What if robots learned the same way genAI chatbots do?

To unlock further potential in robotic learning, training objectives beyond
supervised learning, such as self-supervised or unsupervised learning, should
be investigated. It is important to grow the datasets with diverse,
high-quality data. This could include teleoperation data, simulations, human
videos, and deployed robot data. Researchers need to learn the optimal blend
of data types for higher HPT success rates. Researchers and later industry
will need to create standardized virtual testing grounds to facilitate the
comparison of different robot models. ... Think of it as giving robots more
demanding, more realistic challenges to solve. Scientists are also looking
into how the amount of data, the size of the robot’s “brain” (model), and its
performance are connected. Understanding this relationship could help us build
better robots more efficiently. Another exciting area is teaching robots to
understand different types of information. This could include 3D maps of their
surroundings, touch sensors, and even data from human actions. By combining
all these different inputs, robots could learn to understand their environment
more like humans do. All these research ideas aim to create smarter, more
versatile robots that can handle a wider range of tasks in the real
world.
Chief AI Officers: Should Every Business Have One?

The CAIO's mandate extends beyond technical oversight. These leaders define
their company's AI vision, bring solutions to market and establish ethical
governance frameworks, Laqab said. Their systems address data privacy
protection and eliminate bias in AI implementations while aligning with
organizational objectives. At Ascendion, every data scientist and machine
learning engineer develops solutions under stringent guidelines, which Laqab
describes as "prioritizing rigorous planning and transparency" - an approach
critical in regulated sectors such as healthcare and finance where trustworthy
AI proves essential. ... CAIOs work in strategic partnership with CIOs and
CTOs to integrate AI capabilities into organizational systems. Laqab
underscored the importance of unified planning where AI leaders and technology
teams implement initiatives without duplicating or straining resources. This
approach builds cross-functional momentum, enabling CAIOs to embed AI in
broader processes while maximizing existing IT investments and supporting
overall strategy. ... "Just as the CDO emerged to manage data, the CAIO is
essential for navigating the complex landscape of AI technologies.
New research reveals AI adoption on rise, but challenges remain in data governance & ROI realisation

Commenting on the survey, Noshin Kagalwalla, Vice President & Managing
Director, SAS India, said: “Indian companies are undoubtedly making progress
in AI adoption, but significant work remains. The challenge lies not only in
deploying AI but also in a way that it is trustworthy, scalable, and aligned
with long-term business objectives. Strategic investments in data governance
and AI infrastructure will be crucial to driving sustainable AI performance
across industries in India.” “The disparity in target outcomes between AI
Leaders and AI Followers demonstrates a lack of clear strategy and roadmap.
Where AI Followers are focused on short-term, productivity-based results, AI
Leaders have moved beyond these to more complex functional and industry use
cases,” said Shukri Dabaghi, Senior Vice President, Asia Pacific and EMEA
Emerging at SAS. “As businesses look to capitalise on the transformative
potential of AI, it’s important for business leaders to learn from the
differences between an AI Leader and an AI Follower. Avoiding a ‘gold rush’
way of thinking ensures long-term transformation is built on trustworthy AI
and capabilities in data, processes and skills,” said Mr. Dabaghi.
4 reasons why veterans thrive as cybersecurity professionals

Through their military experience, veterans learn to combat the most
sophisticated adversaries in existence and adopt an apex attacker’s
perspective. Many of today’s malicious actors are not lone individuals wearing
a hoodie and operating from a cybercafe; they’re highly skilled, well-funded
nation-state actors or part of a larger cybercrime group that operates like a
corporate organization. Dealing with such high-level adversaries requires
defenders who are trained specifically to combat their techniques. Many
veterans are trained extensively in red team attack simulations, in which they
pose as an attacker and attempt to breach an organization’s systems to assess
vulnerabilities and boost the organization’s security posture. This training
is used to combat nation-state attackers, with military members engaging in
monthly or multi-year attack simulations. ... Maintaining security requires a
distinct mentality where your approach meets the dedication of the threat
actor trying to hack into your system. Veterans can become skilled in
specialized areas like hunting for advanced adversaries within security
systems. They know that adversaries can be relentless in their attempts and
can be adept in providing relentless defense.
Responsible AI starts with transparency

Today, most foundational AI models have been trained on data scrubbed from the
public internet, so it’s essentially impossible for users to understand the
dataset at web scale. Even the model providers themselves aren’t always able
to fully understand the composition of their own training data when it’s
pulled from so many different sources across the entire internet. Even if they
were, they wouldn’t be required to disclose that information to model users.
This lack of data transparency is one reason that using publicly available AI
models may not be appropriate for enterprises. However, there are ways to work
around this. For instance, you can build proxy models, which are simple models
used to approximate the results of your more complex AI models. Building a
good proxy model requires you to balance the tradeoff between simplicity and
accuracy. Nevertheless, even a very simple approximated model can help you
understand how each feature of a model impacts its predictions. ... When it
comes to building trust, it’s impossible to fully separate your AI models from
the humans who use them. Humans naturally want to have some control over the
tools they use; if you can’t give employees that sense of control, it’s
unlikely they’ll continue to use AI.
Combating Cybercrime: What to Expect From Trump Presidency?

