Chasing The Myth: Why Achieving Artificial General Intelligence May Be A Pipe Dream
 Often, people confuse AGI with AI, which is loosely used nowadays by marketers
and businesses to describe run-of-the-mill machine learning applications and
even normal automation tools. In simple words, Artificial General Intelligence
involves an ever-growing umbrella of abilities of machines to perform various
tasks significantly better than even the brightest of human minds. An example of
this could be AI accurately predicting stock market trends to allow investors to
rake in profits consistently. Additionally, AGI-based tools can interact with
humans conversationally and casually. In recent times, domotic applications such
as smart speakers, smart kitchens and smartphones are gradually becoming more
interactive as they can be controlled with voice commands. Additionally,
advanced, updated versions of such applications show distinctly human traits
such as humor, empathy and friendliness. However, such applications just stop
short of having genuinely authentic interactions with humans. The prospective
future arrival of AGI, if it happens, will plug this gap.
Often, people confuse AGI with AI, which is loosely used nowadays by marketers
and businesses to describe run-of-the-mill machine learning applications and
even normal automation tools. In simple words, Artificial General Intelligence
involves an ever-growing umbrella of abilities of machines to perform various
tasks significantly better than even the brightest of human minds. An example of
this could be AI accurately predicting stock market trends to allow investors to
rake in profits consistently. Additionally, AGI-based tools can interact with
humans conversationally and casually. In recent times, domotic applications such
as smart speakers, smart kitchens and smartphones are gradually becoming more
interactive as they can be controlled with voice commands. Additionally,
advanced, updated versions of such applications show distinctly human traits
such as humor, empathy and friendliness. However, such applications just stop
short of having genuinely authentic interactions with humans. The prospective
future arrival of AGI, if it happens, will plug this gap.
JavaScript Framework Unpoly and the HTML Over-the-Wire Trend
JavaScript is the most popular programming language in the world, and React is one of its leading libraries. Initially released in 2013, React was designed to be a library for helping developers craft user interfaces (UIs). According to Henning Koch, React and Unpoly aren’t entirely opposites. They share some likenesses, but there are a few important distinctions. “What both frameworks share is that they render a full page when the user navigates, but then only fragments of that new page are inserted into the DOM, with the rest being discarded,” he explained. “However, while a React app would usually call a JSON API over the network and render HTML in the browser, Unpoly renders HTML on the server, where we have synchronous access to our data and free choice of programming language.” Still, Koch acknowledges there are some instances where React and SPA’s are suitable choices. He went on to say, “There are still some cases where a SPA approach shines. For instance, we recently built a live chat where messages needed to be end-to-end encrypted.Researchers make a quantum storage breakthrough by storing a qubit for 20 milliseconds
 The new 20-millisecond milestone, however, could be just the breakthrough
Afzelius' team was looking for. "This is a world record for a quantum memory
based on a solid-state system, in this case a crystal. We have even managed to
reach the 100 millisecond mark with a small loss of fidelity," Azfelius said.
For their experiments, the researchers kept their crystals at temperatures of
-273,15°C so as not to disturb the effect of entanglement. "We applied a small
magnetic field of one thousandth of a Tesla to the crystal and used dynamic
decoupling methods, which consist in sending intense radio frequencies to the
crystal," said Antonio Ortu, a post-doctoral fellow in the Department of Applied
Physics at UNIGE. "The effect of these techniques is to decouple the rare-earth
ions from perturbations of the environment and increase the storage performance
we have known until now by almost a factor of 40," he added. The result of this
experiment could allow for the development of long-distance quantum
telecommunications networks, though the researchers would still have to extend
the storage time further.
The new 20-millisecond milestone, however, could be just the breakthrough
Afzelius' team was looking for. "This is a world record for a quantum memory
based on a solid-state system, in this case a crystal. We have even managed to
reach the 100 millisecond mark with a small loss of fidelity," Azfelius said.
