Graphcore Supercharges IPU With WoW Processor

Graphcore affirmed that its Bow IPU chip delivers 40% higher performance and 16%
better power efficiency for real-world applications when compared to previous
versions or models. Furthermore, the British semiconductor firm stated that its
Bow Pod flagship products could deliver more than 89 petaFLOPS of AI computing.
Additionally, the superscale Bow Pod can scale up to 350 petaFLOPS. Graphcore’s
plan to develop an ultra-intelligence AI supercomputer is one of the fascinating
announcements in the tech world. Graphcore emphasized how “approximately 100
billion neurons and more than 100 trillion parameters in a
biological-neural-network system that delivers a level of computing yet to be
matched by any silicon computers.” It also mentioned that it is developing an AI
computer that will exceed the parametric capacity of the brain. The computer’s
name is ‘Good,’ which is named after the pioneer of computer science, Jack Good.
The pivotal achievements of Jack Good during the Second World War are worth
reading.
5 Best Practices For Code Review
You must seek advice or help from fellow developers as everyone’s contribution
is equally important. Experienced ones can identify the mistakes within a second
and rectify them but the young minds come up with more simple ways to implement
a task. So, ask your juniors as they have the curiosity to learn more. To make
it perfect, they find other ways which will benefit in two ways: a) They’ll get
deeper knowledge; b) Solution can be more precise. ... A piece of code that
does a single task that can be called whenever required. Avoid repetition of
codes. Check if you’ve to repeat code for different tasks, again and again, so
there you can use these functions to reduce the repeatability of code. This
process of using functions maintains the codebase. For example, if you’re
building a website. Several components are made in which basic functionalities
are defined. If a block of code is being repeated so many times, copy that block
of code or function to a file that can be invoked (reused) wherever and whenever
required. This also reduces the complexity level and lengthiness of the
codebase.
Rush to cloud computing is outpacing organizations' ability to adapt

Educating the business is a vital piece of an effective strategy. The Harvard
Business Review report describes how Chegg, an educational technology and
information publisher, has been rearchitecting its cloud approach over the past
year to create smaller, more flexible cloud accounts for use by its engineering
teams. "We've been in cloud for so long, we've learned a lot of what's working
and what isn't working," John Heasman, chief information security officer, is
quoted in the study. "We ended up in a position where we needed to take a step
back and look at our architecture to align with best practices in cloud
infrastructure and improve our processes overall." Heasman and his team
concentrated on educating the company's leaders on the ways its cloud strategy
will result in new services. "It's not just a case of saying, 'Here's a new
account. It's yours,'" Heasman says. "It required a lot of planning to ensure
the right level of oversight while still enabling our team to get the full
benefit of cloud-native technology."
How Attack Surface Management Preempts Cyberattacks

ASM is a technology that either mines Internet datasets and certificate
databases or emulates attackers running reconnaissance techniques. Both
approaches aim at performing a comprehensive analysis of your organization's
assets uncovered during the discovery process. Both approaches include scanning
your domains, sub-domains, IPs, ports, shadow IT, etc., for internet-facing
assets before analyzing them to detect vulnerabilities and security gaps.
Advanced ASM includes actionable mitigation recommendations for each uncovered
security gap, recommendations ranging from cleaning up unused and unnecessary
assets to reduce the attack surface to warning individuals that their email
address is readily available and might be leveraged for phishing attacks. ASM
includes reporting on Open-Source Intelligence (OSINT) that could be used in a
social engineering attack or a phishing campaign, such as personal information
publicly available on social media or even on material such as videos, webinars,
public speeches, and conferences.
How artificial intelligence is influencing the arms race in cybersecurity

There are two main ways A.I. is bolstering cybersecurity. First, A.I. can help
automate many tasks that a human analyst would often handle manually. These
include automatically detecting unknown workstations, servers, code
repositories, and other hardware and software on a network. It can also
determine how best to allocate security defenses. These are data-intensive
tasks, and A.I. has the potential to sift through terabytes of data much more
efficiently and effectively than a human could ever do. Second, A.I. can help
detect patterns within large quantities of data that human analysts can’t see.
For example, A.I. could detect the key linguistic patterns of hackers posting
emerging threats on the dark web and alert analysts. More specifically,
A.I.-enabled analytics can help discern the jargon and code words hackers
develop to refer to their new tools, techniques, and procedures. One example is
using the name Mirai to mean botnet. Hackers developed the term to hide the
botnet topic from law enforcement and cyberthreat intelligence professionals.
Three reasons why your API security is failing

