escalations at the cost of missing many actual escalations (low recall, high precision)? If the business stakeholders go for high recall and low precision, they will need to engage more people to deal with a higher number of real escalations and possibly many false escalations. If they choose low recall and high precision, they can engage fewer people to deal with the escalations but will risk having model miss many real escalations. In our case, initially, the Business stakeholders preferred high precision over low recall so that they didn’t have to deal with a lot of false escalation alerts. Our dataset had a few features whose value changed with time. This introduced us to a phenomenon called signal leakage.
Why 60% of IT security pros want to quit their jobs right now

The main reasons cited by the IT pros who wanted to leave were job dissatisfaction and the lack of growth opportunities within their companies, said the release. The survey gathered data from more than 9,000 IT security professionals and decision-makers in the enterprise, said the release. This survey could give businesses better insight into how to retain and support their current tech talent. Other top reasons for employees looking to quit include unhealthy work environments (53%), absence of IT security prioritization from executives or upper management (46%), unclear job expectations (37%), and lack of mentorship (30%), said the release. Buy-in from upper management is crucial for security efforts, since only 38% of CEOs are really engaged in cybersecurity. This low engagement percentage is proof that executives don't prioritize cybersecurity as much as other factors of business, which further validates the dissatisfaction IT professionals are feeling.
NASA is using HoloLens AR headsets to build its new spacecraft faster
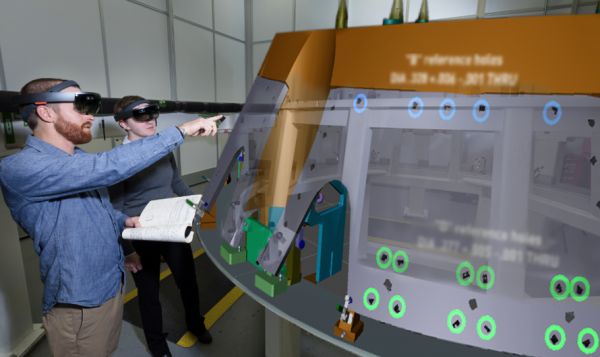
In the headset, the workers can see holograms displaying models that are created through engineering design software from Scope AR. Models of parts and labels are overlaid on already assembled pieces of spacecraft. Information like torquing instructions—how to twist things—can be displayed right on top of the holes to which they are relevant, and workers can see what the finished product will look like. The virtual models around the workers are even color-coded to the role of the person using the headset. For Jory’s team, which is currently constructing the heat shield skeleton of Orion, the new technology takes the place of a 1,500-page binder full of written work instructions. Lockheed is expanding its use of augmented reality after seeing some dramatic effects during testing. Technicians needed far less time to get familiar with and prepare for a new task or to understand and perform processes like drilling holes and twisting fasteners. These results are prompting the organization to expand its ambitions for the headsets: one day it hopes to use them in space.
Why today's containers and microservices will be tomorrow's legacy sooner than you think
The industry will be stuck with container platforms because these are interesting technologies that give the operators a taste of the power of running massive jobs at scale. Unfortunately, the ROI of maintaining that platform is elusive, since very few companies running these platforms will ever reach a point where they can even optimize job scheduling, and the cost of maintaining the container platform itself competes with the modest improvements in the developer's user experience. A similar phenomenon was seen with OpenStack half a decade ago, when, in the rush to have an in-house cloud, many companies grossly underestimated the short- and long-term associated costs and are now stuck maintaining OpenStack in perpetuity for the sake of the unnamed applications running on top of it. Well, that's a depressing thought, isn't it? But true. And why? Well, because technology change is hard.
“Given the way the data was captured and displayed, it would not be readily available or searchable, but [the information commissioner] considers that a motivated individual could locate and extract the data in a more permanent way,” the notice said. Although the USB stick contained more than 1,000 files overall, just 1% of this information could be classified as being personal in nature. Also, a subsequent investigation by the ICO revealed less than 2% of the airport’s 6,500-strong workforce had received data protection training. “Given that Heathrow Airport is Europe’s busiest airport, where high-level security should be inherent, loss or unauthorised disclosure of personal data of staff could have presented a greater risk if found by individuals who had not handled the data responsibly,” the penalty notice said. “Taking into account all of the above, the commissioner has decided that the penalty is £120,000.” According to the report, the USB stick was found in Kilburn, west London, on 16 October 2017, before being handed in to a national newspaper 10 days later
Behavioral Biometrics: Key Challenges
As more companies move away from passwords toward behavioral biometrics, they face new challenges, says Rajiv Dholakia, vice president products at Nok Nok Labs, a company which is into next generation authentication. Behavioral biometrics relies on a behavioral trait of an individual, rather than a physical trait. Examples include speech patterns, signatures and keystrokes. "There are no standards as such in this area on how the information is collected, how it's stored and how it's processed," Dholakia says in an interview with Information Security Media Group. "And therefore, there may be some privacy hazards associated with the technique unless a manufacturer makes it super clear exactly what is being collected, how it's being processed and whether that profile data is anonymized." Other behavioral biometrics issues include accuracy and concerns about passive collection of information from users, he says. "Moreover, when you are using behavioral biometrics, you have to be super certain that the information coming from all sensors is coming from a real device as opposed to a virtual machine," he says
Quote for the day:
"He who cannot be a good follower cannot be a good leader." -- Aristotle

No comments:
Post a Comment