The Role of Business Architecture in Defining Data Architecture
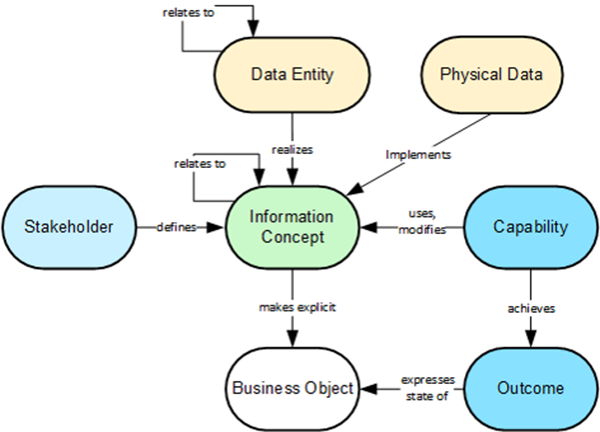
Data architects can systematically examine the information concepts in the
information map and define corresponding data entities for each of those
concepts. There is no assumption that the data model and the information map
will be identical. Data architects will apply data modeling techniques to
formalize data entities as appropriate. The information map’s role is rather to
provide business ecosystem transparency, delivering a business-driven
perspective to ensure that data models and related deployments enable and do not
hinder the organization they are meant to benefit. As data entities are defined,
data architects can leverage information concept relationships to establish
corresponding relationships among data entities in the data models. All
information maps have a set of relationships that data architects may
interrogate to derive their entity relationships. The next step is to attribute
the data entities. Figure 5 depicts data attribute derivation using child
capabilities defined under Agreement Management.
HTTP/2 Implementation Errors Exposing Websites to Serious Risks
To show how such an attack would work, Kettle pointed to an exploit he executed
against Netflix where front-end servers performed HTTP downgrading without
verifying request lengths. The vulnerability allowed Kettle to develop an
exploit that triggered Netflix's back-end to redirect requests from Netflix's
front-end to his own server. That allowed Kettle to potentially execute
malicious code to compromise Netflix accounts, steal user passwords, credit card
information, and other data. Netflix patched the vulnerability and awarded
Kettle its maximum bounty of $20,000 for reporting it to the company. In another
instance, Kettle discovered that Amazon's Application Load Balancer had failed
to implement an HTTP/2 specification regarding certain message-header
information that HTTP/1.1 uses to derive request lengths. With this
vulnerability, Kettle was able to show how an attacker could exploit it to
redirect requests from front-end servers to an attacker-controlled server.
How to prepare your Windows network for a ransomware attack

Too many of us are still reliant on older server platforms that make it harder
to roll out security solutions through Active Directory. We may have Server
2016 and Server 2019 servers in our network, but we’re not taking advantage of
the security features of that domain functional level. Too many of us are
still on older forest and domain functional levels because we have older
servers or applications and a lack of testing that keep us from rolling out
these newer features. Or we have vendors that won’t certify newer platforms
and Active Directory features. Raising your forest level to 2016 provides many
features that better protect the network such as privileged access management
and automatic rolling of NTLM secrets on a user account. If your functional
level is still 2008 R2, you don’t have a UI for the Active Directory recycle
bin, which makes it easier for recovery. It also doesn’t allow you to get rid
of an old security hole of unchanging passwords on your service accounts if
you are still running 2008 R2 functional level.
Can the public cloud become confidential?
The Confidential Cloud is a secure confidential computing environment formed
over one or more public cloud providers. Applications, data, and workloads
within a Confidential Cloud are protected by a combination of hardware-grade
encryption, memory isolation, and other services in the underlying host. Like
micro-segmentation and host virtualization, resources within a Confidential
Cloud are isolated from all processes and users in a default zero-trust
posture. But the Confidential Cloud does more than isolate network
communications, it isolates the entire IT environment used by a
workload—including compute, storage, and networking. That enables support for
virtually any application. Because Confidential Cloud protection is
inextricably part of data, the protection extends wherever the data goes.
Legacy enterprise perimeters are defined by physical appliances, but a
Confidential Cloud’s perimeter is established by an inextricable combination
of hardware isolation, encryption, and explicit least-privileged access
policy.
Why the future of service is hybrid