Trump is no stranger to combating cybercrime. His first administration updated
the National Cyber Strategy for the first time in 15 years. "The
administration will push to ensure that our federal departments and agencies
have the necessary legal authorities and resources to combat transnational
cybercriminal activity, including identifying and dismantling botnets, dark
markets and other infrastructure used to enable cybercrime," it said.
Especially where nation-state attacks are concerned, defending forward -
disrupting malicious cyber activity at its source - has been U.S. military
doctrine since 2018. But experts also see blemishes on Trump's cyber track
record, including his axing the top cybersecurity coordinator role in the
White House, weakening cyber diplomacy - a core strategy for tackling
cybercrime safe havens - and firing the head of the Cybersecurity and
Infrastructure Security Agency, which helps improve domestic resilience.
Whether the U.S. continues its strategy of naming and shaming cybercriminals
it can't reach, often in Russia, is unclear. Ian Thornton-Trump, a veteran
CISO who formerly served with the Military Intelligence Branch of the Canadian
Forces, predicts the administration could redirect resources to focus more on
China and deemphasize the naming, shaming and disruption of Russian criminals'
operations.
Transforming Enterprise Networks With AIOps: A New Era of Intelligent Connectivity
One of the primary benefits of AIOps is its ability to enhance intelligent
network management. In today's complex network environments, optimizing
performance and ensuring seamless connectivity in a continuously changing
fabric is critical. AIOps provides insights across the various IT domains
(e.g., application, security, infrastructure, etc.) that help networking
professionals identify areas for improvement, automate routine tasks, and
maintain optimal network performance. By leveraging AI-driven analytics,
organizations can ensure that their networks are always running smoothly,
reducing downtime and improving overall efficiency. ... AIOps is paving the
way for the creation of autonomous networks that didn't materialize during the
era of software-defined networking or intent-based networking. These
initiatives claimed to create self-managing, self-healing networks that could
adapt to changing conditions and demands with minimal human intervention,
except a crucial element was missing: AIOps. AIOps highlights areas where
automation can be implemented, allowing networks to respond dynamically to
issues and changes in the environment.
CIOs to spend ambitiously on AI in 2025 — and beyond

The big investments in generative AI may eventually rival traditional cloud
investments but that does not mean top cloud providers — all of whom are top
AI platforms providers — will suffer. Amazon Web Services, Microsoft Azure,
and Google Cloud Platform are enabling the massive amount of gen AI
experimentation and planned deployment of AI next year, IDC points out. ...
“In the near term, most enterprises are focusing on automation and
productivity use cases that can be implemented without fundamentally
changing business processes,” McCarthy adds. “However, the higher value use
cases involve new business models, which require widespread organizational
change.” Stephen Crowley, senior advisor for S&L Ventures and former CIO
of global technology solutions at Covetrus, still sees that future as a
little way off. “Building the foundation is different from moving to
production with AI apps. I think that will take longer,” he says. ... The
risks of accidentally exposing sensitive corporate data or designing gen AI
models that fly afield of their intended missions are also top of mind for
Dairyland Power’s Melby, who is working with a Microsoft partner to deploy
Copilot and Azure OpenAI capabilities to employees in a secure manner.
Building a workplace culture that supports mental well-being: A guide
Balancing productivity and employee well-being can be challenging but
achievable. Creating a supportive work environment makes employees more
likely to be engaged and productive. This approach not only benefits
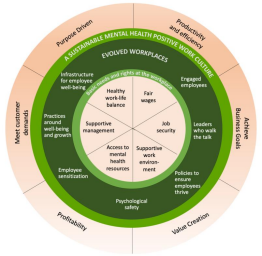
employees but also drives better business outcomes. ... To co-relate this
model to mental health in the workplace, we can consider the inner
foundational level as the basic needs and rights that must be met for
employees, such as fair wages, job security, and a healthy work-life balance
... The inner circle or foundational level showcases the basic needs and
rights of employees. Ensuring employees have fair wages, access to mental
health resources, supportive management, and a healthy work-life balance.
Avoid overwork, and reduce workplace stressors. The middle circle depicts
evolved workplaces. A mental health mature workplace will invest in engaged
employees, leaders who walk the talk, policies that ensure employees thrive,
and psychological safety and the necessary infrastructure, sensitization and
practice to support employee well-being and growth. The outer circle depicts
a sustainable mental health positive culture that balances and is focused on
achieving higher levels of maturity in culture and processes.
7 reasons security breach sources remain unknown

As attacks become more sophisticated it can become more difficult to unpack
the cause of problems, says Raj Samani, SVP and chief scientist at security
firm Rapid7. “We must acknowledge that many threat groups take measures to
obfuscate their tracks, invariably making any investigation more
challenging,” he says. “However, this is often only part of the reason why
identifying the source of the breach is so difficult.” Samani adds: “Whilst
technologies will aid the investigation, the time spent retroactively
reviewing such incidents often competes with the urgency of the next issue,
or indeed, the demand to get the environment operational again.” Many
breaches are detected long after they occur, and delays make it harder to
identify root causes. Here, time is on the side of an attacker, with
computer forensic capabilities fading over time as data is amended,
overwritten, and deleted. “Hackers are always finding new ways to blend into
regular network traffic, so even the best detection systems can end up
playing a never-ending game of ‘whack-a-mole’ with threats,” says Peter
Wood, CTO at Spectrum Search. “And while the systems might flag something
suspicious, figuring out exactly where it started is another story
altogether.”
Quote for the day:
“Creativity is thinking up new things. Innovation is doing new things.” --
Theodore Levitt
No comments:
Post a Comment