Many organisations have adopted DevOps practices, realising efficiencies in the
development cycle. It’s natural that they would want to remove similar barriers
with security. In the recent Salt Labs State of API Security report, 40% of
respondents said developers or DevOps teams hold primary responsibility for
securing APIs, but 95% of respondents experienced an API security incident in
the past year, highlighting that the burden cannot fall solely on developer
shoulders. Developers make applications work, but attackers make them perform in
unintended ways. It’s difficult for developers to shift into an attackers
mindset. Despite the methods available to identify potential vulnerabilities,
it’s rare that all aspects of code are tested. Furthermore, as it is so
difficult to keep up with today’s ultra-fast code, developers typically only
test primary apps or specific areas of functionality and most scanning tools
depend on best practices and signatures to identify vulnerabilities. Yet, these
approaches are ineffective at identifying unique logic vulnerabilities.
Kremlin’s Aggression Divides Digital Ecosystems Along Tech Trenches
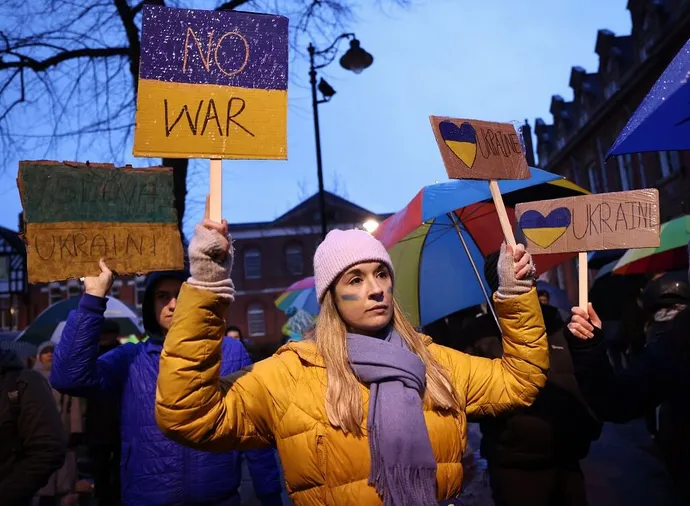
Sanctions to restrict international financial transactions and other commerce
with Russia have already been put to work. Now that country faces the loss of
certain technology services and resources as more tech companies seek to
decouple themselves from the aggressor state. As the grim war on the ground
wages on, new lines of demarcation emerge in response across the digital world.
The future of greater connectivity may look drastically different than expected,
says Raj Shah, head of tech, media, and telecoms for North America at digital
consulting firm Publicis Sapient. The first globalization was supposed be a
singular, interconnected world, he says, but China emerged as a challenger to
the United States and other economically allied nation states. Now Russia’s
actions may further fracture the dynamics of the digital landscape. “There does
appear to be this fragmentation that’s going to start to happen,” Shah says. ...
There may be some interchanges of information in buffer zones, he says, where
some technology and commerce from opposing geopolitical spheres can intersect,
but there will also be cordoned-off spaces.
Update: Samsung Confirms Source Code Stolen in Breach
The ransomware group released a teaser on its Telegram channel before posting
the data saying, “get ready, Samsung data coming today.” Then the gang posted
confidential Samsung source code data in a compressed file, available on torrent
and split it into three parts, which includes almost 190GB of data. Lapsus$
published a description of the leak, which it says includes: source code for
every Trusted Applet installed on all Samsung device's TrustZone with specific
code for every type of TEE OS (QSEE, TEEGris, etc). Trusted Applets are used for
sensitive operations such as full access control and encryption. The group says
it also includes DRM modules and Keymaster/Gatekeeper. Algorithms for all
biometric unlock operations include: “Source code that communicates directly
with sensor (down to the lowest level), we're talking individual RX/TX bit
streams here and boot loader source code for all recent Samsung devices,
including Knox data and code for authentication," the gang says.
Three unusual questions to make job candidates think

A job interview is intended to be a kind of crystal ball, one that gives the
employer a sense of what somebody is going to be like not only the first day but
also after six months, when the honeymoon period is over and they’re facing a
few challenges. I can’t think of a better question for ascertaining how an
employee will behave over time. Of course, the thought of asking such a personal
question may understandably make interviewers uncomfortable (although I’ve been
assured by many HR professionals that the question is fair game). If so, simply
focus on the positive by asking, “What qualities do you like the most in your
parents?” Here’s the question that Clara Lippert Glenn, then CEO of the
energy-industry training company Oxford Princeton Programme, told me she poses
to candidates: “If you woke up tomorrow morning, and there were no humans left
on the earth—just animals—what kind of animal are you?” I’ve used this question
many times as an icebreaker with small groups, and added a second beat to the
question, which is to ask people to explain why they chose that particular
animal.
Agile transformation: 3 ways to achieve success

Too many organizations left much of their knowledge untapped due to outdated and
bottleneck processes. In fact, 80 percent of undocumented human knowledge goes
untapped. By mining every organizational knowledge resource, employees can work
together beyond the scope of their own team, personal network, and
organizational silos, eliminating remote worker disconnects, data gaps, and
inaccurate or outdated information. Moreover, employees become empowered to
build on their knowledge set, increase productivity, enjoy a greater stake in
their work, and reach their potential without organizational hierarchies,
geography, cultures, or languages impeding their work. The result is higher
cultural inclusivity and increased organizational agility. Investing in tools,
procedures, and cultural shifts that close the knowledge gaps, break down silos,
and foster greater collaboration provides a return on investment in agility,
retention, and productivity. Additionally, higher concentrations of knowledge
collaboration unleash enormous amounts of tacit knowledge that would otherwise
remain hidden and unutilized.
Quote for the day:
"Take time to deliberate; but when the
time for action arrives, stop thinking and go in." --
Andrew Jackson
No comments:
Post a Comment