For their experiments, the researchers kept their crystals at temperatures of
-273,15°C so as not to disturb the effect of entanglement. "We applied a small
magnetic field of one thousandth of a Tesla to the crystal and used dynamic
decoupling methods, which consist in sending intense radio frequencies to the
crystal," said Antonio Ortu, a post-doctoral fellow in the Department of Applied
Physics at UNIGE. "The effect of these techniques is to decouple the rare-earth
ions from perturbations of the environment and increase the storage performance
we have known until now by almost a factor of 40," he added. The result of this
experiment could allow for the development of long-distance quantum
telecommunications networks, though the researchers would still have to extend
the storage time further.3 Tips to Take Advantage of the Future Web 3.0 Decentralized Infrastructure
 There's been a lot of talk of innovation and helping the little guy through
blockchain. But, huge resources and backing are needed in order to sustain a
project and take it mainstream on a longer time horizon. Even with a brilliant
technical team, excellent developers and a well-thought-out whitepaper and
tokenomics ecosystem, the project won’t go anywhere. Unless, it's marketed on
major outlets and pushed towards consumers consistently. This is an
attention-based economy and it takes effort to capture mainstream attention and
to keep it. Moreover, it will take a great deal of finance to develop VR
technology that is high-quality, integrated into the many metaverses,
cost-effective and marketed well. A small team might be able to conjure up a
good initial project. But, they will likely need to partner up or hand off the
project so it can become mainstream. Always assess who a project is affiliated
with and what partnerships they have. This is a strong indication of how much
they value their own project and also offers numerous other benefits for various
scenarios.
There's been a lot of talk of innovation and helping the little guy through
blockchain. But, huge resources and backing are needed in order to sustain a
project and take it mainstream on a longer time horizon. Even with a brilliant
technical team, excellent developers and a well-thought-out whitepaper and
tokenomics ecosystem, the project won’t go anywhere. Unless, it's marketed on
major outlets and pushed towards consumers consistently. This is an
attention-based economy and it takes effort to capture mainstream attention and
to keep it. Moreover, it will take a great deal of finance to develop VR
technology that is high-quality, integrated into the many metaverses,
cost-effective and marketed well. A small team might be able to conjure up a
good initial project. But, they will likely need to partner up or hand off the
project so it can become mainstream. Always assess who a project is affiliated
with and what partnerships they have. This is a strong indication of how much
they value their own project and also offers numerous other benefits for various
scenarios. A diffractive neural network that can be flexibly programmed
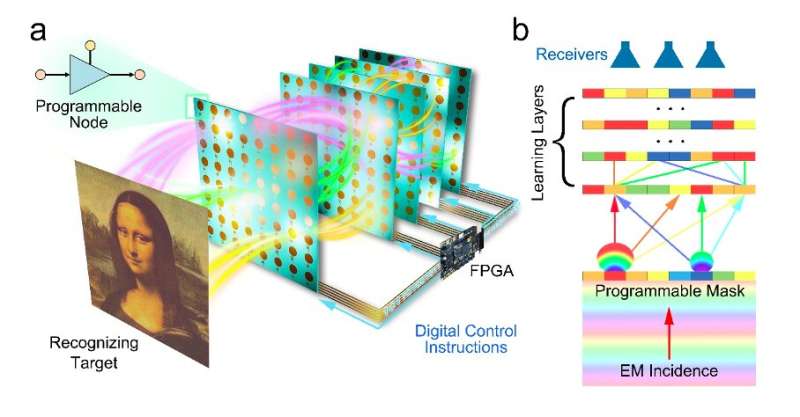 In initial evaluations, the diffractive neural network introduced by this team
of researchers achieved very promising results, as it was found to be highly
flexible and applicable across a wide range of scenarios. In the future, it
could thus be used to solve a variety of real-world problems, including image
classification, wave sensing and wireless communication coding/decoding.
Meanwhile, Cui and his colleagues will work on improving its performance
further. "The prototype implemented in this work is based on a 5-layer
diffractive neural network, each layer has 64 programmable neural networks, and
the total number of nodes in the network is relatively low," Cui added. "At the
same time, the operating frequency band of this network is lower, resulting in a
larger size of the physical network. In our next studies, we plan to further
increase the scale of the programmable neurons of the network, improve the
network integration, reduce the size and form a set of intelligent computers
with stronger computing power and more practicality for sensing and
communications."