For many businesses though, this has led to employment issues, especially as
the workforce ages. Knowledge loss is an increasingly common problem.
According to the Service Council, 70% of service organisations say they would
be burdened by the knowledge loss of a retiring workforce in the next five to
10 years, while 50% claim they are currently facing a shortage of resources to
adequately meet service demand. Automation is great, but it will only go so
far to help. Interestingly, the TSIA recently found that half of all field
services organisations don’t have a formal career path in place for their
field service engineers. This, in my view, is a huge point of unnecessary
commercial risk. These organisations are not doing enough to prepare younger
service techs for a mixed reality future – one where they will have to work
more closely with digital technology and machines than any previous
generation. It won’t happen by accident. There is certainly a need for an
integral ‘system of record’ that captures accurate data about equipment ‘as
maintained’.
How to Recognise and Reduce HumanDebt
HumanDebt™ is the equivalent to Technical Debt but for people. All of the
initiatives, the projects, the intentions we (the organisation) had to do
better by our employees, but we abandoned halfway. All of the missed
opportunities to make their lives and their work easier and more joyful. All
of the empty talk on equality, respect, lack of blame, courage and trust. All
of the missing focus on empowered teams and servant leadership. All of the
lack of preoccupation or resources for building better team dynamics. All of
the toxic culture created by these. That’s Human Debt. ... It is tempting to
believe that this type of debt is the organisation’s problem only. Even more
tempting is to believe that it only happens at that macro, cultural level and
that that is the only level where it can be fixed. Both are fallacies though.
It’s important that the organisation has a degree of recognition, which
enables them to offer "organisational permission" and help, as there really is
only one solid thing to start with - empower teams to work on their own
dynamics and improve their happiness by giving them the resources they need to
do so.
How to deal with a toxic teammate
Toxic behavior may have occurred less frequently or been less noticeable
during the pandemic. “There has been more stress but also a lot of
grace-giving and cutting-of-slack to account for whatever people have going on
in their personal and professional lives,” Cuthbert says. “The water cooler is
gone and hasn’t been replaced and there is less of a forum for those who are
negative or unhappy.” But it can take numerous forms. “Motivating through fear
and unattainable goals and timelines, obfuscating expectations and scope of
job descriptions or projects, not clearly identifying the North Star and who
is doing what, being inconsistent in holding people accountable, dominating,
yelling, talking over others, and interrupting are all signs of toxic
behavior,” Mattheis says. “Working remotely has not changed that reality. What
it has done is adjust how it looks and feels as well as made it more difficult
to speak to it and hold people accountable.” Like dealing with a toxic boss,
responding to a peer’s unhealthy dynamics can be tricky, but there are
constructive approaches for using emotional intelligence to address the issues
and mitigate their impact on your own productivity and well being.
Chip shortage has networking vendors scrambling

The semiconductor industry is predicting a possible recovery in 2023. But who
knows what demand will be at that time, Sadana said. Part of the problem is
that current semiconductor foundry capacity is not adequate to meet the recent
surge in global demand, wrote Baron Fung, industry analyst at Dell'Oro Group,
in a recent blog. “The cost of servers and other data center equipment is
projected to rise sharply in the near term partly due to the global
semiconductor shortages,” Fung stated. “An increase of server average selling
prices could approach the double-digit level that was observed in 2018, which
was another period of tight supply and high demand. However, in the longer
term, we anticipate that supply and demand dynamics could reach equilibrium
and that technology transitions could drive market growth.” ... “We continue
to proactively manage the supply chain, and our strategic relationship with
Broadcom is helping us in this regard. Importantly, we have secured vendor
commitments that will allow us to accelerate product delivery and bring down
backlog as of Q2 and beyond,” Thomas stated.
Why businesses should embrace cloud-native development

Containers provide the infrastructure to realise a microservices architecture
in practice. It provides individual standalone components for an app that can
be independently replaced, changed, or removed without jeopardising the rest
of your infrastructure. This is essential to realise the cloud-native vision
because the completeness of a container package and its agnosticism to its
environment ensures the portability needed for cloud-native apps –
containerised apps can be deployed in whatever cloud environment you operate
in, whether it be public, private, or hybrid. The use of containers in the
cloud-native model thereby brings speed and scalability that cannot be
achieved through traditional systems architecture, and addresses a fundamental
business need: for changes in software to be applied quickly and seamlessly so
that tasks can be completed efficiently and inexpensively. For all these
reasons, containers are one of the biggest trends in enterprise software
development
CISA's Easterly Unveils Joint Cyber Defense Collaborative
"To some extent, some of these activities are already going on across the
federal government, but they're running largely in stovepipes. So the idea is
that we bring together our partners in the government and our private sector
partners to really mature this planning capability," Easterly said. Besides
CISA and its parent organization, the Department of Homeland Security, other
federal government participants will include the U.S. National Security
Agency, U.S. Cyber Command and the FBI. Easterly announced nine companies have
signed up to participate,: CrowdStrike, Palo Alto Networks, FireEye, Amazon
Web Services, Google, Microsoft, AT&T, Verizon and Lumen. The JCDC will
build on the relationships CISA has with Information Sharing and Analysis
Centers, or ISACs, which represent various industries. The concept for the new
initiative came from the Cyberspace Solarium Commission, which published its
report in 2020 (see: Senate Approves Chris Inglis as National Cyber
Director).
Quote for the day:
"Added pressure and responsibility
should not change one's leadership style, it should merely expose that which
already exists." -- Mark W. Boyer
No comments:
Post a Comment