In initial evaluations, the diffractive neural network introduced by this team
of researchers achieved very promising results, as it was found to be highly
flexible and applicable across a wide range of scenarios. In the future, it
could thus be used to solve a variety of real-world problems, including image
classification, wave sensing and wireless communication coding/decoding.
Meanwhile, Cui and his colleagues will work on improving its performance
further. "The prototype implemented in this work is based on a 5-layer
diffractive neural network, each layer has 64 programmable neural networks, and
the total number of nodes in the network is relatively low," Cui added. "At the
same time, the operating frequency band of this network is lower, resulting in a
larger size of the physical network. In our next studies, we plan to further
increase the scale of the programmable neurons of the network, improve the
network integration, reduce the size and form a set of intelligent computers
with stronger computing power and more practicality for sensing and
communications."Microsoft Azure Developers Awash in PII-Stealing npm Packages
 In this case, the cyberattackers were pretending to offer a key set of existing,
legitimate packages for Azure. “It became apparent that this was a targeted
attack against the entire @azure npm scope, by an attacker that employed an
automatic script to create accounts and upload malicious packages that cover the
entirety of that scope,” researchers said in a Wednesday posting. “The attacker
simply creates a new (malicious) package with the same name as an existing
@azure scope package, but drops the scope name.” Npm scopes are a way of
grouping related packages together. JFrog found that besides the @azure scope,
other popular package groups were also targeted, including @azure-rest,
@azure-tests, @azure-tools and @cadl-lang. The researchers added, “The attacker
is relying on the fact that some developers may erroneously omit the @azure
prefix when installing a package. For example, running npm install core-tracing
by mistake, instead of the correct command – npm install @azure/core-tracing.”
The attacker also tried to hide the fact that all of the malicious packages were
uploaded by the same author, “by creating a unique user per each malicious
package uploaded,” according to JFrog.
In this case, the cyberattackers were pretending to offer a key set of existing,
legitimate packages for Azure. “It became apparent that this was a targeted
attack against the entire @azure npm scope, by an attacker that employed an
automatic script to create accounts and upload malicious packages that cover the
entirety of that scope,” researchers said in a Wednesday posting. “The attacker
simply creates a new (malicious) package with the same name as an existing
@azure scope package, but drops the scope name.” Npm scopes are a way of
grouping related packages together. JFrog found that besides the @azure scope,
other popular package groups were also targeted, including @azure-rest,
@azure-tests, @azure-tools and @cadl-lang. The researchers added, “The attacker
is relying on the fact that some developers may erroneously omit the @azure
prefix when installing a package. For example, running npm install core-tracing
by mistake, instead of the correct command – npm install @azure/core-tracing.”
The attacker also tried to hide the fact that all of the malicious packages were
uploaded by the same author, “by creating a unique user per each malicious
package uploaded,” according to JFrog.An Introduction to Mathematical Thinking for Data Science
Schwinger effect seen in graphene
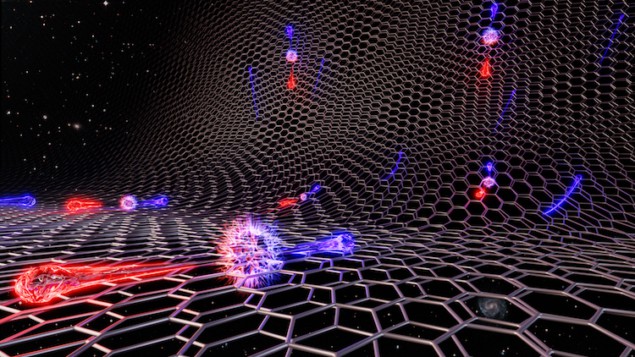 In theory, a vacuum is devoid of matter. In the presence of strong electric or
magnetic fields, however, this void can break down, causing elementary particles
to spring into existence. Usually, this breakdown only occurs during intense
astrophysical events, but researchers at the UK’s National Graphene Institute at
the University of Manchester have now brought it into tabletop territory for the
first time, observing this so-called Schwinger effect in a device based on
graphene superlattices. The work will be important for developing electronic
devices based on graphene and other two-dimensional quantum materials. In
graphene, which is a two-dimensional sheet of carbon atoms, a vacuum exists at
the point (in momentum space) where the material’s conduction and valence
electron bands meet and no intrinsic charge carriers are present. Working with
colleagues in Spain, the US, Japan and elsewhere in the UK, the Manchester team
led by Andre Geim identified a signature of the Schwinger effect at this Dirac
point, observing pairs of electrons and holes created out of the vacuum.
In theory, a vacuum is devoid of matter. In the presence of strong electric or
magnetic fields, however, this void can break down, causing elementary particles
to spring into existence. Usually, this breakdown only occurs during intense
astrophysical events, but researchers at the UK’s National Graphene Institute at
the University of Manchester have now brought it into tabletop territory for the
first time, observing this so-called Schwinger effect in a device based on
graphene superlattices. The work will be important for developing electronic
devices based on graphene and other two-dimensional quantum materials. In
graphene, which is a two-dimensional sheet of carbon atoms, a vacuum exists at
the point (in momentum space) where the material’s conduction and valence
electron bands meet and no intrinsic charge carriers are present. Working with
colleagues in Spain, the US, Japan and elsewhere in the UK, the Manchester team
led by Andre Geim identified a signature of the Schwinger effect at this Dirac
point, observing pairs of electrons and holes created out of the vacuum.
The risk of undermanaged open source software
 Some risks are the same regardless of whether solutions are built with
vendor-curated or upstream software; however it is the responsibility for
maintenance and security of the code that changes. Let’s make some assumptions
about a typical organization. That organization is able to identify where all of
its open source comes from, and 85% of that is from a major vendor it works with
regularly. The other 15% consists of offerings not available from the vendor of
choice and comes directly from upstream projects. For the 85% that comes from a
vendor, any security concerns, security metadata, announcements and, most
importantly, security patches, come from that vendor. In this scenario, the
organization has one place to get all of the needed security information and
updates. The organization doesn’t have to monitor the upstream code for any
newly discovered vulnerabilities and, essentially, only needs to monitor the
vendor and apply any patches it provides.
Some risks are the same regardless of whether solutions are built with
vendor-curated or upstream software; however it is the responsibility for
maintenance and security of the code that changes. Let’s make some assumptions
about a typical organization. That organization is able to identify where all of
its open source comes from, and 85% of that is from a major vendor it works with
regularly. The other 15% consists of offerings not available from the vendor of
choice and comes directly from upstream projects. For the 85% that comes from a
vendor, any security concerns, security metadata, announcements and, most
importantly, security patches, come from that vendor. In this scenario, the
organization has one place to get all of the needed security information and
updates. The organization doesn’t have to monitor the upstream code for any
newly discovered vulnerabilities and, essentially, only needs to monitor the
vendor and apply any patches it provides.
Confessions of a Low-Code Convert
A lot of programmers hear “low-code tools” and get twitchy. But the reality, especially if you are building processes versus tools, is that low-code solutions don’t prevent me from being creative or effective; they enable it. They handle tedious, labor-intensive boilerplate items and free me up to write the lines of JavaScript I actually need to uniquely express a business problem. And there are still plenty of places where you need to (and get to!) write that clever bit of code to implement a unique business requirement. It’s much easier to fix or refactor an app written by a low-code citizen developer in the line of business than it is to decipher whatever madness they’ve slapped together in their massive, mission-critical Excel spreadsheet. I find low-code platforms incredibly sanity-saving. They reduce noise in the system and obviate a lot of the admittedly unexciting elements of my work. The technology landscape has changed dramatically. Cloud adoption has introduced a world of serverless containerization.Quote for the day:
"Leadership - leadership is about taking responsibility, not making excuses." -- Mitt Romney
No comments:
Post a Comment